Proper form is very important to lifting weight and strength training. One wrong move could potentially lead to an injury. Follow along in this how-to video critique by Mark Rippetoe as he guides someone through the correct set up for a power clean and push jerk. Better form can lead to more effective lifting. Practice your power clean and push jerk.

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Need a little power from your car battery? This OzLabs video will show you how to get that power in a detailed demonstration.

This video shows how to check and add power steering fluid to your car. If your like me and don't even know where the power steering fluid is this will help you.

Did you know there are several functions accessible by shortcuts using the power button on the Nokia N900 smartphone? This tech support video from Nokia details how to bring up a menu allowing you to turn on silent mode, lock the screen and keyboard, and more.

Doing electrical work is one of the most intimidating tasks for a novice home repairman. But if you know what you're doing, the risk is pretty minimal. In this clip, Mark Donovan of HomeAdditionPlus.com shows us how wire a combo outlet with power.

Learn how to charge a 12 Volt Battery using a Solar Power Battery Maintainer by watching this how-to video. This method can be used to charge 12 volt batteries of any kind - cars, trucks, boats, motorcycles, tractors, lawn equipment - any kind of 12 volt battery you can think of!

SiFu Lee talks about power training and his student demonstrates shock-up training. Later in the video he talks about different Wing Chun Punches

Fixing power door locks requires replacing the door lock actuator. Learn how to replace the power door lock actuator in these free auto repair video instructions featuring a certified mechanic.

So, your children have the same old boring Fisher-Price Power Wheels that all the other kids on the block have. Do you really want your child to be like all of the rest? No, I didn't think so. Turn those miniature Power Wheels, Dumar or Peg Perego vehicles into a little bit of realism, if you can handle it. All it takes is a little modification and you'll be wishing you were five again. With a few simple hacks, your son and daughter will be burning rubber, jumping curbs and burying those othe...

The story of the HoloLens has been a mix of work and play. But while many developers have devoted time to creating gaming and entertainment apps for the HoloLens 1, with the HoloLens 2, Microsoft has been encouraging everyone to focus more on the enterprise side of things.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

Google just released the second developer preview of the Android 8.1 update for Nexus and Pixel devices, and even though it's just a point-one release, there are lots of cool changes. Before you run off to join the Android beta program and try the new version, it's worth reading up on what's new.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

How do I get rid of these zits?! Whether its pimples, blackheads, or whiteheads, the name is the same, and the name is acne.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

The drinking straw isn't just there to help you make annoying noises when you get to the bottom of your soda. That little tube of plastic is extremely versatile and can make your life a lot easier with a little know-how. Curious? Read on to find out more.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

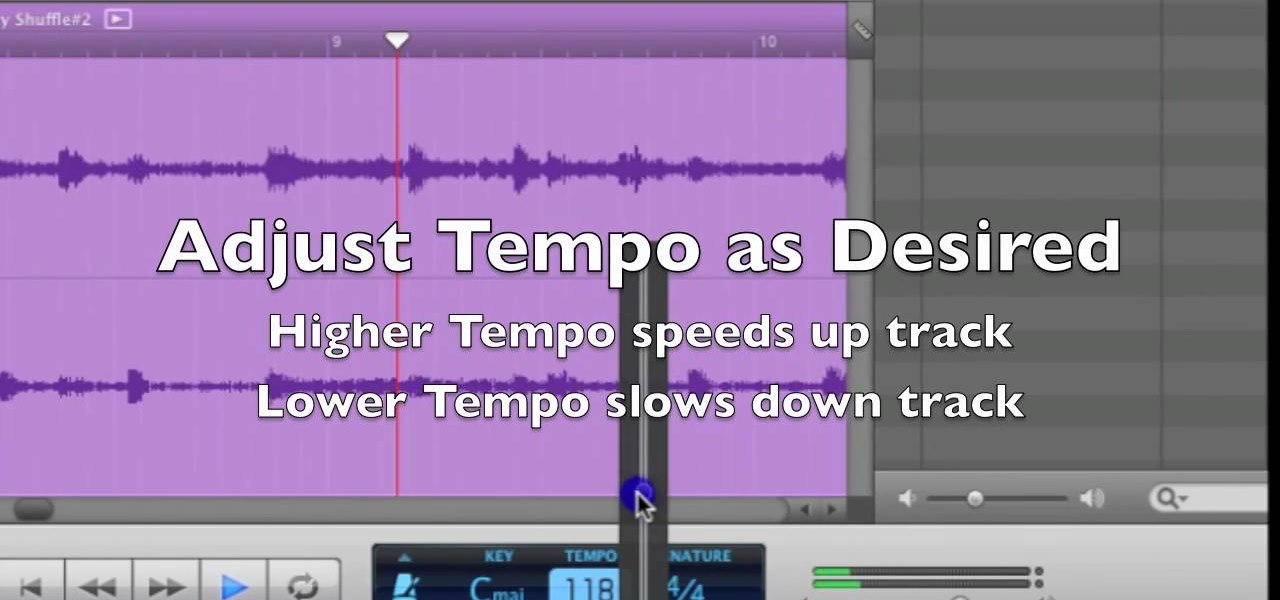
Anyone with a Mac knows the power of GarageBand, but not all iLife users know the ways to slow or speed up their songs in GarageBand. This video will show you exactly how to change the tempo of your song creations, which is actually a really simple thing to do.

Everyone could benefit from shedding a few pounds, but what about those who need to lose a little bit more weight? Exercise isn't an option for everyone, with as busy as our lives are right now. It's hard to go running and do a few pushups when you have a hard enough time scheduling your day already. But if you're looking to shed a couple pounds here and there— without lifting a finger— this two-part video will help you out with some Jedi mind tricks!

Zabernism. What exactly is it? It's a term that originated in 1912, during an incident involving an overzealous soldier who killed a cobbler for smiling at him is Saverne, a small town in Alsace in north-eastern France. The said event ultimately triggered an intervention from the army who took over the power from local authorities.

Air conditioning systems are cold and wet and make great breeding grounds for bacteria and mold, and adding a nasty odor to the air coming out of the vents.

In order to make a retro wireless handset, you will need the following: vintage handset, a momentary switch, a resister, a Blue tooth headset, wires, a drill, and a blue LED and mount.

This five-part cookie decorating tutorial is a godsend for someone who's looking for an all-inclusive guide to decorating cookies. While you'll find many individual videos out there showing you how to put on buttercream icing or corn syrup icing, you usually won't find one depicting both.

HTPC. It stands for Home Theater PC. Some refer to it as simply a Media Center. But no matter what you call it, you're going to learn how to build one today. Why would you want to do that? Because one of the main advantages of creating your own home theater system is that you are control, not only of the cost, but the features and functions, as well.

Kipkay is at it again with his pranks. In this video, he shares four fun and easy pranks that anyone can do to drive their friends (or victims) crazy! Their all very simple. They include a cell phone prank, a floss prank, and more!