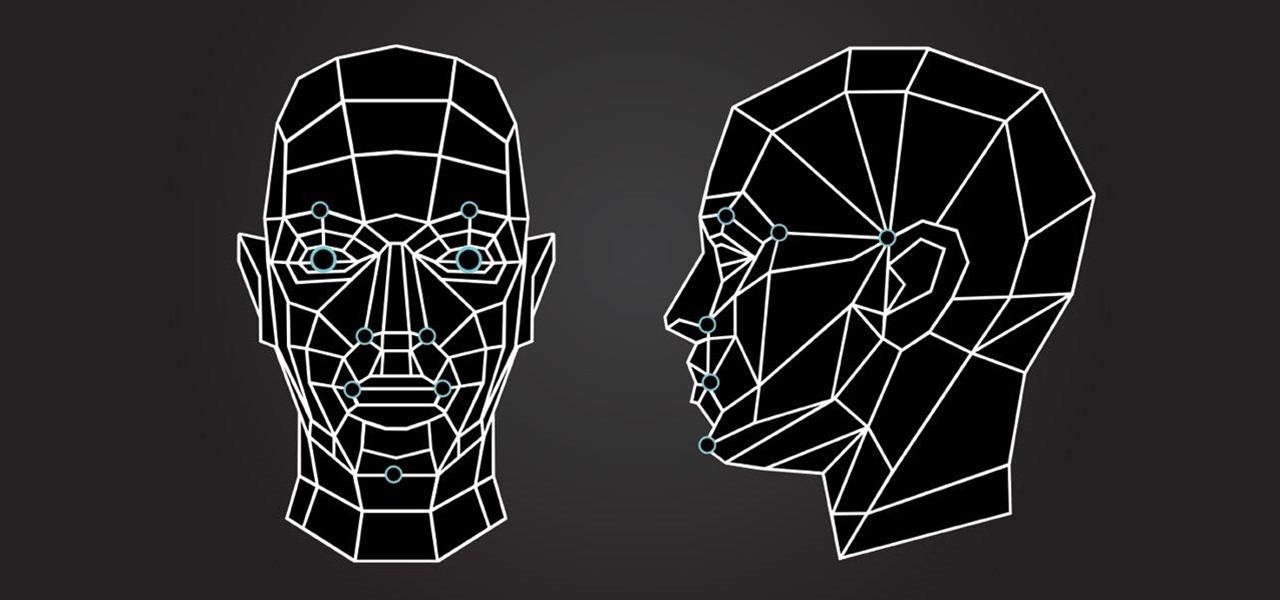
Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

If you're a fan of sleek, powerful computers and highly-customizable smartphones, then you probably own a Mac and an Android device. But the downside to this glorious hardware pairing is that it can be hard to get the software on the two devices to play nice together.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

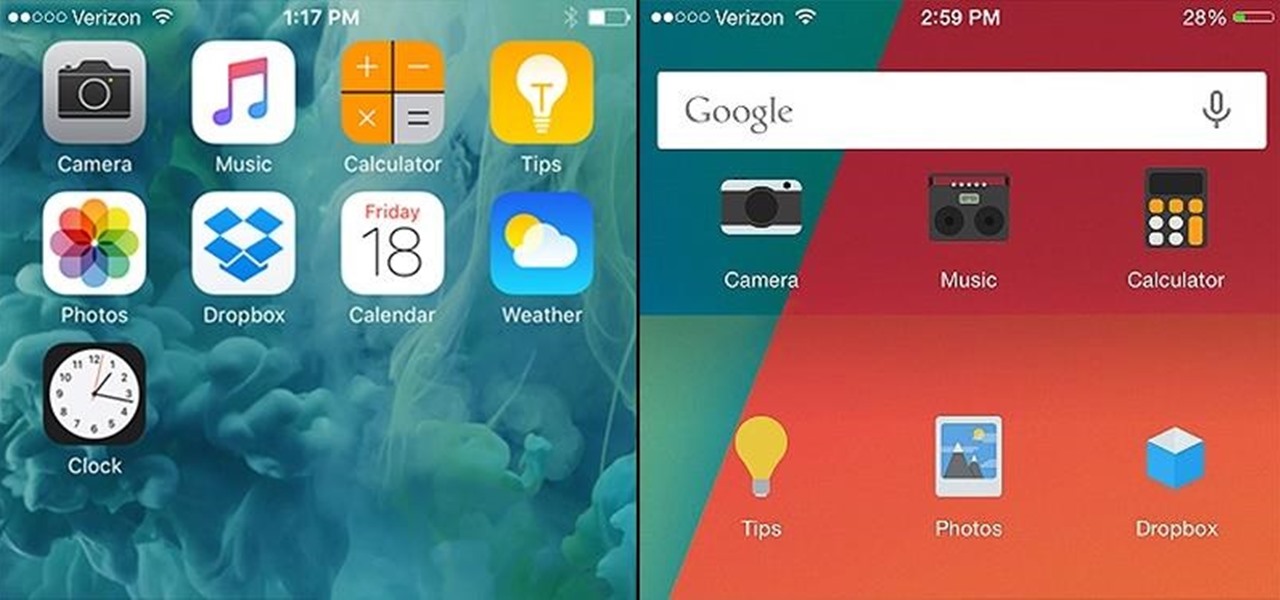
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aesthetics of an Android.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Google just announced a new and improved Chromecast at an event in San Francisco this morning, and debuted a new "Chromecast Audio" for streaming music directly to any speaker. I'm sure you rushed off to the Google Store to buy one of these promising and powerful devices, but while you wait on the new one to come in the mail, your old Chromecast just got a lot more functional by way of a simple app update.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

In my family, if a food could be made instead of bought, it was made. It wasn't until I went to college and started eating dorm food that I tasted the store-bought versions of many kitchen staples. I quickly learned that there is an enormous quality difference between homemade dressing and the kind that comes in a bottle at the supermarket.

Eating flowers is a time-honored culinary tradition, from nibbling on nasturtiums to grazing on candied violets. And why not? They look beautiful and lend a unique floral flavors to salads, desserts, and anything in between.

Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the lavender lemonade.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top.

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Welcome back, my nascent hackers!

Welcome back, my greenhorn hackers!

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Admit it: when nothing's at stake other than your boss's disapproval, you don't exactly feel the urge to get working. Finding the motivation to take on a task, whether at work or home, can be a constant struggle. Though working through your laziness might seem like the best course of action, a meaner method can make more of an impact on your productivity.

Apple's iPhone 6 packs a powerful 4.7-inch Retina HD display with 1334-by-750 resolution, and it's so incredible in person that it almost looks fake. However, as awesome at this display is, it can always be better.

The "Smart Keyboard" on the LG G3 has received a lot of praise for its ability to adequately analyze user keystrokes, provide adjustable sizes, and customize key placements, among other things. These features, combined with predictive text, swipe gestures, and autocorrect make the Smart Keyboard one of the most powerful typing tools available for Android. Now, it's easy to get it installed on your Samsung Galaxy Note 3.

In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?