Google Now is a wonderfully powerful service—with its predictive cards and voice search, it serves as a great starting point for any searches you need done. In fact, Samsung liked it so much that they decided to build the "Okay, Google" hotword detection right into the Galaxy S5's stock launcher.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Smartphone manufacturers strive to craft the most powerful cameras they can, but are limited to using hardware that will conform to small form factors. In most cases, the cameras end up fairly underwhelming, unless we're talking about the 41-megapixel shooter in the Nokia Lumia.

If you've ever used IFTTT, you know how well it can automate your online world. The premise is simple—If This, Then That—but the results are powerful. From automatically printing images based on hashtags to getting around Twitter bans, the service is quite useful with a wealth of possibilities.

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most powerful cameras on the market, with an impressive 20.7 megapixels. Since the device is only available for T-Mobile here in the States, unless you currently have that carrier, the chances of you getting your hands on Sony...

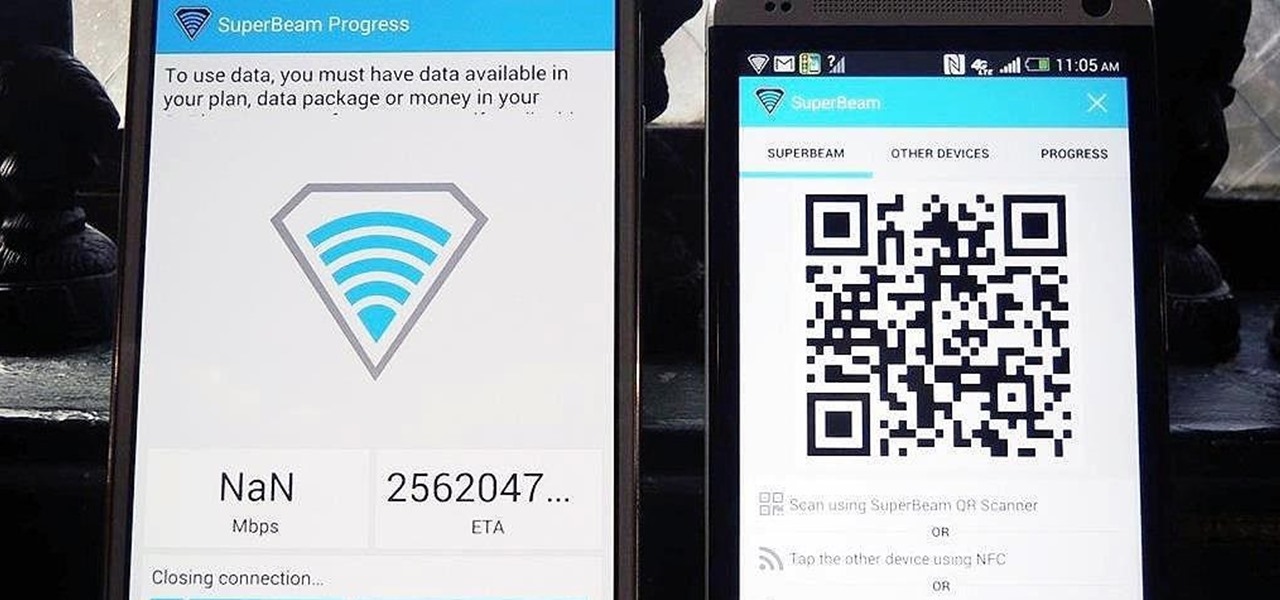
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

You've got a brand new Nexus 7 tablet for Christmas, and you're extremely eager to start using it. There are many things you can do with it, like shake for new wallpapers, get rounded screen corners, and make it help you fall asleep at night. But, before you get into softModding your Nexus 7, you should know the basics, and if you've come over from a Kindle, turning your new Android tablet into a powerful eReader is a must.

Note to admins: If there's anything wrong with the links or the article itself (legality), let me know.

If I were a math major, I'd probably be rolling in dough somewhere in Silicon Valley right now, but since multiplying numbers and figuring out tangents gives me panic attacks, I went the English route... pays much better.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

During last week's D11 event, Sundar Pichai, head of Google's Android division, announced that a Google Edition of the HTC One would be available for sale on June 26th in the Google Play store.

The battery in the Samsung Galaxy S4 may pack 500 more milliamps per hour than the old S3 battery, but that doesn't necessarily mean more battery life. High-powered devices need lots of juice, and the S4 is definitely more powerful than its predecessor. The new battery can handle a third more in standby days, and over twice as much in talk time hours. But, when you live on your phone all day long, that means nothing. You're battery is still going to have a hard time keeping up with you.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

Screenshots are great, but sometimes they don't tell the whole story. You can show off that new app you got or that awesome new live wallpaper, but a screenshot isn't going to get the point across. What exactly am I trying to show you in the screenshot above? You probably have no idea, and that's the point. You can't see the action I'm trying to demonstrate, but in a video you can.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

The Braun immersion blender is cheap yet powerful. It is strong enough to crush ice, frozen fruit, nuts, vegetables, etc. and is typically used to make smoothies. Watch this how to video to learn how to make an ice cream and banana smoothie with a hand held blender.

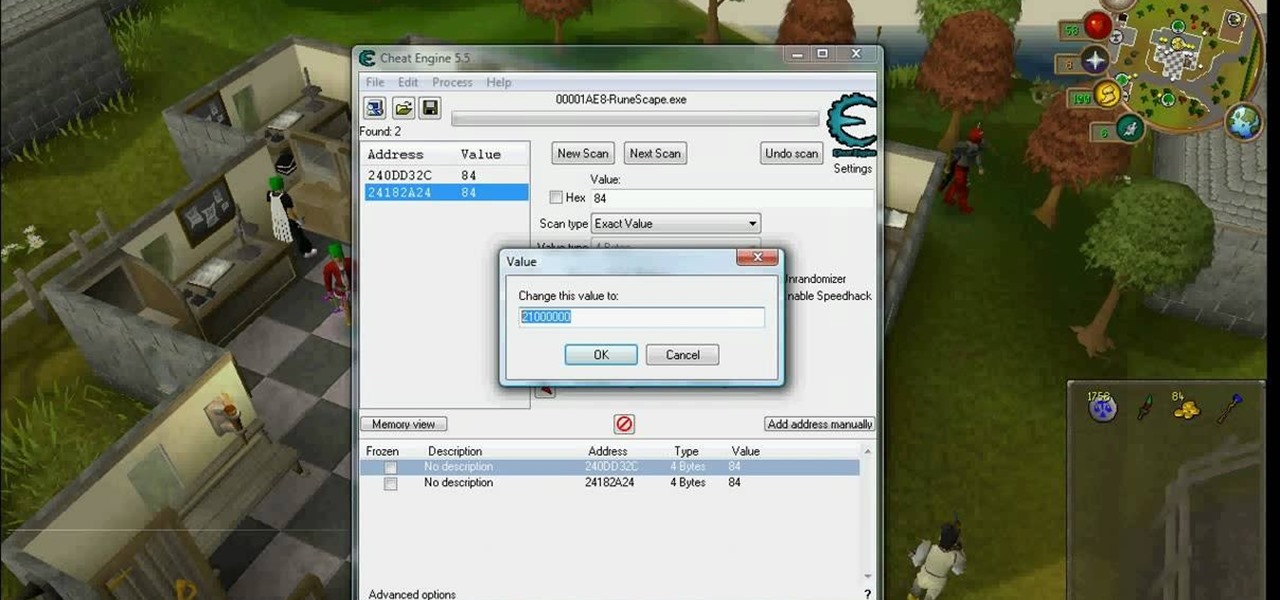
RuneScape hacks, cheats, glitches. How to hack the flash game RuneScape. Watch this video tutorial to learn how to hack RuneScape with Cheat Engine (08/31/09).

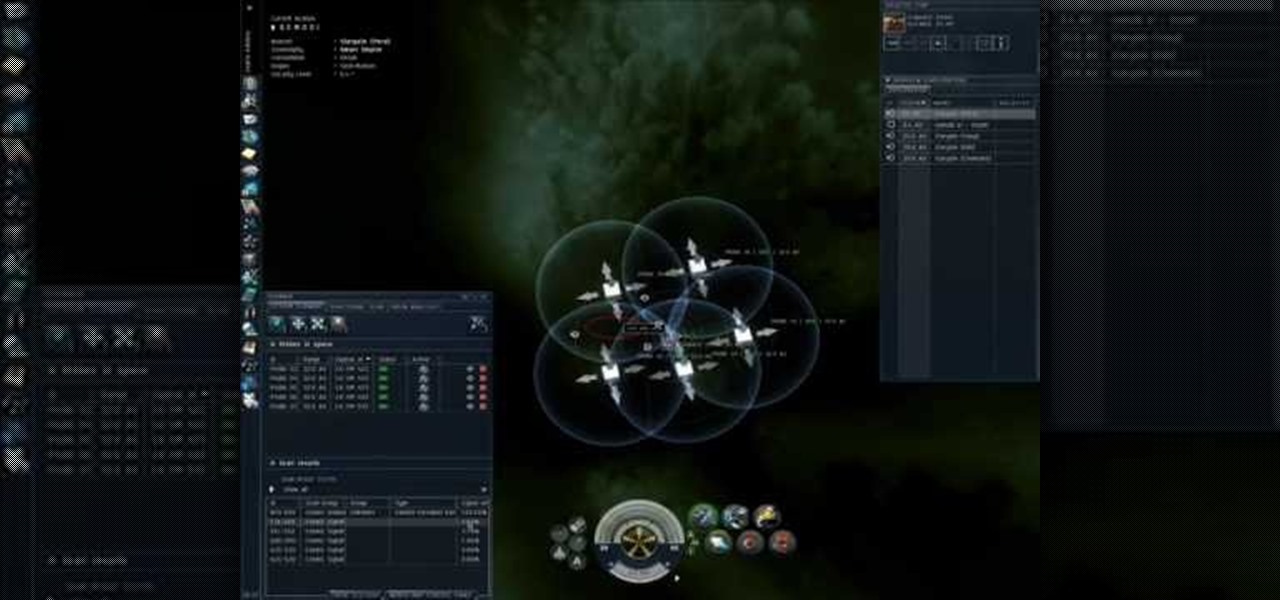
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

The pandemic has forced a number of public-facing businesses to either temporarily close or permanently cease operations, with one of the biggest victims of this trend being the movie theater business.

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.