Whether it's an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, know that these devices are the most powerful smartphones Apple has ever made. Still, bugs happen, and you might find yourself with an app that isn't performing quite as it should. When that happens, it's best to force-close (or force-quit) the problematic app instead of waiting for it to fix itself, which may never happen.

Apple just released iOS 14.1 for iPhone today, Tuesday, Oct. 20. This update first hit iPhones one week ago, but not for long — Apple pulled the release almost immediately, later seeding it to iOS developers only as a GM (golden master) release.

Apple just released the third public beta for iOS 14.2 today, Wednesday, Oct. 14. This update includes new glyphs for the HomePod mini and Beats Flex, support for HomePod's upcoming new "Intercom" feature, new core media features, and SwiftUI fixes.

Apple released iOS 14.2 developer beta 3 for iPhone on Tuesday, Oct. 13. The update adds new glyphs for HomePod mini and Beats Flex, support for HomePod's upcoming "Intercom" feature, new Core Media features for developers, as well as resolved SwiftUI issues.

Apple erroneously released iOS 14.1 for iPhone as a stable OTA update on Tuesday, Oct. 13, just after the special event where it announced the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max. It's not surprising given Apple's track record lately.
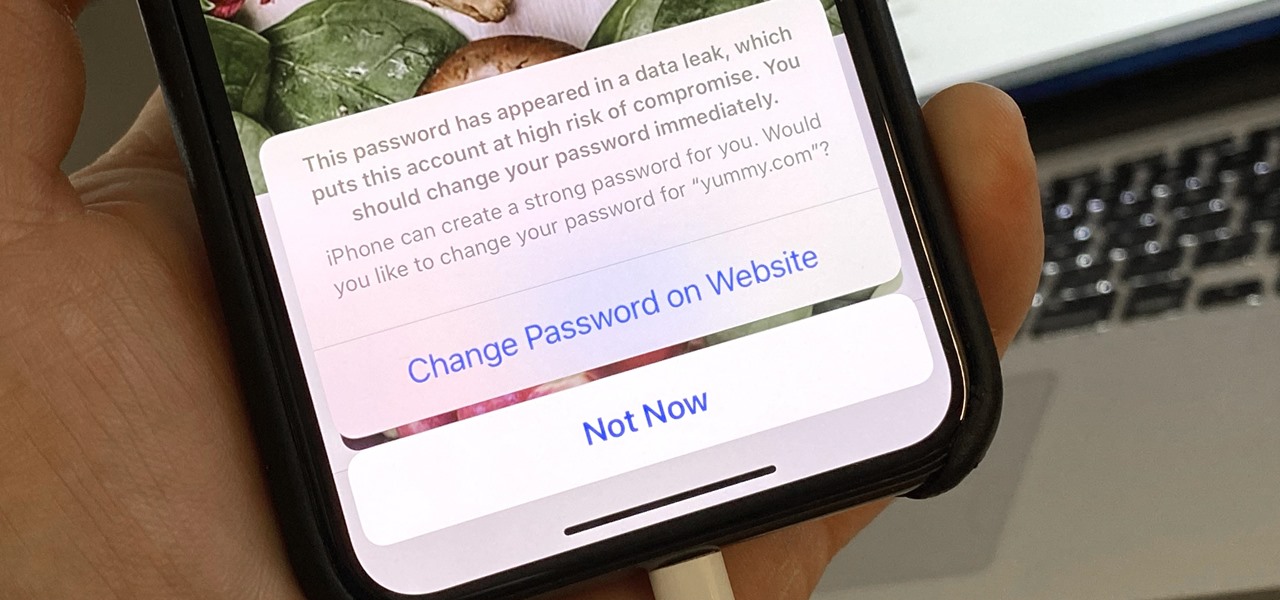
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

Apple released the first beta for iOS 14.2 to iPhone developers on Thursday, Sept. 17. A significant new feature that iOS 14.2 brings to the table is a new Control Center tile for Shazam music recognition. A simple tap of the tile will launch the operating system's built-in Shazam capabilities, scanning for music playing in the immediate area.

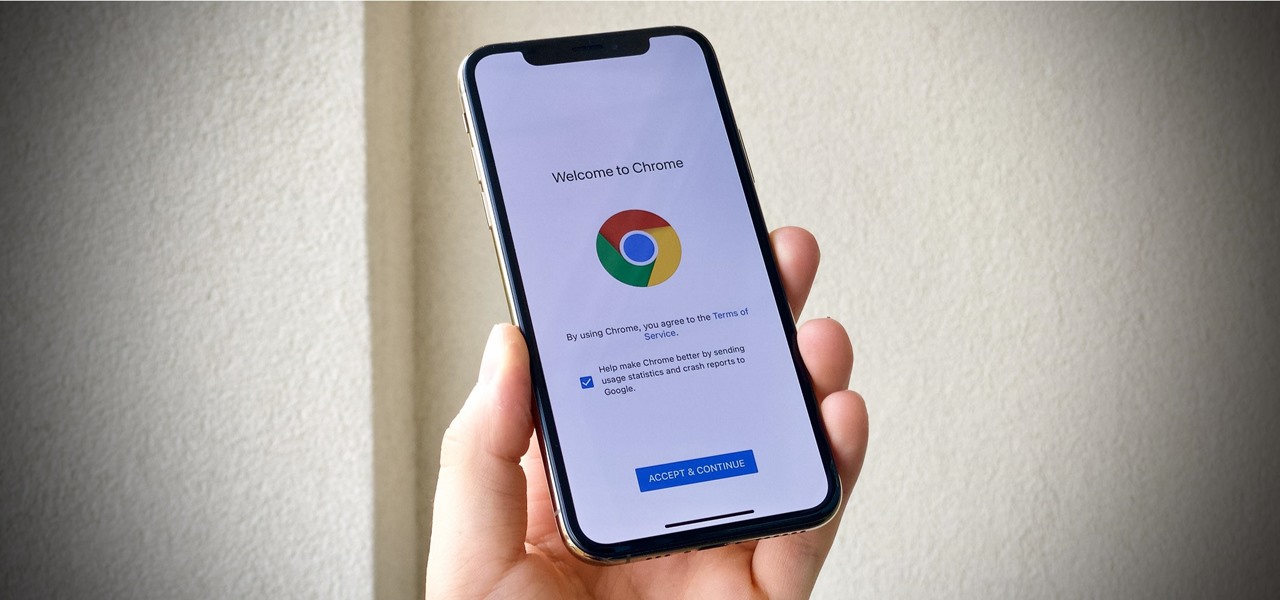
For the longest time, we were simply stuck with Safari on the iPhone. Sure, you could install a third-party browser, but Safari was always the default, so tapping on links would always open Apple's app. Times have changed, however, and now you can set third-party browsers like Chrome, Firefox, and Edge as your iPhone's default choice.

One of the most significant changes in iOS 14 is something we've wanted for a very long time, and it will change the way you use your iPhone. Since the very first iPhone OS 1 (yes, before it was even "iOS"), we've been stuck with Apple Mail as the default emailing app. That all changes now.

Social media apps like Instagram, Snapchat, and TikTok have plenty of editing tools that go beyond the basics, but there are still a lot of things they can't do. So if you want to apply interesting, unique effects to your photos and videos for social media, you'll need to add some other apps to your iPhone's arsenal of tools.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

What if, back in 2013, Google Glass had launched not as a Star Trek Borg-like eyepiece, but as a pair of seemingly normal shades, with the augmented reality lens and camera hidden within the frame?

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.