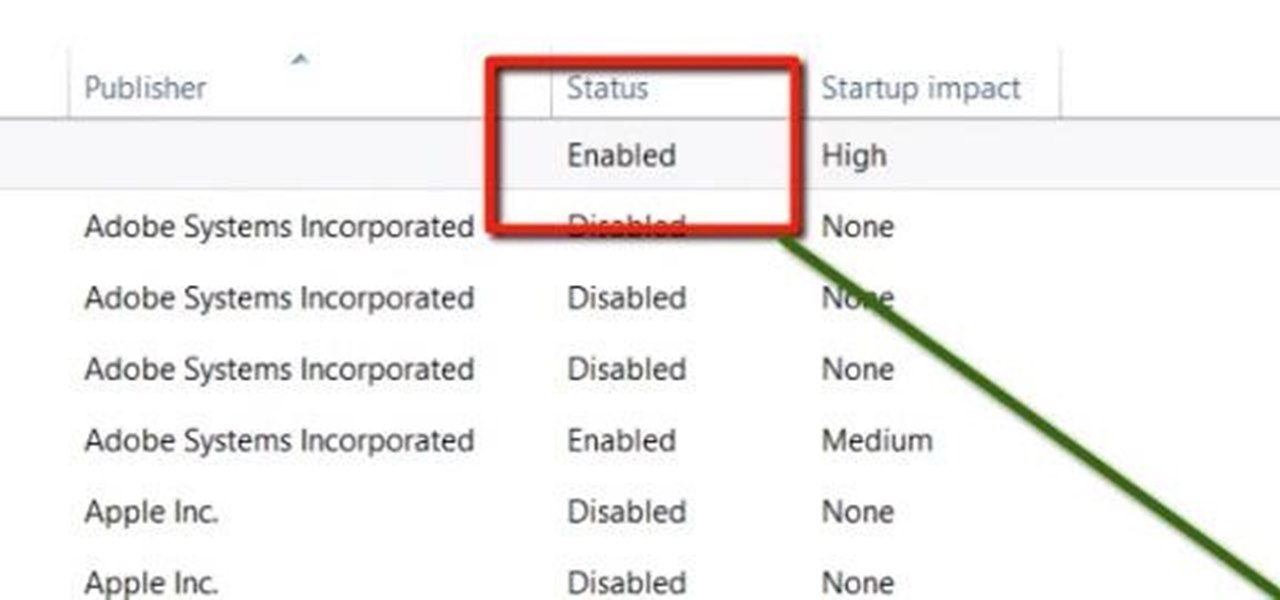
This Windows 8 tutorial will show you how to enable or disable applications from starting up when you boot up your computer. It is sometimes important to disable applications to ensure a smooth start, especially if you computer doesn't have very powerful hardware.
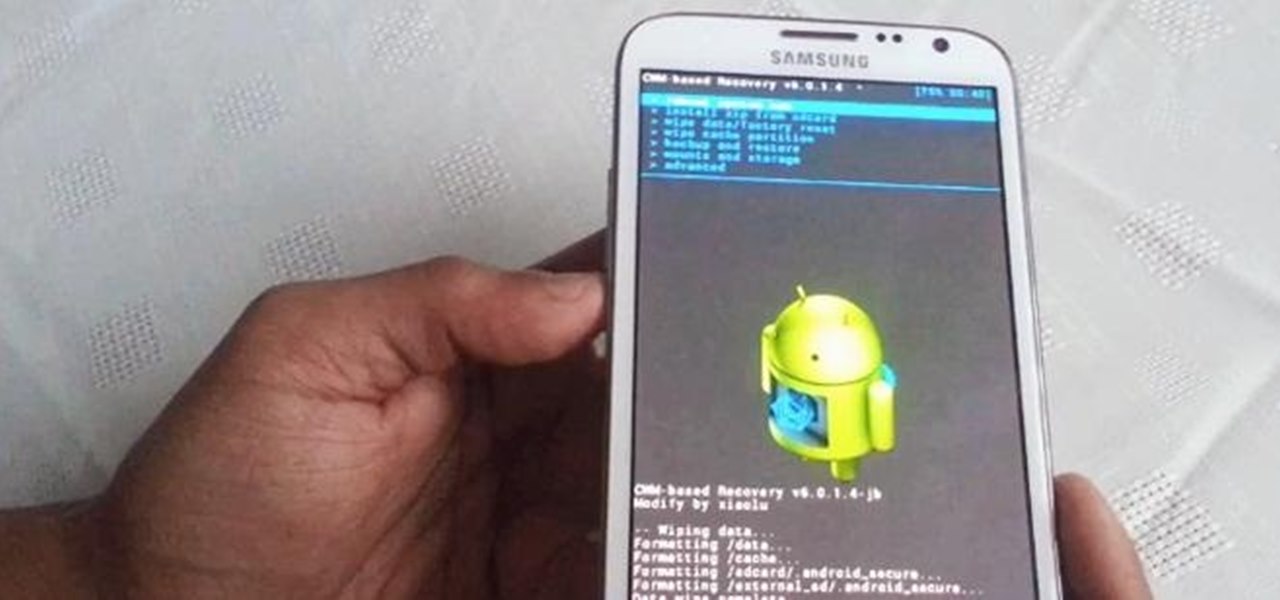
The new Samsung Galaxy Note II is a powerful and sleek device that begs for some customization, and there's no better way to customize your Android device than installing a custom ROM of your choice. One of your choices is the Omega ROM, which is just one of many that you can download and flash to your Galaxy Note 2. Before you begin, you'll need to root your Galaxy Note 2 and install Odin and CWM Recovery. You can get a toolkit of everything you need over at XDA Developers. Then follow the v...

Sputnik was the very first man-made object to be sent into space. Though it was a truly epic accomplishment, all this Soviet sky surfer actually did was transmit a constant beeping noise back to the surface.

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.
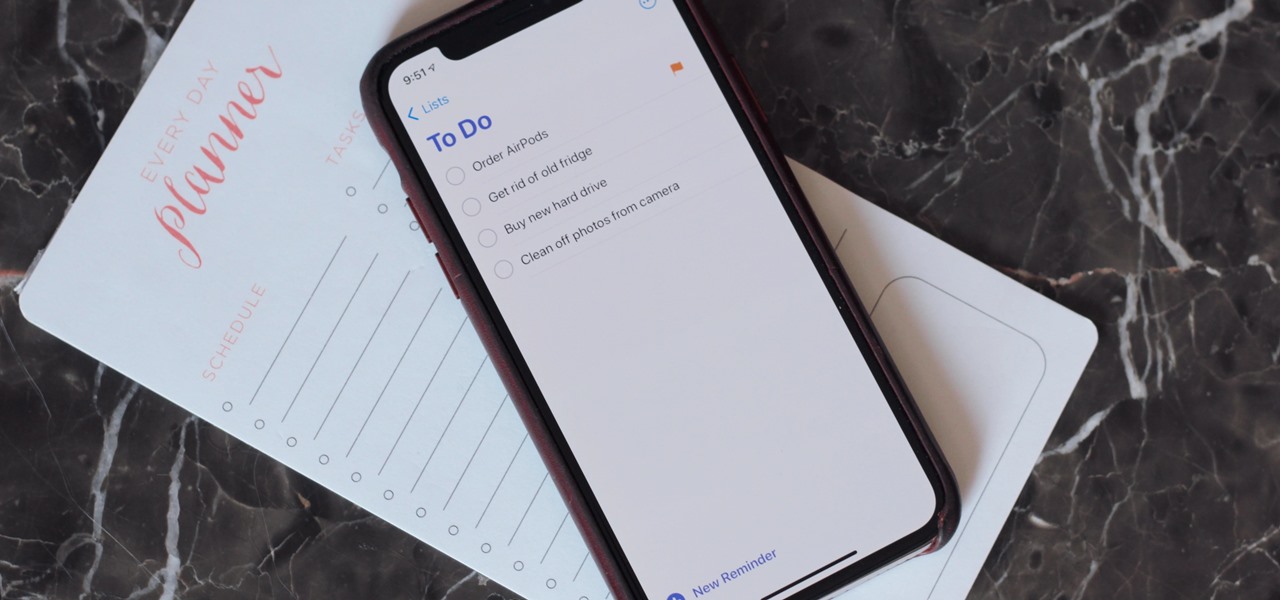
The iPhone's built-in Reminders app got an overhaul last year with iOS 13, giving us a more modern design and plenty of new features, and iOS 14 doesn't mess with a good thing. Instead, iOS 14 brings lots of small tweaks all over the app to smooth out the experience and make Reminders more powerful and more customizable than ever.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

You use your iPhone's Reminders app to keep track of everything from grocery lists to the day's most important tasks. Over recent iOS updates, Apple has added tools to Reminders to make it even more powerful, like assigning tasks to other people and setting location-based reminders. Now there's another great update, and it gives you the ability to sort your lists.

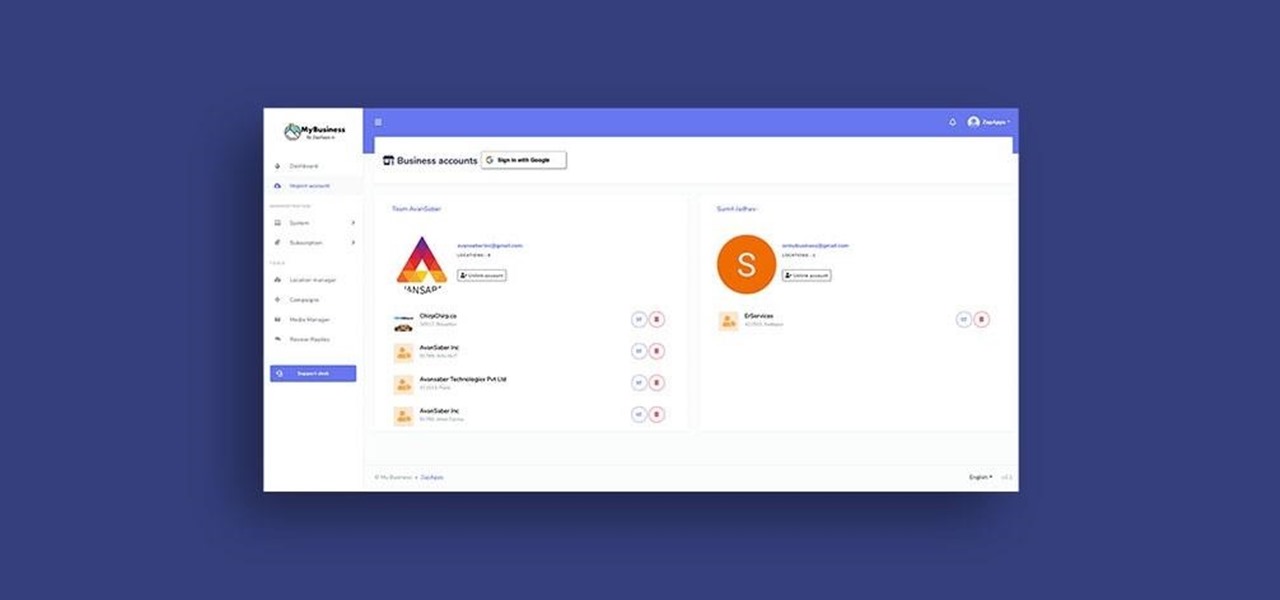
Google My Business lets you connect with customers across Google Search and Maps through a unique business profile. The web app allows you to connect and chat with customers in real-time and provides rich analytics to help you manage and grow your company.

We all know how hard it can be to stay productive, especially when working from home. There are many distractions throughout our day. Organizing your workflow is necessary for getting anything done.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Whatever industry you're in, there's a decent chance you've had to work with Excel — that number-crunching powerhouse that drives the accounting departments of countless corporations across the globe.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, we're here to guide you to the best ways to take part in all the streaming fun when you're not glued to your mobile devices.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

The Sony Xperia XZ Premium brought 4K HDR to a Sony flagship along with some competitive internals, while the Xz1 brought some powerful specs in a more midrange, traditional form factor. Now, Sony has unveiled the XZ2, which sees not only an upgrade in performance, but a complete design overhaul as well.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

Welcome back, my greenhorn hackers!

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Siri has long relied on basic sources like Google and Wikipedia for answers, but with iOS 18.2 and iPadOS 18.2, Apple is taking its virtual assistant to a new level by integrating ChatGPT. Now, you can use Siri to generate text and images with ChatGPT — and that's not all. ChatGPT is deeply integrated into Apple Intelligence and goes beyond just Siri.

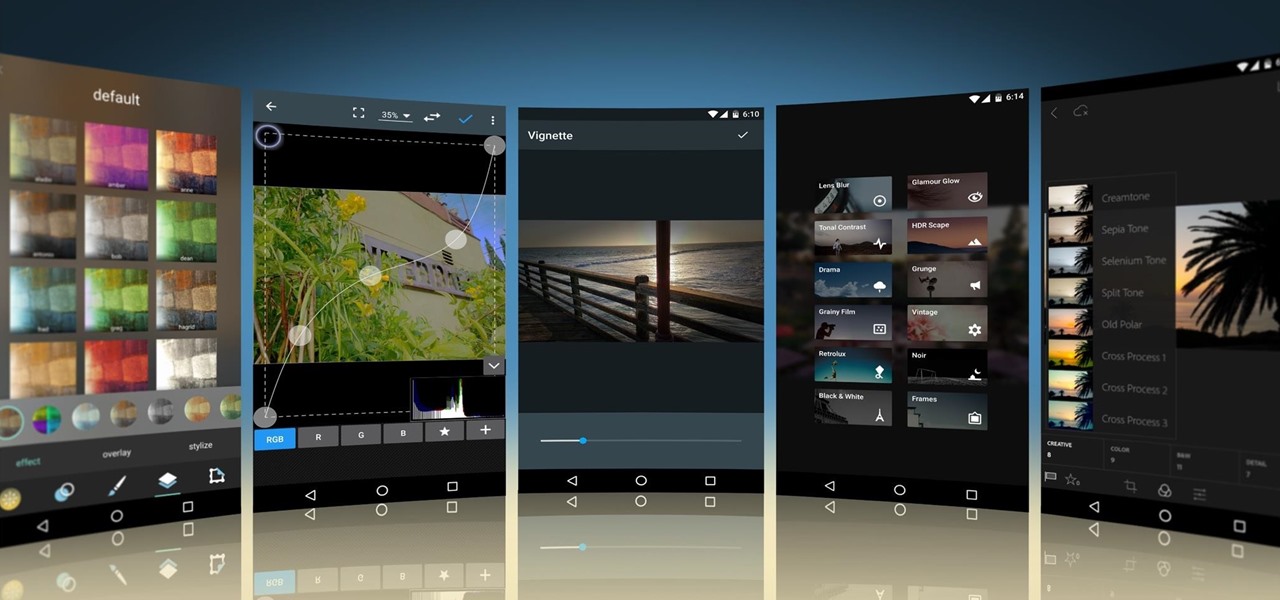
Social media apps like Instagram, Snapchat, and TikTok have plenty of editing tools that go beyond the basics, but there are still a lot of things they can't do. So if you want to apply interesting, unique effects to your photos and videos for social media, you'll need to add some other apps to your iPhone's arsenal of tools.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

Maintaining a clean living space is important, but it shouldn't have to be a hassle. The KAPSULE™ UV Sanitizing Wand 2.0 is designed to keep surfaces pathogen-free. This powerful wand emits 254nm UV-C light and makes quick work of pathogens. In a laboratory test, KAPSULE even eliminated more than 99% of E-coli!