MrfixitRick demonstrates the Shake Flashlight Shaker, as it generates electric power out of faucet water pressure. A Tesla CD Turbine is used to convert the kinetic energy of water into rotation. Then, a connecting rod and magnets charges the built-in battery of the shake flashlight.

This video series shows you all the steps involved in properly presenting your models inside SketchUp. The videos correspond to Chapter 10 of the book Google SketchUp for Dummies. PART 1 discusses standing in the right spot and how to use the position camera tool. PART 2 explains how to walk around your model using the walk tool. PART 3 shows you how to stop and look around. PART 4 shows you how to set your field of view (how much you can see). PART 5 talks about creating actual scenes. PART ...

Next time you make dinner in your crockpot, be sure to follow these crockpot safety tips. The temperature should be at least 140 degrees. Food needs to cook at this temperature or higher to prevent the growth of bacteria. Do not put frozen foods into a crockpot. All foods should be defrosted before cooking, so the temperature can reach 140 degrees as quickly as possible. Do not lift the lid to stir, especially if you are cooking on the lowest setting. Each time you lift the lid, heat escapes ...

After you've learned the basics about shapes, transformations, and times, it's time to move onto learning the color scheme of things in the C++ programming language. You can't have a beautiful 3D game or program with out vibrant colors! This video lesson will show you how to add colors to 3D scenes with OpenGL for C++, so you can start making your own 3D programs.

Long term power outages can be an inconvenience. It means that you no longer can heat or cool things. This how to video talks about how to protect your home from a long term power outage, or how to protect your valuables from power loss with a generator.

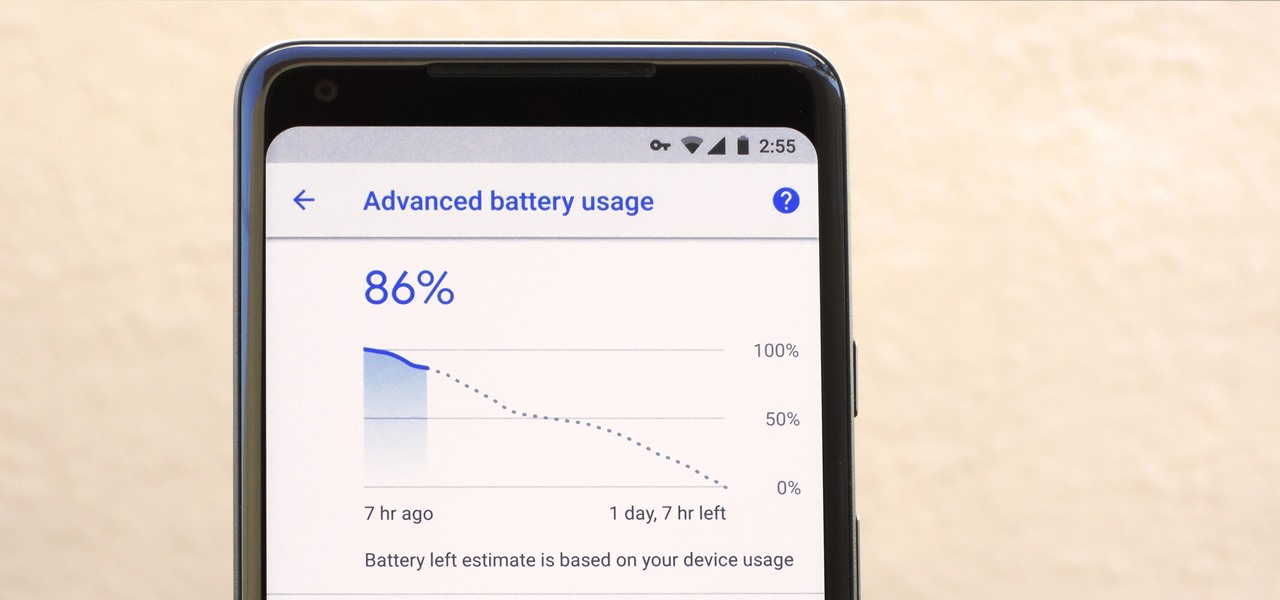
Android 11 is available as a simple beta install for Pixel devices right now. Just visit Google's beta signup page, make sure you're signed in with the same account used on your Pixel, then opt into the program. You'll get an OTA update that will put you on Android 11 in no time. But is it ready to be a daily driver?

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's because Apple introduced a new feature in iOS 13 that slows down charging — but for a good reason.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

We've seen all the Magic Leap One glamour shots, and we've even shown you a bit of what it looks like to view augmented reality on the device. But there's something else us super geeks appreciate more than anyone else: the grand unboxing!

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

Everything that has a beginning has an end. This week marked the end of the long wait for the reveal of Magic Leap's first product and the beginning of the wait for more substantive details. Likewise, Google Tango will meet its end in March 2018, when ARCore will officially begin its public rollout.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

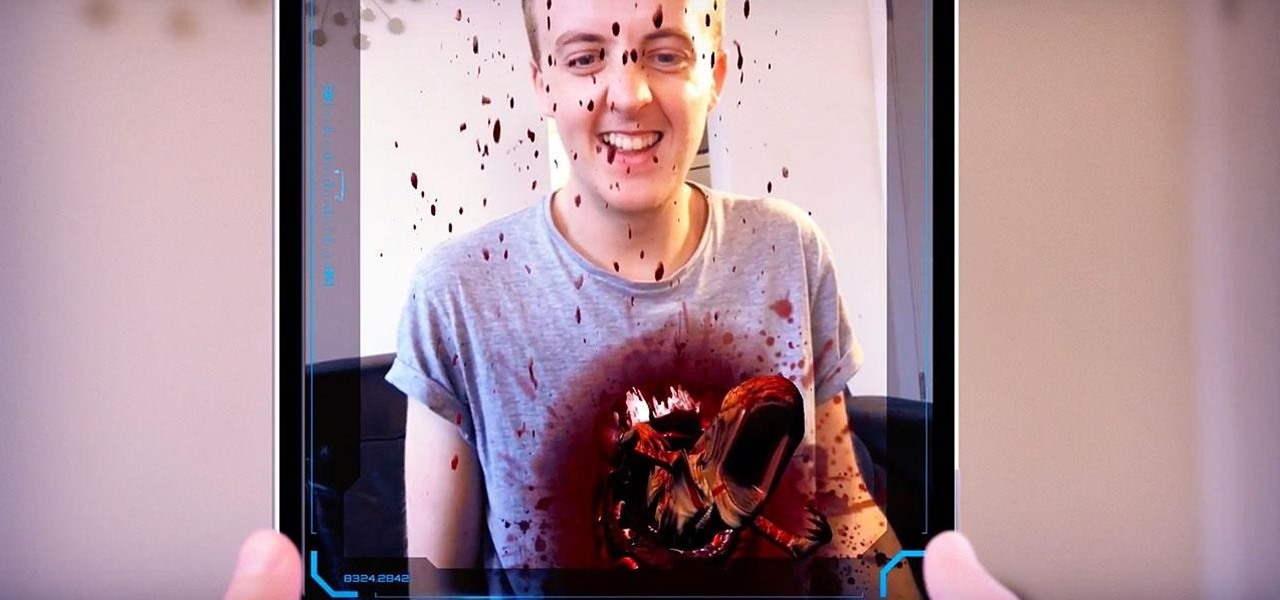
The latest installment in the Alien movie franchise, Alien: Covenant, came out many months ago, and the fan day dedicated to the franchise, Alien Day, April 26, is long past. But for many Alien fans, Alien Day is every day. For those loyal members of the xenomorph-worshipping tribe, a new augmented reality-powered book has arrived to serve their science fiction needs until the next film is released.

The fact that the iPhone X, XS, XS Max, and XR don't have Home buttons means that you'll need to learn a few new gestures. There's the home gesture, the multitasking gesture, and even a new way to access Apple Pay, among others. But one less-common action that has issues due to the lack of a Home button is taking a screenshot.

Elon Musk has repeatedly said Tesla models in production today have the requisite hardware to offer "full self-driving" capabilities. But for features more advanced than Level 3, Tesla will, in fact, have to revamp Autopilot's hardware to handle the extra computing load.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Three years ago, with VR enthusiasts prepared to throw their money at Oculus to get their hands on the yet-to-be-release Rift headset, Google surprised the audience for Google I/O with Google Cardboard, a seemingly late April Fool's joke that actually jump-started virtual reality.

The Gorillaz have launched a new app in promotion for their new album Humanz that allows you to "[s]tep inside the hallowed halls of the Gorillaz house" through the power of augmented reality.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

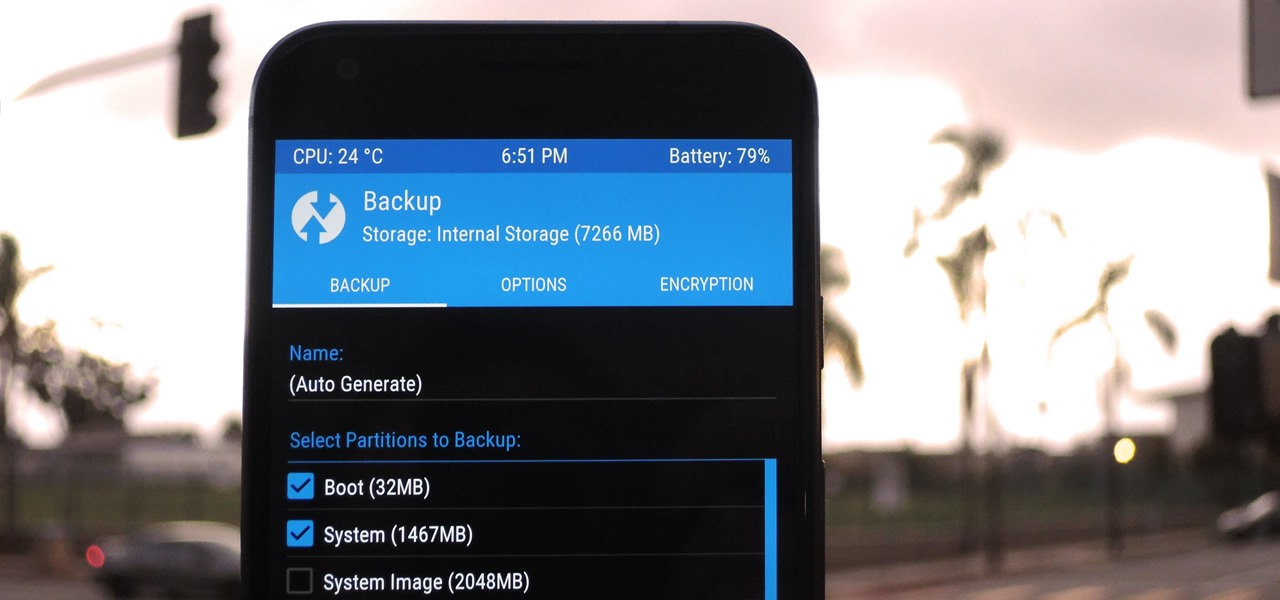
A custom recovery is a very powerful tool. You can flash ZIPs that modify your Android device in ways that not even root can accomplish, and of course you can use it to install custom ROMs. But when you're applying all of these cool mods, there's always a chance that something could go wrong, and you might even end up bricking your device.

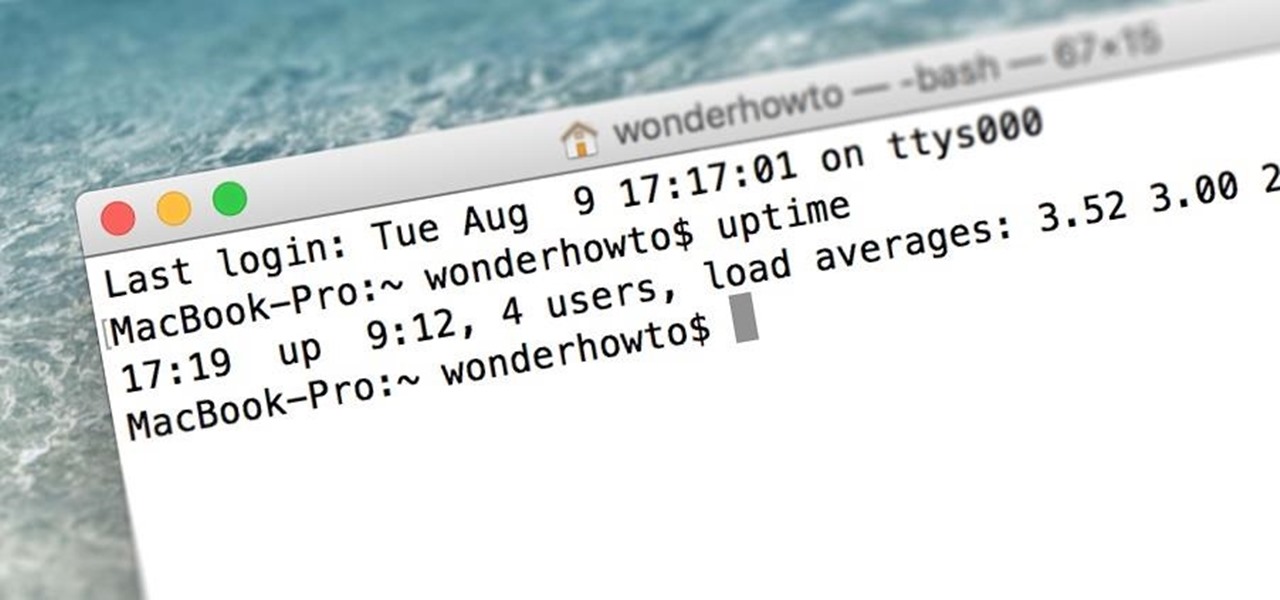
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

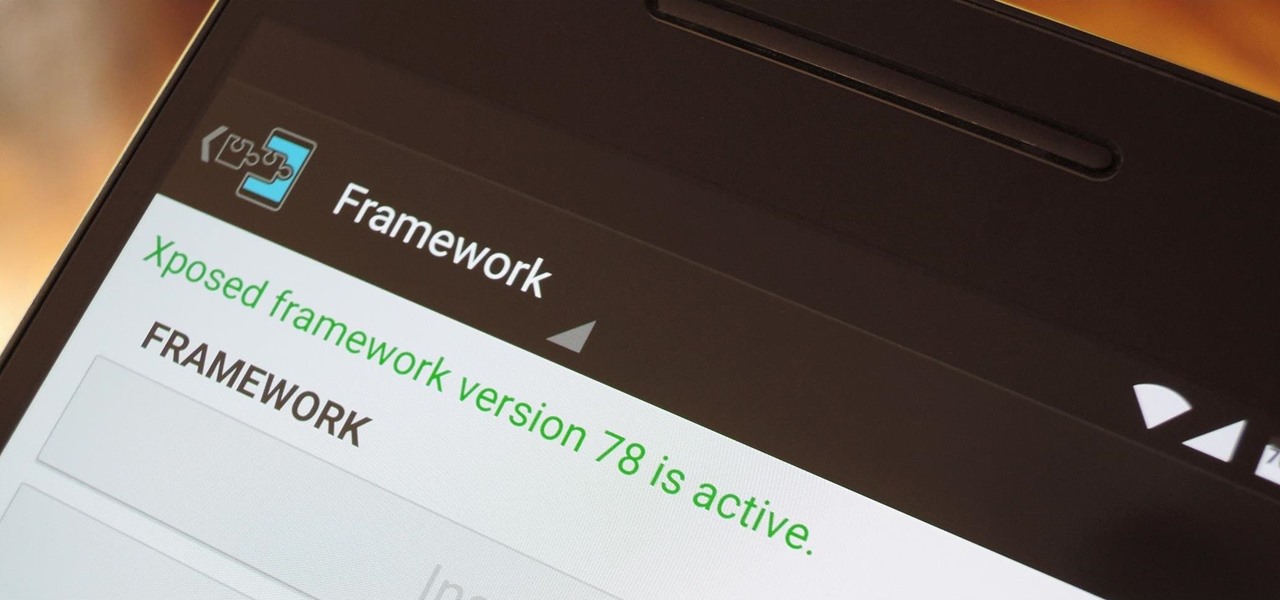
When someone asks me why they should root their phone, one of the top reasons I always give is that it enables you to install the Xposed Framework. Created by developer Rovo89, Xposed basically hooks into the Android system, then allows users to simply install mini-apps called modules that can change almost anything in a device's interface or other installed apps.

There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the stock firmware can even resurrect a soft-bricked phone.

If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

CyanogenMod continues to be the most popular custom ROM for a good reason. Their team of developers always stay on top of the latest trends, and ensure that their software is packed with nice tweaks and awesome features. One such feature is an audio equalizer that allows you to fine-tune your device's various sound outputs. It's got a great interface, and works with any app that calls on Android's default audio mixer.

Sony has a gorgeous line of smartphones using the moniker "Xperia," and the latest and greatest model is the Z3. The firmware for the Xperia Z3 was just updated to Android Lollipop, and many system apps of course got tweaked and refreshed with this latest version.

With the Nexus 6, you get a very clean software experience with minimal bloat. While this is generally the main selling point for most Nexus fans, it can be a bit of a detraction for some.

If you've ever flashed a custom ROM on any of your devices, one of your main motivations for doing so was likely the set of neat tweaks and extra options that come with something like CyanogenMod. Another deciding factor was probably the fact that most custom ROMs offer a much cleaner interface than manufacturer skins.

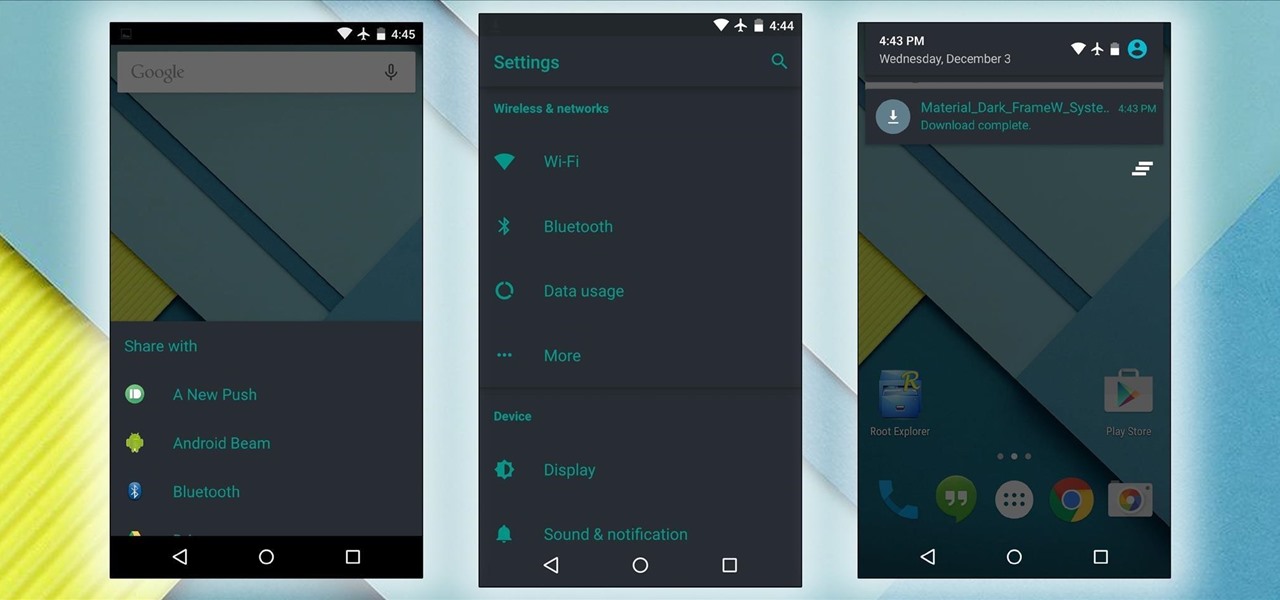
Android Lollipop's new Material Design interface does its best to strike a delicate balance between intuitiveness, usability, and aesthetics. For some folks, though, the use of a lighter color palette throughout the interface disrupts this balance.