Technology is awesome. You can use your iPad to record music or even turn your tunes into a solar system, but sometimes being plugged in all of the time can leave you nostalgic for simpler times. This new concept by Joelle Aeschlimann brings together the best of both worlds by turning your iPad into an old-fashioned, hand-cranked music box. The artist created three different music boxes, each one with its own unique song and visualization. The music boxes were made using wooden cylinders with...
If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Hello! I want to share a few hints about staying literally cool when the temperature of the air outside rises incredibly. So, if you're in a very hot area, please continue reading!

Performance art is conceptual, usually visual art that involves bringing a concept to an audience. Learn to be a performance artist in this free conceptual art video.

This how to video clears up why there is a tone and a half in a harmonic minor scale, and goes into detail about leading tones, and what harmonic and melodic scales are used for. These are very important concepts in music theory and piano playing. Watch this how to video and you'll be playing piano in no time.

This how to video covers playing arpeggios, dominate 7ths and diminished 7th's on the piano. These concepts are essential for every pianist to learn. Watch this video and you will be playing arpeggiated 7th chords in no time.

This simple band saw jewelry box is easy to make. Measurements can be quite varied, as it is the concept which is important.

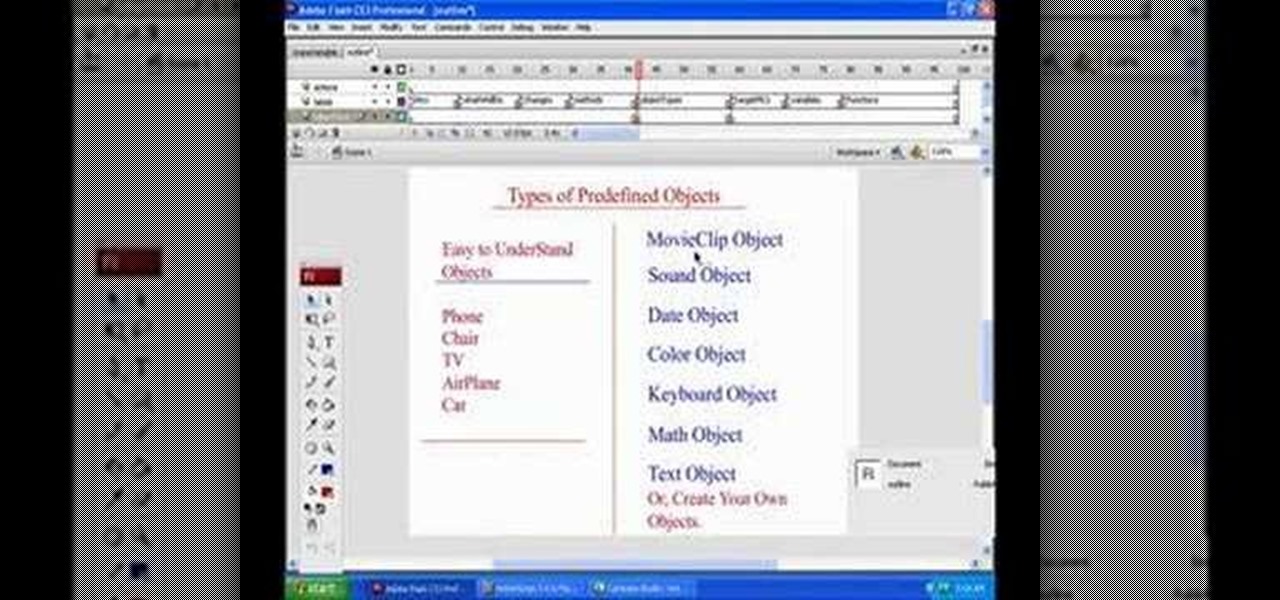
An Object within Flash CS3 is a thing - a thing that has attributes and can perform actions. That thing may be a ball bouncing in your animation or a dog barking. In this short tutorial, author Bill Dallas Lewis presents the concept of Objects within ActionScript 3 and Flash CS3 as well as how to interact with objects within your presentation.

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my rookie hackers!

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

Bhakti yoga focuses on the concept of love and devotion. Learn how to practice Bhakti yoga in this yoga video clip. To practice Bhakti yoga you should shatter your ego, surrender yourself to object of devotion, and pray & meditate. With this how to video you will be able to practice the principles of Bhakti yoga.

This how to video covers time signatures, beats, and using the metronome when playing piano or keyboard. These concepts are essential to understand if you want to read music and play piano with accurate rhythm. Watch this musis theory tutorial and you will understand musical time and rhythm.

A ledger line or leger line is musical notation to inscribe notes outside the lines and spaces of the regular musical staffs. This music theory how to video teaches you the concept of ledger lines in written music. Learn how to read and write music with this tutorial.

Two tones in unison are considered to be the same pitch, but are still perceivable as coming from separate sources. Understand the concepts of unison and with what instruments you can play them with this two part how to video.

This tutorial teaches and easy technique for learning notes on the guitar. This concept makes reading guitar music easier and faster to learn. Follow this how to video and you will be jamming on the guitar in no time.

Learn how to use a tape gun to tape a cardboard box. A simple concept that so few people understand the premise behind.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

If you're interested in nabbing superhero memory strength, the secret behind training your brain is not necessarily what you might expect. Your standard G-rated brain strengthening exercises range from crossword puzzles to Sudoku to calculating fairly simple math problems to improve short term memory, but the real clincher used by some of the pros is essentially... porn. Yep, you read right.

Tents are a practical and easy shelter to use on any camping trip. Learn how to set up a tent in this free camping video series from an Eagle Scout.

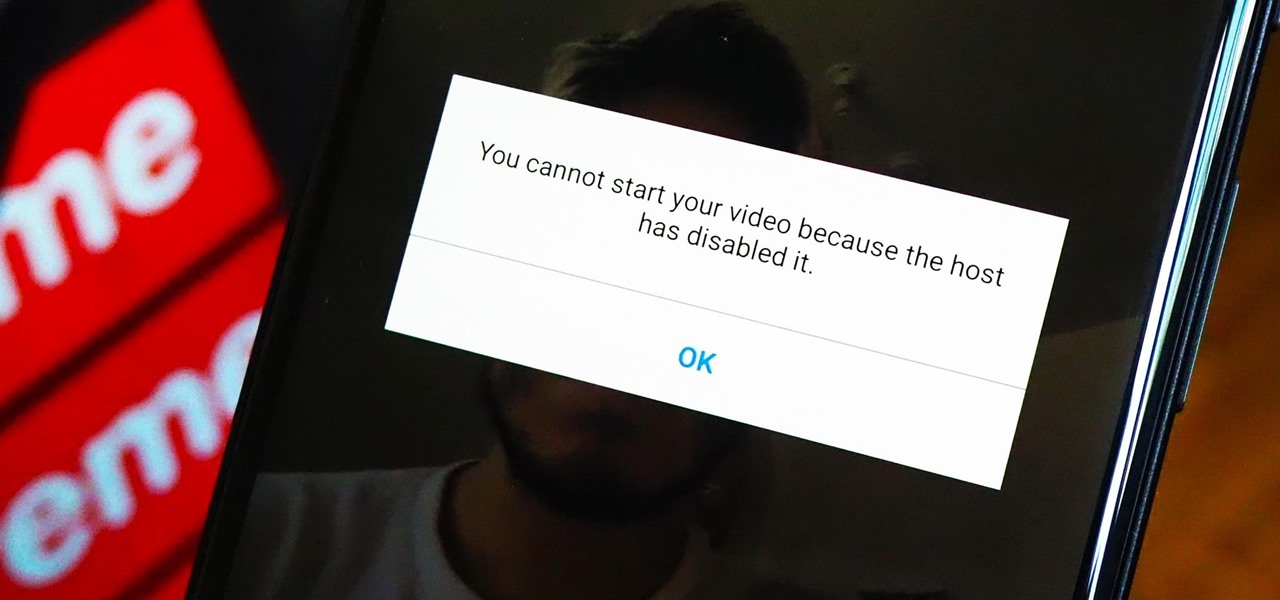
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

Legendary drum-and-bass artist Squarepusher, the Warp records labelmate of fellow electronic music legend Aphex Twin, is back with his fifteenth album called Be Up a Hello, which is set to drop on Feb. 1.

Brace yourselves: Nreal Light clones are coming. Since the China-based startup wowed the crowd at CES 2019 with its consumer-centric smartglasses, a number of followers from Asia have emerged, and all with very similar aesthetics to Nreal Light.

What better band than Pink Floyd, the pioneers of psychedelic and progressive rock, to show the music industry how to reinvent album art for the augmented reality age?

As a frequent collaborator with Qualcomm, it would be kind of weird if Nreal didn't have something new to unveil at this week's Snapdragon Summit.

Following up on the initial tease over three months ago, Snap Inc. is finally letting the public get its hands on its new Spectacles 3 wearable device.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

Augmented reality enthusiasts who expected an AR hardware unveiling at Apple's annual iPhone launch event might not have to wait much longer.

Augmented reality can be more than simply a way to enhance navigation, or superimpose virtual sunglasses onto your face. It can also be a platform for shining a light on important social issues.

Ever since Skynet took over the world in the Terminator film franchise, a large segment of the world's population has feared artificial intelligence.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.