You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.
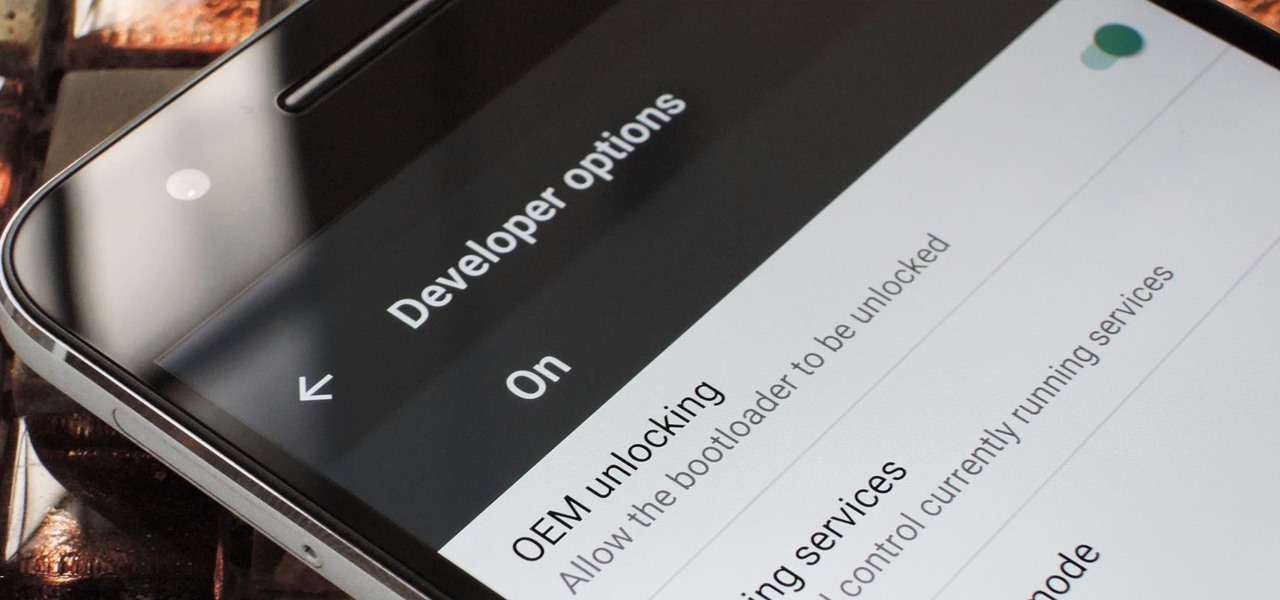
If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

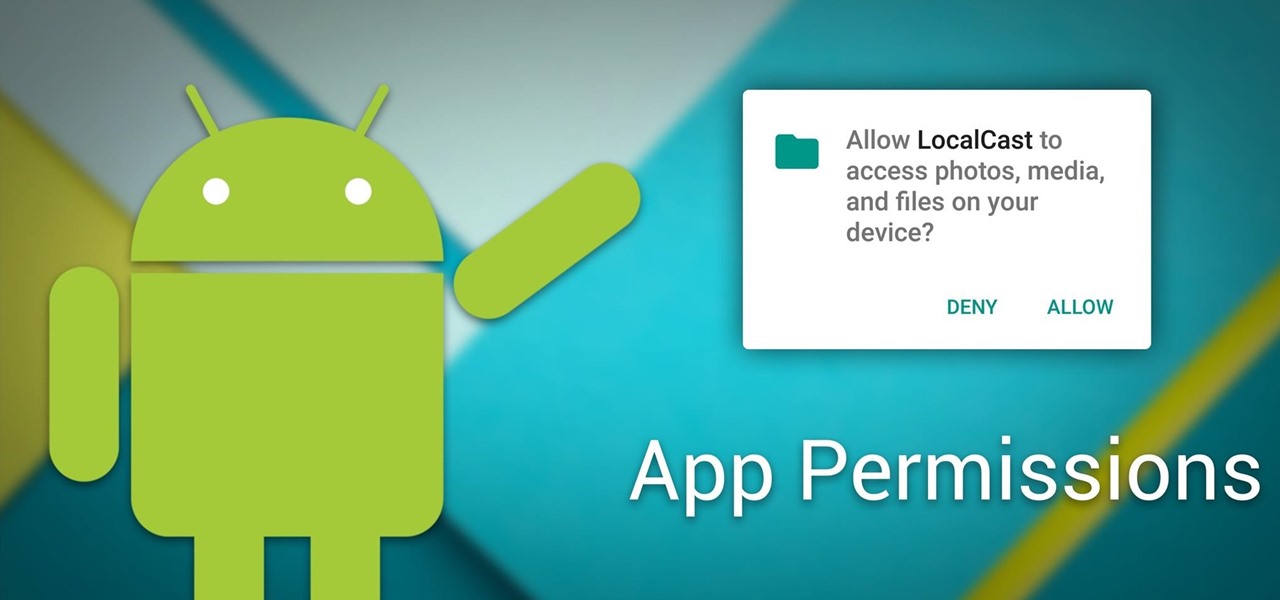
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

Sushirrito offers burrito-sized sushi rolls that are on the cusp of becoming the trendiest handheld snack to hit the foodie world. According to its website, Peter Yen created the Sushirrito brand, trademarked it in 2008, and opened his first restaurant in 2011 in the Bay Area with Ty Mahler, executive chef.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

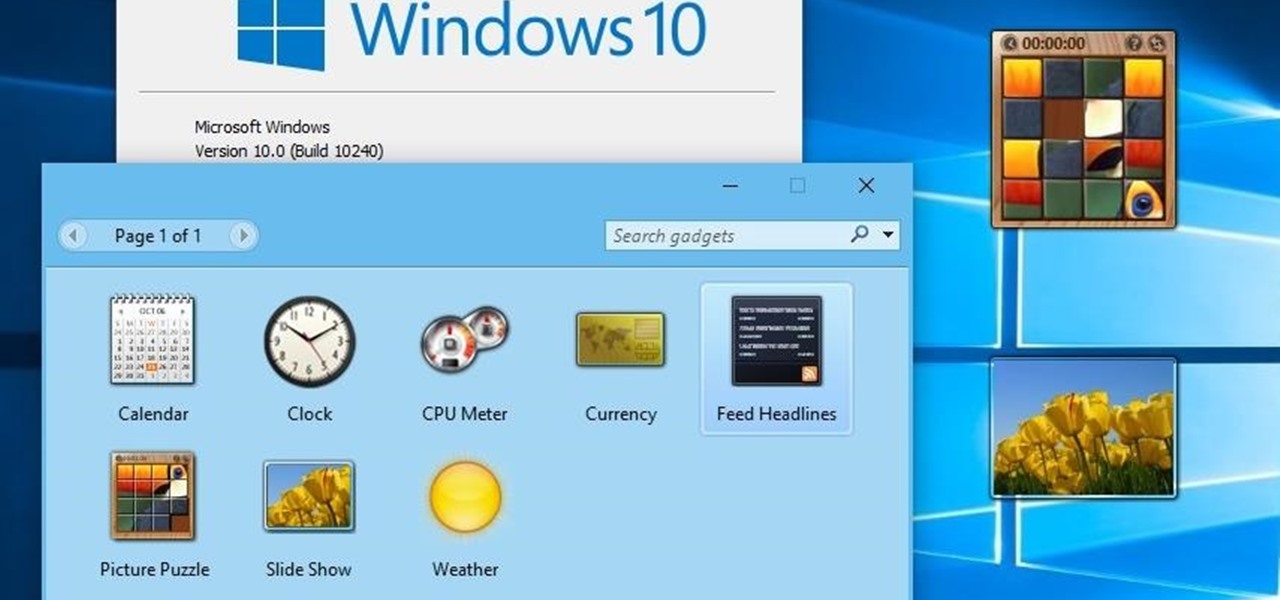
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

Most primary cocktail ingredients just sound delicious. Lime and tonic water? Yes, please. Bitters and simple syrup? Sign me up. Egg whites and... wait... egg whites? In a cocktail?

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platform in PlayStation Vue, NBC has decided to stream the Super Bowl and all of its festivities online. Before we get to all of the many ways you can stream Super Bowl 49 between the New England Patriots and Seattle Seahawks ...

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

If you are having problems playing your sweep picking arpeggios fast and clean then you are not alone. Many guitarists have the same problem. I suffered from the same problem, years ago. In fact, playing sweep picking arpeggios with poor technique is one of the most common problems that I encounter with my guitar students. After helping them overcome these challenges I have discovered 2 different approaches to improving your sweep picking technique. The first will keep you frustrated with bad...

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

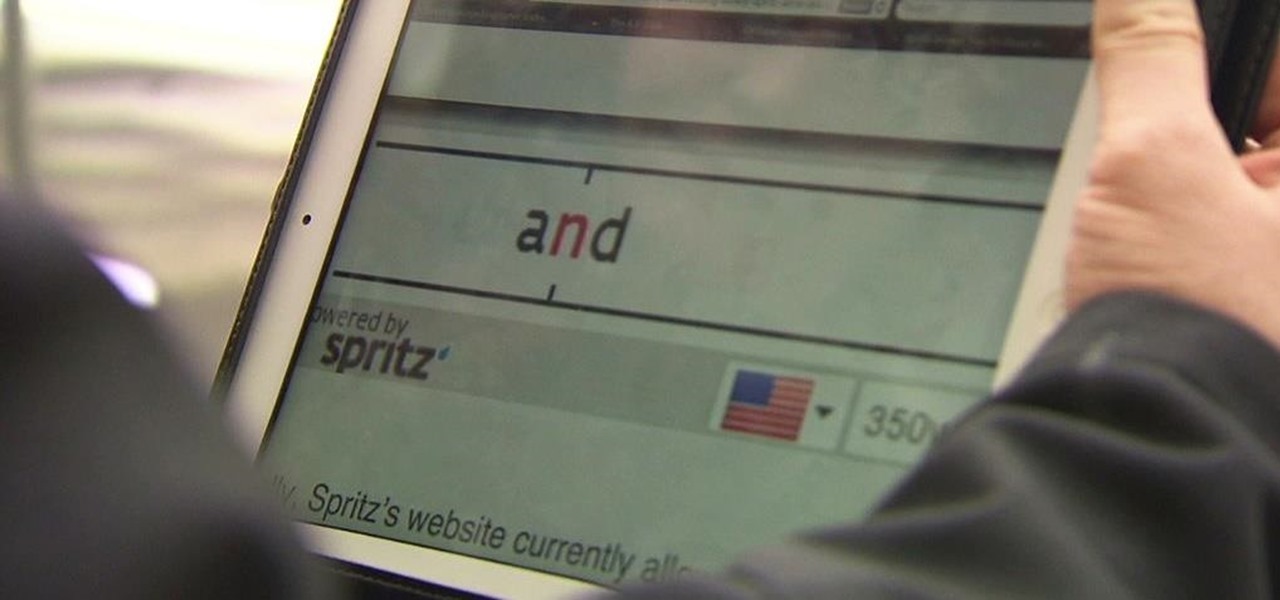
Reading is no longer a leisure activity—it's an on-the-go activity that requires speed and less attention. That's why speed reading apps are growing in popularity. As smartphones and tablets increasingly take over the traditional book market, reading skills need to be adjusted accordingly, so you can cram in 5 pages in-between texts and emails.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

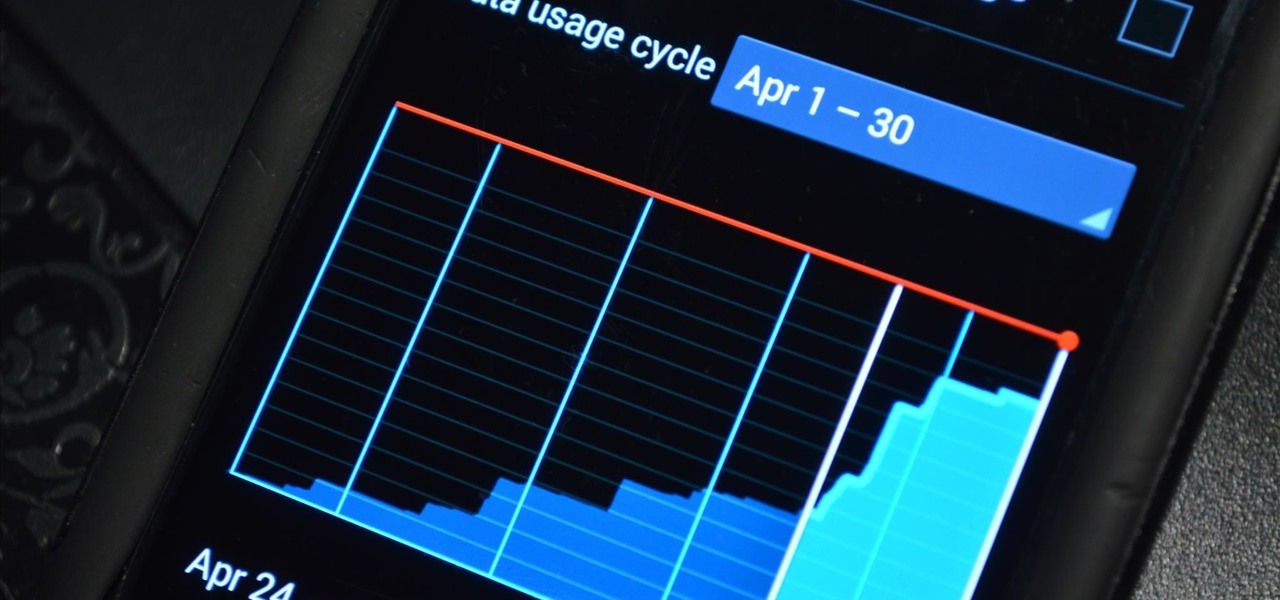
Your status bar is a hub of essential information, displaying things like battery life, signal strength, and missed calls and texts.

Photo mosaics have interested me since I was a kid. I could never understand how someone took the time and effort to make one large masterpiece out of hundreds of smaller images. Maybe I'm too daft to grasp the concept, but it seems extremely difficult. I certainly don't have the necessary skills to make my own work of art, but luckily my Nexus 7 does.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

It's a done deal. KitKat is the shit, and everyone wants in on it. Unfortunately, the Samsung Galaxy S3 won't see any of Android 4.4's features incorporated into TouchWiz for some time, as we're still on a 4.1 version. Still, we can throw a few of KitKat's features onto the device ourselves, like the home launcher and new keyboard. And now, we can even get a feel for its smarter phone app.

The upcoming web series "Crypto-Historians" does for cryptohistory what Indiana Jones did for archaeology. For those who don't know, cryptohistory is the study of supernatural or alien elements throughout history, and yes—it's a "real" field.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

From the front lines of mainstreaming augmented reality smartglasses comes the latest update from Snap and its Spectacles wearable.

Snapchat parent company Snap may finally be taking the big step into the fully-functioning augmented reality wearables realm with the next iteration of its Spectacles devices.