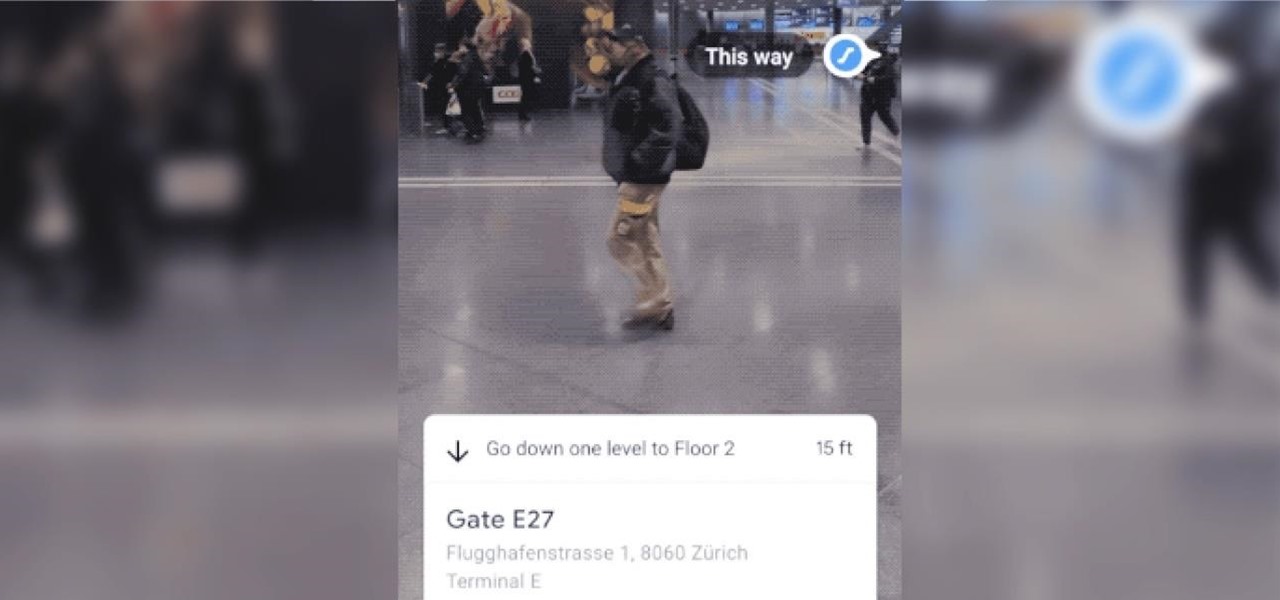
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

You only 'thought' the HoloLens 2 was the most expensive augmented reality device on the market. As with many things tech, Japan is here to up the ante with what may indeed be the most expensive AR-dedicated wearable we've seen—the Canon MREAL S1.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.
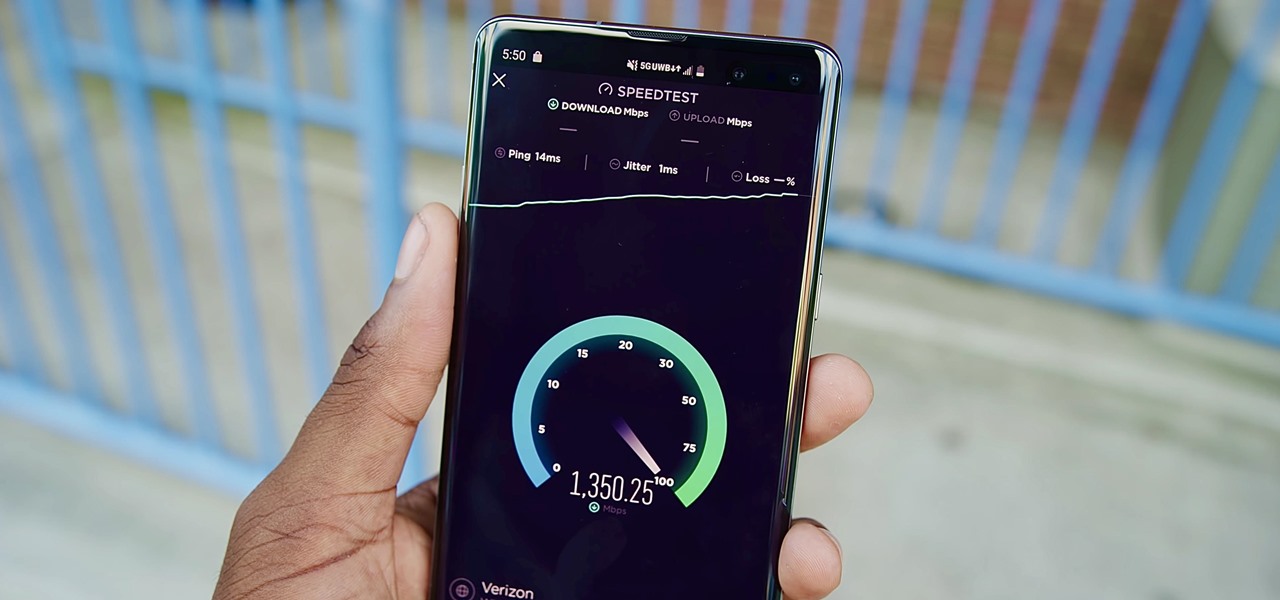
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

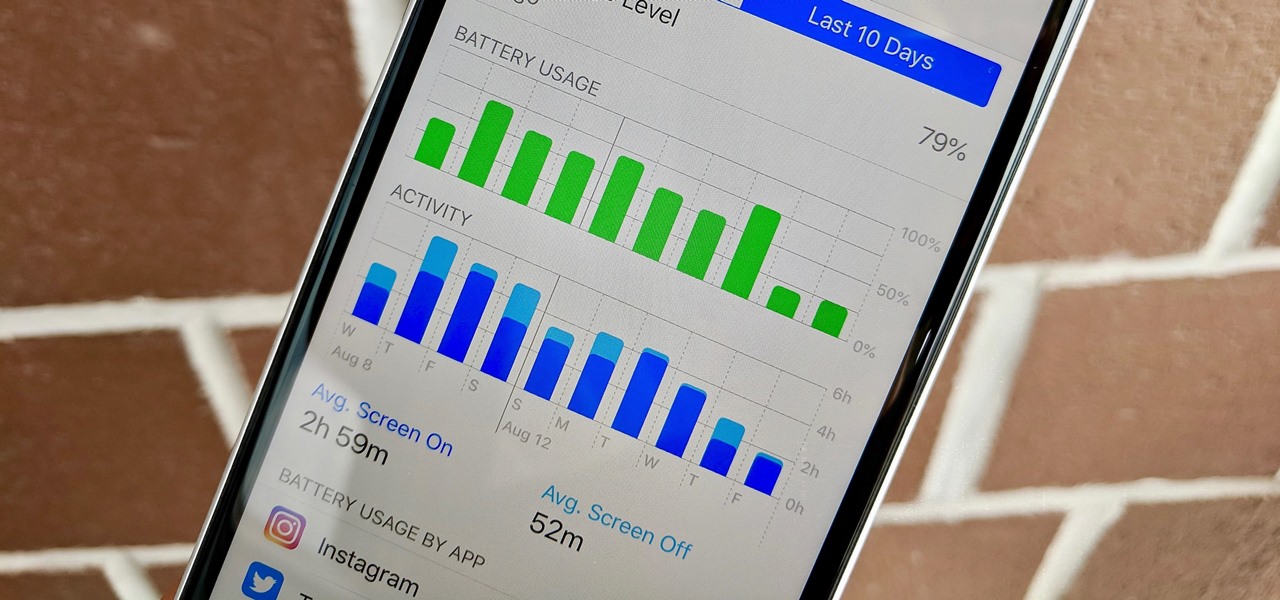
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

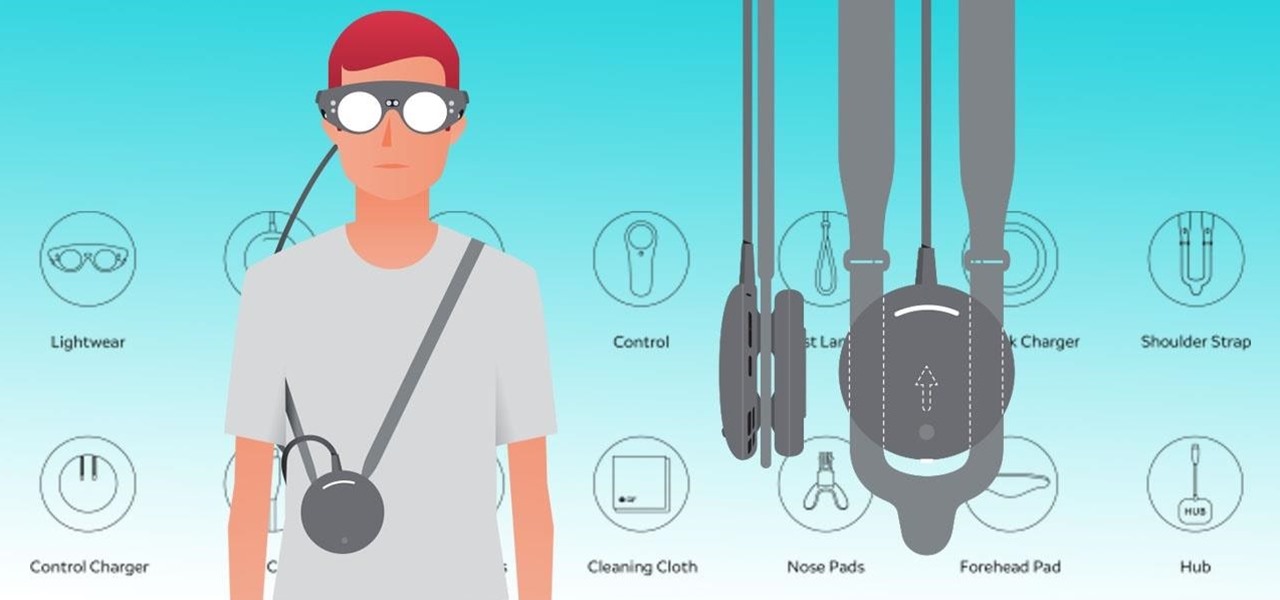
Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

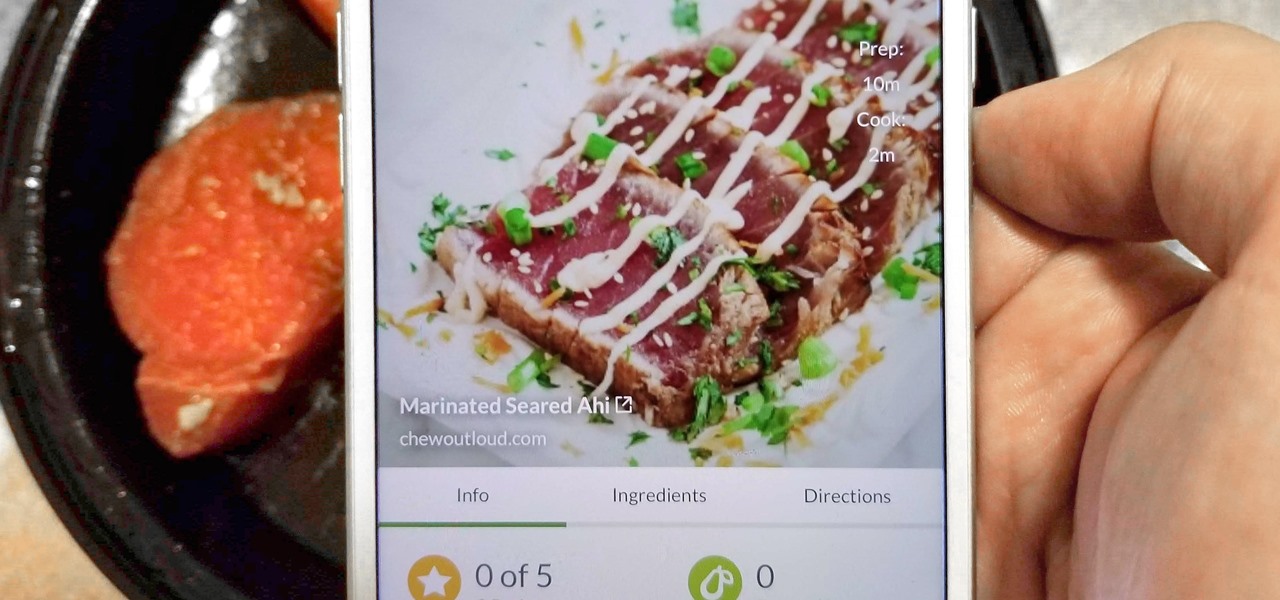
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

OnePlus surprised the mobile industry last year when it revealed the OnePlus 3T in November, an improved version of the OnePlus 3 that came out just months earlier in June. While many thought this was a fluke, history has repeated itself with the arrival of the OnePlus 5T.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

At Build 2017, the annual developer's conference, Microsoft featured a Windows Mixed Reality Academy. This class was designed to get a developer started creating Mixed Reality experiences quickly. For those of us already developing for the Microsoft HoloLens, while the class — which is now available on the Microsoft website — did offer our first real chance to work with the new Acer HMD, there was not much depth.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

After poor sales of last year's HTC 10 and the terrible reviews their first 2017 flagship received, HTC really needs the HTC U11 to succeed. But they're not taking things lying down, as they've come up with some interesting tech for their latest handset.

The big day has finally come—the new iPhone 7 and iPhone 7 Plus have been officially unveiled. Apple debuted their new flagship devices at a keynote event in San Francisco on September 7, and as we've grown to expect, there are tons of changes in store for the world's top-selling smartphone.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

Running out of any shower necessity is just a temporary annoyance, but it always seems worse when it's an empty can of shaving cream or gel. Sure, you could dry shave or use whatever liquid toiletry item is in hands reach, but if you want a truly smooth shave without irritation, you'll want to try one of the following alternatives. Some of them might even work better than your can of Barbasol or Skintimate.

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Everyone and his mother (and grandmother) has a chocolate chip cookie recipe that he swears is the absolute best recipe, guaranteed to produce a chocolate chip cookie so good it will make you weep with joy. The problem with that is that everyone—relatives included—has a different idea of exactly what constitutes a perfect chocolate chip cookie.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

Making a good crêpe takes practice and commitment. The batter is rich—most recipes incorporate melted butter, whole milk, and several eggs—and the cooking of the crêpe requires good technique. You have to learn to deposit and swirl just the right amount of batter to get the thinnest possible crêpe, and then learn how to loosen the entire circle and flip it over without tearing or snagging.

It's that time of year when high school students say goodbye the their past four years of coddling, ready to enter the "real world" and the next chapter of their lives—college.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Americans consume over 1.2 billion pounds of potato chips each year, making it one of the most popular snack foods in the United States.

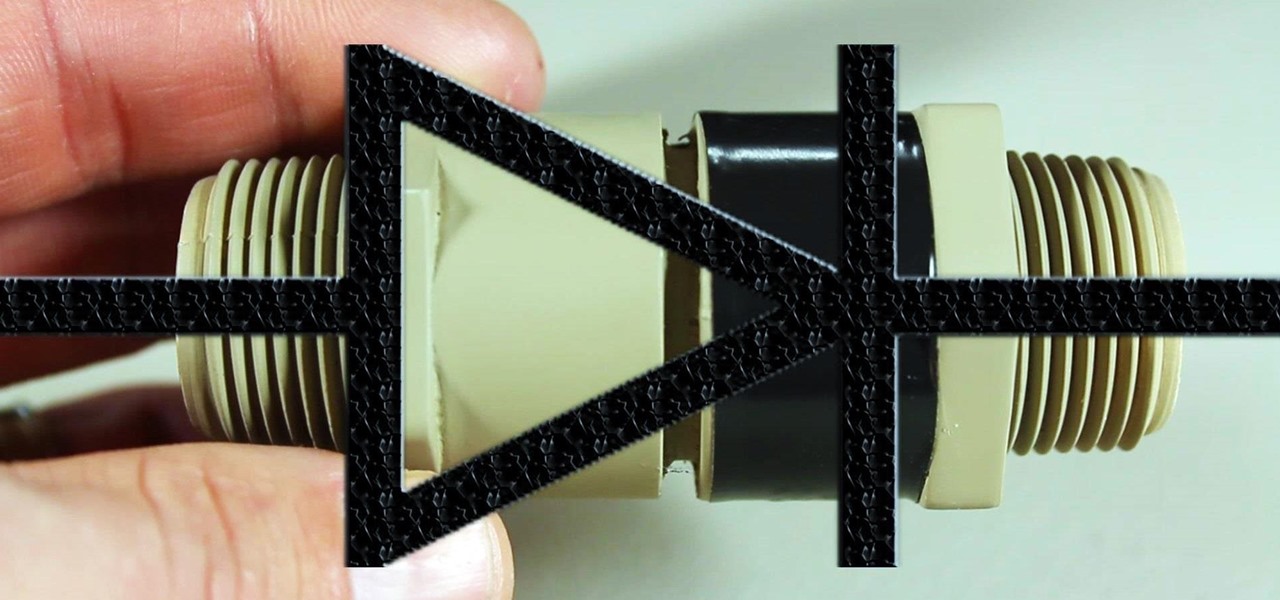
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.