With the Android 4.4 KitKat update slated for release sometime in October (according to Nestle), I'm sure you're excited to get your hands on and test out all of the new features of Google's latest mobile operating system.

One of the most heated topics in the Android community now (and probably forever) is stock Android, with lots of users requesting the ability to use it rather than the manufacturer's skin.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

One thing that gets overlooked on Facebook is the amount of videos you can watch, and I'm not just talking about videos uploaded directly by Facebook users—I mean everything ever shared—YouTube, Vine, Instagram, Vimeo, etc.

I know Americans love to hate on the French, but from my standpoint, they've given us a lot of things we should all be thankful for, like French kissing, casual sex, Pepé le Pew, and of course, French fries. Well, maybe not...

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

The new Samsung Galaxy S4 just received an update to Android 4.2.2, so why is it that my Galaxy Note 2 is still running an older version of Jelly Bean? It felt like yesterday that my device was finally updated to 4.1.2, but why even bother since 4.2 has been around since last November?

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

McDonald's is probably the most recognizable fast food chain in the entire world, with over 34,000 restaurants in more than 100 countries. In may not be the healthiest place to get a meal, but like millions of kids in America, I grew up on McDonald's unquestionably delicious products—and I'm still alive.

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

Finding love is tough. Movies like The Notebook and Twilight have ruined the expectations of love and relationships for us guys. Some women's ideal love situation is being kissed by a glittery sparkling vampire. "I know we only met a few seconds ago, but I'm deeply in love with you."

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.

There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it last-minute again, do you?

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Ready to stop going threw life blind? Try to get a glimpse of the future or at least a use these as a reflection of what’s happening in your life with your own tarot cards. Tarot cards can provide endless hours of entertainment.

Eeverst isn’t for armatures. If you have the ambition of climbing Mt. Everest you will have to do a lot of preparations including physical fitness work, travel arrangements, not to mention putting aside thousands of dollars to make your dream a reality.

Detache is French for separate bows, not to be confused with the English "detached", with space between the notes. With this tutorial you will learn to play the detache bowing technique on the violin. The detache technique helps build a consistent and confident sound, improves projection and improves control of the entire bow, especially at the very frog and tip. Play as loud as possible. Bow next to the bridge (Control the "Sounding Point"). Keep the bow straight and flat. Use the entire upp...

Lose weight and stay healthy by learning how to do aerobic exercises with the expert tips in this free fitness video series on doing aerobic exercises.

Our mountain biking expert discusses the correct way to get over, around and through any obstacles you may encounter on your adventures. He also demonstrates proper weight distribution and riding techniques, and discusses modulation and braking theory. If these topics sound sophisticated, that's because they are, a veritable master's class in mountain biking physics. So get your degree today!

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

The Pixel 4 isn't for everyone, but it does have its appeal in several specific use cases. Thanks to Instagram, YouTube, and other social media platforms, the fitness industry and smartphone world are now intertwined like never before, and it appears Google's aware of this.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

Unlike many other OEMs, Samsung has two prolific phone series they release each year, the Galaxy S series and Galaxy Note series. At first, the latter was the bleeding edge of technology, but in recent years, the line has been blurred. So what do you get with the Note 10+ over the S10+ besides a stylus? Let us compare.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

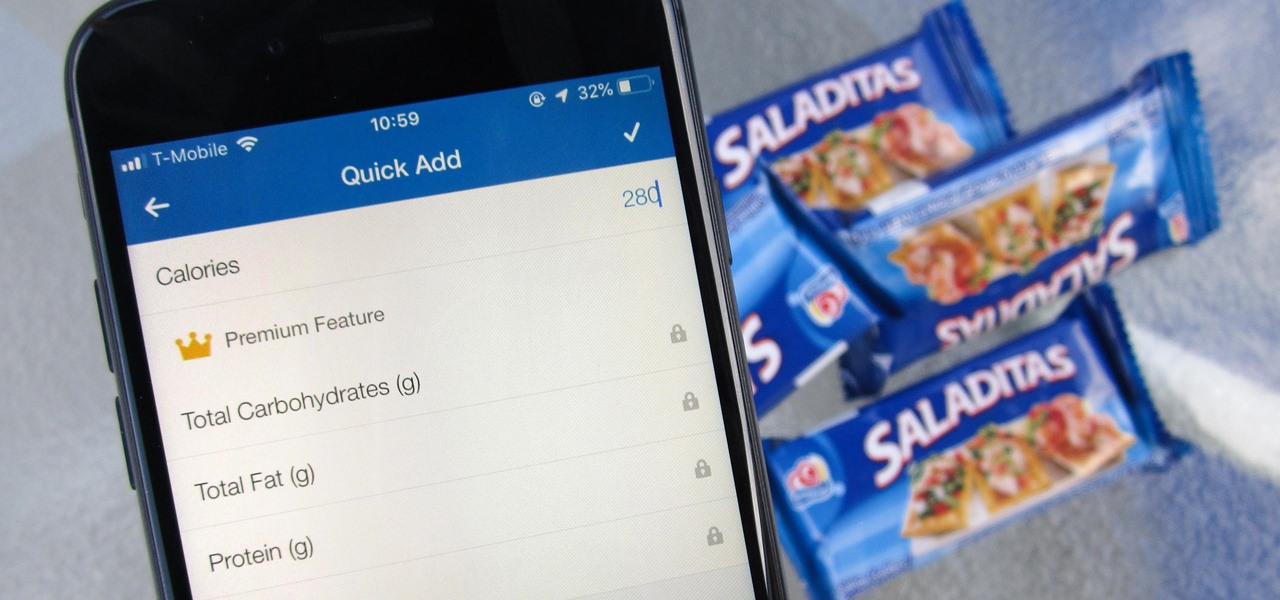
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.

Niantic's most successful app, Pokémon GO, has become the first app to integrate the company's Real World Platform, the developer's AR cloud technology that enables multiplayer AR, persistent content, and occlusion with physical objects.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

Unfortunately, the very places we go to receive health care put us at risk for becoming infected with superbugs, bacteria exposed to so many antibiotics that they have become immune to their effects. Clostridium difficile (C. diff) is one such bacteria. It causes inflammation of the colon and rampant diarrhea that can have life-threatening consequences. Part of its virulence lies in the tough spores formed by the bacteria. They are responsible for starting infections in the colon and for spre...

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.