
News: Magic Leap Teams with HBO & AT&T to Deliver Game of Thrones Experience
In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.


In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.
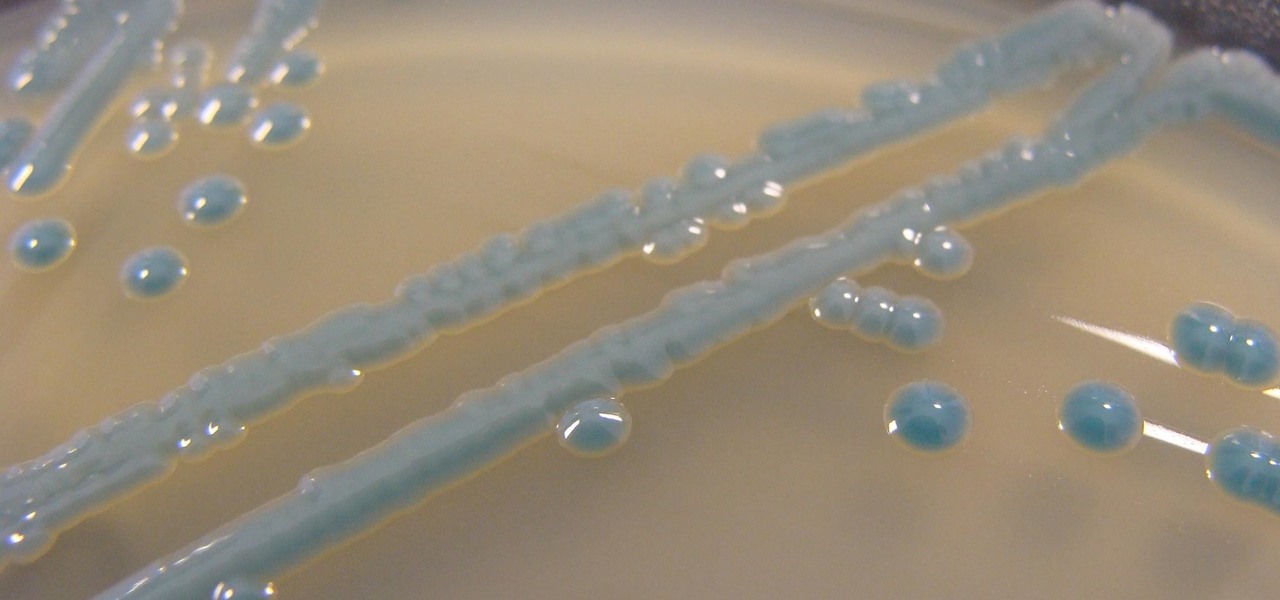
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

People who have heart disease get shingles more often than others, and the reason has eluded scientists since they first discovered the link. A new study has found a connection, and it lies in a defective white cell with a sweet tooth.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

While Lyme disease can be disabling, the wrong treatment for the infection can be fatal.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

Yellow fever has emerged again in Brazil, causing death and disease to people unprepared for this mosquito-borne illness.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.
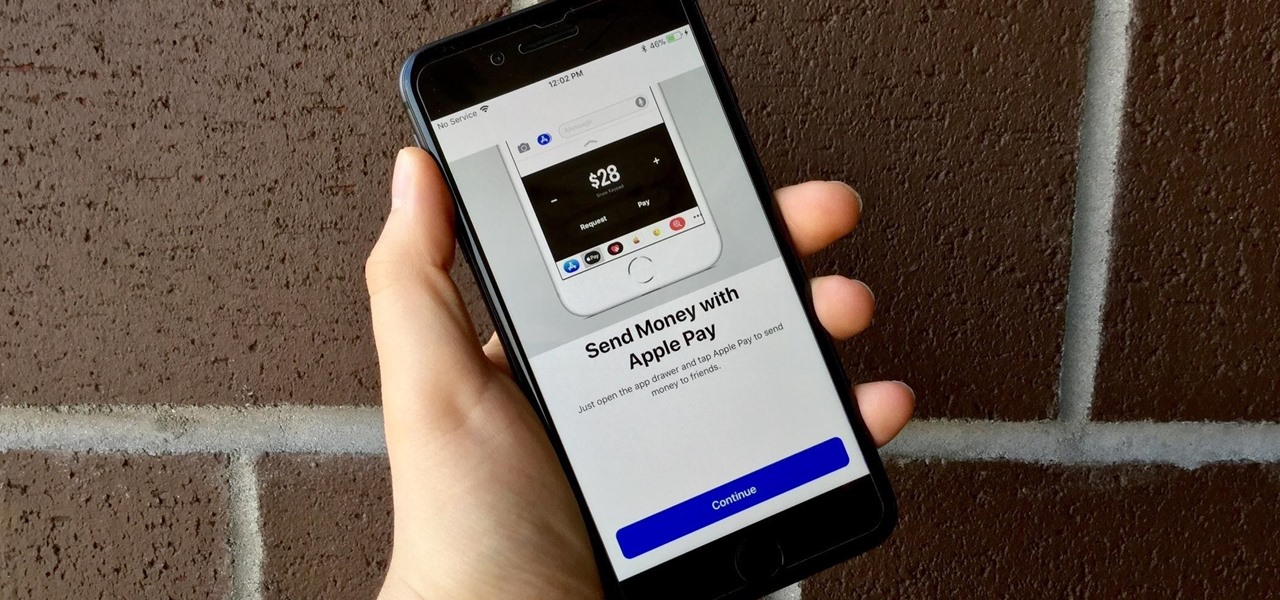
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Curious about the basics of metal inert gas welding? Watch this instructional welding video for some vital safety tips. A shielding gas tank contains 3,000 psi of pressure, so keep your welding equipment safe distance from your high pressure tanks. To run a bead, you need to set your wire feed speed and your voltage in order to begin welding with an average angle iron. This video provides all of the preliminary steps to running a short bead.
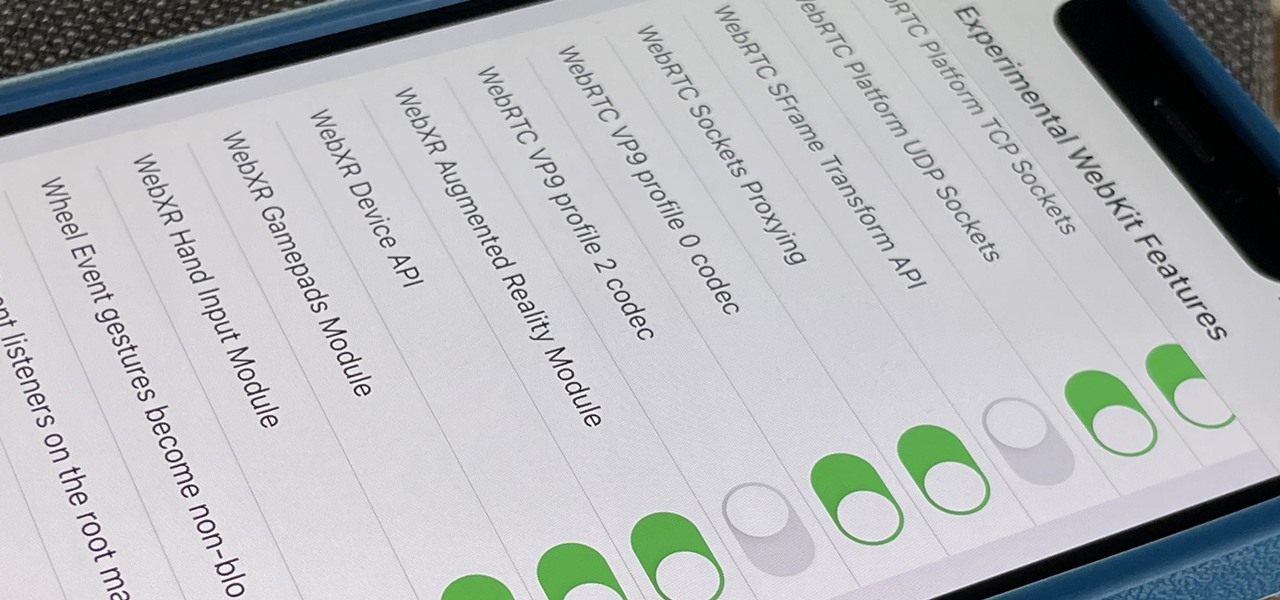
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

As the sports world slowly gets back to normal while observing pandemic protocols, fans are once again being folded into the mix in innovative ways.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.