
How To: Test yourself with the Stroop Effect
This video examines the psychological phenomenon known as the Stroop Effect and shows you a test for it.


This video examines the psychological phenomenon known as the Stroop Effect and shows you a test for it.

Asphalt5 is a racing game for the WebOS phone operating system, originally developed by Palm. If you want to play it (and you should) on your Nokia N900 handset there are some complications you're going to have to get through, and this video will show you how step-by-step.
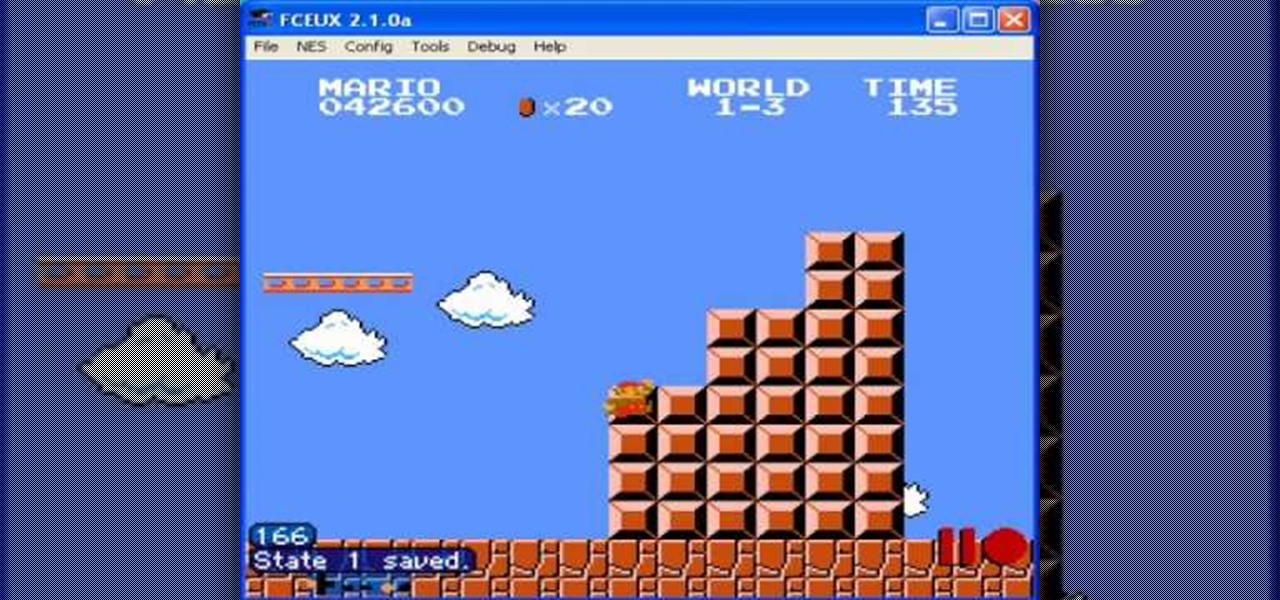
The flagpoles at the end of each level in Super Mario Bros are rewarding when you're playing the game, but if you're setting up a TAS they suddenly become infuriating wastes of time. This video will show you how to TAS skip the flagpoles, which should improve your time substantially.

The single-player campaign mode in Call of Duty: Black Ops may be intense, but the multiplayer mode is a bloodbath of pure addiction. Black Ops takes the super successful formula of Modern Warfare and adds its own special twist. There's some changes, and Jessica Chobot from IGN Strategize is going to tell you all about them!

The Care Bears have stood the test of time, from their first appearance on greeting cards, to cutesy, plush teddy bears, to animated television series, to adventure-filled movies. The Care Bears may be long gone from television, but not from out hearts (especially Sara Griffith's of SharksBiteOfLife).

In a previous Nurd Rage video (here), Dr. Lithium showed you that pyrolytic graphite was diamagnetic, and that it could be stably levitated over magnets. It was repelled by a magnetic field, and this repulsion was strong enough to levitate it. In this science video tutorial, you'll learn how to levitate plain old pencil lead this time.

This video will show doctors the process of examining the upper extremity of the body. When you exam the extremities or any joints, it's good to have a systematic approach to how you will examine each joint. Learn about the inspection of each joint, range of motion, palpation and strength testing from Eve Bargmann, M.D. When examining the upper extremity, you should start with the shoulder and work you way down to the elbow, then the wrist, and lastly, the hand.

Rust protection doesn't have to cost a fortune. With a little zinc and some electricity, you can protect your precious metals from rust by galvanization. When you galvanize something, you're giving it a protective coating, and in this case, it's a zinc coating.

This ball isn't like any you've ever seen before. It's stubborn, it's unpredictable — it's practically immovable. Gravity cannot control this magic ball.
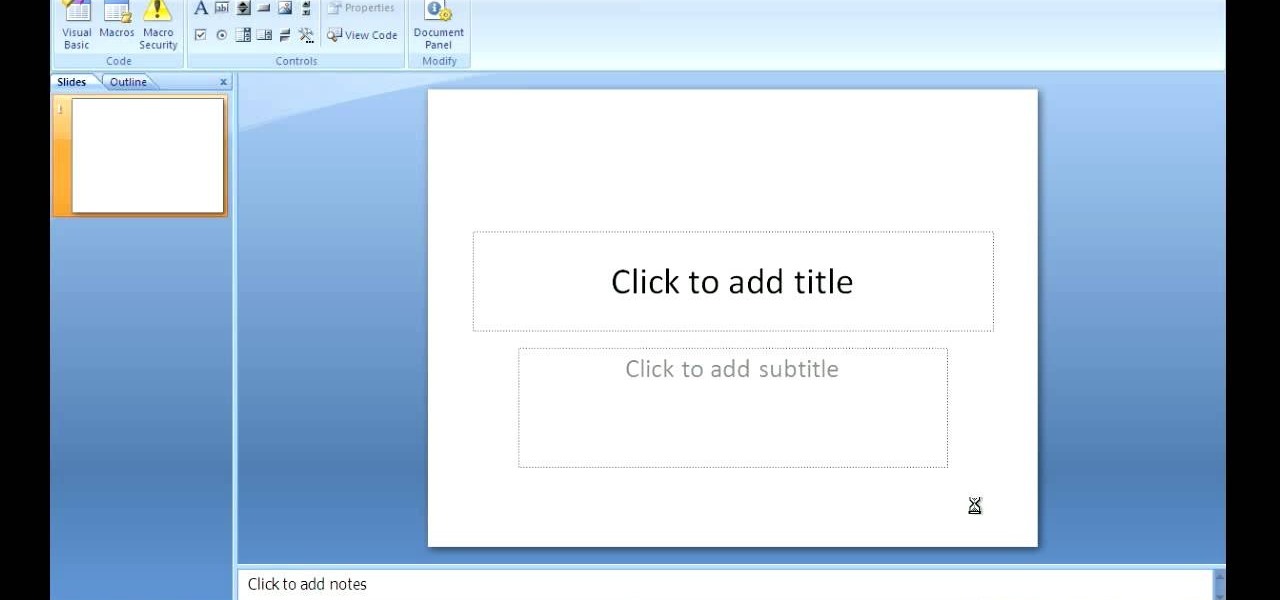
Chris Davis with the Educational Technology Center shows us a few easy steps to putting YouTube videos in our Microsoft PowerPoint 2007 presentations. To start you'll need to have an active internet connection and you should have the developer tab in PowerPoint active. To do this go to the Office menu, PowerPoint options, popular and click show developer tab. Locate the hammer looking more control option button and scroll down to Shockwave Flash Object and click it. This allows you to draw a ...

This video is about how to make a classic American pot roast. You start with a chuck roast. You want to start by generously salting and peppering both sides. Heat about 2 tablespoons of canola oil in a skillet and then brown the roast on both sides. Then remove it from the pan and add an onion that's been cut into 8 wedges, 2 carrots that have been cut and peeled into 2 inch pieces. Add a few pieces of time and rosemary. Once the vegetables have a good color you move them to the side and add ...

Do you know what an idiom is? If you don't, this English lesson is sure to make you an expert on idiom usage.

This video shows you a mind-reading card trick. This particular trick requires 8 cards: 4 kings and 4 queens. First, the subject is asked to memorize one of the 8 cards as they are laid out before the subject, face-side up. The cards are picked up and sorted in various ways and the subject is asked a series of questions. The questions are always asking whether the card the subject memorized is in a certain group that the trick performer presents. The card in question always is in the group th...

This instructional video series is on how to build any type of 2/5th (40%) scale, fully functional tank. The specific model demonstrated is the M60 Patton. An MBT. A destructive force. If you have any questions about your backyard tank build, please address them to "Dave's Tank Foundry" at Scaled Tanks.

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Check out this video tutorial on how to make a cheap multi-touch pad like in the MacBook Air. Yes, that's right... you can make your very own multitouch, finger-sensitive touch pad for your computer. This is definitely the cheap way to go to make a Multitouch Mini (MTmini), with a maximum of fifty bucks down the drain. This multitouch touchpad (or trackpad) is easy!
If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on testing your phone line (NID) if you have no dial tone. If there is no dial tone on your home lines, just test your NID (Network Interface Device) on your house to see what's going on. This is an important step to getting your High-Speed Internet up and running.

Do you think you might have a Thyroid Problem? Dr. Stephen Langer shares how you can tell if you have thyroid problems through a home test.

The flame test is used to visually determine the identity of an unknown metal of an ionic salt based on the characteristic color the salt turns the flame of a bunsen burner.

Amber, emergency, and public safety alerts on an iPhone are loud — startle-you-to-death loud even. They can happen at any time, day or night, and sometimes back to back when you're in a big city. Those blaring sirens can wake you from sleep, interrupt an important meeting, or disrupt an entire movie theater mid-movie, but you can turn most of them off if you're tired of hearing them.

Google recently started testing a new SafetyNet check that might spell trouble for rooted Android devices. It cross-checks your SafetyNet status with Google remote servers, making it impossible to fool by normal means. If Magisk shows you pass SafetyNet and you're still having issues, you might be affected by this change.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?
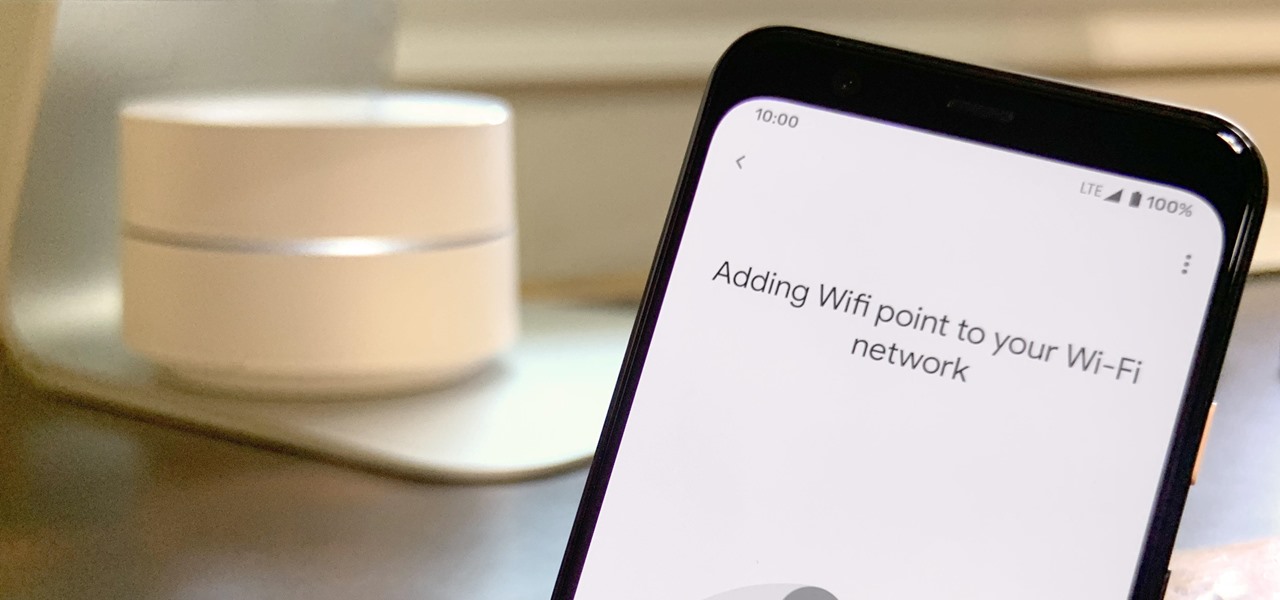
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Beta testing Apple's mobile OS has never been more interesting. After eight seeds of iOS 13.0, Apple unexpectedly released the first beta for iOS 13.1, a whopping 23 days before iOS 13.0 made its public debut. Since 13.1, however, we haven't had any betas to sink our teeth into. That is, until now, as Apple just released the first developer beta for iOS 13.2 today, Wednesday, Oct. 2.
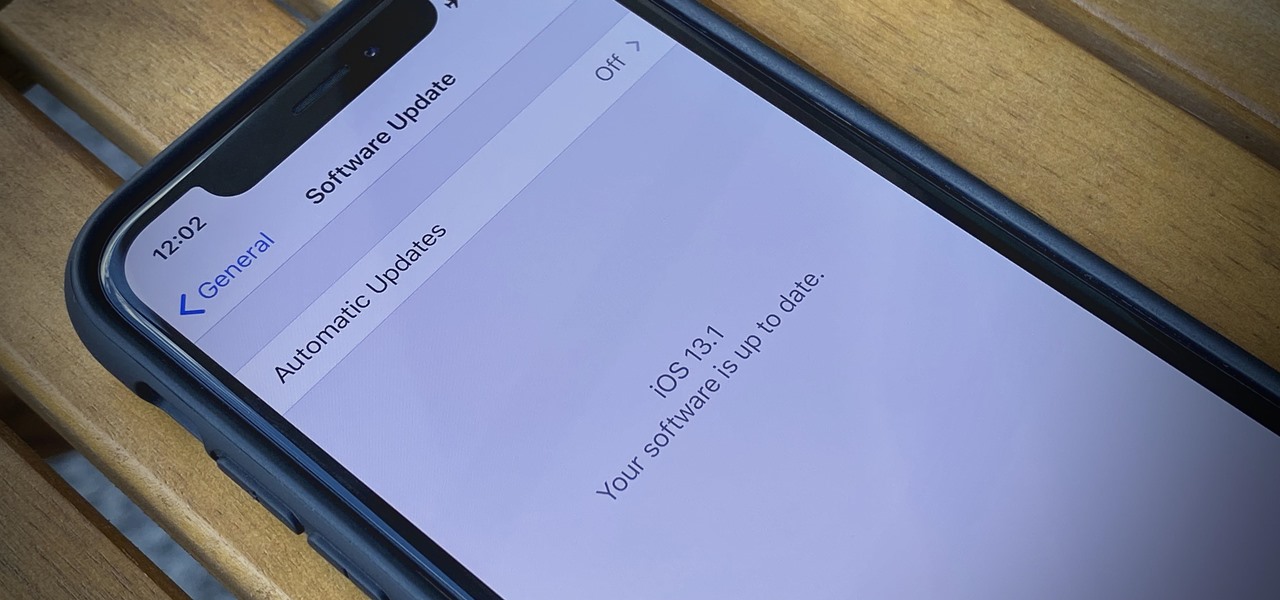
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.
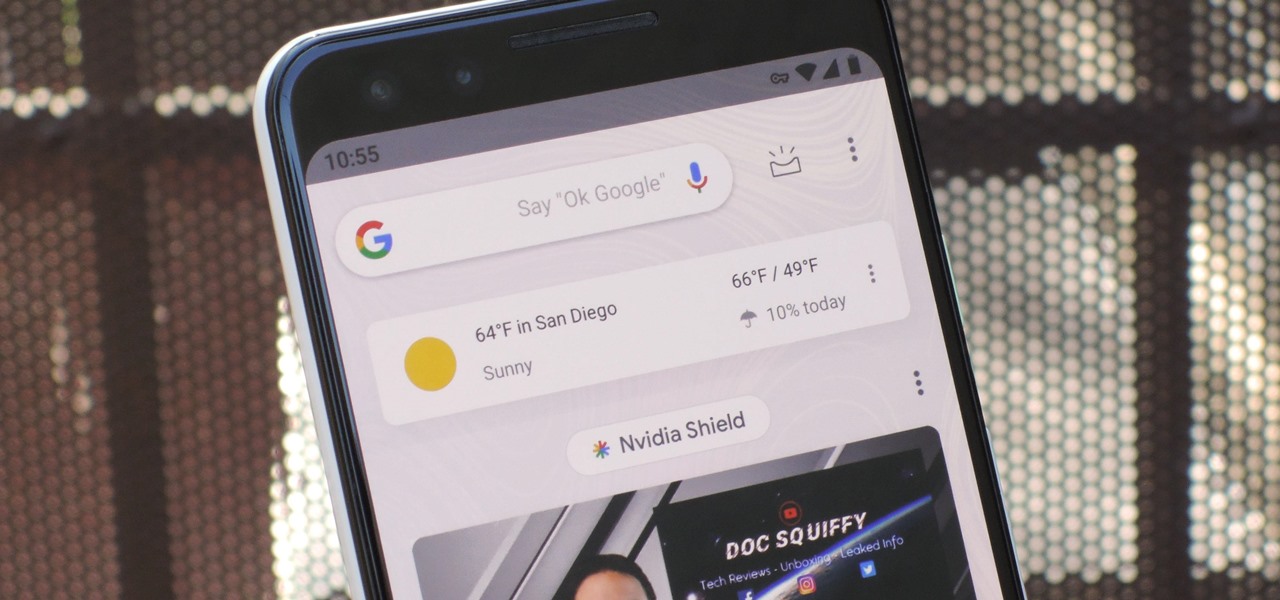
One of the most useful features of the Pixel Launcher is access to the Google Discover page. Initially, this feature was exclusive to Google's launchers, forcing users to give up the customization of apps like Action Launcher if they wanted the quick access to relevant news and updates it provided. Fortunately, this is no longer the case.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Google Chrome is an incredibly popular web browser on both iOS and Android devices, just like its desktop version. That's why it's number one browser in both the iOS App Store and Google Play Store. But for those of you who want even more features, you can test drive the Chrome Beta and get new updates first.