Could you boost your brain power by eating a banana? Improve your memory and IQ by pressing certain points on your body? Absolutely! In this video, we'll show you how to amp up intelligence using super simple natural remedies.

You've probably tried every alleged hangover cure--from cold showers to hot coffee--with little success. But a hangover remedy does exist! So watch this video and learn how to be a drunk without suffering hangovers ever again!

Pink eye, or conjunctivitis as your doctor may call it, is a contagious disease that affects many college students. Blame close quarters and bad hygiene for this itchy ailment that affects the eyes. Here's how to treat and even avoid this condition.

Someone you love is consuming much too much and you want to stage an intervention. While interventions can work, a person who abuses alcohol has to be willing to stop drinking. Here, everything you need to know to help encourage a friend to quit drinking.

You know you're in pain, but are you just feeling the aftershocks of that spaghetti dinner, or is it a heart attack?

Every year, 250,000 Americans are diagnosed with a form of skin cancer called squamous cell carcinoma. What exactly is SCC?

If you know the triggers that bring on a migraine you can more easily sidestep experiencing one.

Heart disease affects more than 20 million Americans. Let's explore the various forms that heart disease can take.

A dislocated shoulder results when the head of the humerus pops out of the socket joint. This is not a gradual event, but rather a sudden even where the shoulder moves out of its normal location. Learn how to treat a dislocated shoulder and stay fit in this sports medicine how to video.

Home improvement expert Danny Lipford teaches how to cut drywall around outlets Just watch the video tutorial to see how to cut drywall around electrical outlets.

This pilates how-to video illustrates the Swimming exercise. This pilates exercise is good for core stabilization, upper back extension and hip extension. This is good to improve back strength and those deep abdominal stabilizers.

Teflon tape or pipe dope can be used to create a seal on black iron pipe. Tim Carter of AsktheBuilder.com demonstrates how to do the job right and shares some helpful tips. This black iron pipe is used to transport natural gas to your furnace, water heater and stove. This pipe has threaded fittings at the connection point which need to be sealed with pipe dope or Teflon tape. Teflon tape should be wrapped onto the male end of the pipe in a clockwise direction. Pipe dope has the consistency of...

Tim Carter explains why vent pipes are important and how a vent pipe works. These are excellent videos to watch if you need to learn how to prevent clogging in vent piping. If you notice a gurgle when flushing the toilet, it might be an indication that the vent pipe is clogged. Get up on the roof and put a garden hose down the pipe and turn on the water. Be sure to have someone inside checking for any leaks. The water from the hose hopefully will flush out the blockage and your gurgle will di...

In these two videos, Matt discusses 1.d4 d5 2.e3 Bf5, preventing White's Stonewall setup by beating White to the d3-h7 diagonal. The only way White can play for an advantage is to play 3.c4 with the goal of an early attack on b7. Some of these positions can also be reached via the Slav Defense.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

The wait is finally over. Apple just released iOS 13.2 for iPhone, the latest update to this year's iOS 13 release. The update contains a slew of exciting new features, such as Deep Fusion for 2019 iPhones, a suite of new emojis, the long-awaited Announce Messages with Siri, among many, many others.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

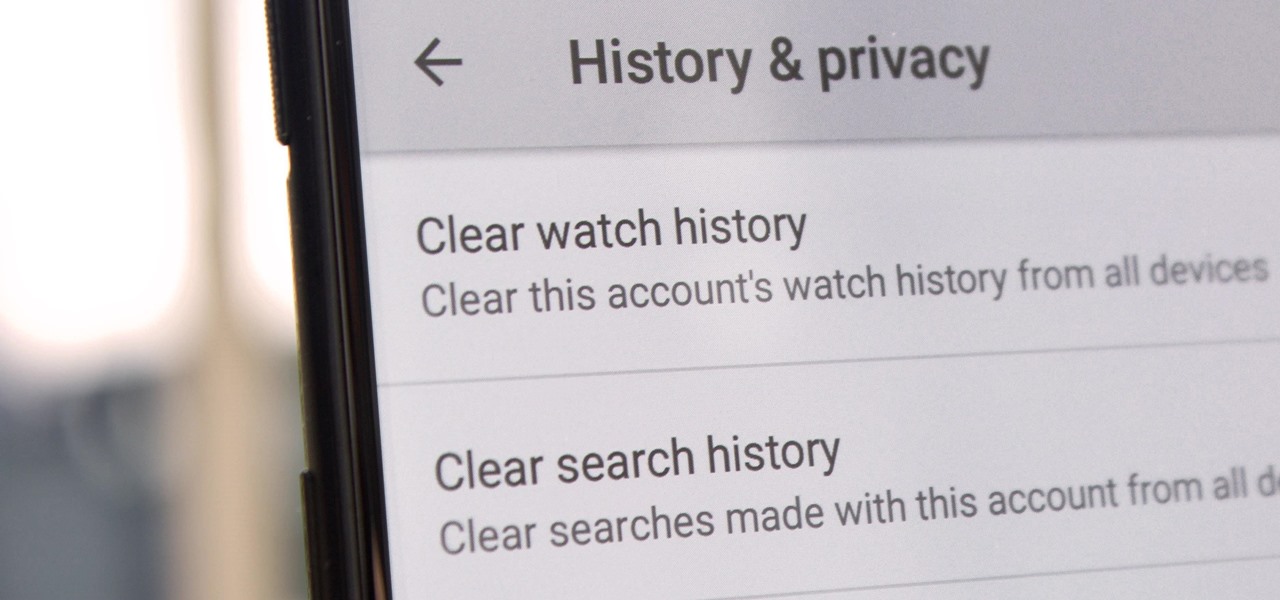
Yeah, yeah, yeah. Get your mind out of the gutter. Search histories can and should be managed. Many folks are uncomfortable knowing that every video they click and every phrase they search is being recorded and saved, and YouTube is no exception.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

A promising new antibiotic has been discovered in, of all things, another bacteria. Burkholderia bacteria live in diverse habitats, including soil, plants, and humans where they thrive by knocking out other microbes that compete with them for resources or threaten their existence. Scientists have discovered they accomplish this by producing a very effective antibiotic.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

The Centers for Disease Control and Prevention estimated that there were 212 million cases of malaria across the world in 2015, and 429,000 of those people died — mostly children living in Africa. Preventing and treating those infections has been a challenging world priority. That makes a new malaria drug discovery — published in Science Translational Medicine — incredibly important.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

Most females have had at least one urinary tract infection in their lifetimes. Recurrent UTIs are particularly problematic in young, sexually active women, where about 80% of the infections are caused by the bacteria Escherichia coli, better known as E. coli.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

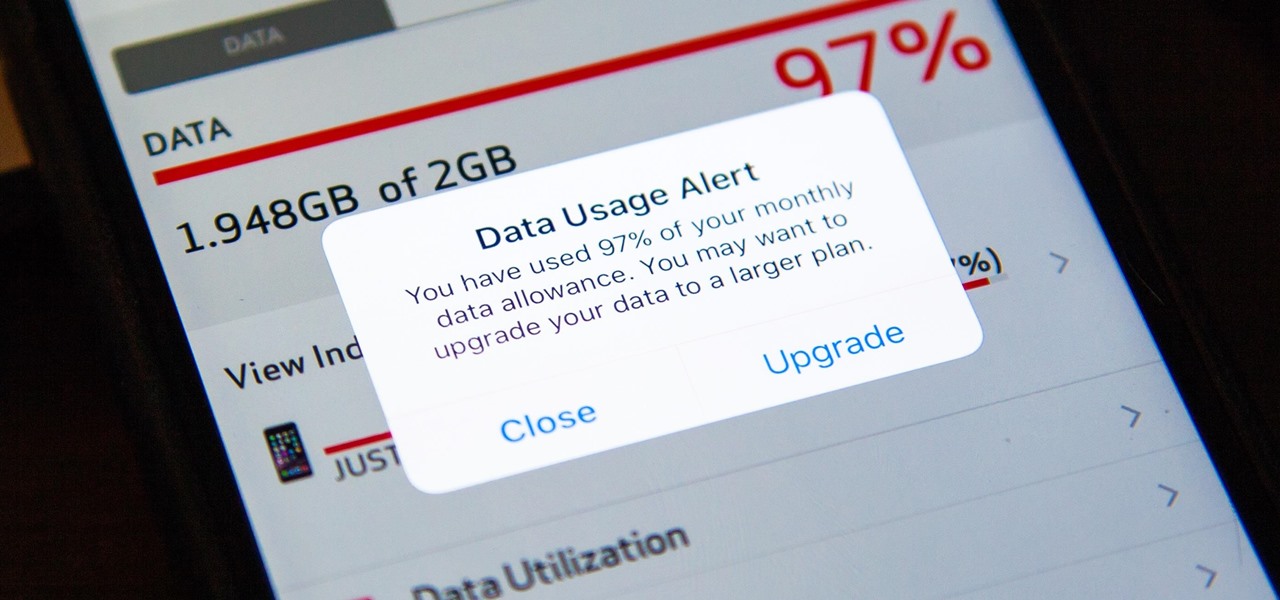
I was one of the first to install the iOS 10 developer beta, and I remember thinking that everything was working insanely well compared to the first iOS 9 developer beta—but then I got a warning that I used 90% of my data 11 days into my following cycle—one day before I updated to beta 2.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.