When you're at work or in class, there's nothing more annoying than sites that automatically play media. One minute you're happily distracting yourself, and the next, you're scrambling to hit pause while everyone stares at you. Not to mention now your boss knows you're slacking off.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

RFID cards are becoming a fairly common way to purchase goods, but they're already widely used to pay fares on buses, trains, subways, and trolleys across various cities. TAP cards are quick and reliable, but it can be a real pain to remember to bring them with you, especially if you weren't planning on using public transportation that day. Luckily, an intrepid tinkerer at Adafruit has managed to find a way to embed an RFID card into her phone, something you're far less likely to leave at home.

Today I would like to share a few data about painting on silk with all the creative readers. The knowledge comes in handy if you want to give a homemade gift or even try to sell a few of your masterpieces.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

You must ONLY conduct this experiment if you are experienced in using combustibles and understand the risk. Fire is very dangerous and can seriously burn you. Seems harmless at first, but believe me, these are bubbles turned evil. When ignited, the bubbles pop almost instantly, and all the propane is released in a huge fireball.

Sodium (chemical symbol Na) is an interesting element. It reacts in contact with both oxygen and water, and several sodium salts are used to produce a yellow color in fireworks.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Impress everyone by bringing a beautiful homemade tart to the next celebration. You can use seasonal berries or even other fruits to create a colorful and flavorful dessert that will make any occasion seem extra special. With its rich pastry cream and tangy fruit wrapped in a flaky, buttery shell, the fruit tart is a classic dessert. Make this version with one or more of your favorites berries.

1. Before applying eye makeup, eliminate under-eye swelling by applying cold compresses to your eyes for ten minutes. Any fluid retention around your eyes will cause eyes to look smaller.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

1. Remove the old makeup and sealer. If you are working on a vinyl or resin doll, you can remove the makeup with a non-acetone nail polish remover. Afterward, wash the face well with soap and water. Work at any stubborn stains with a Mr. Clean Magic Eraser. 2. Sand the head, if necessary. Sometimes dolls will come with set-in stains that no stain remover can touch, or with scratches and gouges in the face. If your doll head is made of resin, in particular, do all your sanding underwater to pr...

Despite all the tragic stories you hear on the news, you'll probably never be involved in a shooting. But you never know. Nobody thinks it’s going to happen to them – until it does. Be prepared to survive a shooting rampage, just in case.

In this how-to video clip series on how to maintain healthy teeth and gums, learn how to practice good dental hygiene, including how to prevent gingivitis, plaque buildup and cavities, how to brush your teeth properly, whether to use an electric toothbrush, how to clean your tongue, how to prevent bad breath, how to floss correctly, and other tips and techniques for a healthy mouth.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Split ends are a pain. They make your hair look fried and frayed, when it should look smooth and shiny. In this tutorial, get some helpful tips on how to reduce and eliminate your split ends.

In this how-to video, you will learn how to take apart your Xbox 360 controller. This will be useful for any repairs or modifications you want to perform on your controller. First, flip the controller over and take off the back. Unscrew the screws in the back. Carefully remove the bottom panel. This will prevent the buttons from falling out. Take off the shoulder buttons. If you want to continue to dismantle the controller, remove the thumb sticks. Next, remove the rumble sticks by pulling th...

In this video tutorial, viewers learn how to rotate the hips to cure a push shot in golf. The mistake often happens at the start of the down swing. People tend to slide the hips too far out and pass the point of the target. This blocks your swing out from going to the target and makes the club swing out to the right, causing a push shot. The proper way to fix this problem is to shift the left leg and rotate the hip. This video will benefit those viewers who enjoy playing golf and would like t...

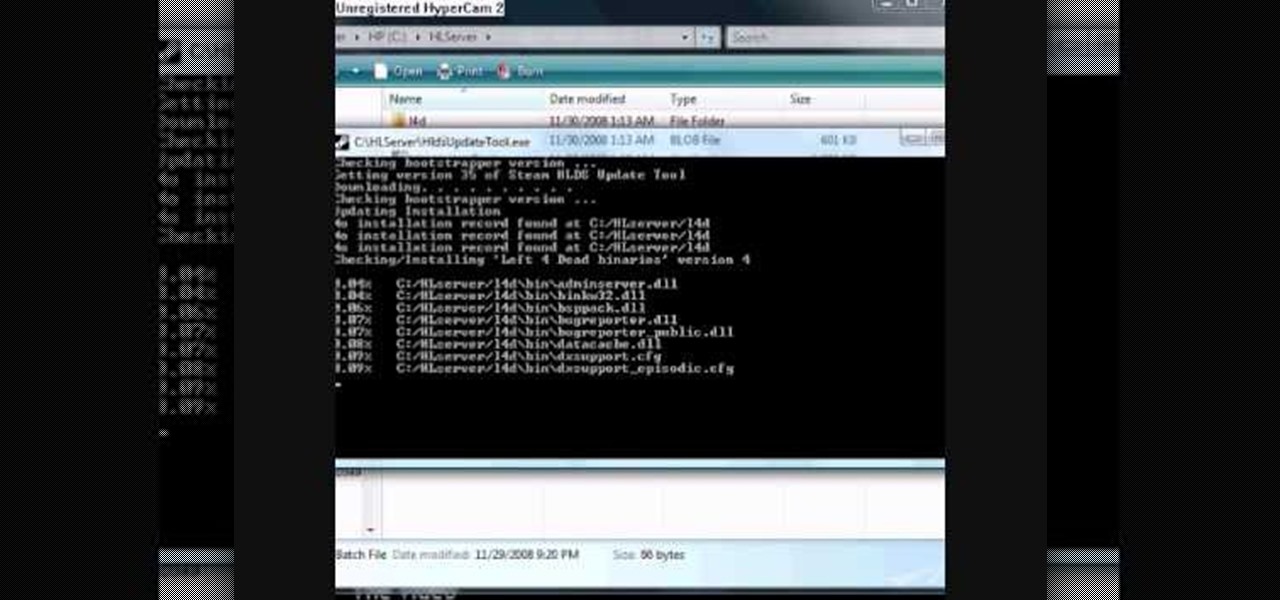
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

The mother's body can be the source of delivery complications like placenta previa or uterine rupture. If delivery problems do occur, your doctor can usually help you manage these childbirth complications with medication or an emergency cesarean section.

Those moisture cracks in your concrete driveway could have been prevented. This how to video hows you how to keep your concrete driveway protected and looking good. Its a total DIY project.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

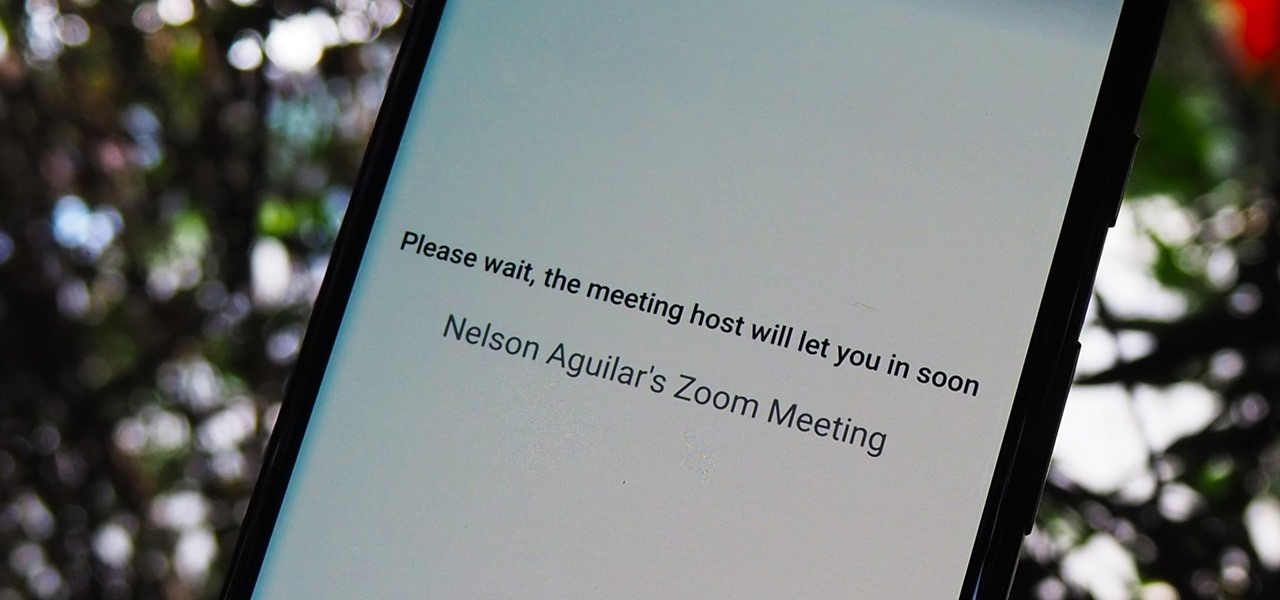
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

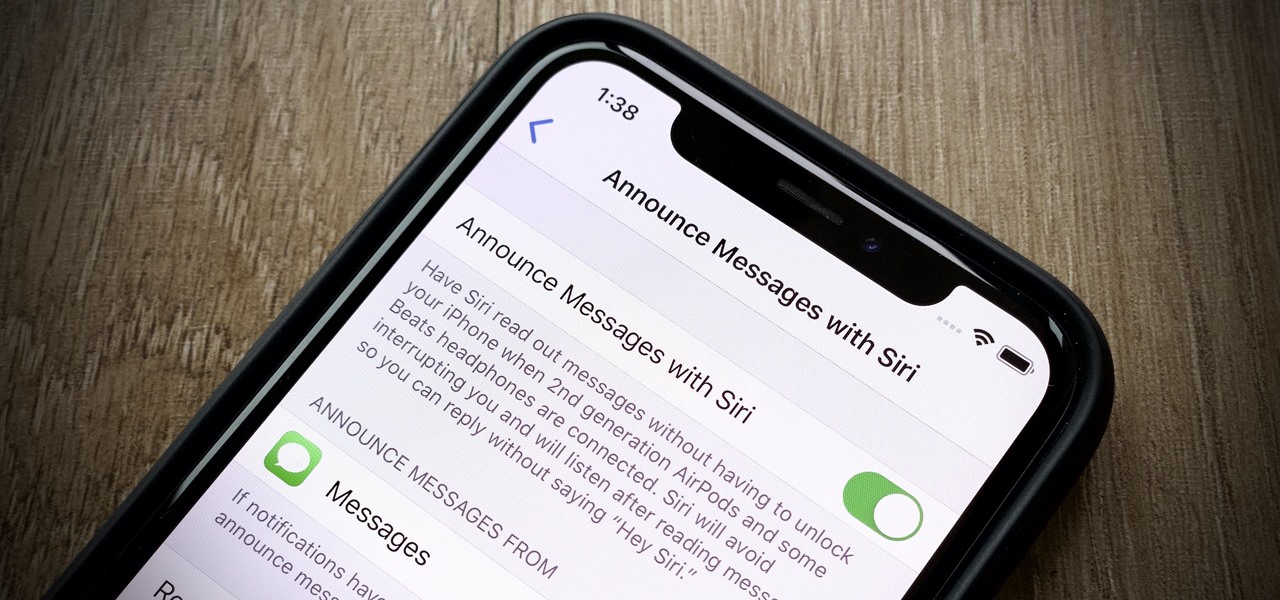
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

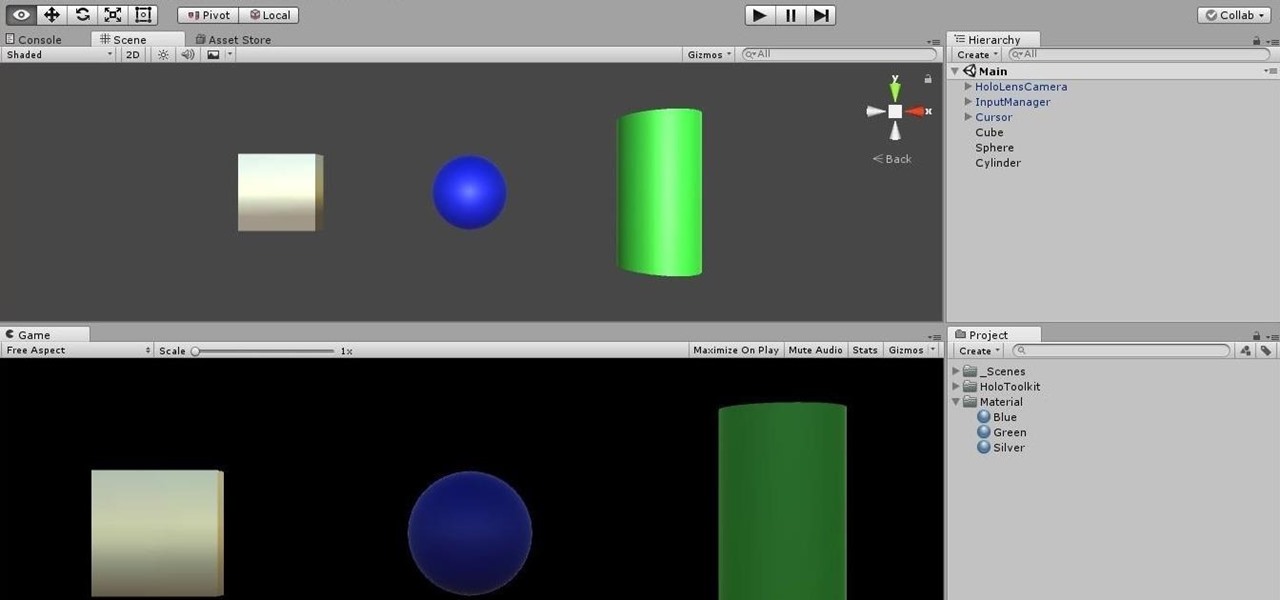
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.