As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Stereoblindness is an extremely unfortunate condition where someone cannot perceive depth correctly. Bruce Bridgeman was one such individual, having an eye condition which prevented him from developing functioning binocular vision. In essence, he was living in a "flat" world.

Magnetic ink is generally used by the banking industry to allow computers to read information off of a check, but that doesn't mean you can't have some fun with it. The guys over at openMaterials have figured out a great recipe for a DIY magnetic ink that you can use for an interesting art project—or just to mess around.

While it's easy to make fun of water with "electrolytes," there's actually some science behind it. Despite the name, electrolyte-enhanced water isn't all that high-tech, it mostly means that it's been infused with vitamins and minerals such as potassium and sodium, which are very helpful in preventing dehydration. Unfortunately, electrolyte water isn't especially cheap, and compared to the tap, it's downright expensive. Luckily, there's a few recipes out there that can help you mix your own e...

A minigame we built with redstone! Video: .

Keep you and your family safe by equipping your home to prevent home invasion. Discourage home invasions by being cautious and making a break-in more difficult. Have a plan in the case your home is invaded.

Holding breath underwater is an important part of learning to swim. Knowing how to hold breath underwater can prevent choking and drowning. Get expert tips and advice in this swimming video tutorial.

Hypothermia can be a real danger when swimming in very cold water. There are both emergency and non-emergency steps the swimmer can take to prevent hypothermia. Get expert tips and advice in this swimming video tutorial.

So, you're solving your Rubik's Cube, like the speedsolver you are, and all of a sudden... clink, its center cap falls off. What do you do now?

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

These videos show you how to use baking strips to make a better cake. Use caution when using baking strips, and watch your oven carefully.

Hub bearing assemblies are one of the most expensive things you could get fixed on your vehicle. And it's not an easy task to repair yourself if you're not a semi-professional mechanic. But with the help of this video, you'll learn the steps to changing hub bearing assemblies, from a licensed technician.

In this how-to video from projectink we are shown how to make a lamp out of a tequila bottle. There's no need to spend 100 bucks on a lamp when making your own is cheap and easy and fun. These are the supplies you'll need: A bottle (we're using a Jose Cuervo tequila bottle), a plastic bag, super glue, a hot glue gun (or you can use epoxy), a screwdriver, a lamp kit (you can get these at the hardware store for about 12 bucks), and a glass-cutting drill bit. For the glass-cutting bit, try and f...

Julie Goodnight guides you through how to safely mount and dismount a horse. First make sure you put the reigns up over the horses head. Keep the reigns in your hands so you always have control of your horse. Check the cinch on the saddle before putting your foot in the stirrup. Make sure the horses feet are square so it can properly brace when you go to mount. Stand to the front of the horse, facing the rear, so you can see the legs at all times. This will also discourage your horse from ste...

In this installment of Show Me the Curry, you'll learn how to make a delicious fresh fruit tart fit to rival any made for the Red Queen. For a detailed, step-by-step walkthrough of the recipé and instructions outlined below, watch this free video cooking lesson!

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

Rajma-Chawal is a combination that is ‘to-die-for’. The best rajma (kidney beans) and chawal (rice) can be had at the obscure stores alongside the highways all over North India. Watch this how to video to learn how to make an kidney been curry.

Learn how to do speed full sit ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

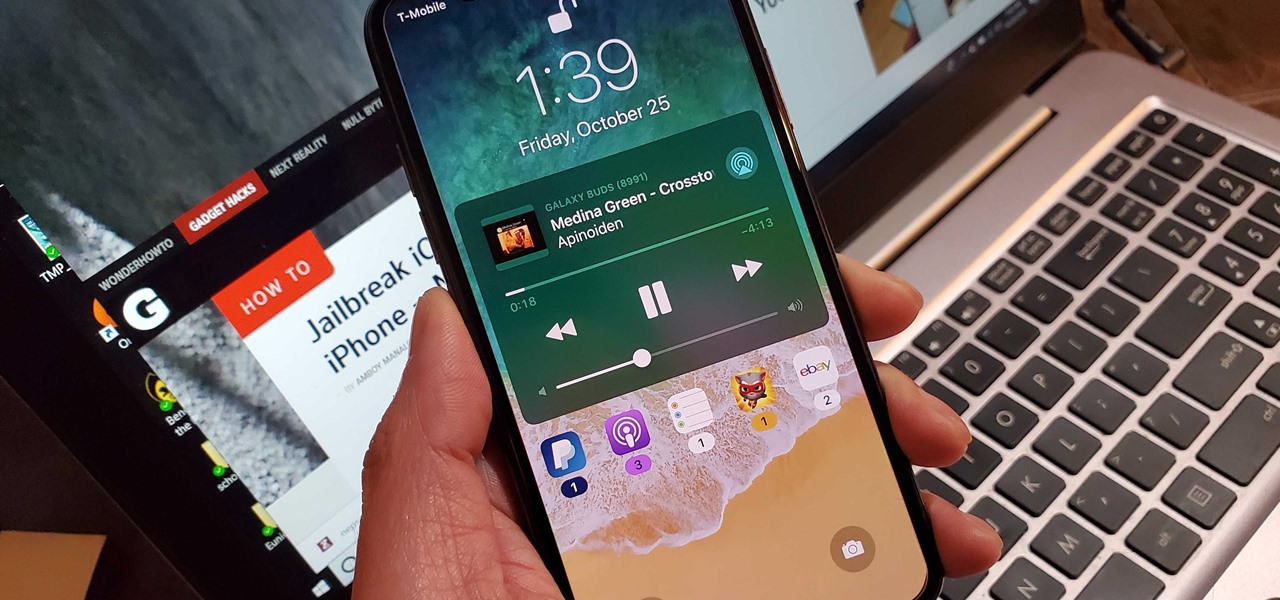
It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

In July 2017, LG announced a new smartphone lineup, the Q series. These devices focus on providing some flagship features at a more affordable cost — features such as an 18:9 1080p display. LG's goal here seems to be adding value for the more budget-conscious users, and in 2018, they've continued the series with the Q7.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.