Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.
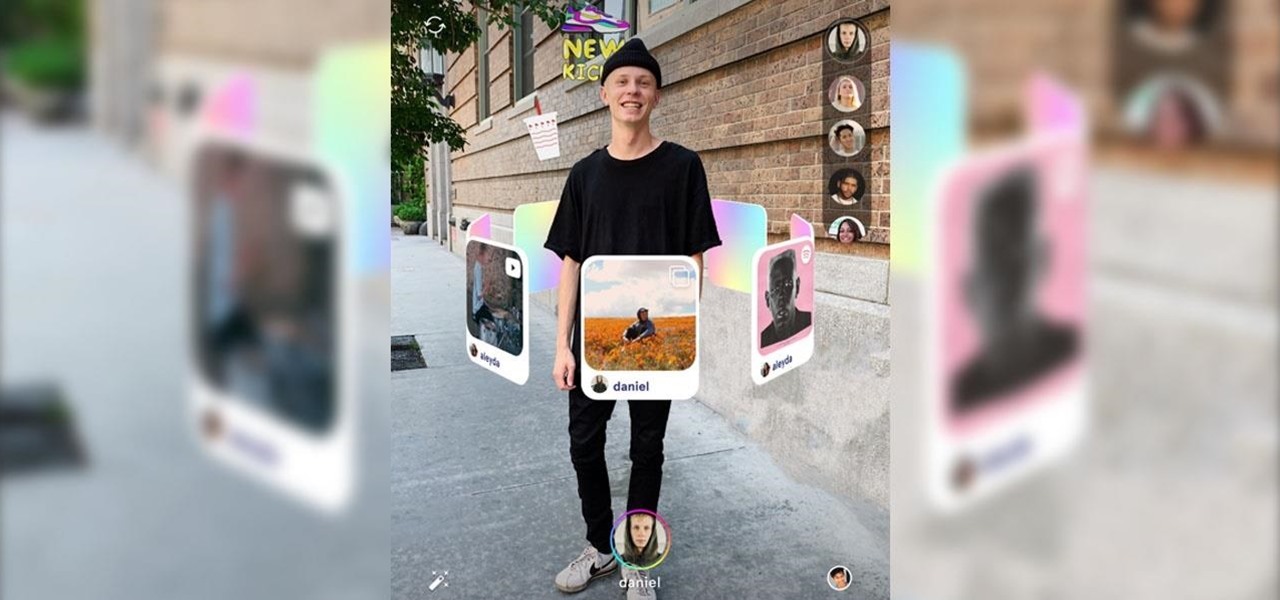
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

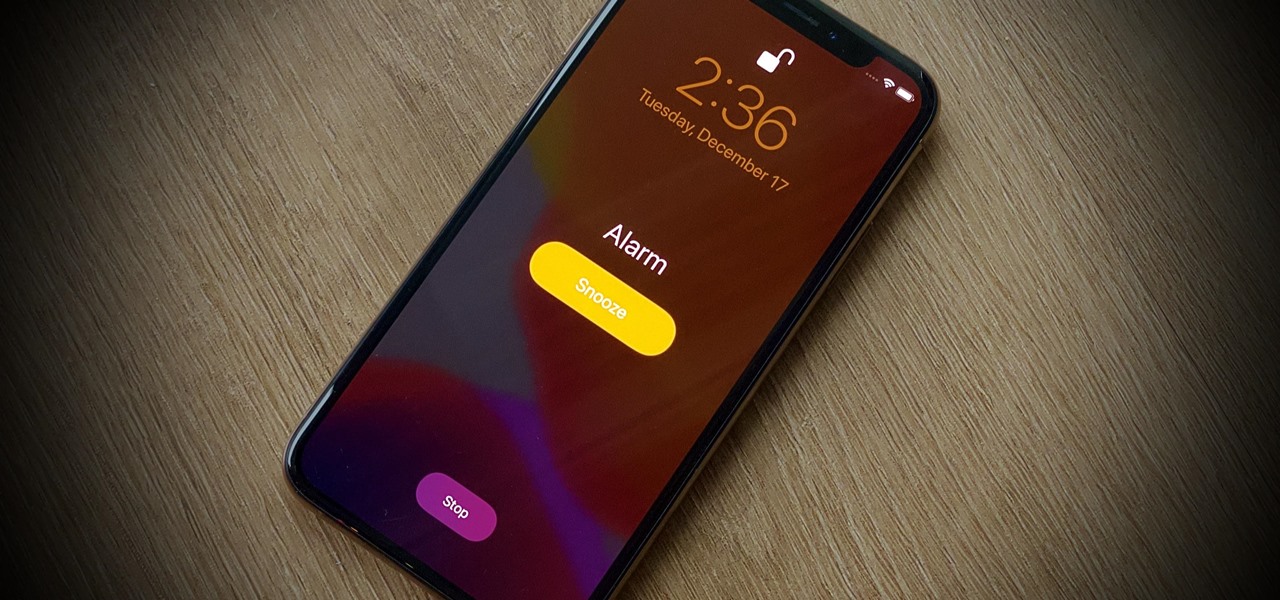
It happens to almost everyone. You wake up one morning, check your phone, and realize your alarm never went off. Now you're late to start the day, and you spend every night onward paranoid it'll happen again. But if you have an iPhone, there are two things you can check to make sure the alarm always goes off on schedule.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Those going on crazy off-road adventures, taking their inspiration from various SUV commercials, are likely to encounter many unexpected, all-terrain dangers.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

While most users are on iOS 13.1.2, you have the option to run something a bit newer. We're talking about beta testing, specifically iOS 13.2. Apple released the first developer and public betas for 13.2 last Thursday, Oct. 3. Now, the company is doing it all over again, with the release of iOS 13.2 developer beta 2.

The augmented reality space is brutal, and that means shifting directions quickly to meet whatever need the market demands.

In iOS 13, Safari has become even more powerful, especially when it comes to privacy. The browser will warn you when you create a weak password for a new account. Your history and synced tabs in iCloud are end-to-end encrypted now. And there are per-site settings that let you choose which domains can and can't have permission to use particular device hardware or sensors.

There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

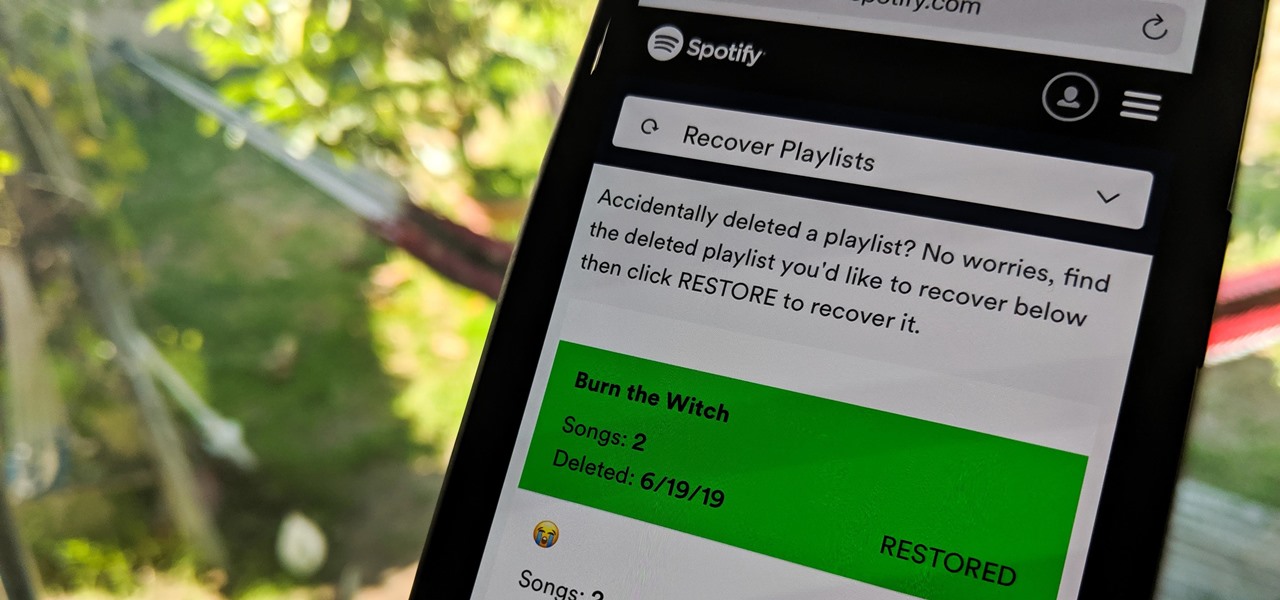
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

The long-awaited Dark Mode may have grabbed all the spotlight with iOS 13, but Apple has made subtle changes across the whole platform to make your iPhone even more user-friendly. A small option aimed at people who are sensitive to motion is one such example — a feature that can also be a godsend for the rest of us.

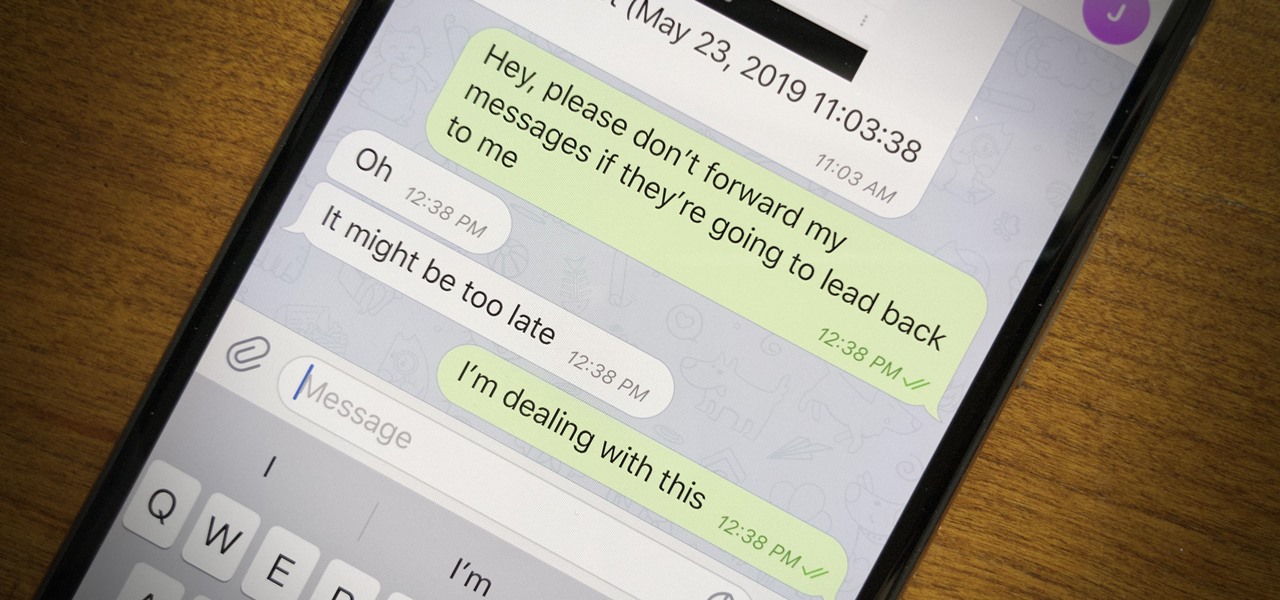
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Luckily, you can make your messages anonymous, so anyone receiving messages of yours that are forwarded won't be able to see you originally sent the message.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

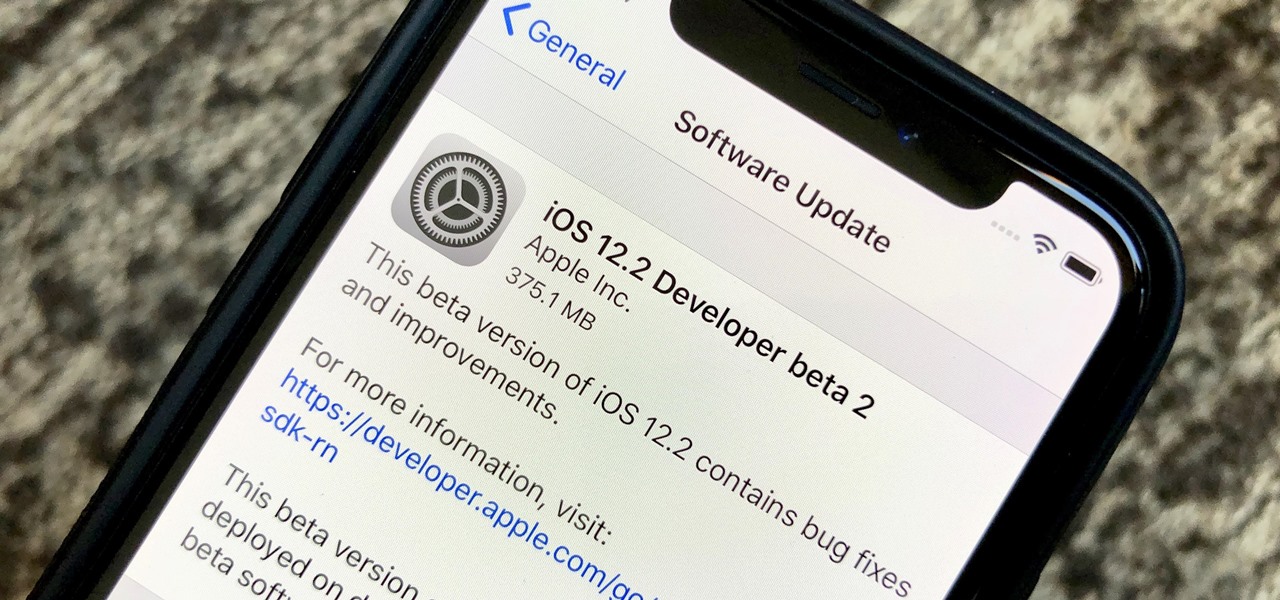
Apple just released the sixth beta release for iOS 12.2 today, Monday, March 18. Just as expected, the update to the developer version dropped just past 1 p.m. EDT (10 a.m. PDT), and comes with new changes and features from iOS 12.2 beta 5 and beyond, including a new warranty status in the "About" page in Settings.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

When you don't want certain friends viewing your account or just need to take a break from social media, Instagram lets you do so. While you can completely delete your Instagram account, then start over when you're ready again, it makes much more sense to just disable your account temporarily. Doing so will hide your profile, photos, comments, and likes from everyone, including your friends.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.

On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

One day after the official release of iOS 12.1.3, Apple released the first beta for iOS 12.2 to developers. The software appears to be the first in some time to be a major update. Apple's last beta cycles included 12.1.2 and 12.1.3, incremental updates to iOS 12.1. Now, we've entered a new version of iOS 12 entirely, hopeful for new features.

These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

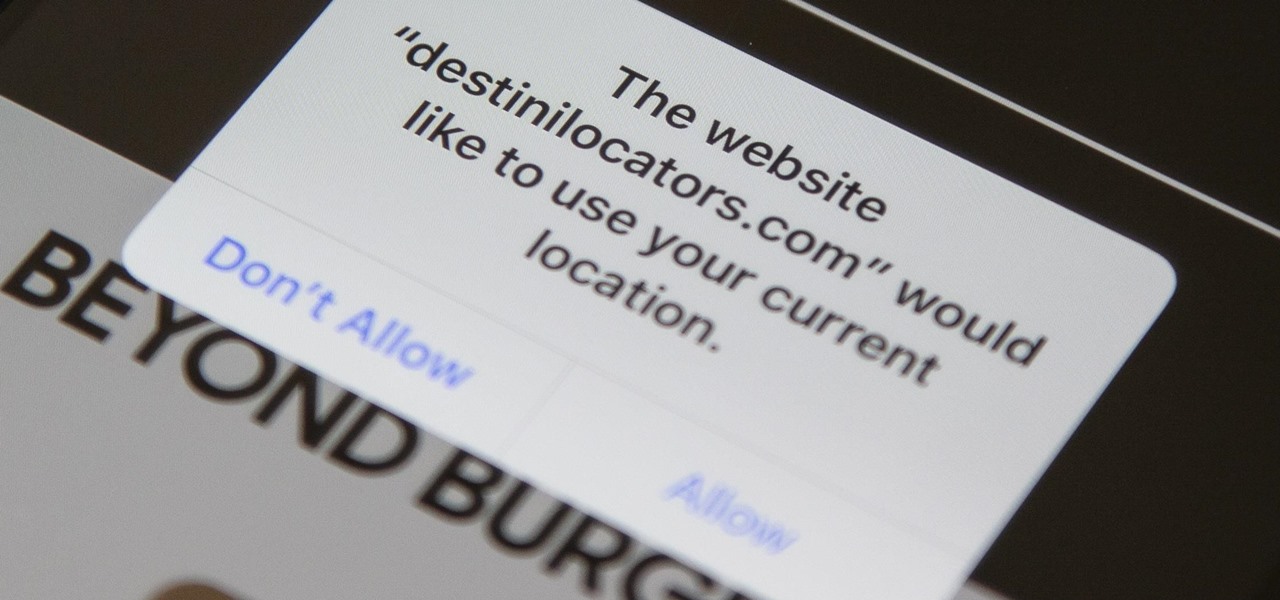
Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's what the iPhone XS Max brings to the table.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

With every new Android update, hidden features are lurking under the surface. Google hides these options to prevent unnecessary tinkering by average users, leaving them in place for power users to discover. These secrets range from silly to really useful, with the latter opening up new ways to manage your phone.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.