Pick up any iPhone with a Home button, and you'll notice something peculiar when compared to your iPhone with Face ID. If you press the Side button (aka Sleep/Wake) on the Home button model, it sleeps immediately. When you press the Side button your Face ID model, it lags a bit or a whole lot. What's going on here, and can it be fixed?

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.
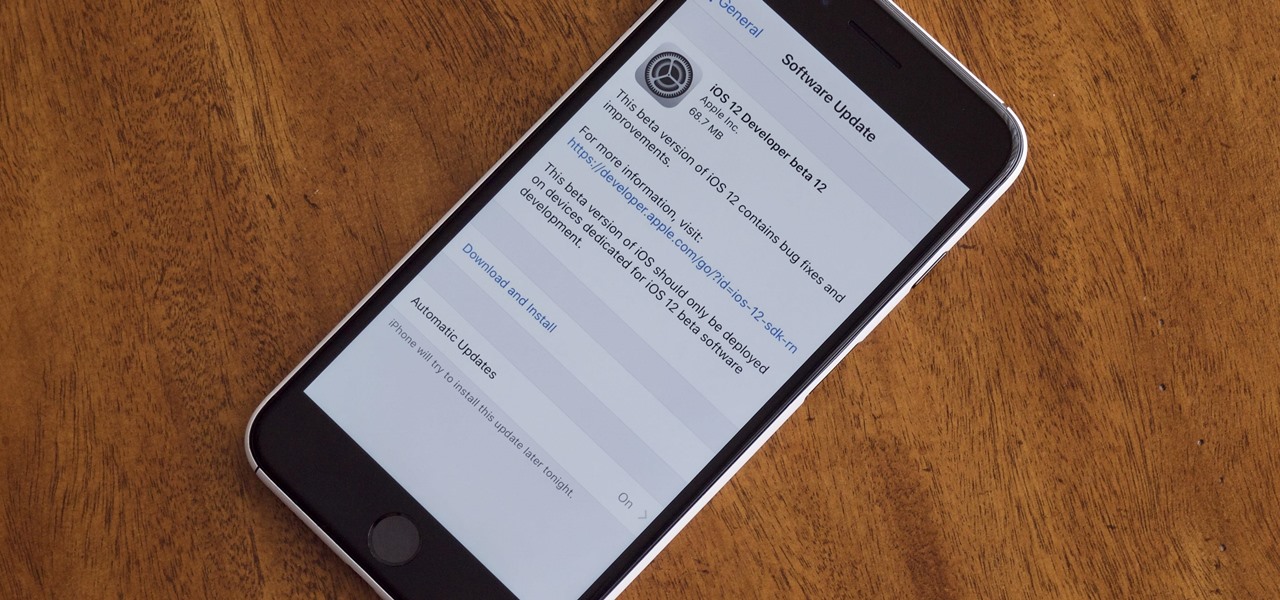
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

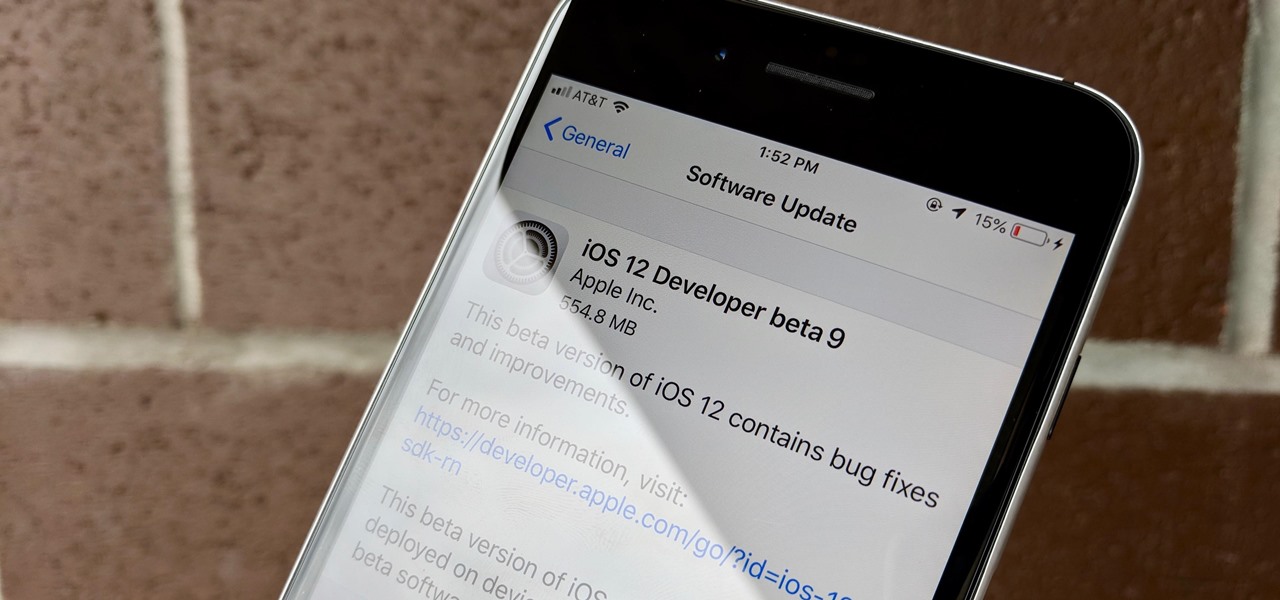
Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

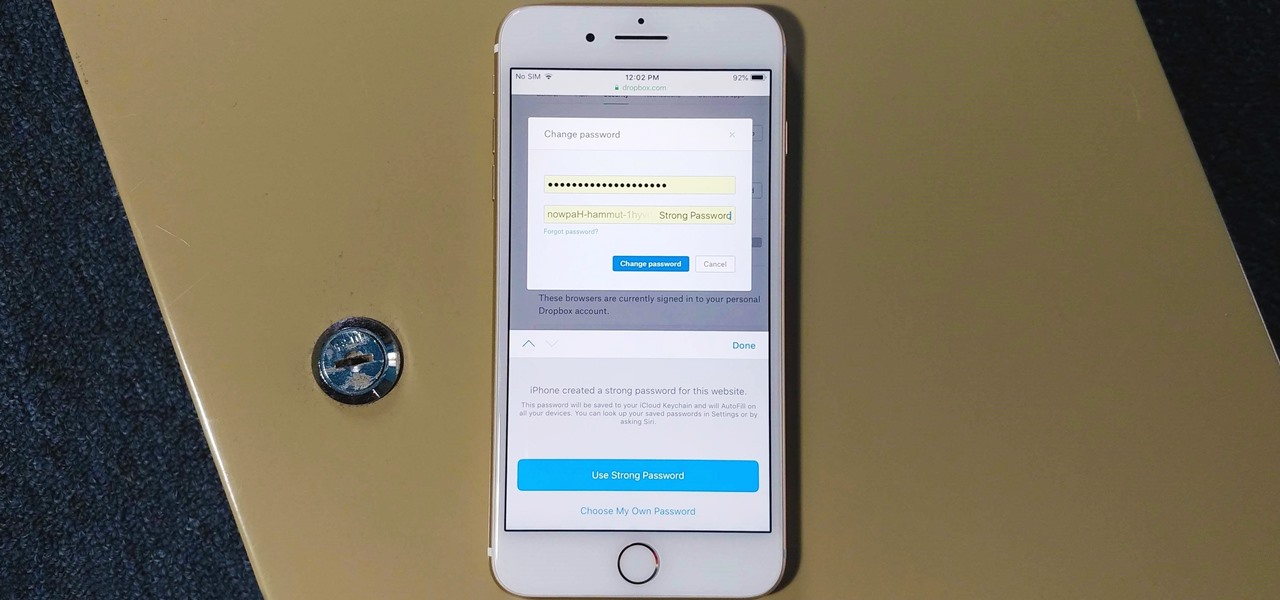
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

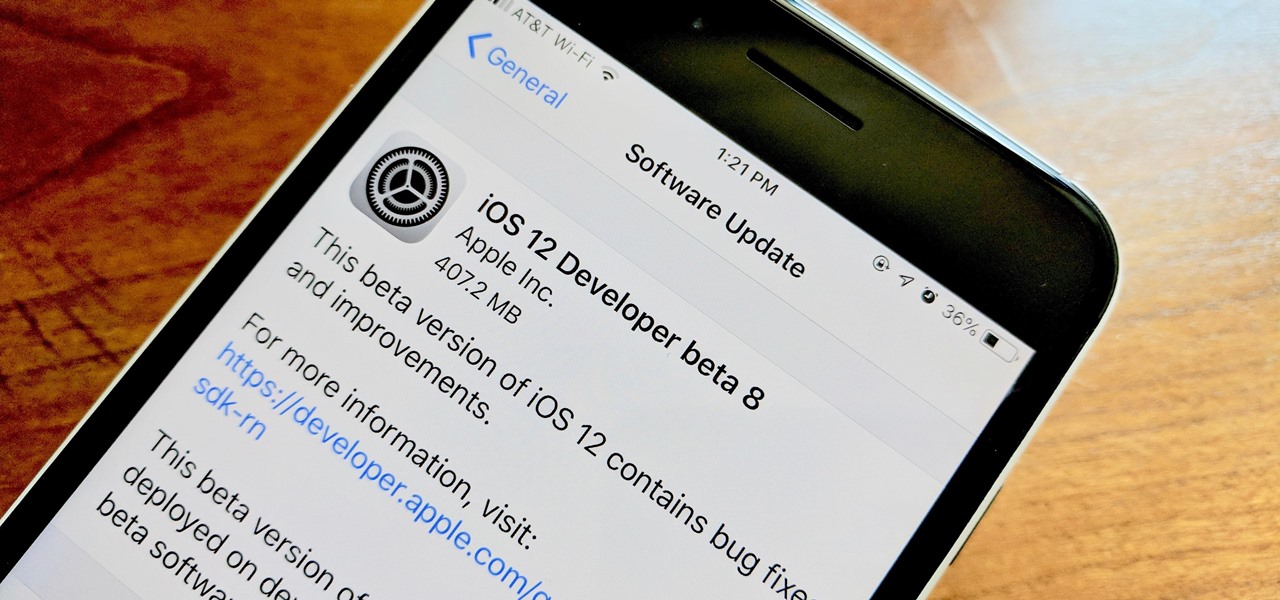
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

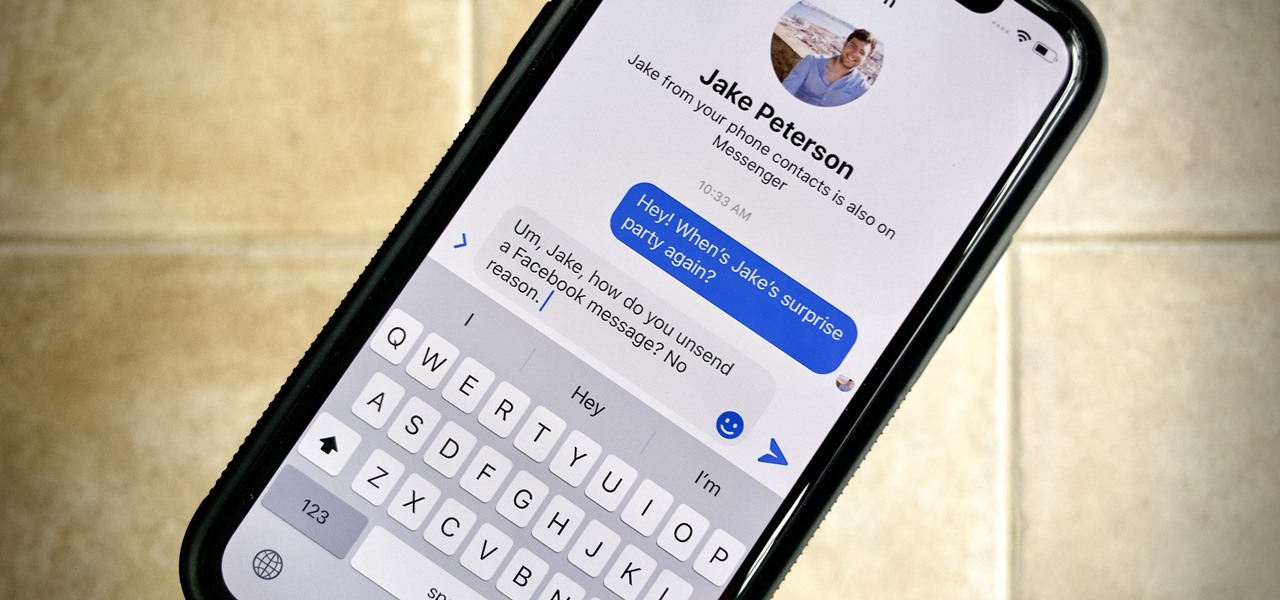
How many times have you sent a message on Facebook Messenger that you immediately wanted to take back? Most email services have an unsend option, as well as Instagram Direct, and Messenger has caught on to this convenience with a take-back button for any chat you're in — even in groups. Plus, you can also remove other people's messages.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

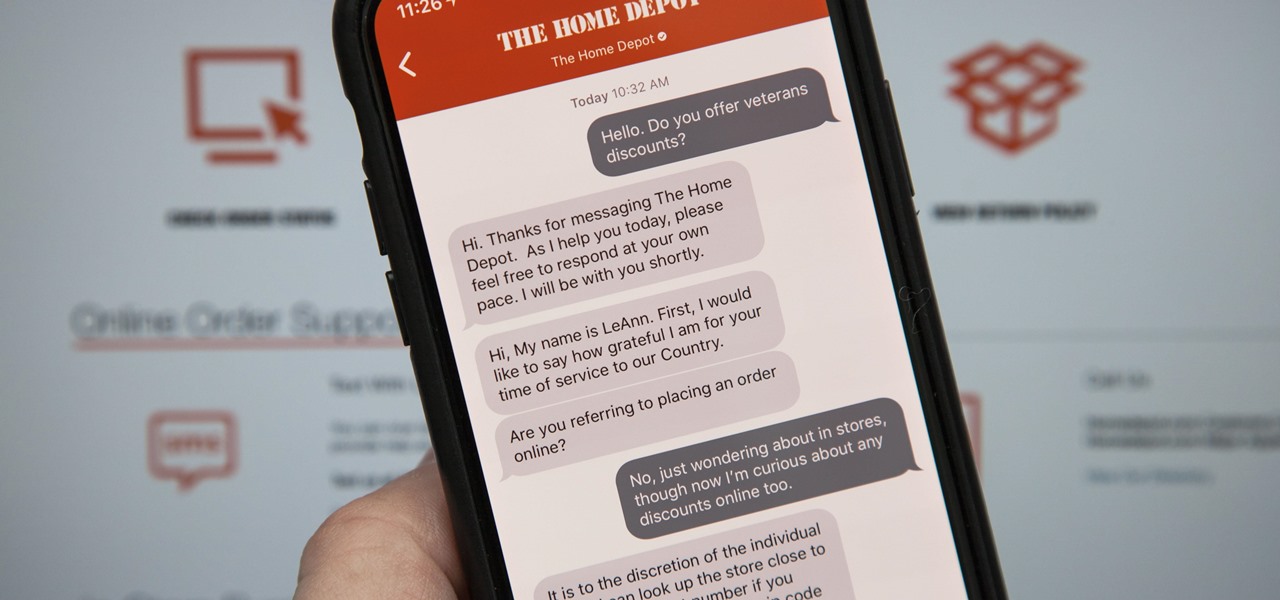
Apple first announced Business Chat, a new way for customers to communicate with companies, at WWDC 2017. While Business Chat did not arrive with the initial release of iOS 11, Apple pushed it out in iOS 11.3 so companies can offer customer service in a whole new way, and it works pretty much the same in iOS 12 and higher as it did back then.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

Whether you mean to or not, taking burst photos is super easy on the iPhone. In the Camera app, just compose your photo, tap-and-hold the shutter button, and watch the number of pics go up and up until you take your finger off the screen. However, finding that one special keeper out of all of them in the Photos app isn't as intuitive as taking them in the first place.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Preserving battery life has become one of the biggest problems for the average user. Whether you're on Android or iPhone, your battery is probably a massive concern. While there are a ton of battery-saving tips out there, they mainly rely on you manually performing actions yourself. This isn't the case if you use IFTTT to take care of your battery automatically.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Android users have had access to live wallpapers since the Eclair days, but some newer apps have made this feature even more useful. Now, you have the ability to use GIFs as your wallpaper, and through the marvels of modern technology, you can even set a video as your home screen and lock screen background.