For me, the worst thing about makeup has always been taking it off. It's always that one last thing you have to do before you go to bed, and if you don't, you instantly regret it when you wake up. When you're tired, makeup removing wipes are a godsend because they're so quick.
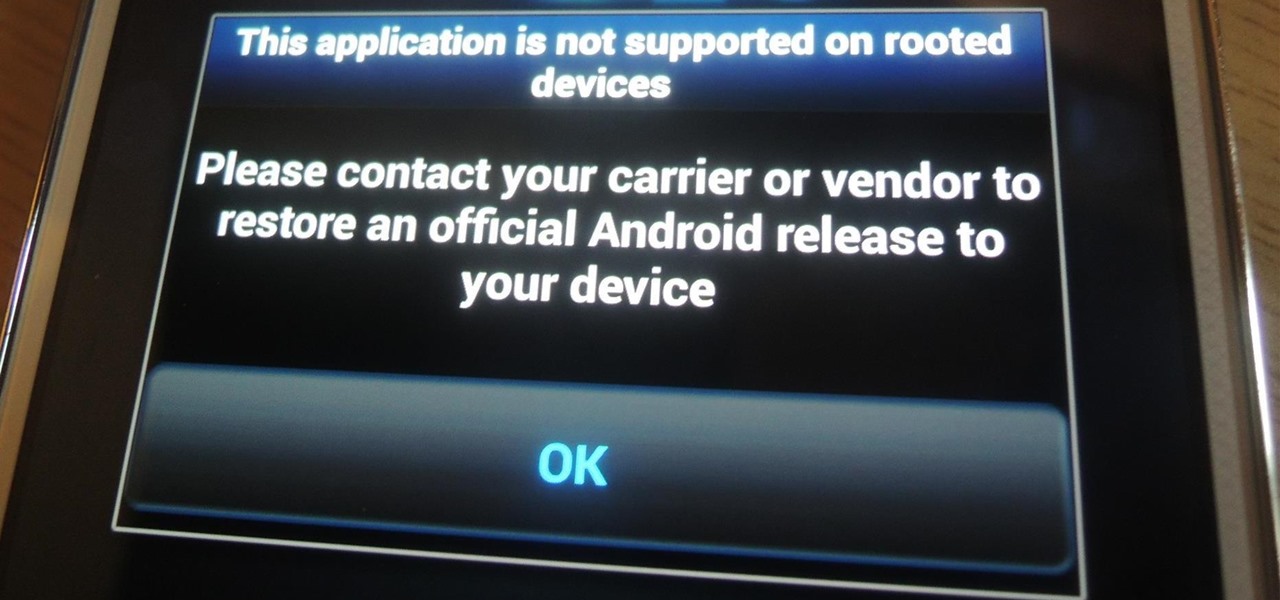
As a preventative measure against exploitation, certain Android applications won't work if your device is rooted. Opening one of these apps that detects root will typically end up with a warning and an inability to access its features, like in the picture below. AS IF!

Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry.

Headphone cords are one of those things we all deal with because it beats the alternative (no music). But they can be so obnoxious—they're always getting caught on things, and they seem to be perpetually tangled. If you have ear buds, you can make a simple a cord container to keep them organized, but over-ear headphones are a little more tricky.

Just about everyone I know has broken a phone at least once in their life. It's almost inevitable considering we carry them everywhere we go, but that doesn't make it any less irritating. A cracked screen is difficult to read and can actually be a little dangerous if there are loose pieces of glass. Simon, a designer and producer over at Sugru, came up with a quick fix that'll help hold your screen together in the meantime until you can get it fixed properly. He figured out that a paper-thin ...

Beach Effect Nail Art Design Tutorial For Beginners!!!!! Sunset the palm trees and the birds..perfect for canvas. Well why not to try it out on nails. This perfect picture has been produce on the nails in a very simple and easy way. Just watch the tutorial to know about this !! Step 1: Apply Base Color

The cord on your headphones is usually more enemy than friend. While they obviously need it to function, a tangled or unnecessarily long cord can wreak havoc on your sanity. Personally, I've broken at least two pairs of headphones by tripping over the cord and yanking the jack right off of the wiring. There is a fix for that, but you can prevent the problem altogether by organizing your cords. There are plenty of ways to wrap a cord so it won't get tangled, but you still have to unwrap it if ...

Guacamole is one of those things that tastes far better than it looks. To someone who isn't a huge fan of avocados, guacamole's texture can appear slimy, and on top of that, its chunky green appearance brings up visions of Nickelodeon-style slime. What's even worse is the browning that occurs in just a few minutes of being exposed to air, and it's even worse if there's salt in it. I love guacamole, but that brown is enough to turn off even the most enthusiastic connoisseur. Few things are mor...

Electronic devices seem to have an uncanny ability to make noise at the worst possible times. It's always during an important meeting, a quiet study session at the library, or a biology final that your laptop or smartphone decides to play some obnoxious or embarrassing sound.

There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should.

Video: . The macho and easy way to make golden eggs. How to scramble eggs inside their shell useing a drill. AKA Fuwatoro Eggs.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

Most of the time, if you're actually using your computer, it won't just go to sleep on you. But when you're reading a long article or watching a video and don't move the mouse or use the keyboard for a while, the screen automatically dims or goes into sleep mode.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

Did you know that the average cost to make a penny is about 2.4 cents?!? That's why the Obama administration asked Congress earlier this year for permission to change the metals in the penny, hoping to get the cost back down where it makes sense.

Hello! Today I would like to introduce a simple tiny braid - so called the small wrap up. I recommend it to every person who wants to prevent the hair from falling onto the face. It is suitable especially for the people who have long or medium sized hair and very delicate skin. And for all who just want to quickly bind together some hair.

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Magnetic ink is generally used by the banking industry to allow computers to read information off of a check, but that doesn't mean you can't have some fun with it. The guys over at openMaterials have figured out a great recipe for a DIY magnetic ink that you can use for an interesting art project—or just to mess around.

A minigame we built with redstone! Video: .

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

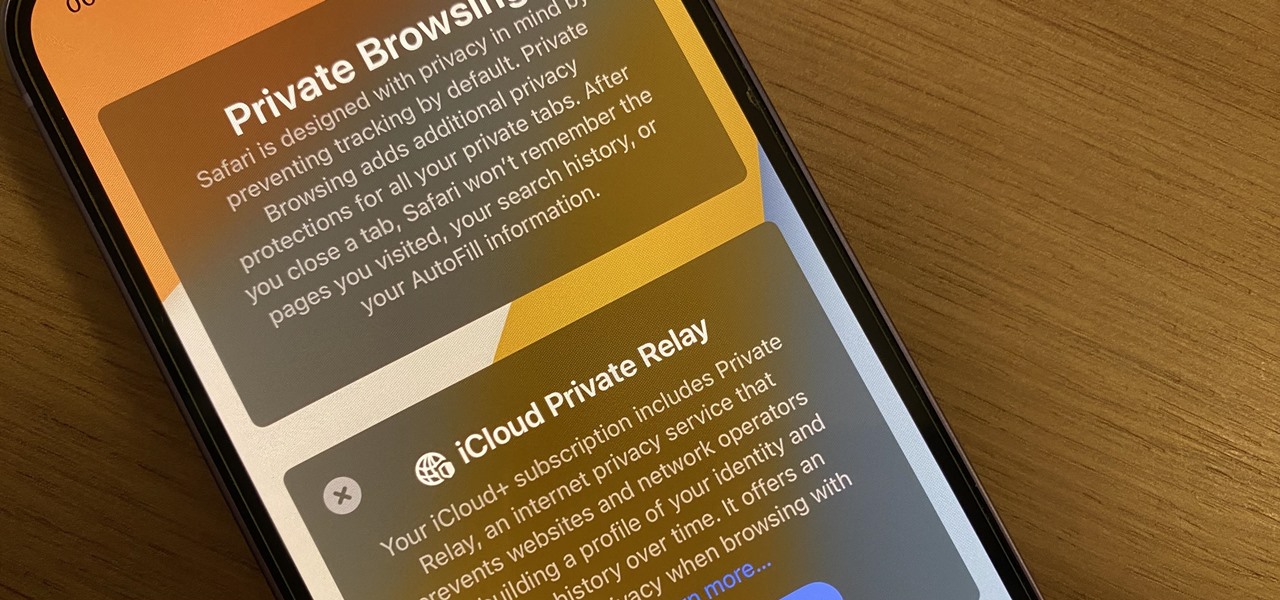
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Apple just released iOS 14.1 for iPhone today, Tuesday, Oct. 20. This update first hit iPhones one week ago, but not for long — Apple pulled the release almost immediately, later seeding it to iOS developers only as a GM (golden master) release.

For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. But for others, it can be annoying when it appears unexpectedly all of the time, and there's a way to stop it.

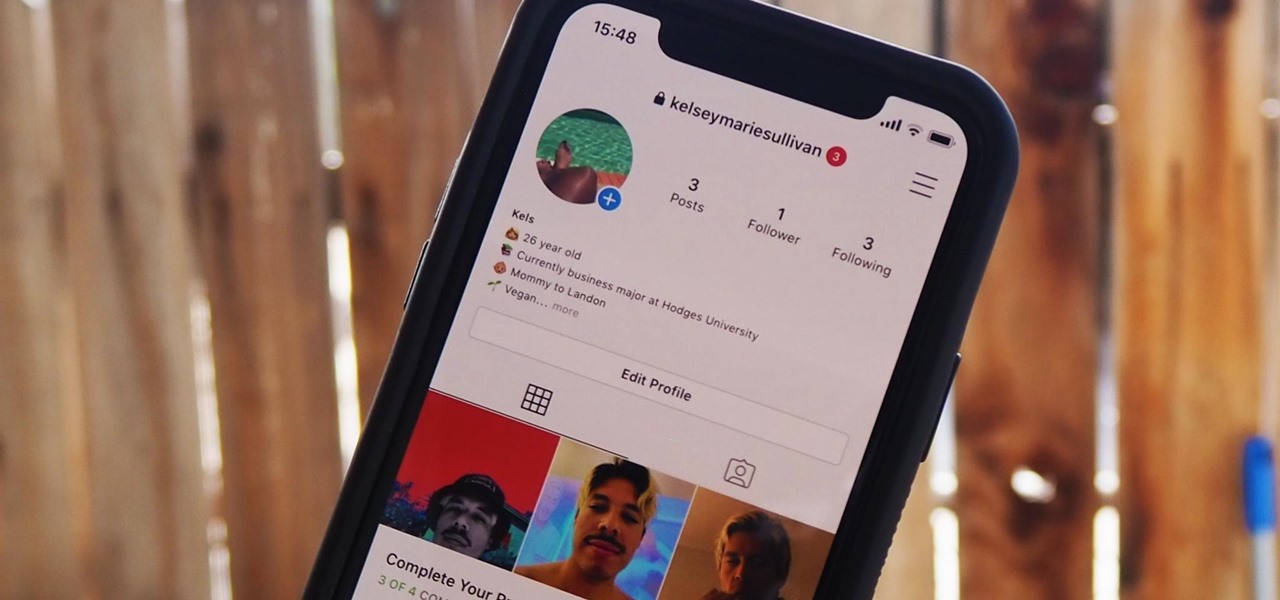
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.