
Hacking macOS: How to Create an Undetectable Payload
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.


Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's what the iPhone XS Max brings to the table.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.
With every new Android update, hidden features are lurking under the surface. Google hides these options to prevent unnecessary tinkering by average users, leaving them in place for power users to discover. These secrets range from silly to really useful, with the latter opening up new ways to manage your phone.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

I don't know about you, but nothing is more annoying than when my phone hits 15% and I'm nowhere near a charger. Not just because I know my phone will die soon, but until I reach a charger, I have to deal with the annoying low battery notification and LED light. Well, with Android 9.0 Pie, we finally can escape this.

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.
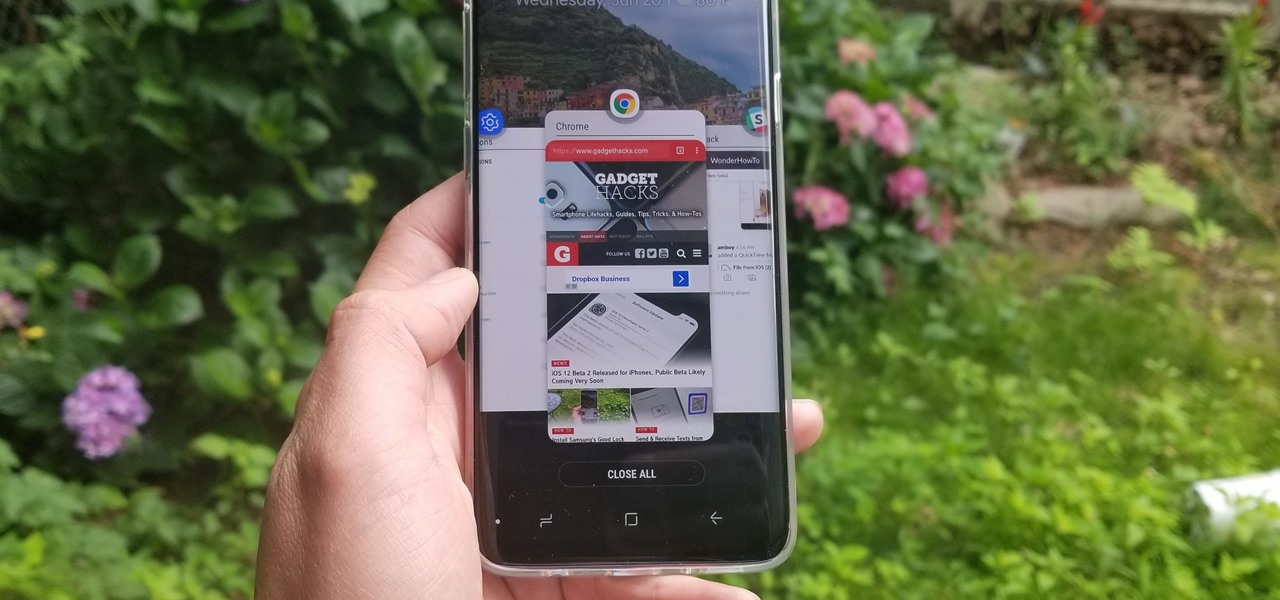
A revamped Recent Apps overview is one of the most significant changes set to arrive with Android P when it touches down later this year. Incredibly, Samsung has beaten Google to the punch, and has made this feature available for all its Oreo-based Galaxy handsets courtesy of its Good Locks app.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.
Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.
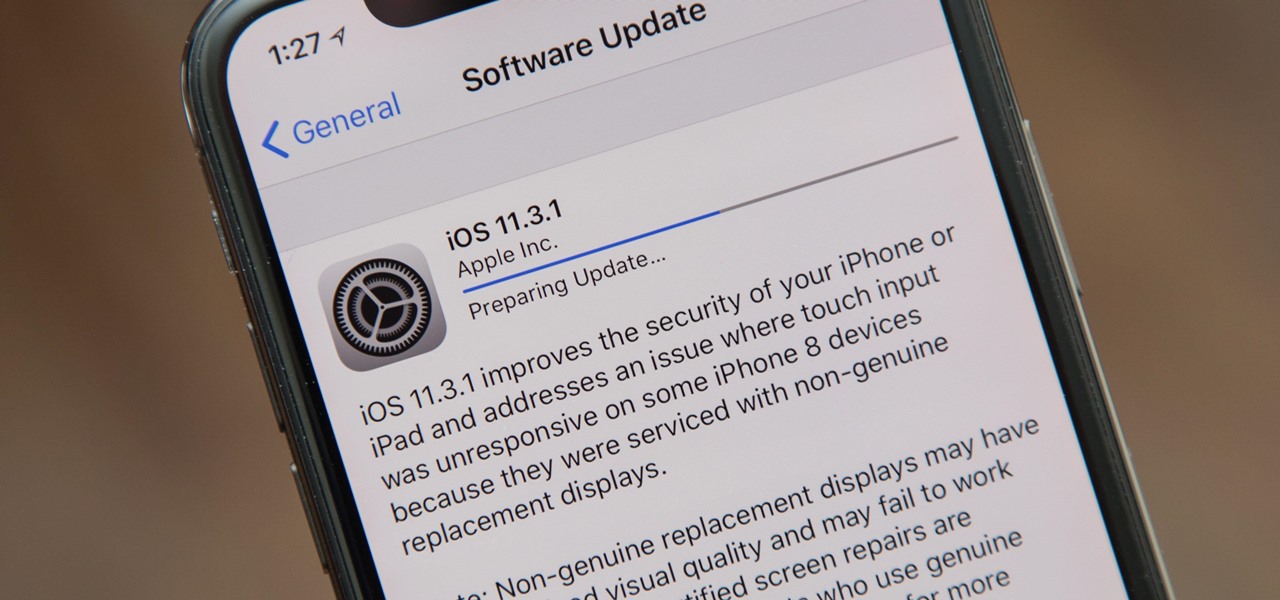
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

If you've unlocked your iPhone lately and noticed some apps aren't fully installed anymore, you're not alone. After updating my device recently to a newer version of iOS 11, I didn't immediately understand what caused a few of my games to uninstall themselves. It turns out, there's a simple setting that explains what's going on.

Even though smartphone audio quality has improved in recent years, the tiny built-in speakers aren't always loud enough. But if you want to turn the volume up to 11, all you need is a few household items to make a rig that will amplify your phone's speakers throughout the whole house.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

All those early prototype images Magic Leap is so fond of showing off are great, but they rank a far second when compared to a new set of images just revealed by Microsoft in relation to the HoloLens.
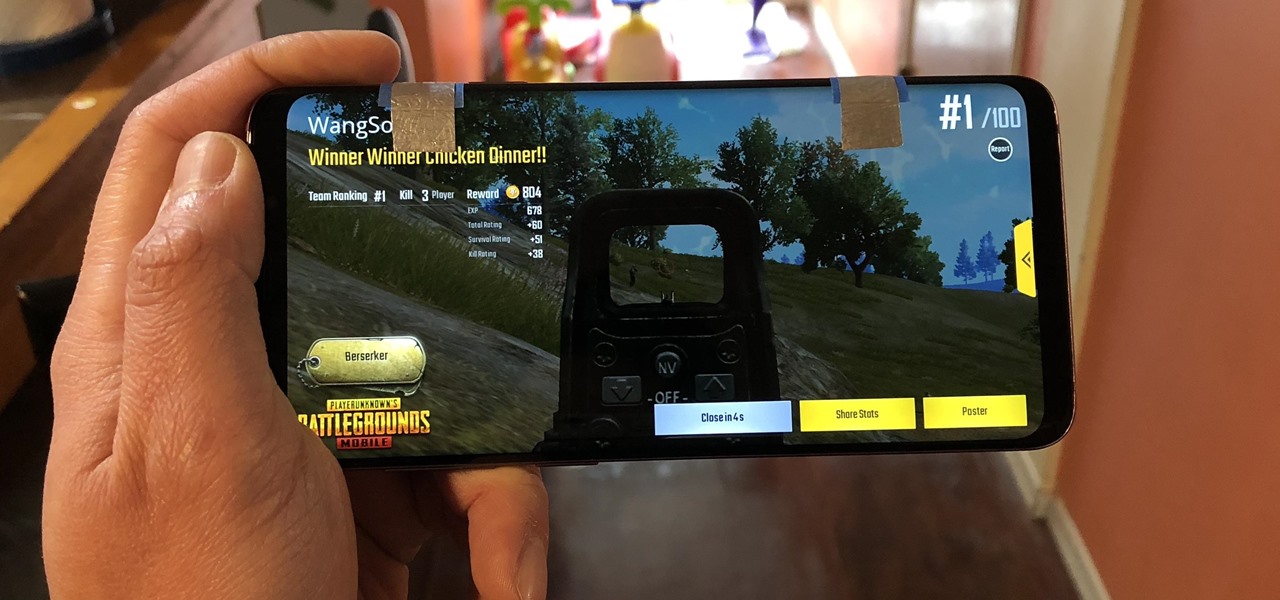
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

While it may not be an obvious feature, Apple actually built a way into iOS that lets you hide specific pictures and videos in the Photos app that you want to keep on the down-low, for your eyes only. If you show off your photos a lot or stream slideshows to your TV, this is a great way to keep less appealing content private.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Before, the only way to really tell how your iPhone's lithium-ion battery was performing was to use tools such as Geekbench and Battery Life, but now Apple has included some quick battery health checks right into iOS 11.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
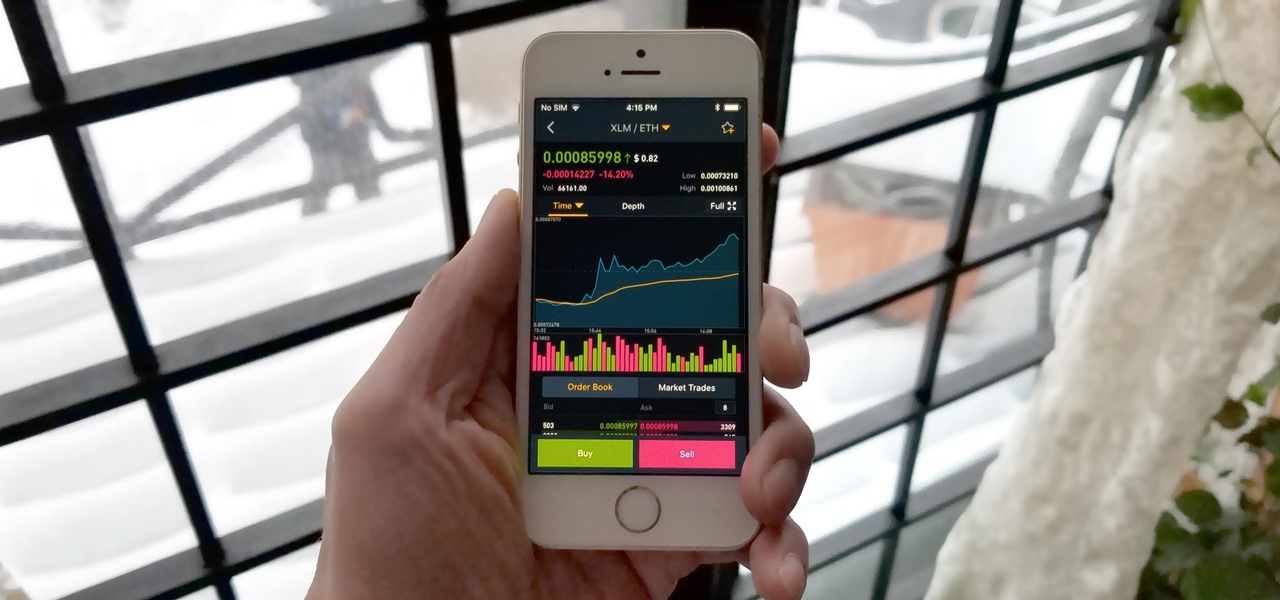
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.
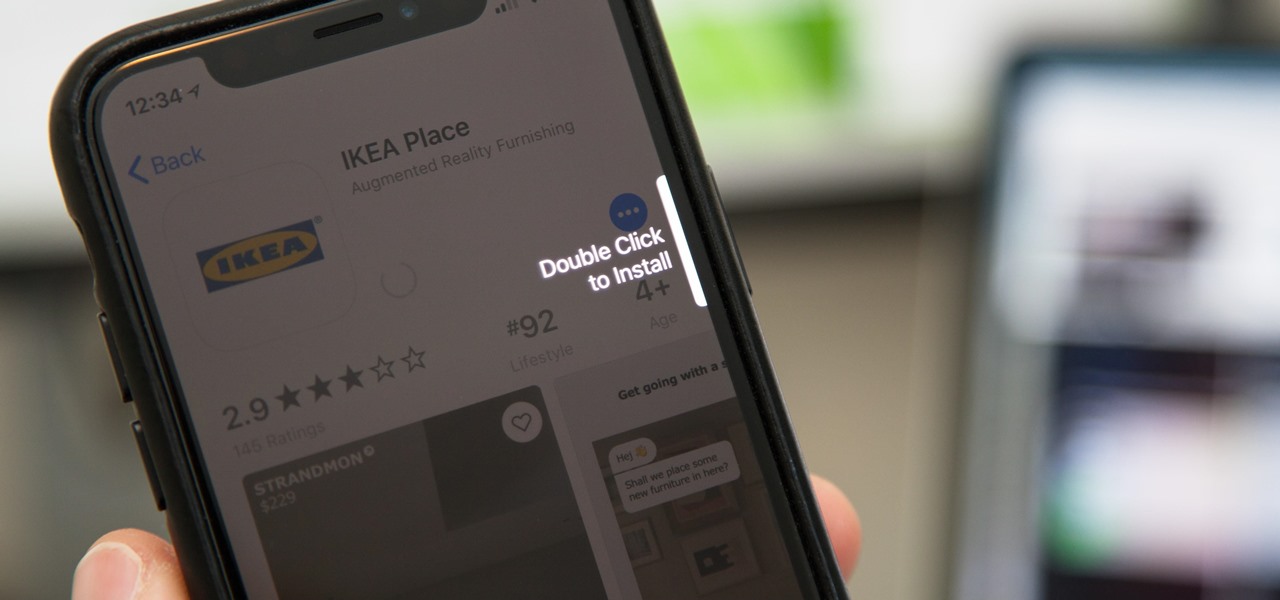
If you used Touch ID on an iPhone before, all you had to do to install apps and games from the App Store was rest your fingertip on the Home button. On the iPhone X, there's Face ID instead, and Apple has included on-screen instructions to help everyone adjust to the lack of Home button. Still, those instructions may not be working for you, but the solution is as simple as a misinterpretation.

A new stories archive feature appeared in the version 25 update for Instagram on both Android and iOS. This means you no longer need to save stories to your phone for later viewing, if you like doing that, but it also means all those stories are saved to your Instagram account whether you want them to be or not.

Whether inappropriate or unimportant, some emails don't need to be viewed at a certain times of the day. For example, you might not want to see any personal emails during work hours. By default, Gmail will notify you of all emails that hit your inbox, but fortunately, there's a feature that can automatically hide certain emails and prevent distracting notifications.
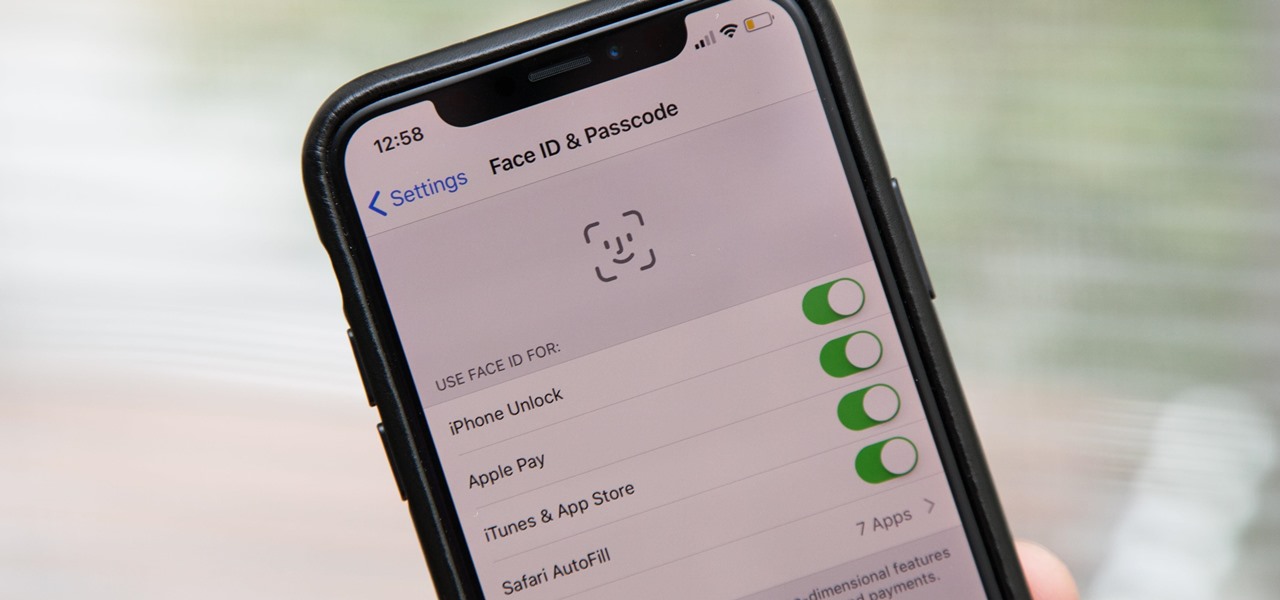
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

If you're following the classic Halloween playbook closely, you've already got a costume or three picked out, you've binged-watched your favorite horror movies, and you've likely visited a haunted house. But it's 2017, so how about trying something new, like a haunted house that's not actually there?
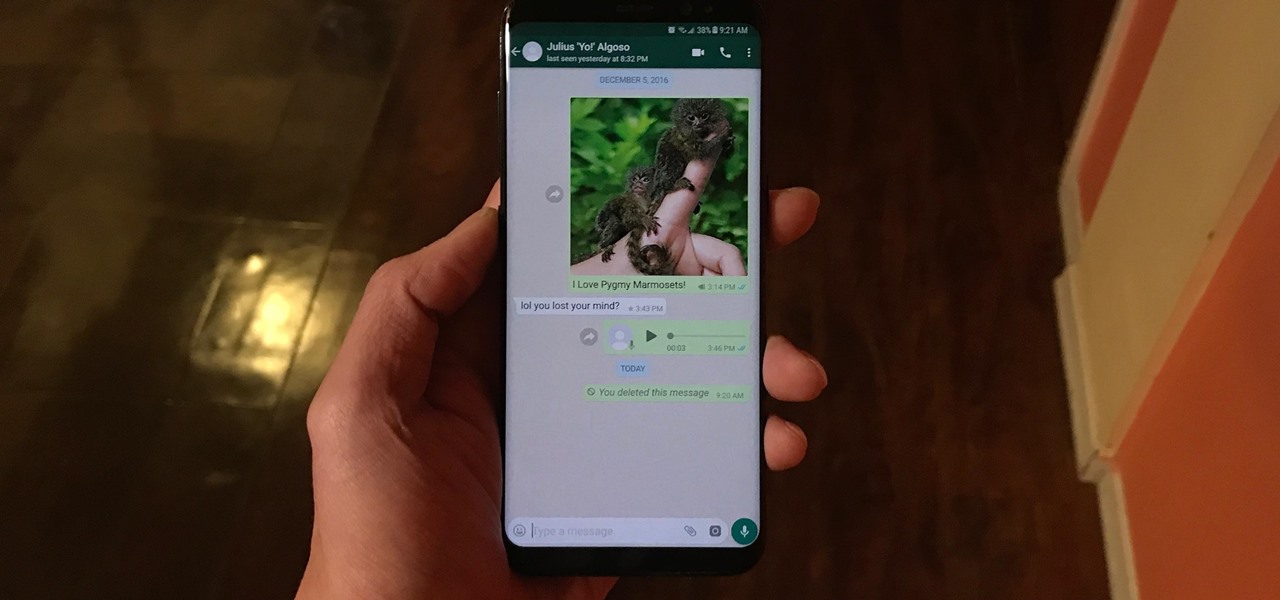
We've all been guilty of sending messages that we instantly regret — be it a moment of anger or plain old drunk texting. More often than not, these silly texts result in unnecessary headaches for both you and your contact. Thankfully, WhatsApp has finally tackled this age-old problem by giving us the ability to prevent drama before it even gets started.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.