Long gone are the days when you needed a fancy recording contract to write and distribute a smash hit. Thanks to a growing number of increasingly powerful and affordable music production platforms, it's now entirely possible to create pro-level audio tracks and even accompanying videos in the comfort of your own home with little more than a laptop and a pair of headphones.

It can feel hard to find time for just about anything these days. But if you really sit down and think about it, you likely have a little more free time in your day than you might actually imagine. The average person has about 4.5 hours of total leisure time over the course of a week.

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

Frequent readers of Null Byte are no strangers to the basic elements of app and web development. Whether you're a seasoned programmer who works extensively on front-end designs or an aspiring app-builder who's working on expanding your portfolio, you're likely familiar with at least a few go-to programming languages and platforms that are popular within your field.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

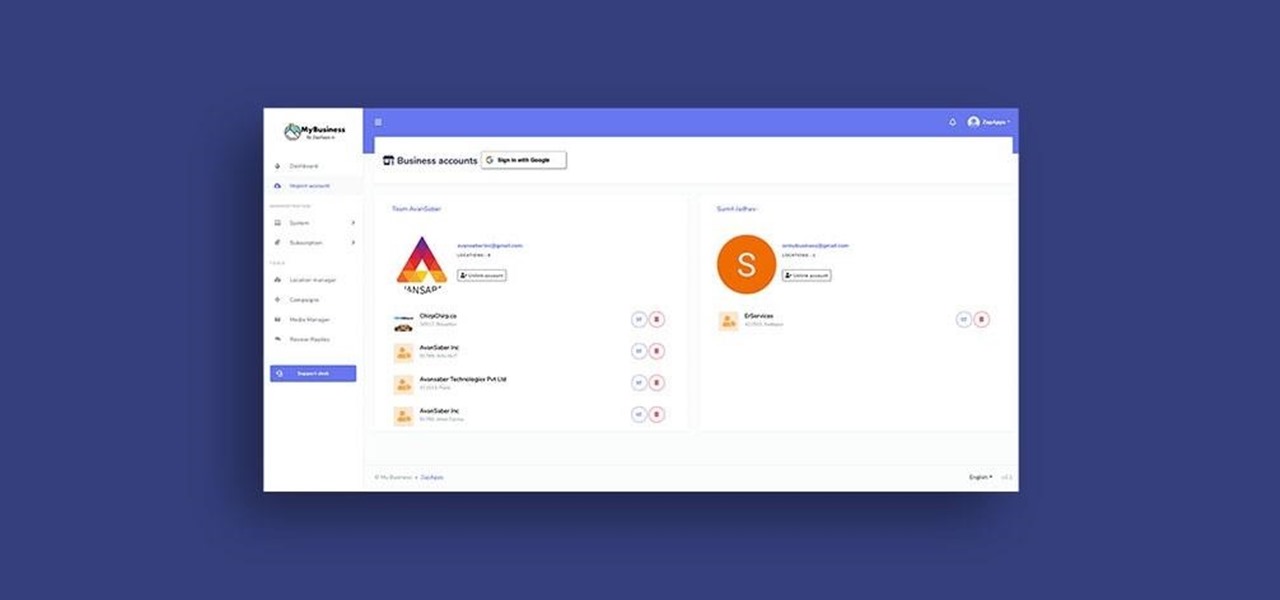
Google My Business lets you connect with customers across Google Search and Maps through a unique business profile. The web app allows you to connect and chat with customers in real-time and provides rich analytics to help you manage and grow your company.

Anyone looking to have a complete set of design tools at their fingertips needs to look no further than Adobe's Creative Cloud. This suite of applications is the go-to platform for creative software and is, in many ways, a must-know in fields like graphic design, video editing, and photography.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential.

We all know how hard it can be to stay productive, especially when working from home. There are many distractions throughout our day. Organizing your workflow is necessary for getting anything done.

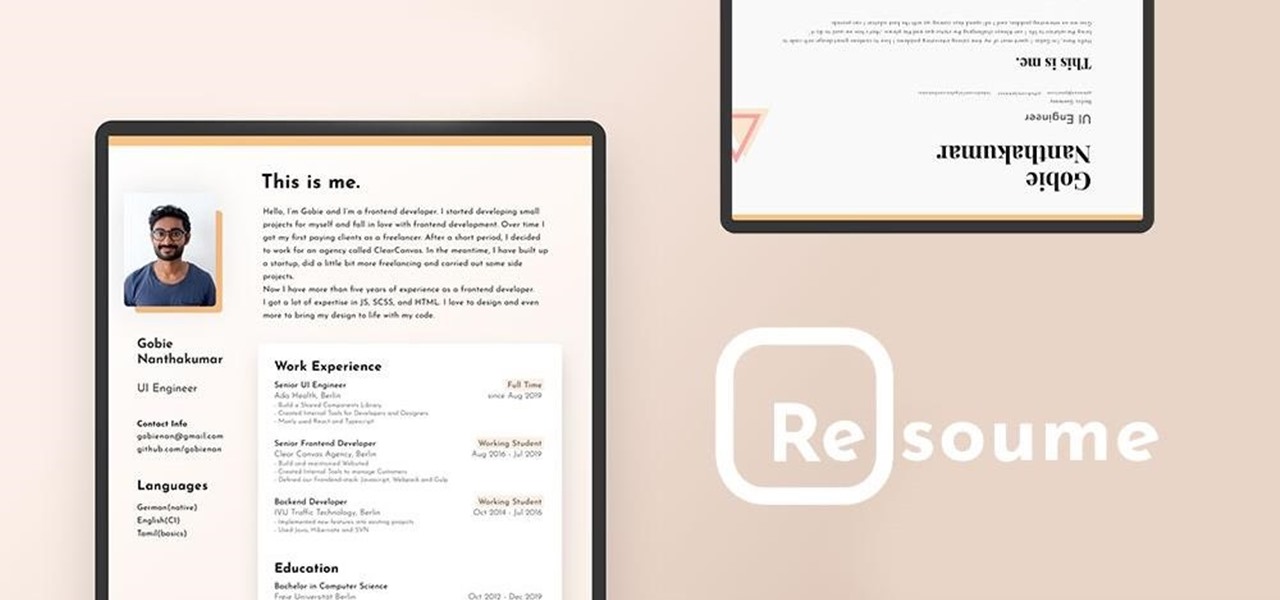
While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.

Wordpress is one of the world's most-loved content management systems (CMS). The user-friendly interface and ease of use have made this open-source system a no-brainer for millions of people. Over one-quarter of the top 10 million websites on the planet use Wordpress.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

As one of the world's largest and most powerful cloud computing platforms, Salesforce is used by countless companies to manage customer relations, deliver services, and innovate solutions to complex problems.

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

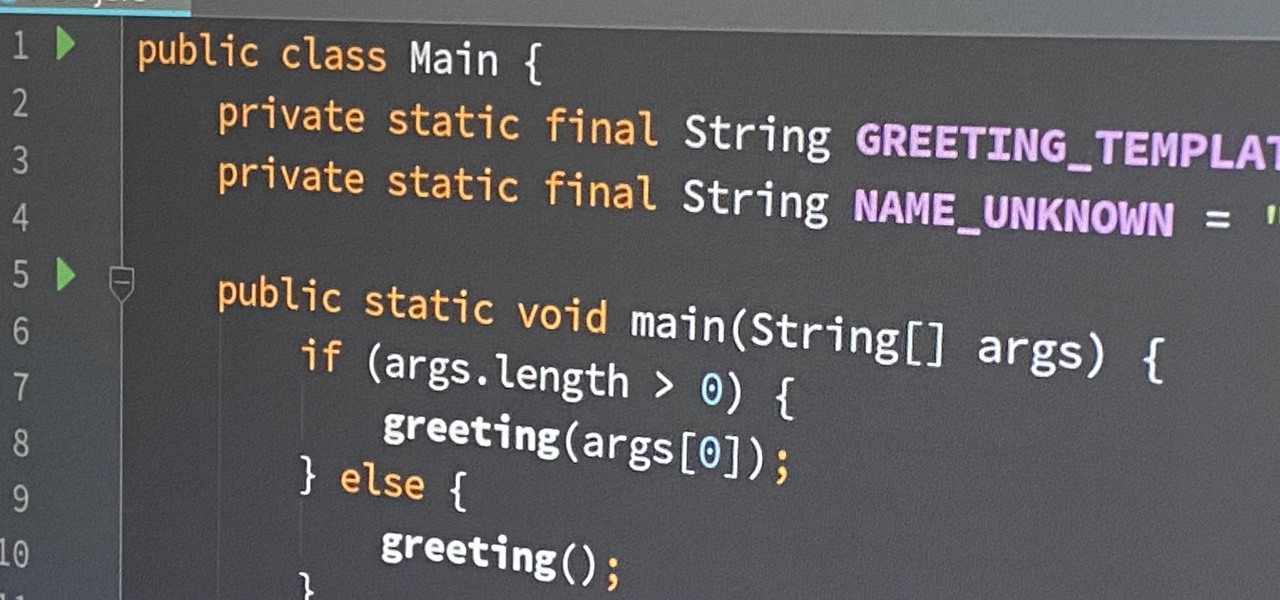
Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

Despite some early and optimistic predictions that the world would have returned to normal by now, the surprisingly stubborn and resilient coronavirus continues to upend and alter how we live our lives when it comes to working from home instead of the office.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

Thanks to a growing demand for talented and trained leaders who can inspire teams and innovate new products and services, there's never been a better time to work as a project manager. Whether you're interested in joining the ranks of a Fortune 500 company or working independently, project managers command high salaries and enjoy unparalleled opportunities for advancement.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

GameGuru was created for game enthusiasts who are not programmers or designers. By offering catalogs with thousands of royalty-free assets, GameGuru lets design novices bring their visions to life.

Since it first launched in 2003, WordPress has dominated the internet. The free, open-source content management system (CMS) is used by over 60 million websites. Wordpress is undeniably one of the most popular CMS solutions in the world.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

If you're a tech-savvy coding pro, you have a virtually limitless number of great career choices to choose from. Whether you're interested in working at a small tech startup, freelancing as a cybersecurity specialist, or founding the next Google, having a solid understanding of development terminology and general programming will inevitably get you far.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.