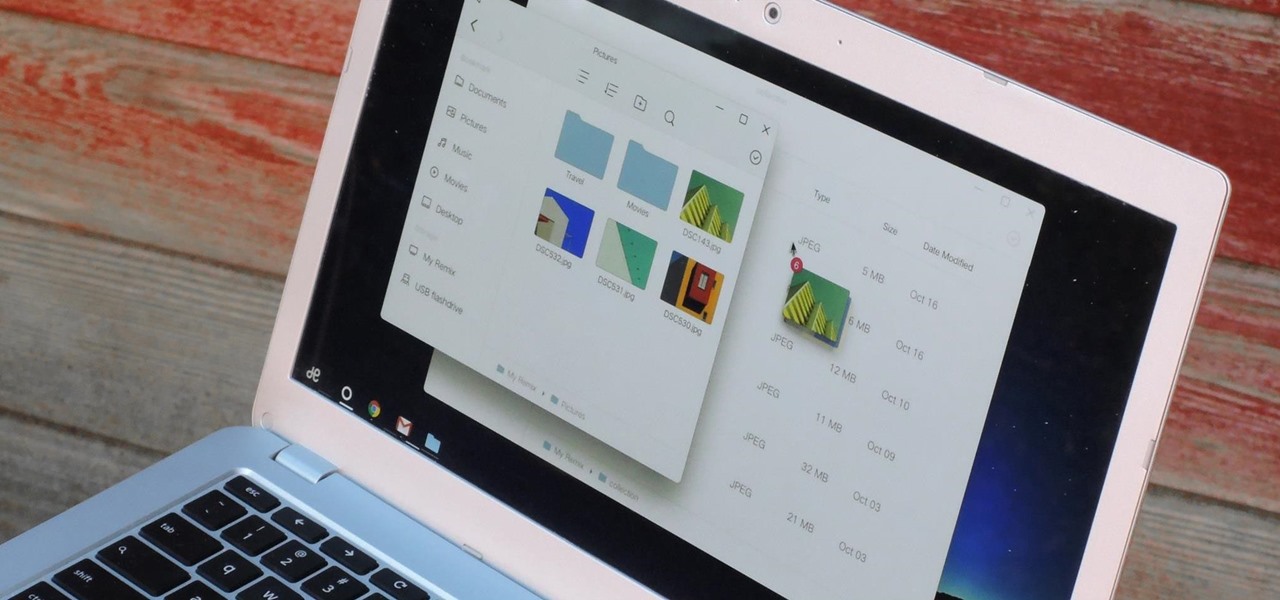
We live in a computer world full of file formats. Whether we are talking about images, videos, or text documents, there are dozens of file types for each, and there are new ones added every year to applications. Keeping in mind that many of these formats were created before the internet was widely available (at least, in infant form), the primary reason for this glut of often complex choices is competition.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

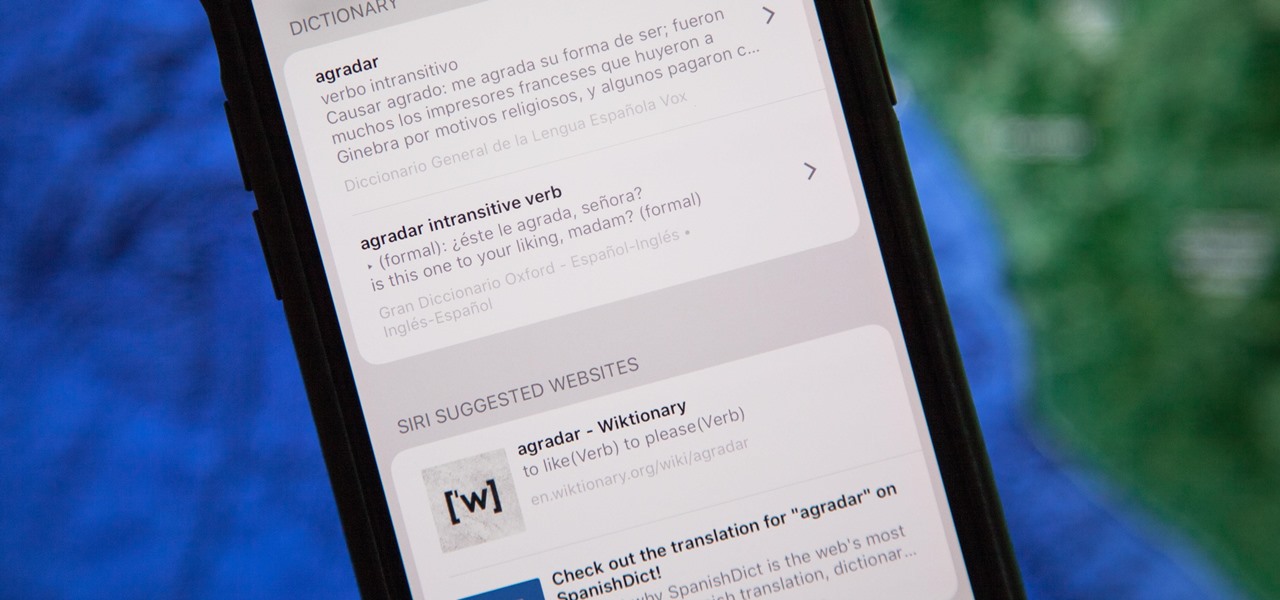
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

If you're anything like me, the urge to bake comes in waves. Winter constitutes an especially large wave; when I need to put on a few extra pounds for insulation, I go a bit carb crazy and take any opportunity to make breads, pies, and cakes.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

One of my favorite things about American Chinese food is how easy it is to eat: the pieces are bite-sized, the flavors are addictive, and the meat is always tender and easy to chew. But if you've ever tried to replicate any of your favorite takeout in the kitchen, you've likely noticed that the high heat required for most recipes thoroughly dries out the meat that you're trying to cook.

One of my favorite things about cocktails is that they're so diverse. They can be sweet or savory, filling or refreshing. And they can take advantage of nearly any ingredient imaginable, including egg whites, smoked ice, flavor cubes, and even beer.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

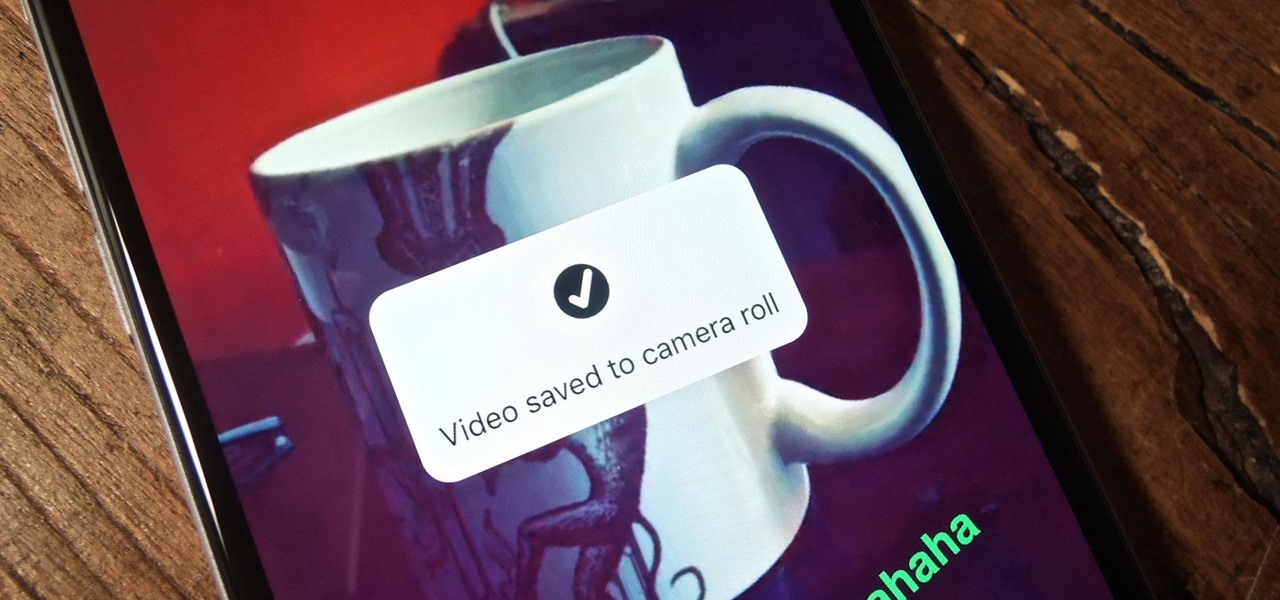
For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

As glorious as a good drink (or five) can be, the aftermath of alcohol on the body is one of life's least enjoyable features. A few hours of fun can come at the expense of a day or two of feeling dead to the world, with an upset stomach, an aching body, and a headache that makes it feel as though your friends used your head for a piñata.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.

Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

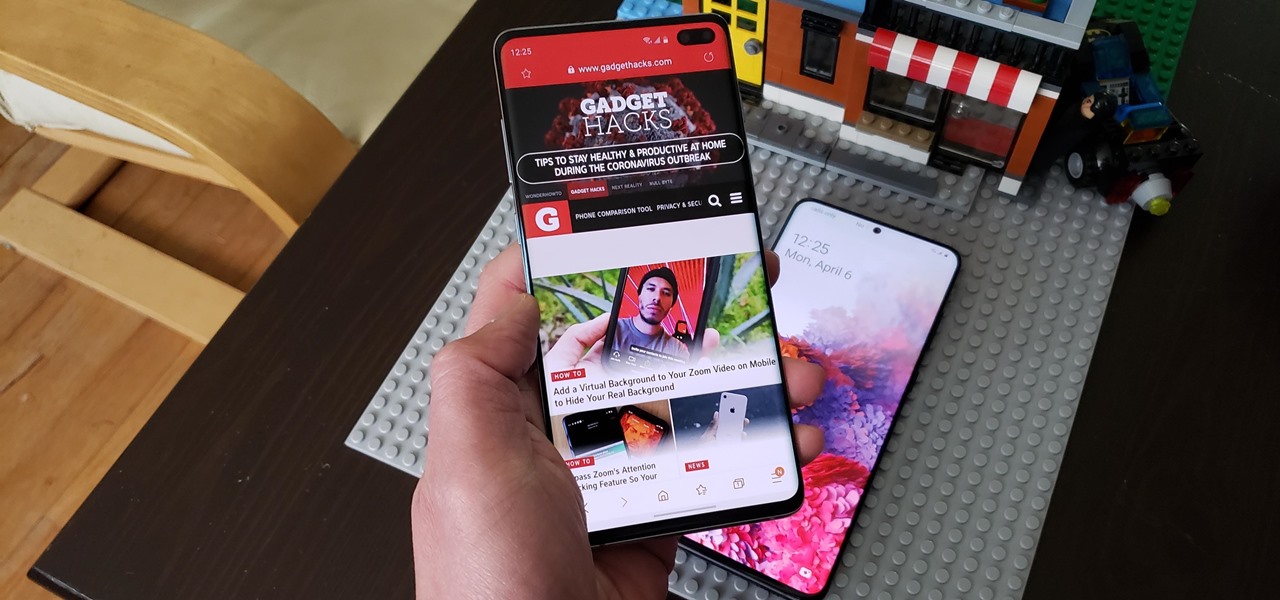
We're all feeling the impact of the economic recession underway due to the coronavirus. With millions of Americans filing for unemployment benefits, now more than ever should we focus on the best deal rather than the best model. And in no industry is that more evident than smartphones.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.