In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.
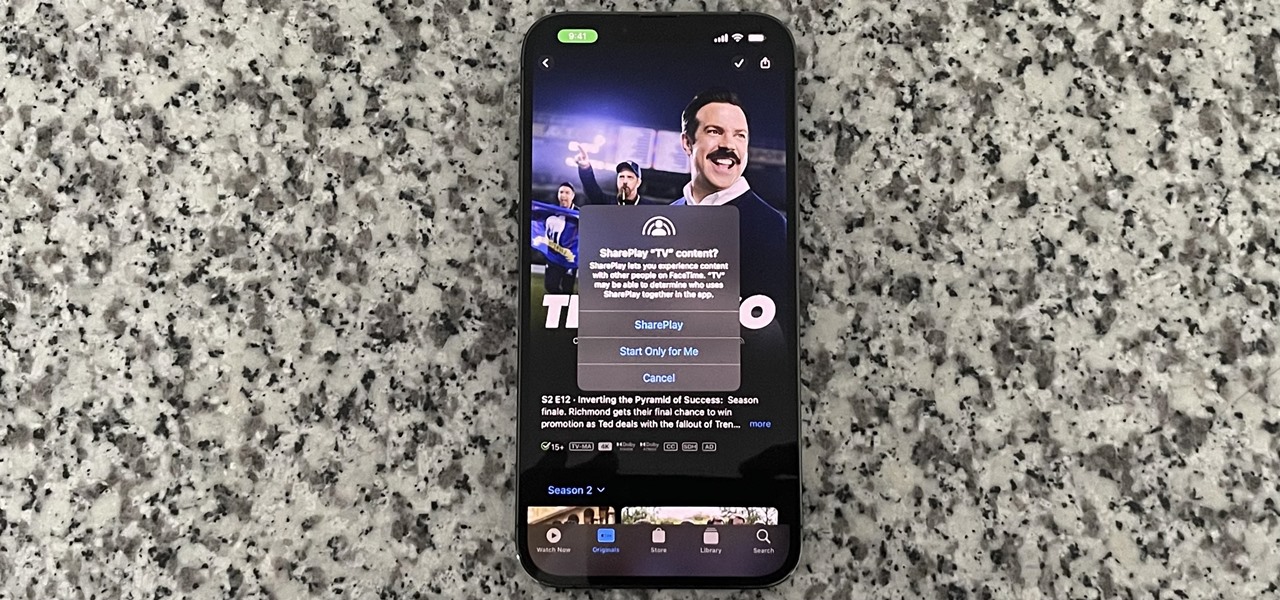
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

Apple's Shortcuts app lets you make and use custom icons for any app on your iPhone, but it won't actually replace any icons. If your goal is to change the official icon for the app itself without any redirects, there's a growing list of third-party apps that'll let you do just that.
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

When Tim Cook, Craig Federighi, and other core Apple leaders take the stage for WWDC 2021 on June 7, we'll hear a lot about exciting new things to come. We're likely to see what's in store for watchOS 8 and macOS 12, but more importantly, we'll get a glimpse at what iOS 15 and iPadOS 15 will be like.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

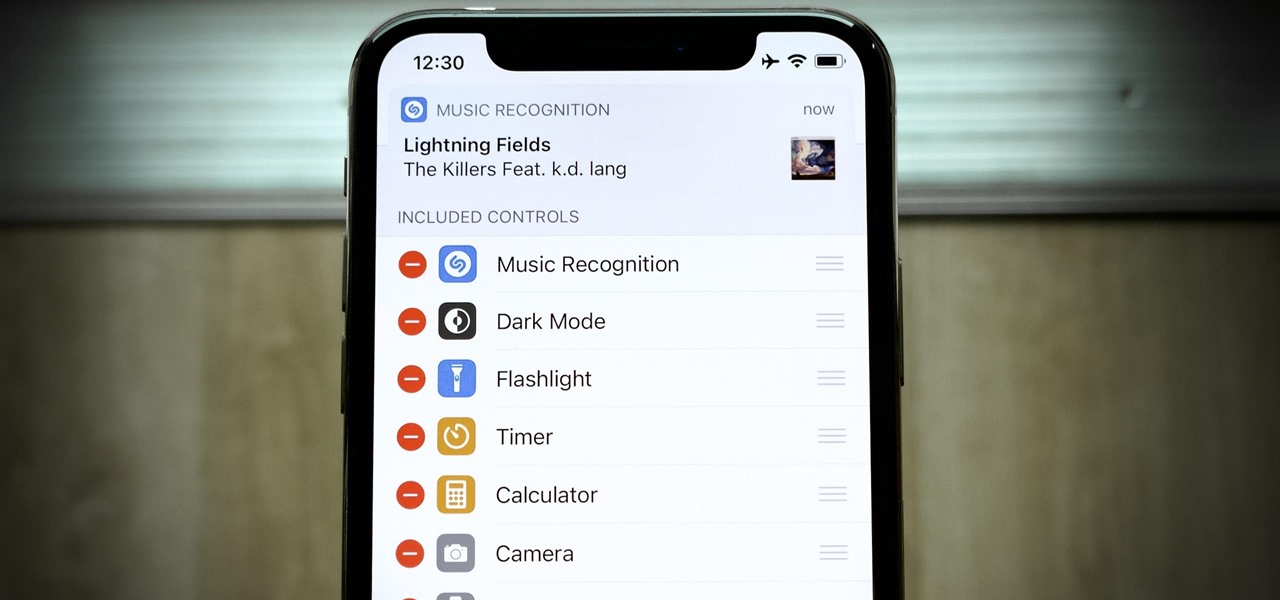
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Last year, many were caught off guard when Google released a midrange Pixel device. It was quickly crowned the best value-buy phone on the market, as it brought most of the camera tech people loved in the flagship Pixel for almost half the cost. Google's 2020 entry in this series has finally made its long-awaited debut.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

This collection of instructional videos from BaseballRox with baseball player Jeff Pick focuses on proper pitching mechanics with an emphasis on safety in the sport of baseball.

Boss's Day is on October 16th, and this year it falls on a Saturday— what better of a day to celebrate Boss's Day? More than likely, you won't be working in the office this weekend, and if you are, you probably don't feel like celebrating and thanking your boss for being so kind and fair. So, forget the cake and ice cream and instead, take the chance to develop a good relationship with your boss, because hating or kissing up to your boss just isn't the way to go.

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

In this Apple Color tutorial Richard Harrington and guest Robbie Carman will use user defined shapes to form vinettes to perform a secondary color correction. Learn about where primary and secondary color correction really occurs in Apple Color and other tips and tricks.

Ben Swann takes a look at "Rule 38" in the Republican National Convention rules which states that States and Congressional Districts cannot "bind" their delegates

What do you think of Brown's first TV ad? Do you think he'd be doing better in the polls if he spent more money on ads? FYI according to Brown's campaign, Whitman has run over 45,000 ads since the primary.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

The mouse is the primary tool most people use for accessing their computer and the vast stores of information on the Internet. Wouldn't it be funny if instead of allowing you to click icons on the computer screen, your mouse just lit up and made noises when you pressed it buttons? Well now you can prank a friend's optical mouse and make it so. This video will show you how to do it using only a mouse, simple tools, and a light-up, noisemaking keychain cow toy. Prank an optical mouse by replaci...

Half-hitches are great knots, but only when use in combination with other knots. By itself, a half-hitch is unsafe and unreliable, but when joined with other knots, can be quite the opposite. Tying two half hitch knots together is great for attaching a rope or line to any object. The half hitch and double half hitch are used throughout specialities, most notably as a boating knot, outdoor knot, and paddling knot.

This project is intended to reuse PVC that makes up the images on billboards and make them into houses for disaster and poverty stricken people. While the images are definitely cg mockups, the concept is awesome. I've personally been working on disaster relief shelters, but my concepts all involve using fresh PVC pipe. These guys have taken it a step further by taking vinyl sign material that is headed for landfills and recycling it into homes.
From Gaming Age: An Xbox LIVE Gold Family Pack includes:

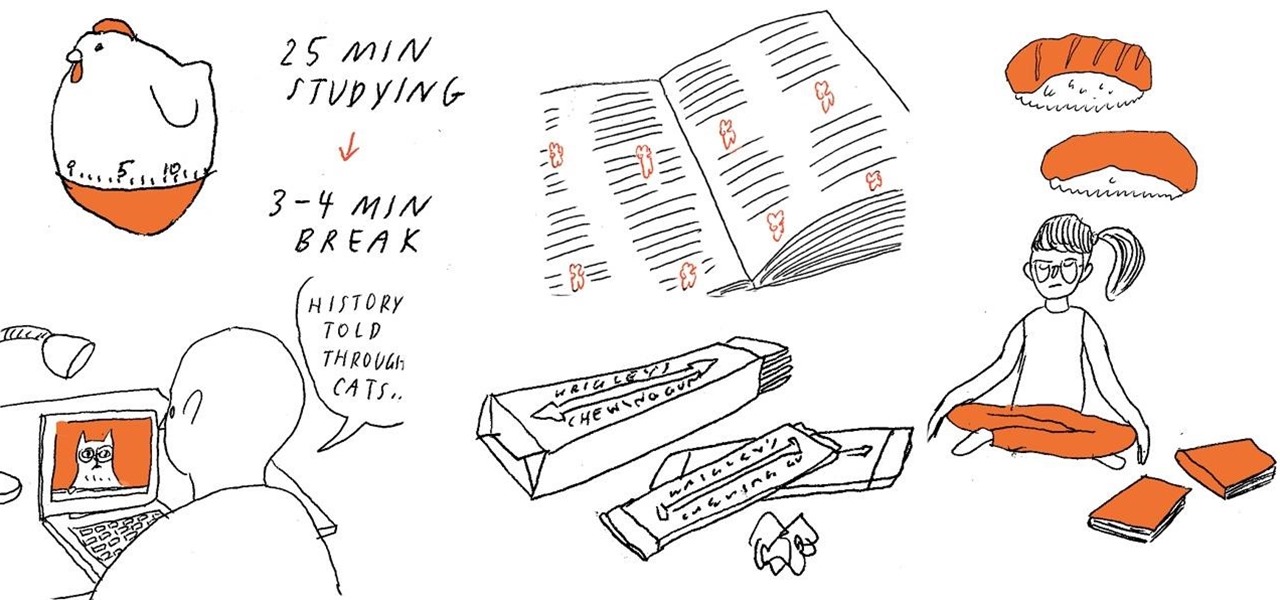
Chew on gum while you're reviewing study material, and then chew that same flavor on the day of the exam to help jog your memory. Or, if you're having difficulty understanding a concept, see if you can find that same concept explained on the internet in the form of a YouTube video or a visual infographic. Studying and memorization works best when you engage all of your senses instead of just one.

Microsoft just revealed the preview of its latest incarnation of Webmail, Outlook.com. One particular Outlook.com feature worth noting, is its support of multiple e-mail aliases. They're a great way to protect your primary e-mail address. And because you can't log in to your Outlook.com account with an alias, it adds another level of security. How To Add an alias

This is an absolutely fundamental concept and is important to development as a filmmaker. It's a really simple pice of shorthand that cinematographers and gaffers use to keep track of lighting setups across different shooting days. It's called a lighting ratio or a contrast ratio.
Conservative challenger Rick Santorum announced Tuesday that he is suspending his Republican presidential campaign after a weekend of "prayer and thought," effectively ceding the GOP nomination to front-runner Mitt Romney.
It is time for a groundswell of Ron Paul supporters to quietly, respectfully but firmly make their position clear to the mainstream media and the GOP establishment. Simply put, "No Paul on the ticket means no vote for the GOP in November."

This infographic from SingleGrain aptly and succinctly describes the primary differences between Facebook and Google+. Which social network will reign supreme?