This tutorial shows you how you can make your own do it yourself green screen out of a bed frame, some hardware (a staple gun is key) and a green blanket (or any large length of appropriately colored green gabric).

For an extra level of security, you can download an app onto your iPhone or iPod that will let you create a customized security key, which you unlock by using the touch screen to draw a simple graphic. This tutorial shows you where to get the app and how to set it up.

Need some help figuring out how to use a Schosche flipSYNC key fob USB cable? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using your own flipSYNC, take a look.
Have you lost of forgotten your administrator password in Windows? There's no way you can do anything without it, so how to do you get your password back? Well, you're not going to be able to get it back, but you can reset it, and Windows Password Key can help. This tutorial will show you the steps to removing your lost Windows password and resetting it altogether.

Masking and keying are two of the more basic and important functions of Adobe After Effects. This video will teach you how to use them quickly and easily, using a little Counter Strike video as an example. There is no narration, but the material is simple enough that you should still be able to follow along.
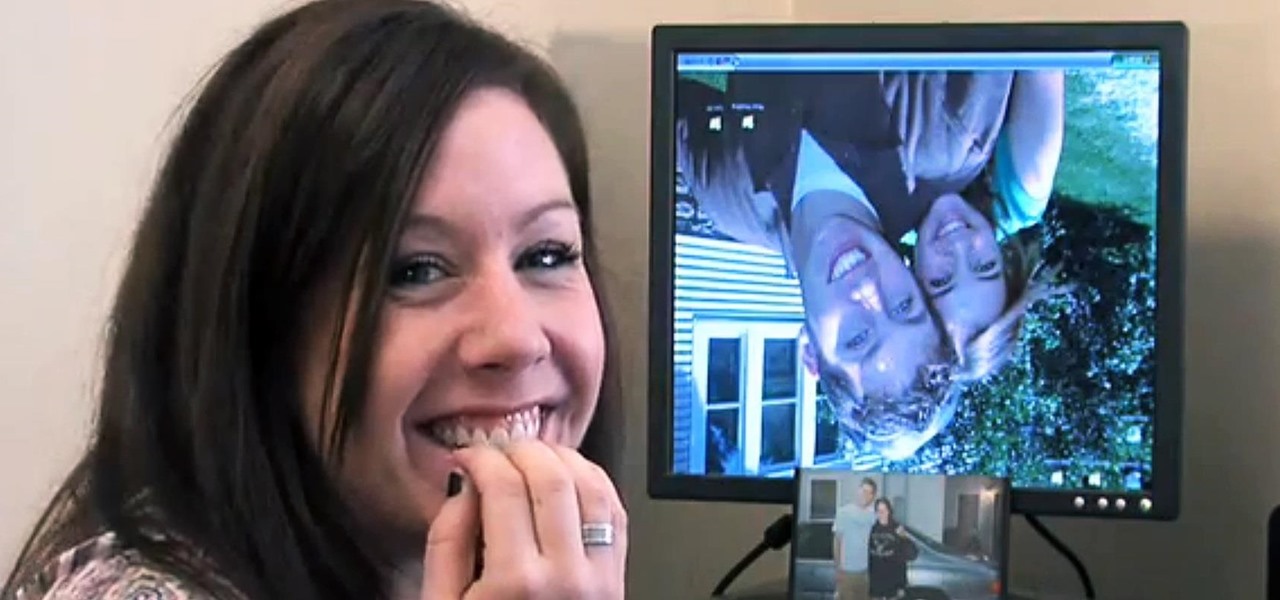
The perfect way to avoid boredom at work or in the classroom is with a good old-fashioned prank, and this one is for tech-minded. In the video below, you'll see how to change your coworker's (or classmate's) computer screen to be display upside-down, which will totally freak them out when they return from lunch or the restroom. The best part is watching them try to revert it back to normal!

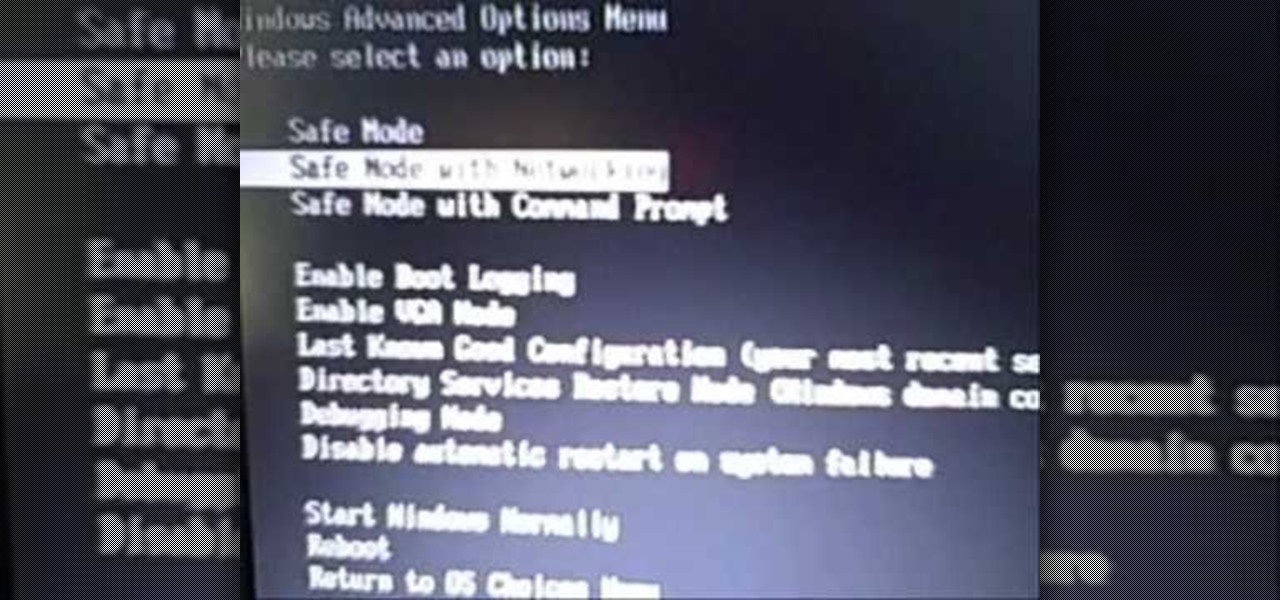
There are times when you must start up your Windows XP computer system in Safe Mode, for example if you need to remove certain viruses, key loggers, adware, etc. that cannot be removed while in standard mode. If you want to learn how to boot in safe mode in Windows XP, you should watch this. 1. Turn on your computer. Make sure your monitor is on and you do not step away from your computer, as booting into safe mode happens within the first minute of when you turn on your computer. You should ...

This is a Computers & Programming video tutorial where you will learn how to take screenshots on Mac OS 10. 5. Andrew Grant says there are several ways of doing this. The easiest way is to hold down the Command and Shift key and press 3. You will get a screenshot of the entire desktop. To take a screenshot of a selected area, hold down the Command and Shift key and press 4. The cursor now changes into a target. The figures next to it are the values of the pixels from the left hand top corner....

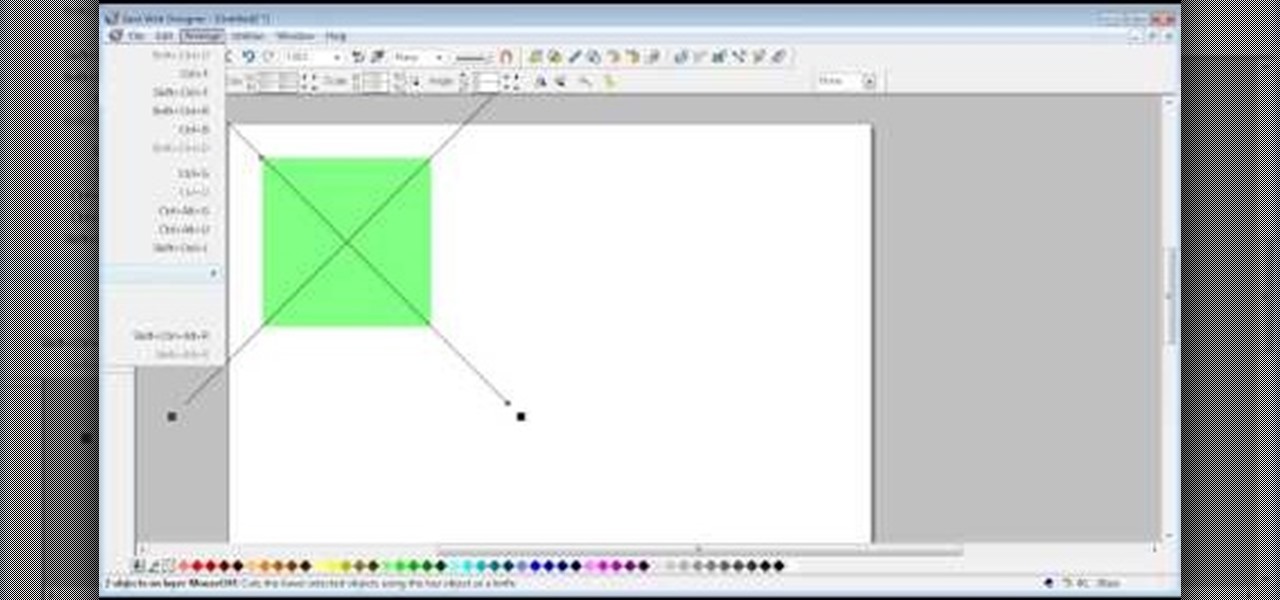
The video shows us how to create bevels in Xara web designer. Firstly using the rectangle tool hold down the Ctrl key to create a square. The problem with the Xara web designer is that it hasn't got a convert to edit the shape features which actually means that you cant select individual nodes with the shape editor tool which may create some other line. However you can select individual nodes by going to arrange/combine shapes/add shapes with selecting the rectangle. And by doing changes the ...

Craving key lime pie? Make one at home! Who knew those tiny little limes could make a pie with so much flavor? Your friends will love this easy to make, tart treat. Learn how to make a homemade key lime pie with help from this instructional video.

OS X has some easy shortcuts, just as Windows does. Watch this computer tutorial video to learn how to use them. This how-to video will help you use OS X's shortcut keys and allow you to use your computer faster.

Ever plug in a Windows keyboard to a Mac only to be frustrated by the swapped layout? This computer tutorial video shows you how to iron out the mix up with this quick tip. Watch this how-to video to learn how to easily make the transition from Mac to PC (and vice versa) by taking control of your command keys.

This Chroma keying tutorial shows you how to use Color Ranger in Photoshop to remove a solid background.

Learn how to play this boogie woogie blues lick in the key of C on the piano or keyboard.

Learn how to use the low key lighting technique to take darker pictures.

With tips from this video, play a Hawaiian hula tune on the ukulele. Start with the key

Chef John and his mother show us how to make her key lime pie.Here is the recipe:it will make enough for two pie crusts. You need salt, flour,shortening,ice water.The filling requires 3 eggs,3 limes, sweetened condensed milk, green food coloring whipped cream, and lime zest.

Israel Hyman shows yow how to use the sun as a key light for film, video, and photography, including how its angle affects your subject’s look.

This is a tutorial on basic chroma keying with Adobe Premiere .

Learn how to make a cool monogram key chain that holds post-it notes.

See how to use chroma keying in Photoshop. This technique is most often used to remove green screen backgrounds from images.

This tutorial tells you how to use pitch and speed in GarageBand '08. In GarageBand '08, they work independently from each other to allow for greater control of key and tempo.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

Learn a stunning effect by just remembering one card. The key card! Follow along as our British headless magician teaches you how to perform this basic magic trick.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Android apps check your system locale settings to determine which language they should display. For the most part, it's a seamless experience—except for those times when an app has not been translated into your language of choice, in which case the app will usually default to English.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

This video will guide you top 10 windows shortcut key which is very useful in everyday computing. Watch the video and follow the steps to know top 10 windows shortcut key.