If you’ve watched The June the Homemaker Show, you’ve heard me mention once or twice that I’m a vegetarian. Over the course of my restricted diet eating, I’ve noticed that vegetarianism is a touchy subject among vegetarians and carnivores alike, particularly in meal-type situations. Here are some things for omnivores and, uh, not-omnivores to keep in mind when talking to each other about food preferences.
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and very time-consuming and one also have to sacrifice their data stored on hard drives if the damage is more severe!

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects

MyShoppingGenie is an online shopping application that can help you find the best deals on products you search for.

Kurt Harris, MD, writes about paleolithic nutrition at his highly recommended blog, www.paleonu.com.

On a Wednesday evening when friends are going to a movie or out to dinner, you’re at the dojo training.

Spent the weekend with Sprint's new phone, the HTC Evo G4. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple will be announcing the new version of their phone this week. If it's comparable to leaked phone shown over at Gizmodo, then to say which phone is better is debatable. The iphone might have a better battery life but the Evo has an unlimited data plan, unlike AT&T's new tier pricing structure.

Hey, would you like to be as cool as this: You wish! But you could do the next best thing, and that's capturing your earth shattering game play with the Easycap DC60.

Motion trails in Autodesk Maya can be very handy at times when animating your scene. Keying a bone/joint or other object every so many frames can take up quite a bit of time and can sometimes be a big hassle, too. I have found many times when I could have really used one. I also don't like to search the Internet with a question and not find an answer (at least, without paying for it). So in this how-to article, I will demonstrate going about creating a simple (or complex) motion trail to make...

Don't ever be caught without your "go-to" items in your bag. In this video, Jennifer, Beauty Vlogger, shares her top seven makeup "go-to" items. Moisturizer

New Year's Eve. It will be one hell of a chaotic night. Trust me. The overcrowded streets. Long lines for the urinal. Maxing out your credit card on that shot of Cuervo. You'll be lucky to make it out alive.

Why a PDF Portfolio? If you've been wanting to create a PDF (portable document format) portfolio for your photos, art or design work, or wanted to create a PDF magazine that can be read by anyone on the net, then this article will show you how to go about it.

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.

So you've found yourself opting to be a vegetarian. The transition into a new way of eating and living is not always easy and as a result people often ditch their vegetarian goals and revert back to their previous eating habits. Here are some steps to ensure a successful transition to vegetarianism:

The Jackass boys are put in large steel cage 15 to 20 feet high; wrestling ring optional. They are soon joined by a mean young bull weighing in the 500-750 pounds. (We don't want too large 2000 lb of a bull that does not have much room too maneuver & we dont want to make thanks too dangerous now do we!)The goal of this prank: The boys have to either climb out of the cage or use a very large step latter to get out. But there is a catch: to keep the boys from immediately climbing out of the cag...

I don't know f you can use this, but here goes:

Here are some charts I made to help you master crafting recipe levels. Don't forget to note the rewards at the bottom of each chart!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

¬¬Just about every business has a website these days but very few businesses know how to effectively use their websites to get more customers. There are two different things that a business owner needs to do to increase their website traffic: optimize their site so that search engines can find them easier and promote their site on the internet so that they have greater visibility. This article will discuss how to optimize a website.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

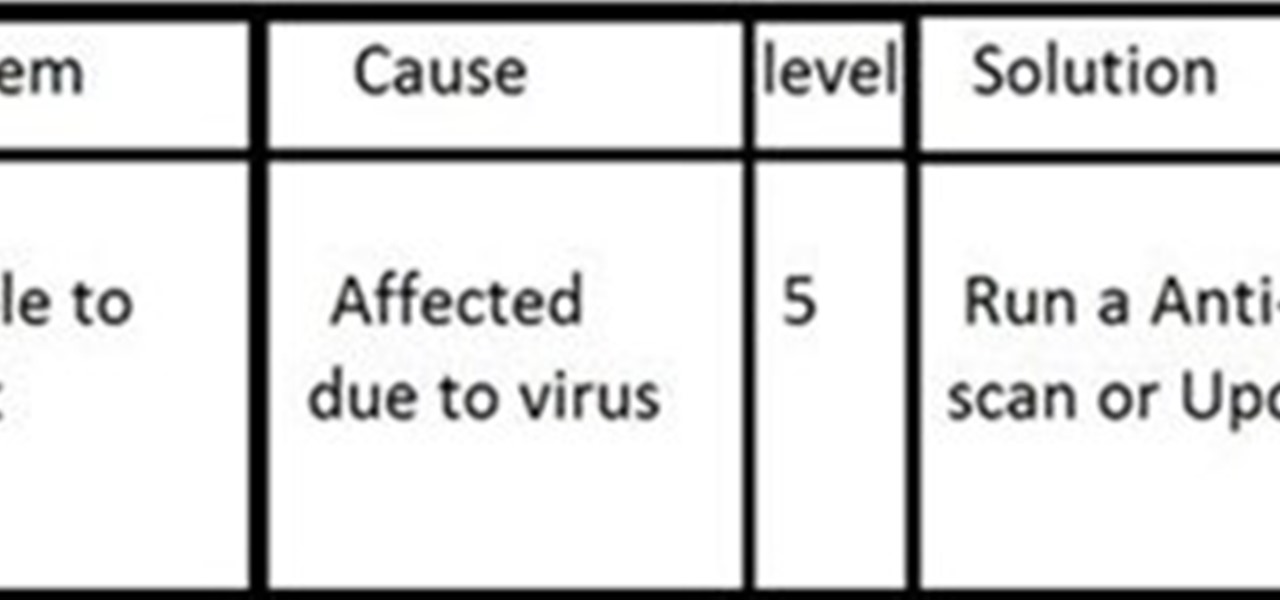
Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

In the age of automatic video editors and all around software-assisted creativity, how can a humble blogger help people master a program if said program does all the work for you?

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

The manual that's included with the Canon EOS 5D Mark II is a great starting point for learning the camera, but it's definitely not the only place you should be getting your information from if you intend to master your 5D Mark II. If you don't have the manual, you can download a copy of it here from Canon's website. It's great for learning the basics of the camera, but sometimes it can be vague and hard to follow. In order to capture the full potential of the 5D Mark II, you need to go a lit...

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.

By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or selfish choices, by governments and individuals, have on rainforests and reefs, cultures and communities.

Who could resist a retro SCRABBLE board game for two bucks? Suereal definitely couldn't, especially with the challenge of totally revamping a board game into something genuine and creative. Craftster's Craft Challenge #51 last June was meant to bring life back to an old board game with the following expectations:

Update This issue has been resolved

Written by JD Coverly of WonderHowTo World, LoadSave:We've spent the last week with Sprint's new phone, the HTC Evo 4G. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple has unveiled the new version of their phone this week and thankfully it's debatable as to which phone is better. The iPhone has better battery life and a more robust App store, but it suffers from a smaller screen, smaller camera resolution, no HDMI out, face talk only on wi-fi networks, and ...