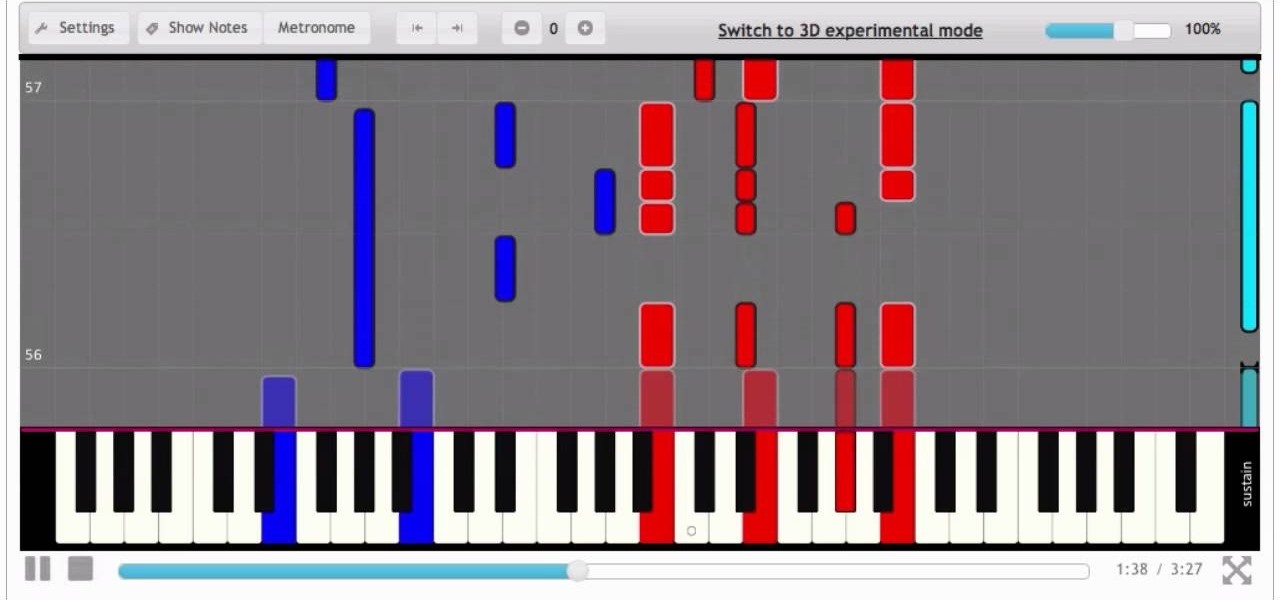
You don't have to know how to read piano chords or piano sheet music in order to use this piano tutorial. Connect a piano keyboard or start playing on your computer keyboard right away! Practice one hand at a time, change playback speed, transpose to a different key, create loops to repeat, track your progress and much more. How to Play Dreams Of Fireflies by Trans-Siberian Orchestra - Interactive Piano Tutorial.
Video: . You don't have to know how to read piano chords or piano sheet music in order to use this piano tutorial. Connect a piano keyboard or start playing on your computer keyboard right away! Practice one hand at a time, change playback speed, transpose to a different key, create loops to repeat, track your progress and much more. How to Play Skyfall by Adele - Interactive Piano Tutorial.
Video: . You don't have to know how to read piano chords or piano sheet music in order to use this piano tutorial. Connect a piano keyboard or start playing on your computer keyboard right away! Practice one hand at a time, change playback speed, transpose to a different key, create loops to repeat, track your progress and much more. How to Play Locked Out of Heaven by Bruno Mars - Interactive Piano Tutorial.

Video: . You don't have to know how to read piano chords or piano sheet music in order to use this piano tutorial. Connect a piano keyboard or start playing on your computer keyboard right away! Practice one hand at a time, change playback speed, transpose to a different key, create loops to repeat, track your progress and much more. How to Play Sweetie by Carly Rae Jepsen - Interactive Piano Tutorial.

http://www.pianocrumbs.com - High quality piano tutorials. "Live While We Are Young" is a single from "Take Me Home" album.

Video: . You don't have to know how to read piano chords or piano sheet music,- start playing piano right away!

The song is included in "Music From Another Dimension" album by Aerosmith. Video: .

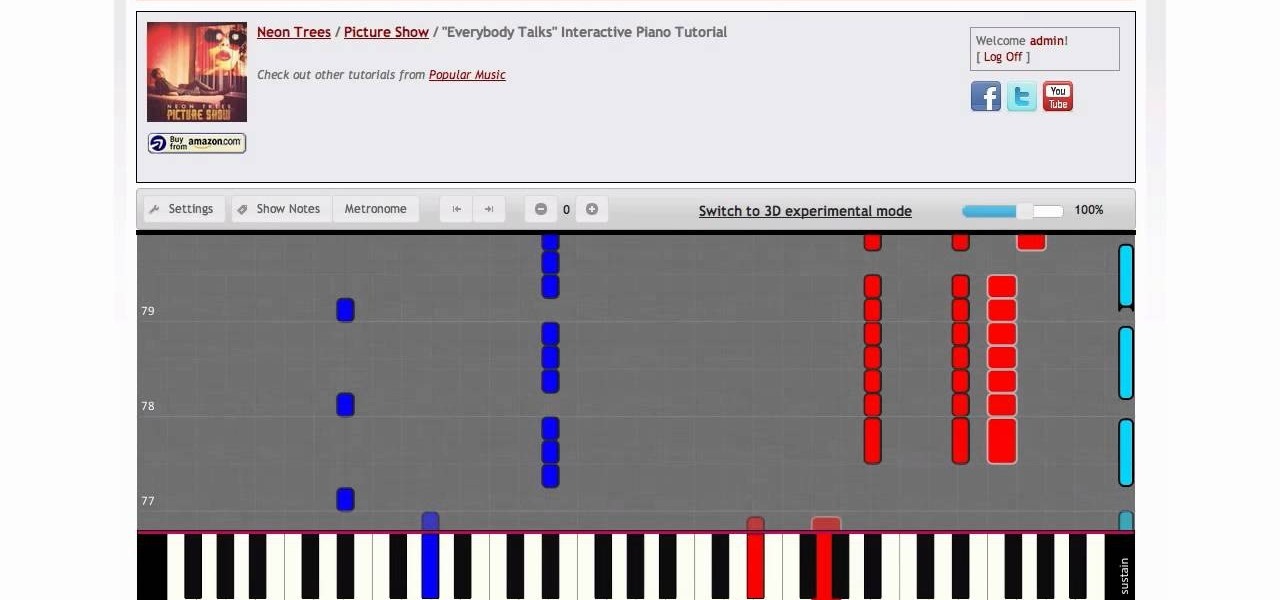
Video: . Learn how to play "Everybody talks" by Neon Trees. The tutorial is made by PianoCrumbs and available online at:

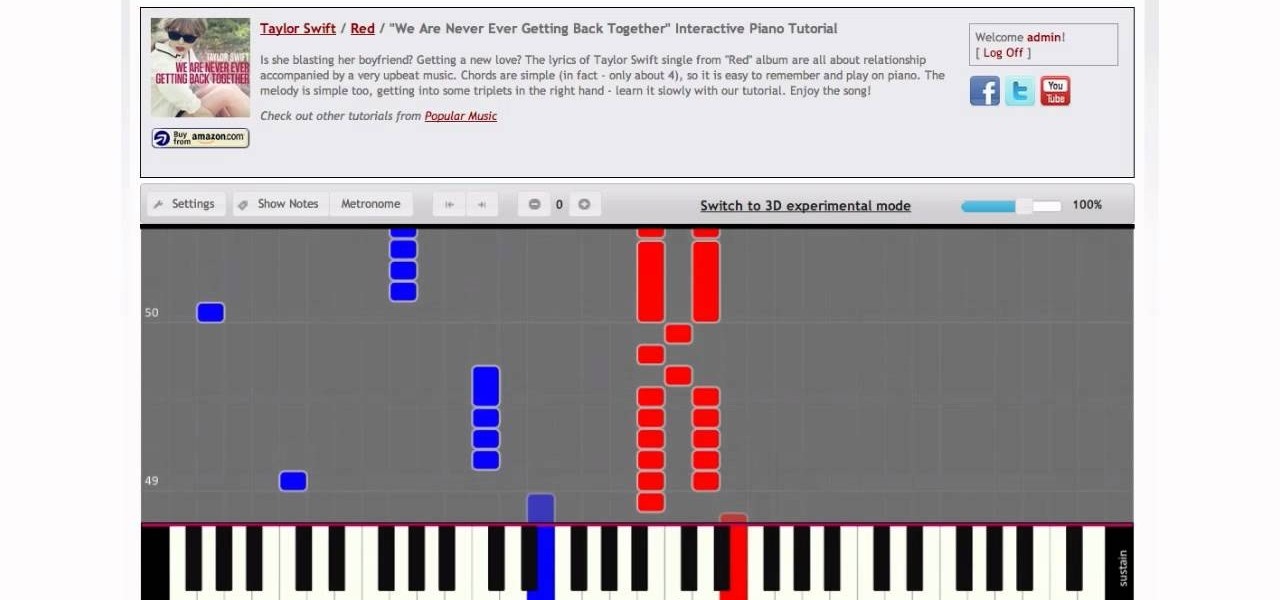
Video: . Connect a piano keyboard or start playing on your computer keyboard right away! Practice one hand at a time, change playback speed, transpose to a different key, create loops to repeat, track your progress and much more. How to Play We Are Never Ever Getting Back Together by Taylor Swift - Interactive Piano Tutorial.

In this series of instructional music videos you'll learn how to play the blues piano in the key of D Flat (Db). Expert Ryan Larson shows you his special 12 key method to help you understand the techniques used by blues musicians through the ages, including the music theory behind 12 chord blues song structure, walking bass & rhythm lines, as well as 7th chords.

In this series of instructional music videos you'll learn how to play the blues piano in the key of D Major.

In this series of instructional music videos you'll learn how to play the blues piano in the key of F major.

With this video series you will be able to learn about the bass guitar and everything you need to know to start playing. Begin by learning the parts of the guitar. Our expert will break down the parts of the bass guitar so you understand what each part does.

This video is a tutorial on how to disassemble and clean a white Apple keyboard. Most of the keys pop out easily, but the bigger ones have metal clips on the back and need to be removed very carefully. Take a picture of your keyboard to remember where each key goes, and don’t lose any.

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

The key to being a good doctor is great patient care and thoroughness, and those are exactly the skills you will learn in this video lesson, as you learn to perform a cardiovascular examination on your patient. This is a great, step-by-step resource for the proper examination procedure. Every medical student should know these techniques, and nursing students could benefit from this knowledge, too. Every cardiovascular exam should include inspection of the pulse, blood pressure, carotid pulsat...

First of all you have to check the three red lights as shown because it indicates that the Xbox is broken and needs repair immediately. However if you open the Xbox the warranty is invalid and it takes six weeks to get it repaired. So go to eBay and buy the repair kit with printed manual for ten dollars. Remove the top and the bottom covers. It shall make a loud slap and it should be expected. Now use a key to unscrew the top cover and then remove it. Now remove the white color fan part. Now ...
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

If you've ever wanted or needed to use an app in a different language than your phone's primary language, your Android phone now makes it a simple process.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Starting Sept. 13, you can preorder the iPhone 11, 11 Pro, or 11 Pro Max from Apple, wireless carriers, and various e-commerce websites. However, unlike with Android smartphones, there is only one set of iOS phones that come out each year, so they're pretty hot items. That means being the first to get your hands on one could be a challenge, but we're here to help you out.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again.

Using a green screen is an affordable and easy way to transport your video to anywhere imaginable, even to places that don't exist. You can use it to sit behind a desk in a busy newsroom or dance on the moon, but first, you have to know how to properly perform chroma key compositing two videos together. Fortunately, Enlight Videoleap on iOS makes it easy.

At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

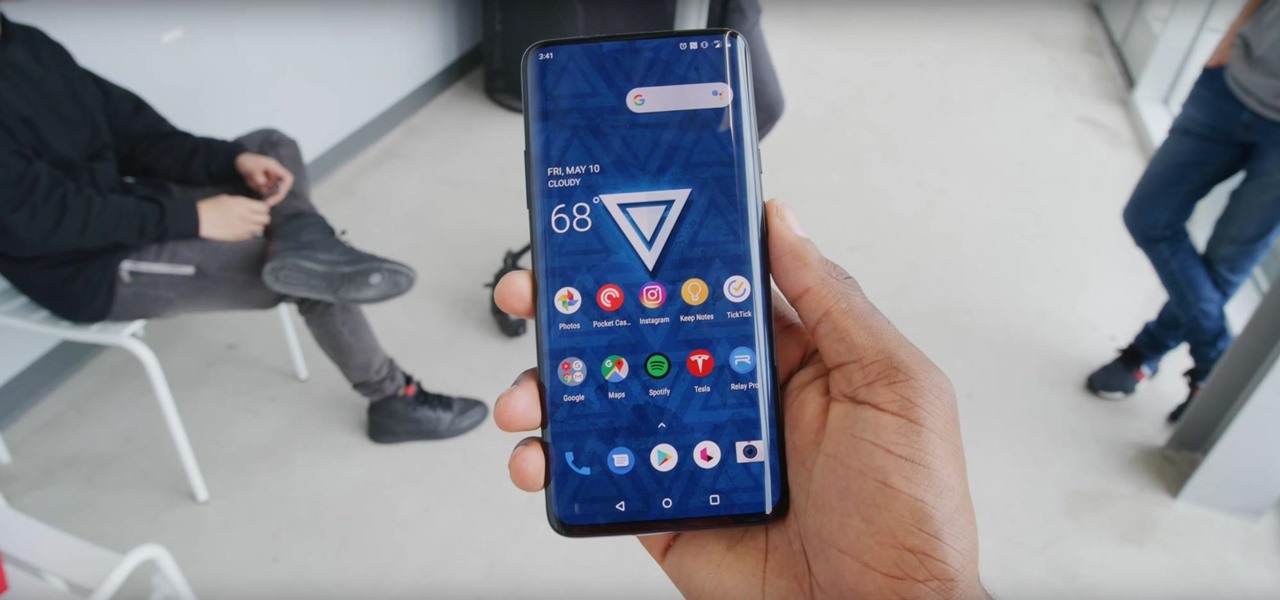
While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

After showing off a prototype of the Grordbattle multiplayer first-person shooter at the Game Developer Conference, Magic Leap has added a new Shared World feature in version 0.95.0 of the Lumin OS update released this week.

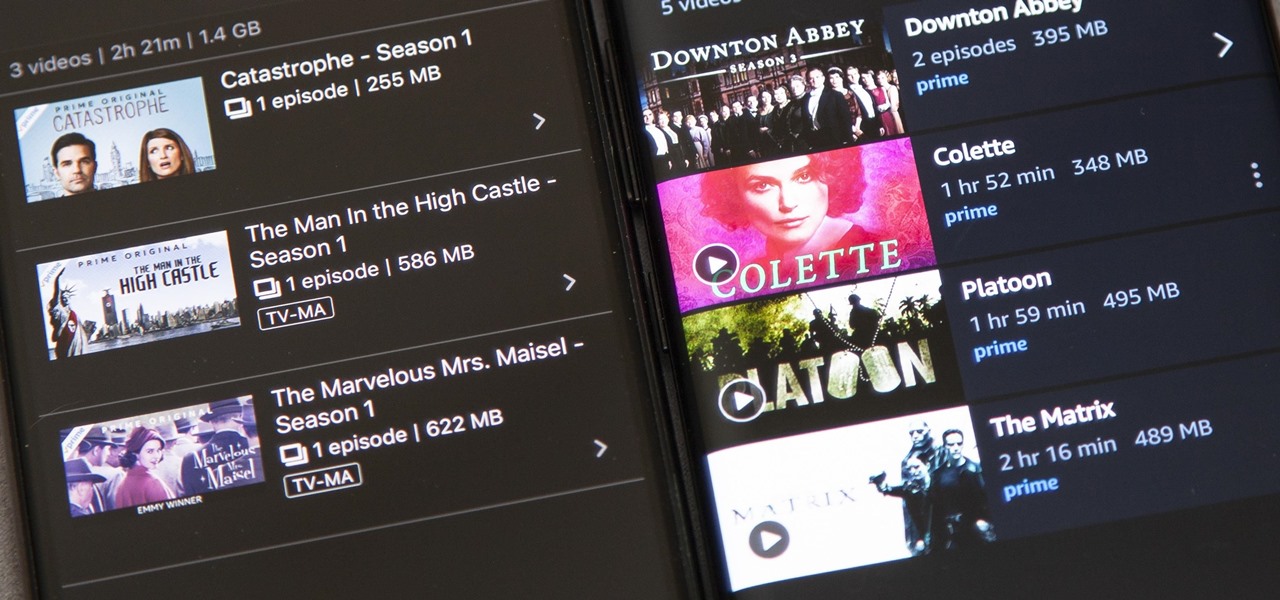
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

For the majority of phones, Android's volume rocker is wrong. A large vocal part of the Android community wishes the volume buttons' default control was the media volume, not the ringer. Although the Galaxy Note 9 is in the "wrong" camp, Samsung has included multiple ways to change it.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.