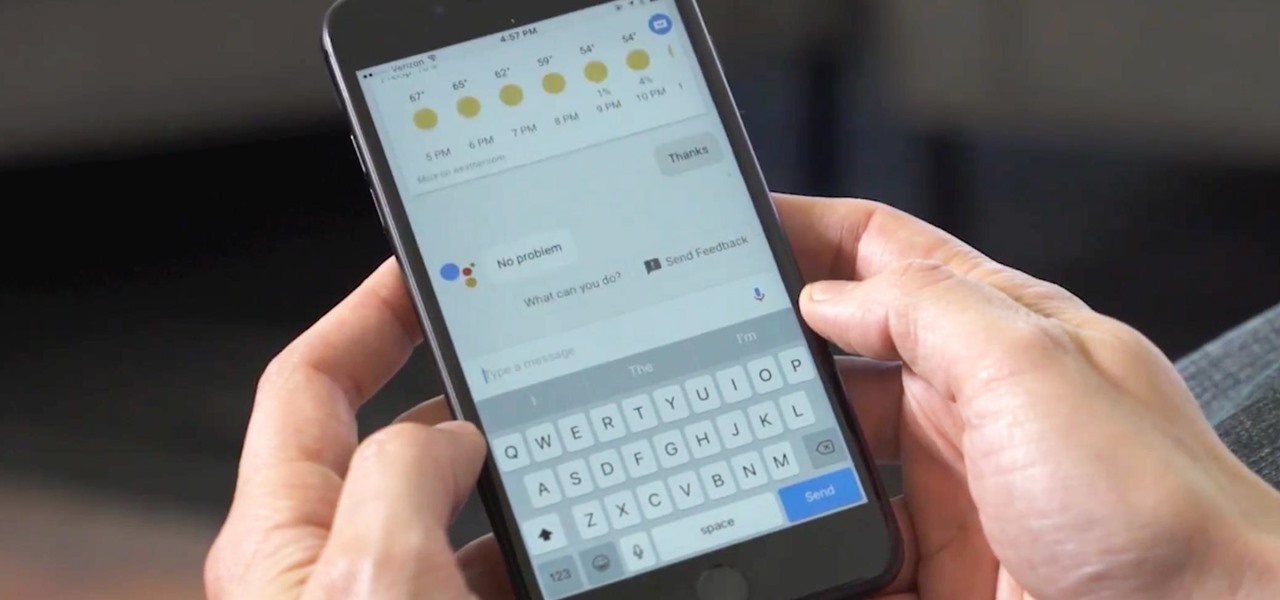
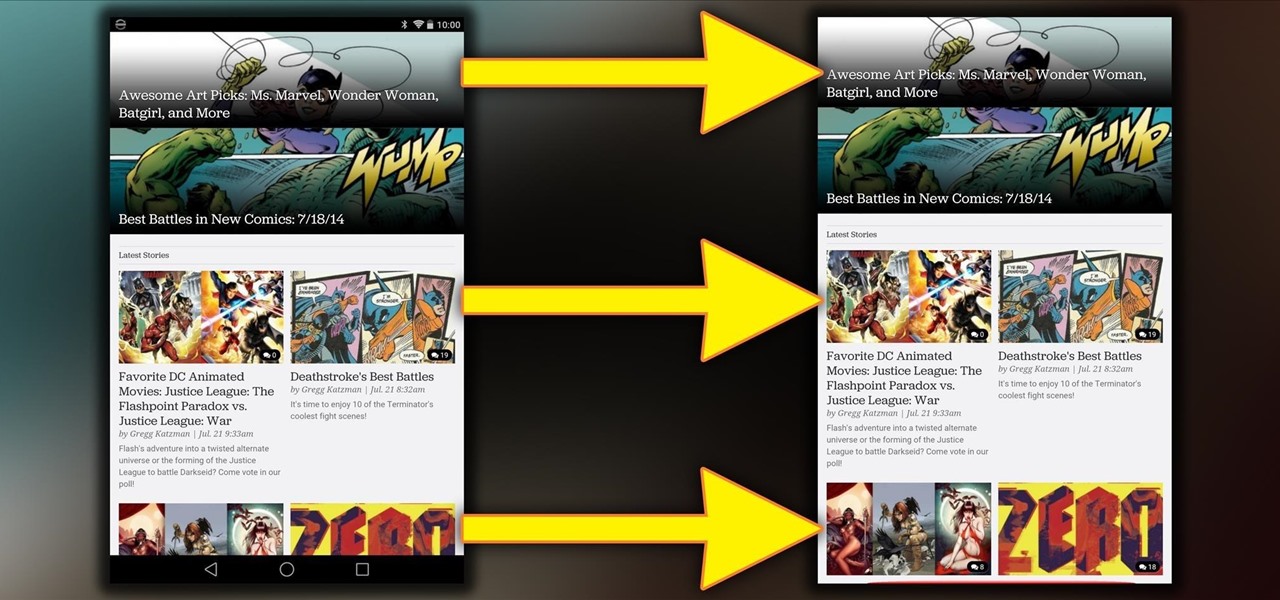
There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

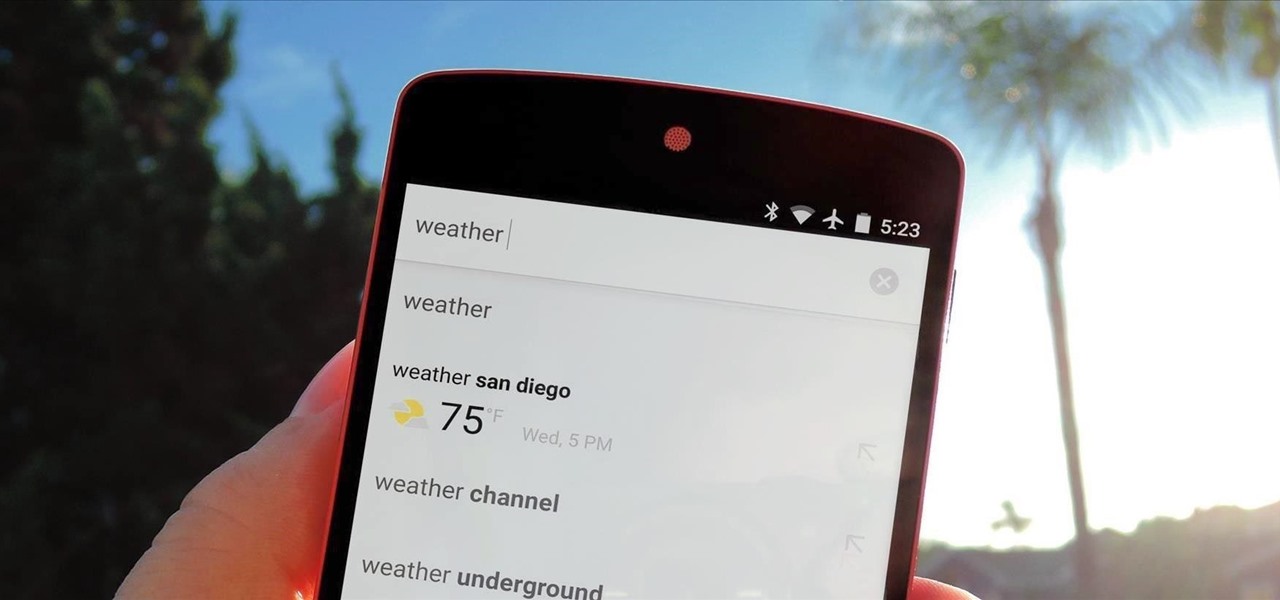
As we've said before, Siri has some major competition moving into its own playground, and Google just announced at its I/O event that Google Assistant is available on the iPhone, starting today.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.

Hello there Nullbyte users! This will be my first article here.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

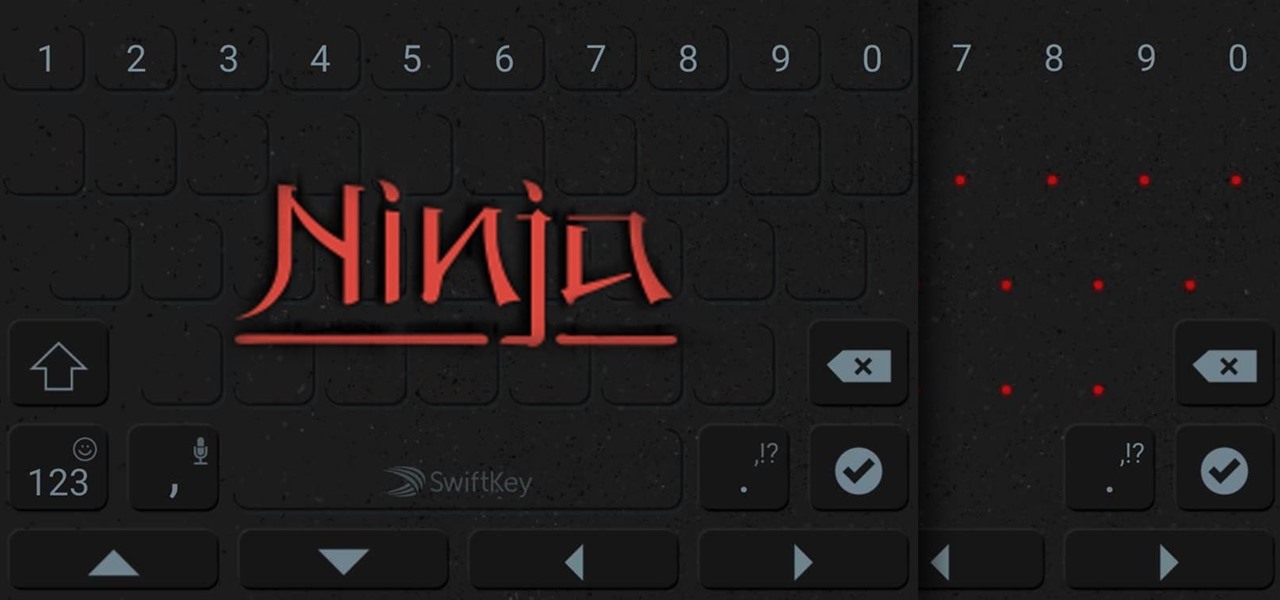
Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

In the U.S., smartphone users spend more time on Facebook and Instagram than on any other app. If this sounds surprising for any reason, it shouldn't. Anyone that's browsed Instagram in a moment of boredom knows that a few minutes can quickly turn into an hour down a rabbit hole filled with Likes, Follows, and straight-up lurking.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

The switch from Dalvik runtime to ART in Android Lollipop has rendered the Xposed Framework useless until a new version is released, but Xposed isn't the only way to mod a phone.

How many times do you think you press the Home button on your iPhone? You probably can't place a number on it, but you know it's a lot.

Google's music offerings have been on a roll lately. First they announced a new music video streaming service called YouTube Music Key, offering ad-free playback with background listening. Then they stated that the new offering would be rolled in with their Google Play Music service, with members allowed to exclusively test the Music Key beta, which just went live. And if all that wasn't enough, they're also offering free music to boot!

iTunes 12 was released alongside Yosemite this year, but it didn't pack quite the punch that the operating system did. Instead, iTunes received a minor facelift, with few new features and somehow lacking the intuitive feel of its predecessor. If you're not thrilled with iTunes 12, we've got a few tips to help you feel like you've got iTunes 11 back on your computer!

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.

With rumors of the Active and Prime versions on the immensely popular Galaxy S5 circling the web for the past few weeks, today, we've got some clear proof of the upcoming Active variant.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

As an added functionality to the S Pen, the Pen Window enables you to create floating application windows on your Samsung Galaxy Note 3—a tool that's extremely useful when it comes to multitasking.

Ever wonder why when you defrost meat, there's all that pink liquid at the bottom of the plastic bag? That liquid is called "purge," and it's not good.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

So, you find an interesting article online, but there’s something you don’t quite understand about it and instinct kicks in. Open new tab. Go to Google. Enter keywords. Search. Find information. Understand.

A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Apple has released the third beta of its iOS 7.1 software to developers, just a few weeks after their second beta introduced us to button shapes, a new calendar list view toggle, a hidden Car Display control and several other tweaks and performance improvements.