As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Lockpicking is a skill that takes years upon years to master. Locks come in all sorts of shapes and sizes, but have common ground in how they work. Most cylinder locks have "tumblers," which are metallic cylindrical objects that sit vertically to the actual locking mechanism. Tumblers have five or six holes with rounded key pins of various height in them, each needing to meet an exact height or the cylinder in the center (the lock itself) will not be allowed to turn. This is the reason why yo...

Aside from food, oxygen, sunlight and water, there are other necessities that humans arguably need today to survive—clothing, love and shelter among them. Almost everyone wears clothes, needs somebody (or something) to love and a place to call home. And what's the one thing that connects all three? Something we all have? Keys.

In this video tutorial, you'll learn how to use Trapcode Sound Keys to control a video clip with an audio source — a song, for example — within Adobe After Effects. For all of the particulars, and to get started using this effect in your own projects, take a look! Control time with audio in Trapcode Sound Keys for Adobe After Effects - Part 1 of 2.

Vinaigrette dressing can definitely make or break a salad, and this version definitely is in the "make" category. Passion fruit, key lime juice, honey, olive oil… how could you go wrong? Watch and learn this recipe for passion fruit and lime vinaigrette.
Conservative challenger Rick Santorum announced Tuesday that he is suspending his Republican presidential campaign after a weekend of "prayer and thought," effectively ceding the GOP nomination to front-runner Mitt Romney.
It is time for a groundswell of Ron Paul supporters to quietly, respectfully but firmly make their position clear to the mainstream media and the GOP establishment. Simply put, "No Paul on the ticket means no vote for the GOP in November."

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

This infographic from SingleGrain aptly and succinctly describes the primary differences between Facebook and Google+. Which social network will reign supreme?

Consistently used in many forms of physical training, the push up has been considered one of the best physical tests of muscular fitness and endurance. Namely known for its use in the military as well as other physically demanding activities such as boxing and the martial arts, the push up is necessary for any physical examination in which many struggle with.

On your keyboard, press WinButton + R to open the Run window Once opened, type Regedit.exe into the textbox and click OK
From LAist: Areas designated as bike lanes on the USC campus are now unfriendly territory for bike riders, after "Dr. Charlie Lane, associate senior vice president for Career and Protective Services, announced at a bicycle safety forum that the school is enacting a bicycle ban on [...] the two major pedestrian thoroughfares on the USC campus," according to the LADOT Bike Blog.

From The LATimes: "Brown, the Democratic nominee, touted talking points — living within California's means, no new taxes without voter approval, returning control to the local level — that could come from a Republican playbook. Whitman, his GOP rival, unveiled her seventh attack ad against Brown, this time enlisting the words of former President Clinton during their contentious 1992 Democratic presidential primary battle. Tellingly, both candidates avoided mention of their political party.

From the Huffington Post: Billionaire Republican Meg Whitman reported Monday that she has spent more than $99 million in her quest to become California's governor, while Democrat Jerry Brown is saving money for what could become the most expensive gubernatorial contest in American history.

To follow up on the Devil's Fork, here is the trailer for Limbo. From the Wiki:The primary character in Limbo is a nameless boy who awakes in the middle of a forest on the "edge of hell" (the game's title is taken from the Latin limbus, meaning "edge")[1] who then begins to seek out his missing sister.It looks innocent, but if you watch the trailer, you can see the kid stepping on dead bodies and so gruesome deaths. It's out on the 360 via XBLA, I don't know if it's out on any other platform.

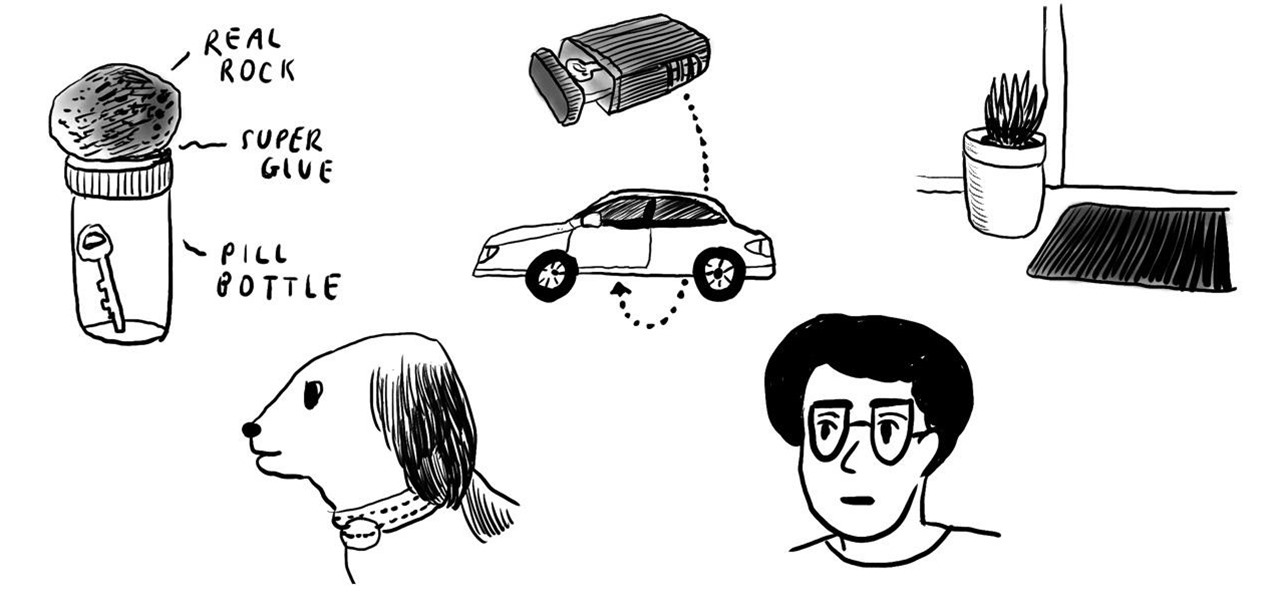
If you're ever paranoid about locking yourself out of your house, the worst thing you can do is to hide your spare key in an obvious spot, like under the doormat, under a planter, or anywhere near the front door.

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

This is a short tutorial about the application of shape keys to create control to animate architectural elements. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial. For more information, including step-by-step instructions, take a look! Animate sliding doors with shape keys in Blender 2.5.

Keys always seem to multiply. You start out with your house keys and car keys, and the next thing you know, your keychain is full and you have no idea what half of them even unlock.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

In this video tutorial, we learn how to use Key Correct Pro to composite with light wraps within Adobe After Effects. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide. Composite with ligh...

Need some help figuring out how to composite with Key Correct Pro plug-in for Adobe After Effects? It's easy. And this clip will teach you everything you'll need to know. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructi...

Adobe Illustrator Creative Suite 4, or CS4, software is a comprehensive vector graphics environment that is ideal for all creative professionals, including web and interactive designers and developers, multimedia producers, motion graphics and visual effects designers, animators, and video professionals. But having the program isn't enough; you'll need to know how to use it. In this video tutorial, you'll learn how to use smart guides and key allignment in Adobe Illustrator CS4. Use smart gui...

Popularized by artists like Son House and Skip James, Delta blues is not only one of the oldest forms of blues music, it is among the most stylistically distinct and technically rewarding to play. In this video guitar lesson from YouTube user deltabluestips, you'll learn how to play a number of simple Delta blues-style riffs and runs, all in the key of E. While this lesson is geared more toward intermediate and advanced guitarists, this means beginning players merely have all the more to lear...

Can't open a lock because you've lost the keys? Well this conning how-to video will teach you how to crack open a keyed lock with a hacksaw blade.Our host uses a hacksaw blade as his pick. Follow carefully and learn the art of picking locks with a hacksaw blade. Pick a lock with a hacksaw blade.

Propaganda and indoctrination at it's peak. My friends, today, when I was browsing through the net for news, I noticed something on MSNBC. It was a very short article, with a title that just wasen't true. Before talking about it, let me tell you why this is important.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Take a look around the next time you open up the File menu and slowly scroll through your editing options. Are your coworkers quietly cringing? Your kids running for the other room? Sounds like you need a few good keyboard shortcuts up your sleeve. Memorizing the right combos can transform you into a super speedy Windows superstar. Forget the mouse. Keyboard shortcuts are the new black.

There have been those times in everyone's life when we have kept our phones on silent mode and forgotten where we kept it. Well, if you have an Android powered phone there is a way by which to find your phone by ringing, just when you want it, even when it is kept on silent mode.

This seven-part tutorial series presents an overview of the techniques needed to model a human head using the Blender 3D modeling application. First, you'll set up the primary edgeloops and then move on piece by piece from there. Upon completion you should come away with some good strategies to model your own heads. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks,...

In this two part episode, Aharon Rabinowitz shows you how to use audio to control time. You'll learn how to make your video automatically move forward in time to the beat of the music - a technique used in tons of music videos and commercials.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a ferret.

This Animal Welfare Foundation three-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a rabbit.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a guinea pig.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a rat.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a hamster.

This Animal Welfare Foundation three-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a gerbil.

Attention cheapskates and locksmith apprentices, this key copying solution is stunningly simple. We've really mulled over this one. As you can read in the comments below, people struggle with executing this successfully. But it can and will work. You just have to modify your key to fit your needs.