Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Reading through various internet forums, it certainly sounds like the Google Pixel and Pixel XL are attracting more iPhone users than any of Google's previous Nexus devices. The sales figures seem to back that up, too, as the Pixel is outpacing last year's Nexus 6P, and pre-order demand has exceeded Google's expectations, causing delays in shipments. (We reached out to Google but they wouldn't give us any specifics on sales numbers or numbers of switchers.)

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.
Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

If you spend a lot of time reading about food, chances are you've heard about bone broth. It's all the rage these days, from high profile chefs like Marco Canora building menus around it, to celebrities like Salma Hayek using it as self-prescribed beauty regimens.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

Cookbook author, celebrity chef, television personality, and former White House nuclear policy analyst Ina Garten is familiar to many as the queen of foolproof cooking. Also known as the Barefoot Contessa, Ina hones in on techniques and tips that make time in the kitchen far less intimidating to folks of all skill sets. We've rounded up 8 of Ina's most useful cooking tips to help you out—from dinner parties to everyday cooking. Her philosophy is that it's always easier than you think!

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Common knowledge is a funny thing: it represents a majority's opinion on a particular subject and somehow makes that opinion fact. If that 'fact' goes unopposed and unchallenged, then it is passed on and preserved from one generation to the next—regardless of whether it is true or not.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).

Contrary to popular belief, sushi is not the raw fish that one gets at Japanese restaurants, but the rice that comes with it. It's hard to tell whether this popular misconception led to or came about because of the primary flavors that we think of in sushi are the fish. We often say a sushi restaurant has great fish, but almost never that it has great rice.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Glow sticks, a popular favor at parties and outdoor events, and a must-have on Halloween, can be traced back to the United States Navy in the mid-1960s. The military desired improved visibility during night operations, and glow sticks, with their small-size portability and lack of batteries, were a perfect tactical solution.

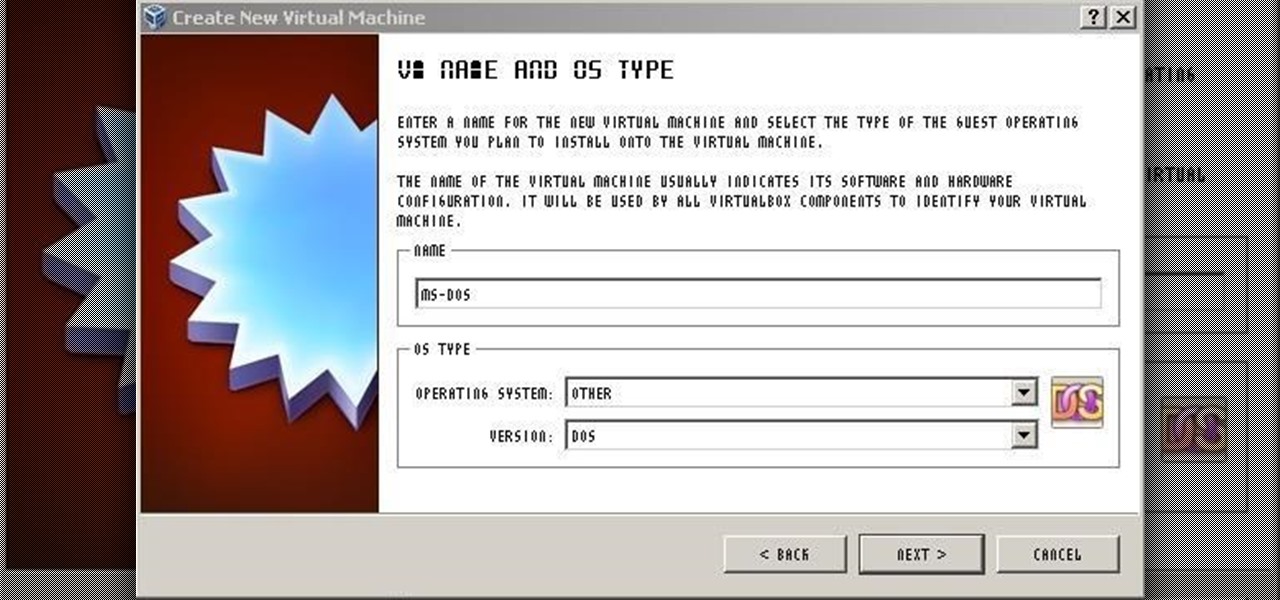
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Steampunking Nerf guns by painting them is a pretty common practice among Steampunks, but unfortunately, the really amazing-looking ones involve literally taking the gun apart, painting it, and then screwing it all back together.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

Next year, fans of Mario Kart will be able to experience the game in real life with the assistance of augmented reality.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Lack of appetite often signals a cold or flu. Eating can be the last thing we want to do when we have a sore throat or are too fatigued or achy to even get out of bed. When hungry, we don't feel as strong as when we are well fed—and we more than likely aren't as strong.