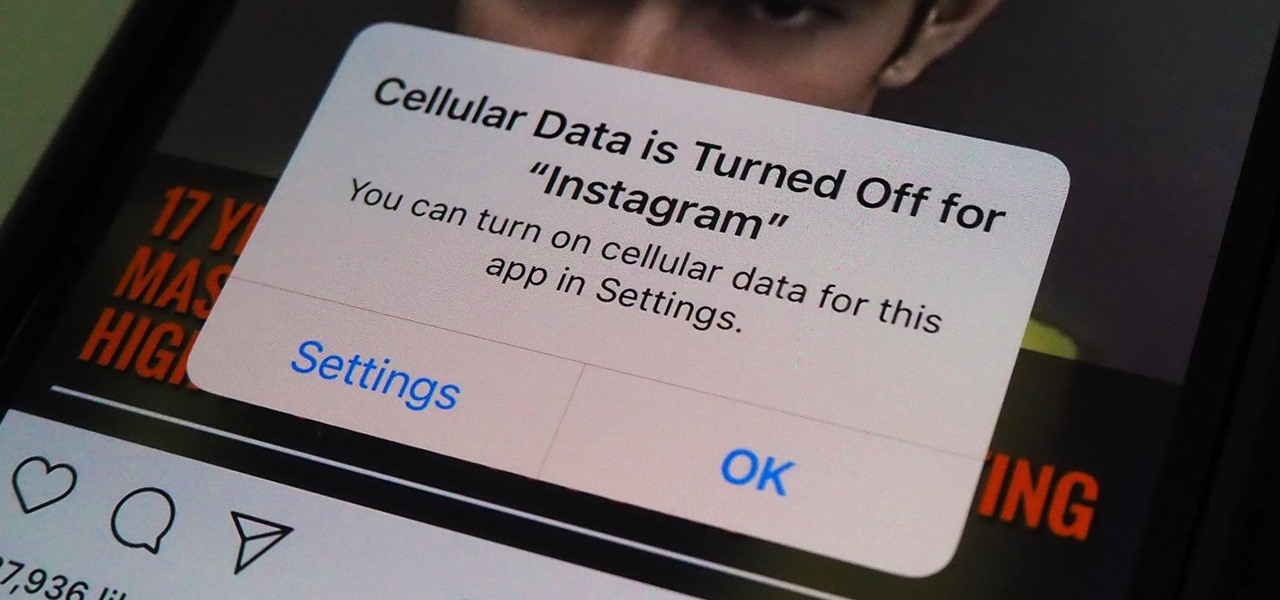
Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

To say we're a nation of coffee-lovers is putting it mildly. Americans consume 400 million cups of joe in one day alone, but how well do we actually know our morning BFF? We know it comes from a bean, and that more coffee drinks exist than there are ways to skin a pig, but what else?

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

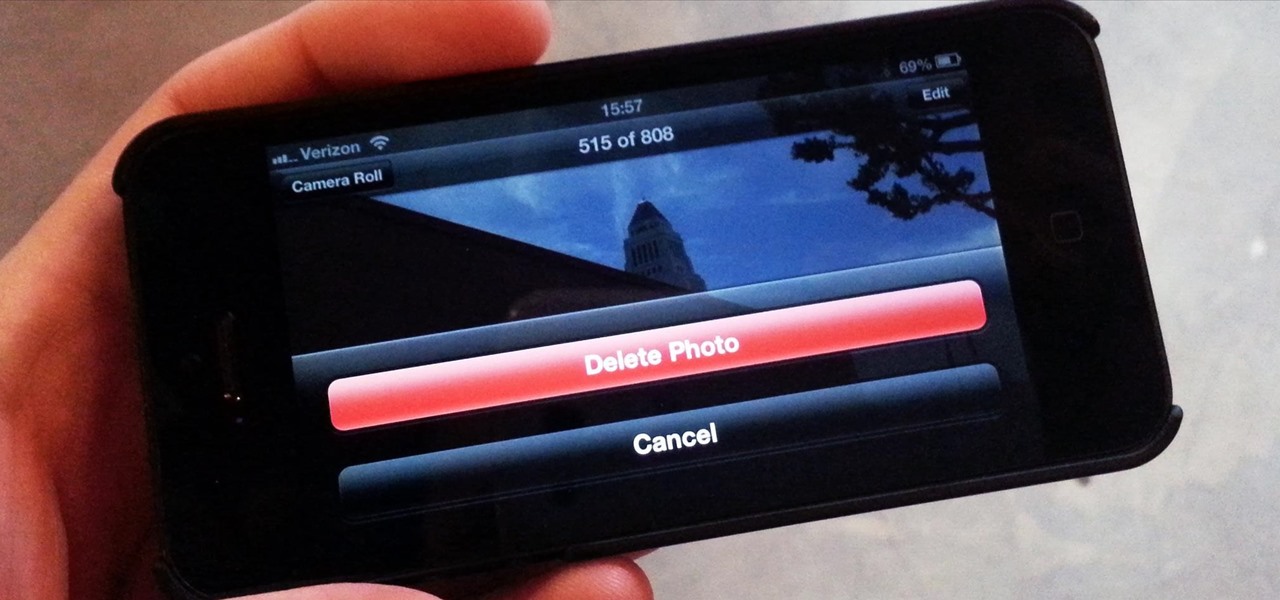
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

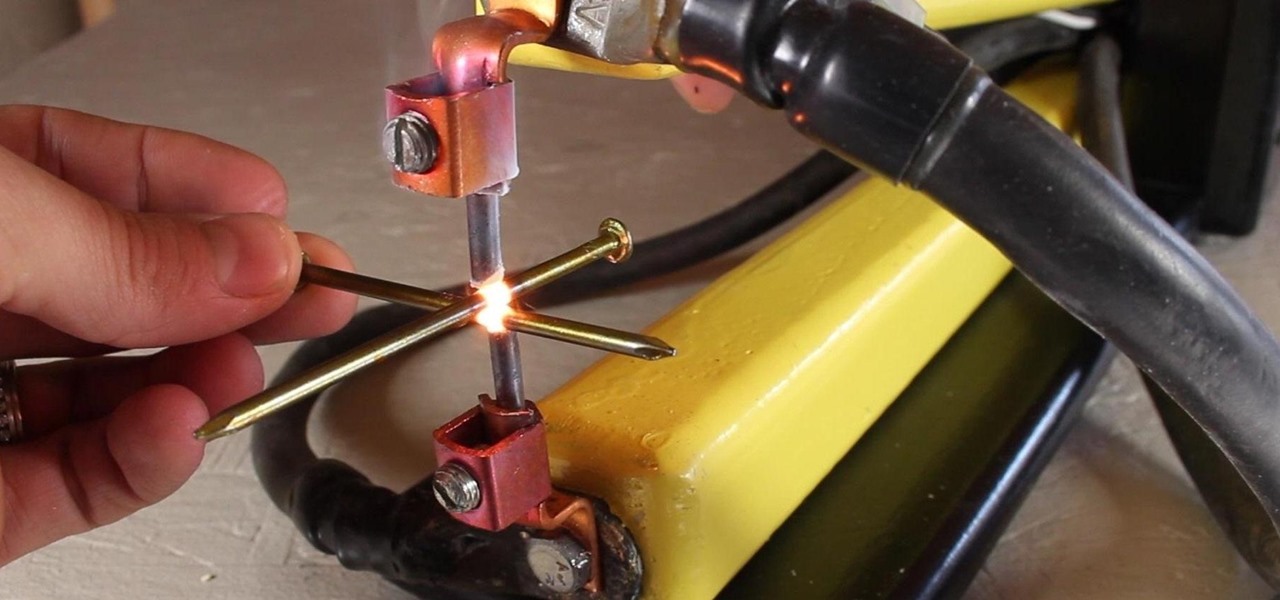
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

Important emails can slip through the cracks in any email client, especially sent emails you were expecting responses to but never received — and ultimately forgot about. Apple has an easy solution for this problem, helping you get answers in Mail for all your pending questions.

The mission to rise above the fray to become a leading player in the augmented reality business is a moving target that depends on innovation, resources, and timing.

The team over at Spatial isn't done innovating its way through augmented reality in 2020. Just days after adding a mobile option to its groundbreaking Spatial virtual collaboration product, the company is releasing Tele, a new app geared toward more casual, AR-powered video chats.

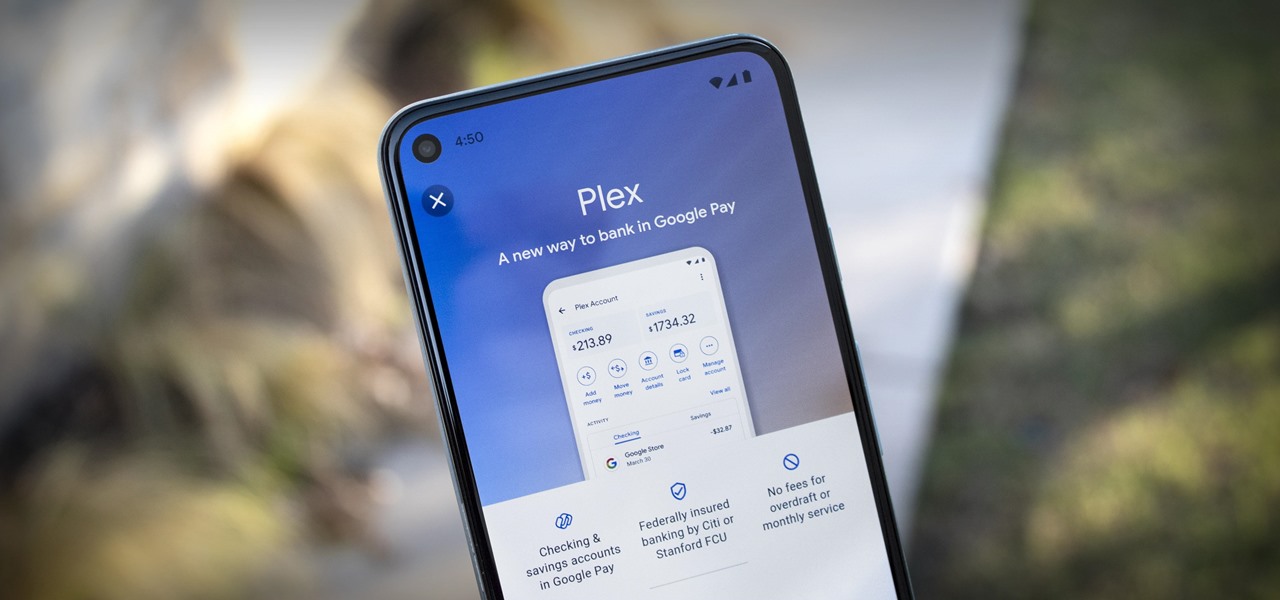
Not only has Google released a completely new Google Pay app for US users on both iPhone and Android, but the've also minted a new mobile banking service. Called Plex, it provides online bank accounts at one of 11 partner banks and credit unions, with no minimum balance requirements, overdraft charges, or monthly fees.

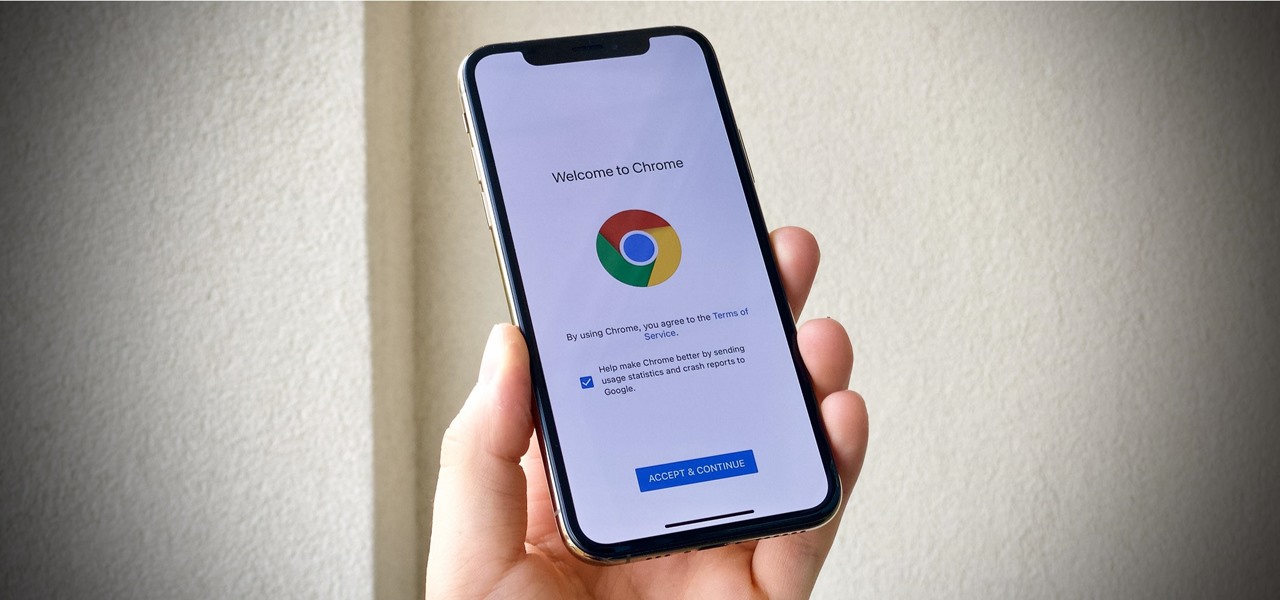
For the longest time, we were simply stuck with Safari on the iPhone. Sure, you could install a third-party browser, but Safari was always the default, so tapping on links would always open Apple's app. Times have changed, however, and now you can set third-party browsers like Chrome, Firefox, and Edge as your iPhone's default choice.

If you're on a cellular plan with a low data allotment, being thrifty with your data can help you avoid a higher bill. But even if you have an affordable unlimited plan from wireless carriers such as T-Mobile or Verizon, going over a certain amount of data may throttle your connection, leaving you with slow web speeds. One way to prevent hitting these thresholds is to keep certain apps in check.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.

There's an official way to install apps onto your Android phone using basically any device that has internet access — heck, you can even download new apps from an iPhone and they'll install in seconds on your Android device.

Google lets you change the system-wide accent color on its Pixel devices, but the options are a bit muted. If you'd like something more vibrant, developer Tulsadiver created a mod that will give you a wide selection of punchier colors.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

So the new iPhones have arrived. Like last year, Apple released three iPhones in three different sizes that vary in price and specs. There's the base model iPhone 11, and then there are the real deal, premium models, the iPhone 11 Pro and Pro Max.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

For years, iPhones have had haptic feedback, but Apple didn't incorporate it into the stock iOS keyboard until iOS 16. To use keyboard haptics in iOS 15 and older — or as an alternative to the default keyboard's in iOS 16 — you can take advantage of third-party keyboards like Gboard.

The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

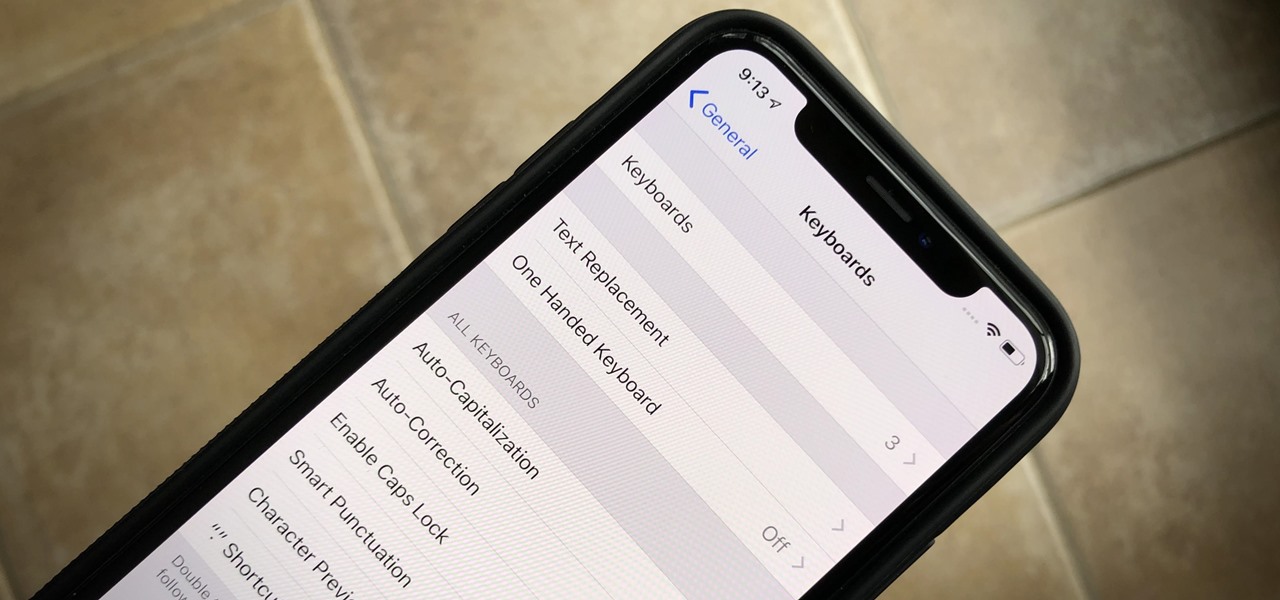
Apple introduced third-party keyboards back in iOS 8, and swipe-input options like Gboard, SwiftKey, and Swype made typing on an iPhone one-handed much easier. Even better, apps like Word Flow moved the keyboard to the side of the iPhone, so there was less thumb-stretching. Well, ever since iOS 11, Apple has had its own option for better one-handed typing in the stock keyboard.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.