Need a little help with your new Adobe Photoshop graphics editing program? Working with Photoshop can be a bit tough if you don't know what you're doing, so instead of getting out the books, check out this 'no nonsense' video tutorial to learn how to create metallic looking objects in Adobe Photoshop. Photo manipulating and editing is always tricky, so just watch to see how to create metallic looking objects, for beginners.

Need a little help with your new Adobe Photoshop graphics editing program? Working with Photoshop can be a bit tough if you don't know what you're doing, so instead of getting out the books, check out this 'no nonsense' video tutorial to learn how to create and use patterns in Adobe Photoshop. Photo manipulating and editing is always tricky, so just watch to see how to create and use patterns, for beginners.
Don't pay for virus protection. You can get basic non-intrusive virus protection from Avira. Check out this quick video tip from Tinkernut to see how and where to get the Avira free anti-virus software program for free!
Dissect the object of its parts. Select the curves to rotate, model or scale the whole character. The Maya hot keys are as follows: W translates, R scales and E rotates.
Check out this tutorial on using motion tweening on a path in Flash. This is a basic tool for creating animations.
This is a tutorial video from Sessions Online Schools of Art & Design's "Photoshop Basics" course. This video is part of Sessions' Graphic, Web, Multimedia Arts, Digital Arts, and Marketing Design certificate programs. You are distorting layers using the transform tool. Use the line tool to check the work. GO Edit: Transform - Distort.

This video shows you how to oil piston valves on trumpets and all brass instruments from NAPBIRT and the Band Instrument Repair program at MN State College-SE Technical. This is an excellent video for learning about musical instrument maintenance and repair. Keep your horns in tip top shape with these oiling instructions.

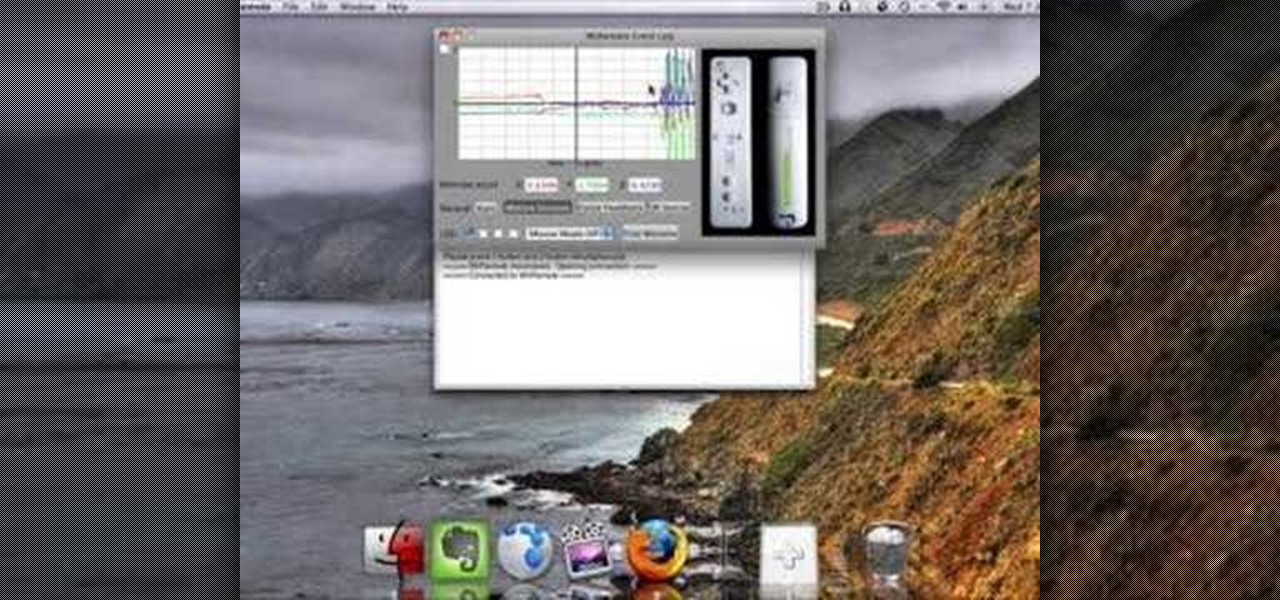
This shows a step by step method for using the Wii controller to output MIDI control to Apple Logic Pro and "conduct" MIDI with the Wii stick! This is a way cool Wii hack that makes the bluetooth controller work with Logic. You need to install another program to receive and control the data.

Here is a Neuro Linguistic Programming (NLP) anchoring technique to help you neutralize negative thoughts and emotions. NLP anchoring is a simple, yet safe and powerful tool for self improvement and growth.

Make it harder for spammers to clog your inbox with ads and scams. Learn how to avoid spam email with this Howcast video. You will need a secondary email address, a keen eye, and an anti-spam program. Tip: Never click on links in spam email - including "unsubscribe" links, and never, ever reply!

Here's a demo which shows a way to produce WAV sound files with TEXT using Photoshop or any photo editing software.

Project 5 from Popular Science's 5 minute Projects with Craftsmen Tool is 'Integrated Circuit Cufflinks'.

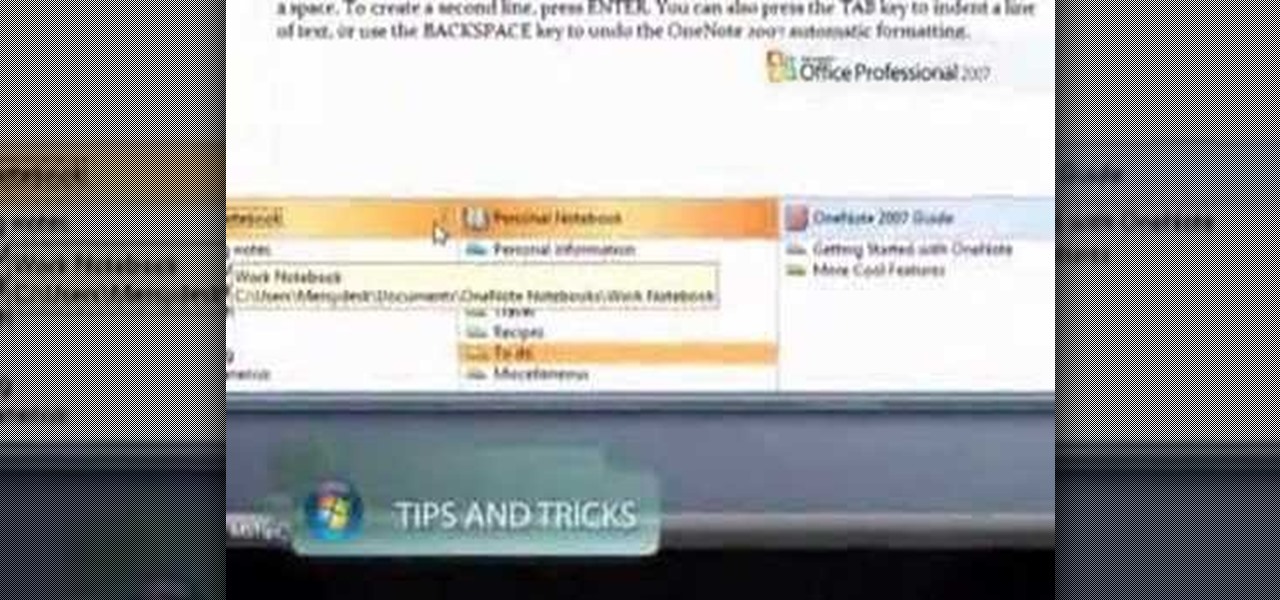
Do you ever wish you had a way to jot down an idea, and then illustrate it with a page from a document, a photo and a sound clip, all without opening multiple applications? Microsoft Office OneNote 2007 note-taking program is that advanced notepad, and is better than ever with new additions to the interface that make it even easier to organize yourself. For more on using MS Office OneNote, watch this video tutorial.

This image editing software tutorial shows you how to create an array from a rasterized object in Photoshop CS3. An array (in design terms, not programming terms) is an object that duplicates itself around a pivot point. So learn how to work with arrays to create designs in this Photoshop video.

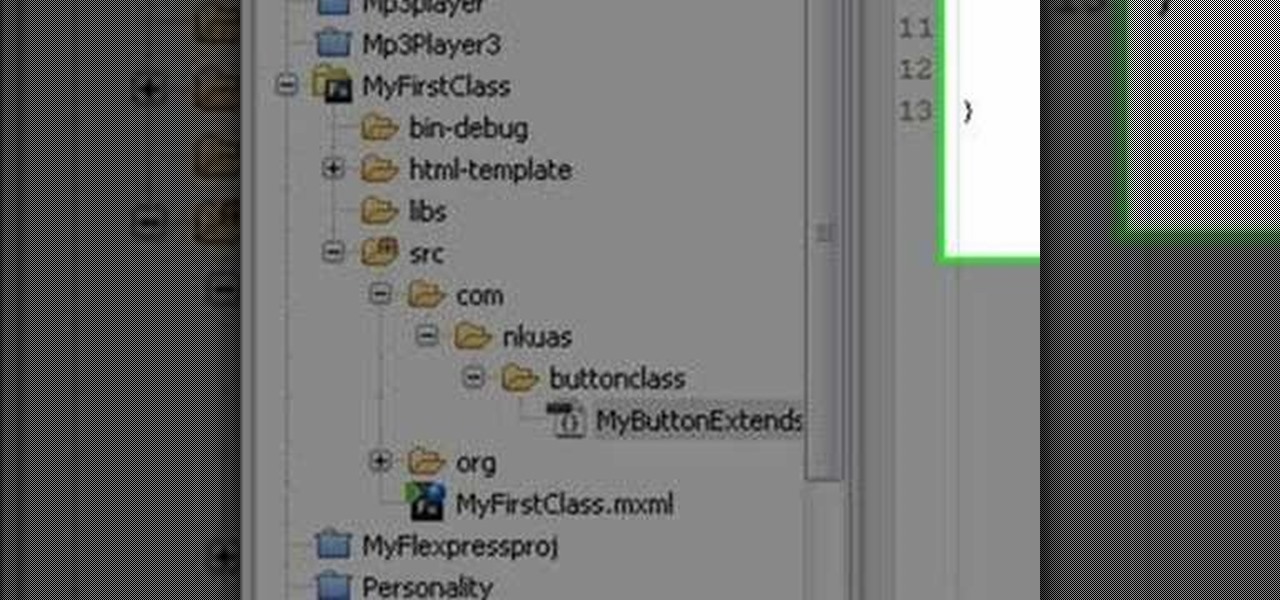
In this programming tutorial, Mike Lively of Northern Kentucky University explains the six parts of a Flex 3 class. He demonstrates how to create and extend a class using Flex 3, and how to bring that class into a Flex project using xmlns name space. Learn how to work with custom classes in this beginners Adobe Flex Builder 3 tutorial.

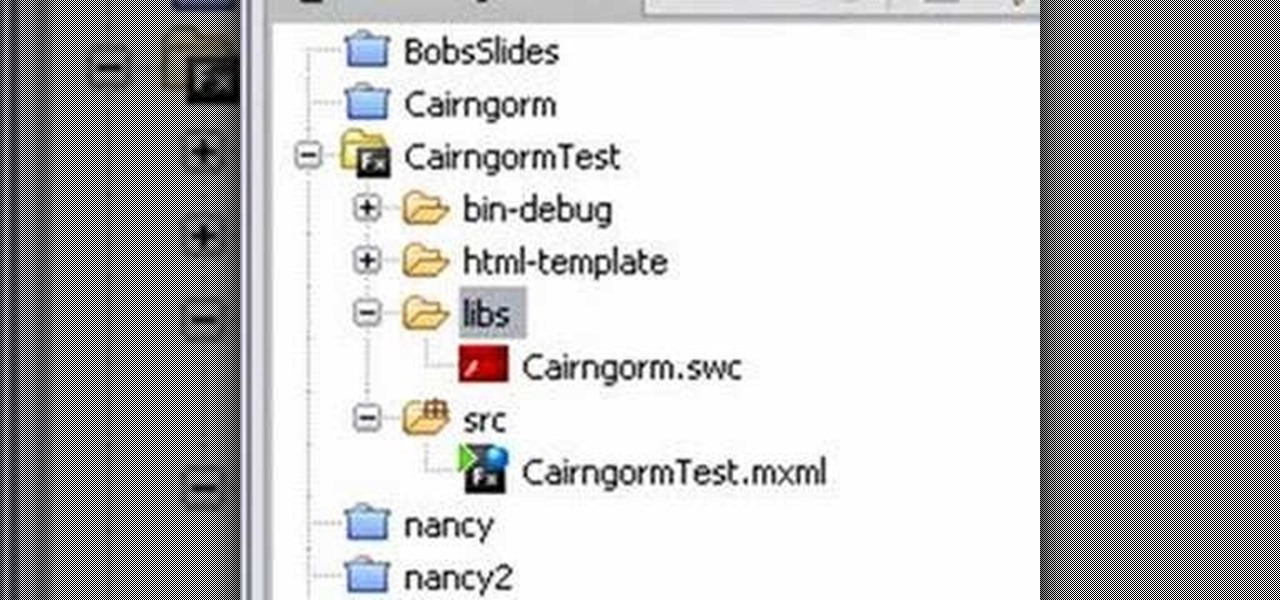
In this tutorial, Mike Lively of Northern Kentucky University discusses the MVC (Model Viewer Controller) architecture, installs Cairngorm into Adobe Flex 3, and discusses one of David Tucker's examples. The MVC model is comprised of a Model (encapsulates information from the d base (XML file), View (presentation layer that the user interacts with, and Controller (processes and responds to events and invokes changes to the model and viewer). See how to use the MVC model and install Cairngorm ...

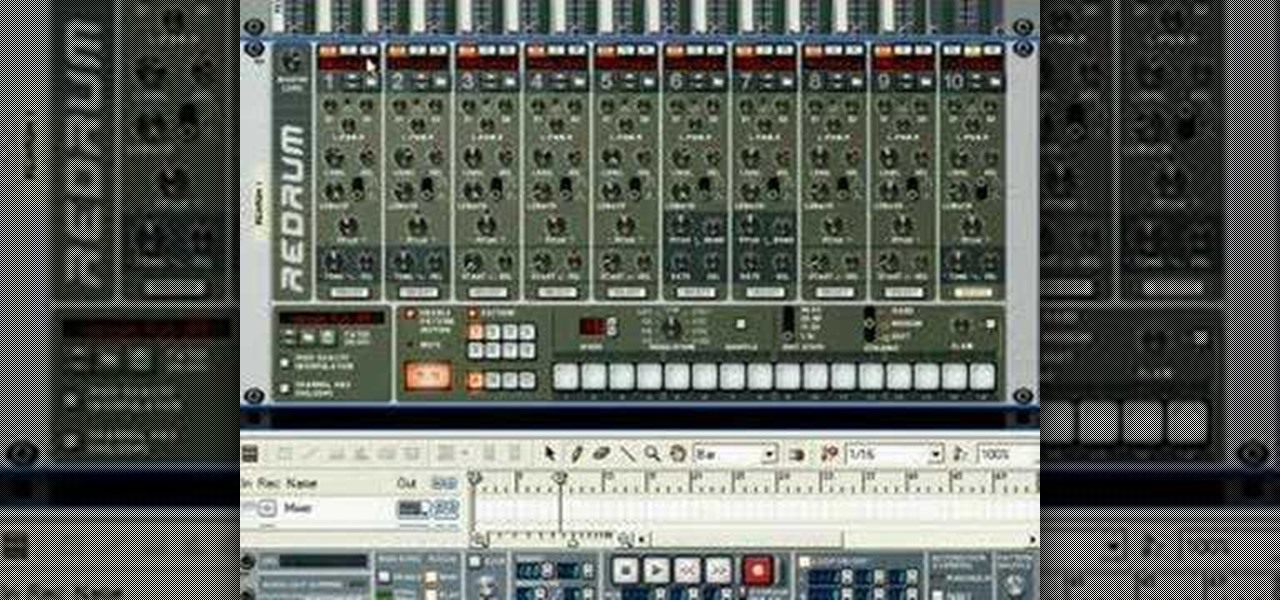
There are many ways to program or automate the redrum in Reason. This music production tutorial looks at an innovative way to auto-quantize using the Drum Solo options. Watch and learn this easy keyboard setup with a lot of potential for ReDrum in Reason.

This music production tutorial covers ADSR and AHDSR envelopes, how to understand and implement them in Reason, FL Studio, Reaktor and almost every piece of music software. The tutorial shows you how to work with envelopes in each program and includes several takes on common use. If you are new to midi sequencers and synthesizers in Reason, Reaktor, FL studio etc., watch this important tutorial on using ADSR and AHDSR envelopes.

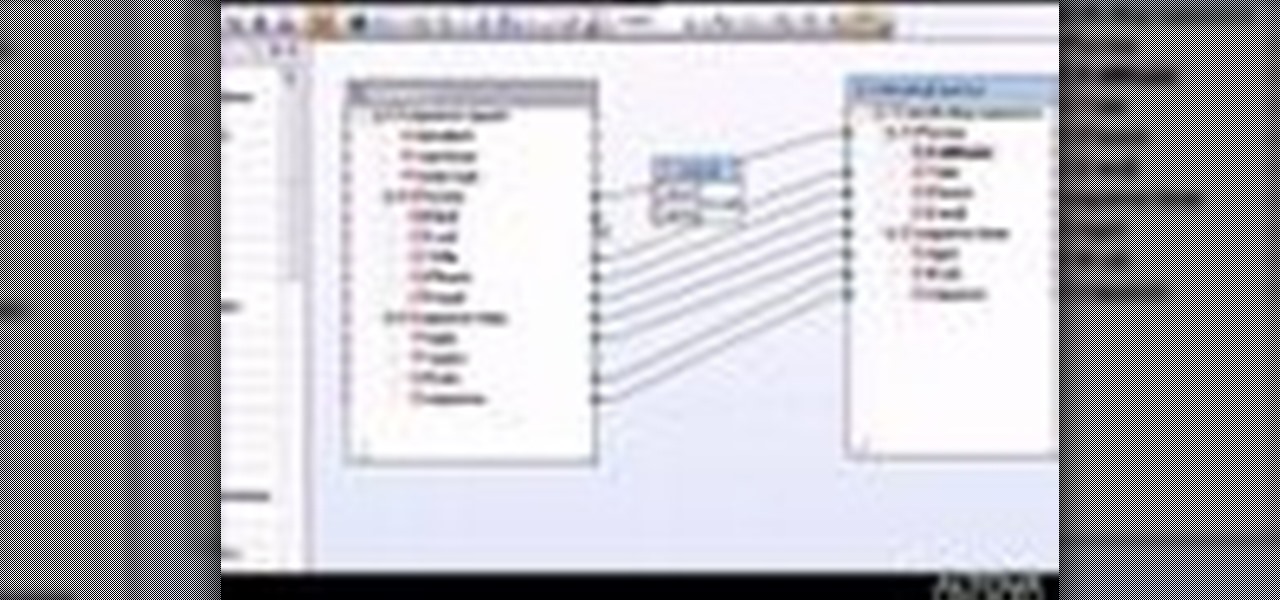
Learn how to use MapForce to map or transform XML data in a visual way, creating XSLT 1.0 or 2.0 transformation stylesheets, XQuery 1.0 documents, or program-code in Java or C# in this tutorial, which demonstrates a simple mapping from one XML schema to another. Take a look!

When performing this iPod hack, make sure to turn off your iTunes and keep it from popping up after you've plugged in your iPod via USB. Take a look at this tutorial and learn how to hack into you iPod on your Mac with the program Alterpod. With luck, no error log will pop up once you click restore.

Following the immediate release of the Nintendo's Wii, many people speculated whether or not the interaction with the Wiimote would only last as long as the novelty did. Naturally, the Wiimote requires to be reconfigured now and then given its heavy use. Take a look at this instructional video and learn how to configure your Wiimote on your Mac with a free program known as Darwinremote.

Use this freeware program from Bill Myers to prevent bandwidth theft of your videos - any format and stored on any site - including Camtasia videos stored on Amazon S3.

Learn how to do a cable triceps press down drop set. Presented by Real Jock Gay Fitness Health & Life.

Watch this video to get an introduction to C++, and learn how to make a 'Hello World' application.

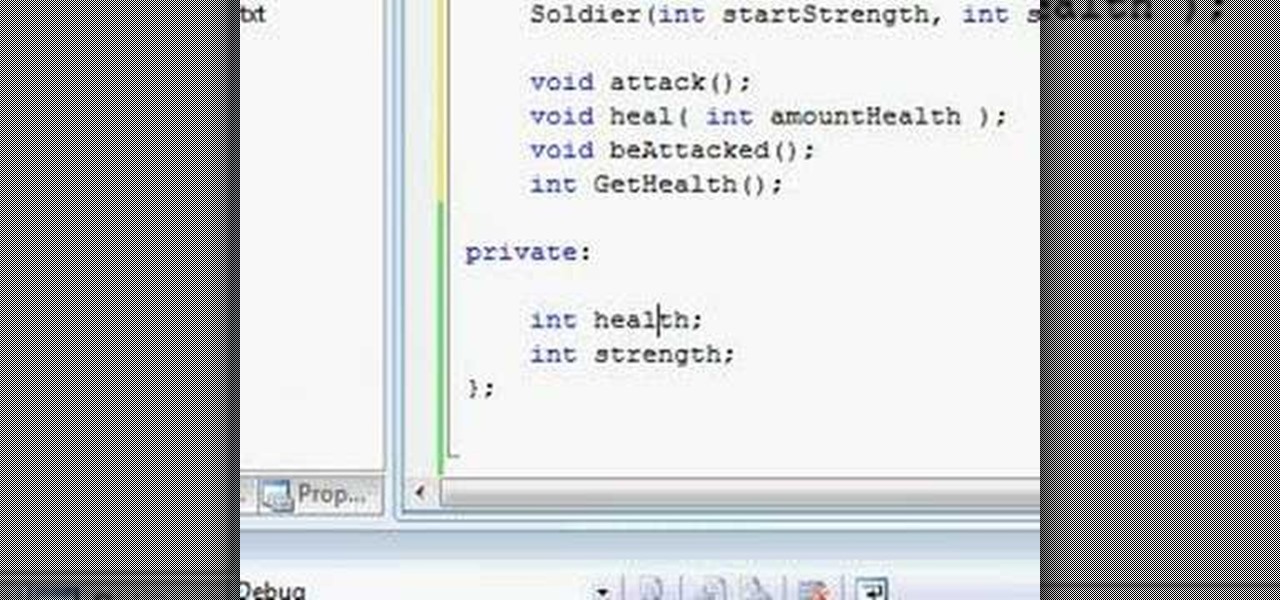
Watch this video to learn how to use OOP encapsulation in C++. Other topics included in the video include class declaration/definition.

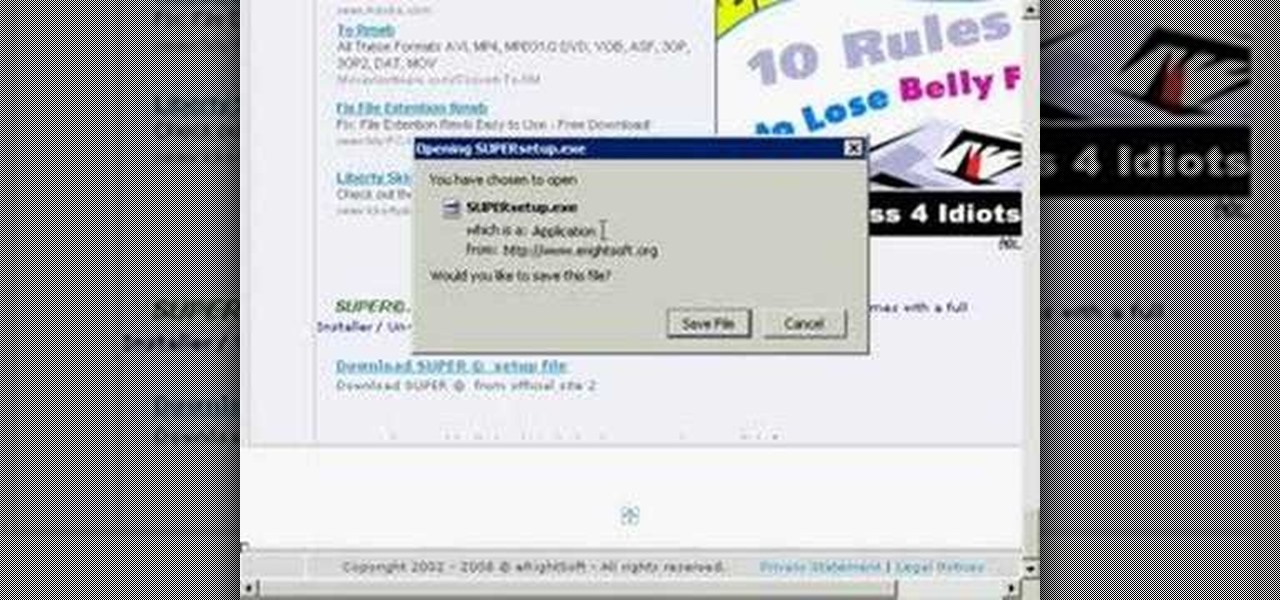
SUPER Converter is a program for Windows XP that can convert a variety of audio and video formats. Here's how to download and install it.

Here's how to find and use Free Public Domain Movies and old TV commercials in your work. Also in this episode, a few inexpensive utilities that will convert video formats so they are ready for editing in your editing program of choice.

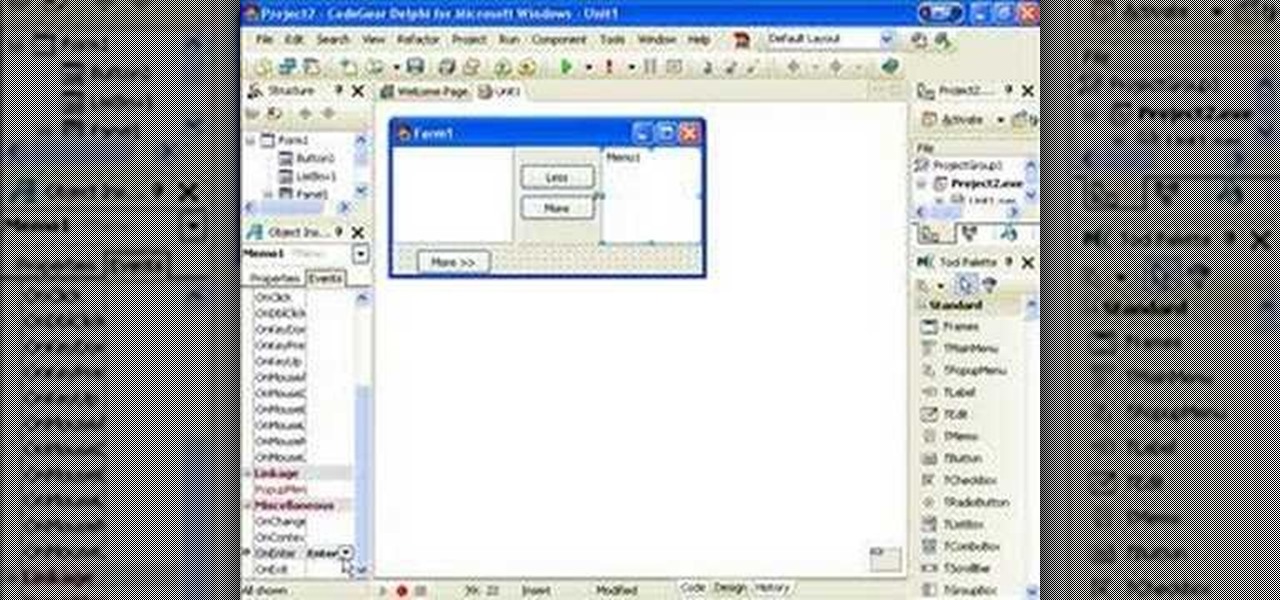
This VB.Net tutorial teaches you some tricks with duel forms and how to do create very basic password protected applications.

In this episode of Ask the Techoes, D.Lee and Brandon answer viewer questions on how to defrag a Mac hard drive, erasing an NTFS hard drive on Mac OS 10.4, how to uninstall programs and their related files on a Mac, questions with Parallels, and how to create a wireless USB hub. Send us your questions at askthetechies@gmail.com Hosts: D.Lee Beard & Brandon Jackson http://AskTheTechies.com

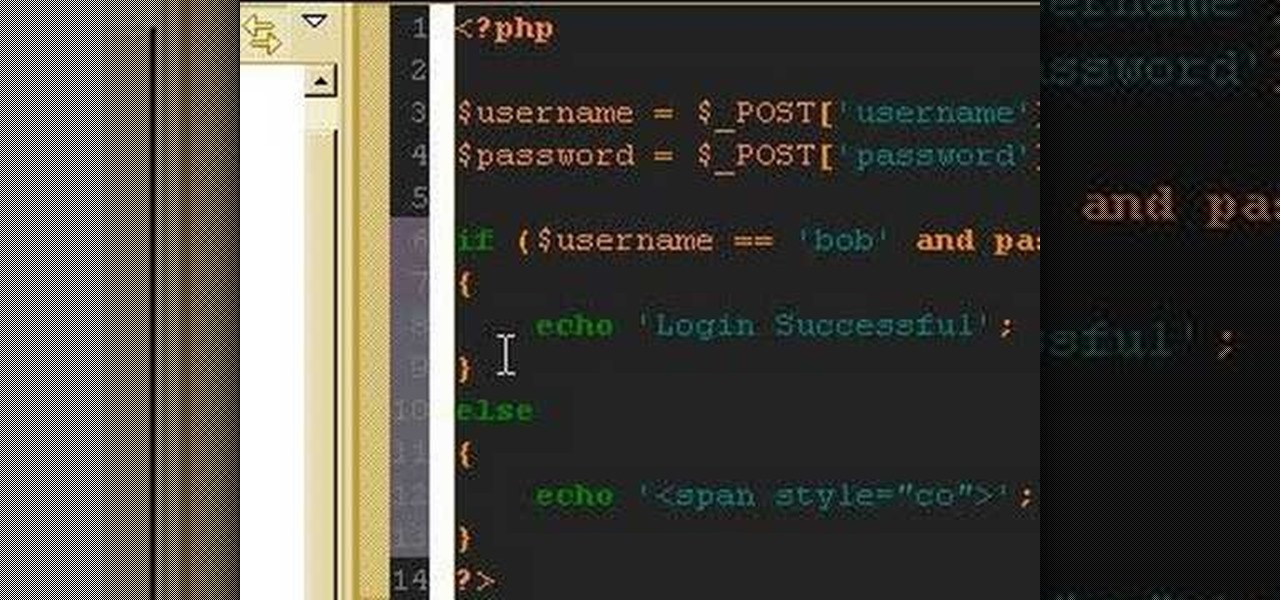
Using PHP & HTML to generate a user login form and authenticate the user.

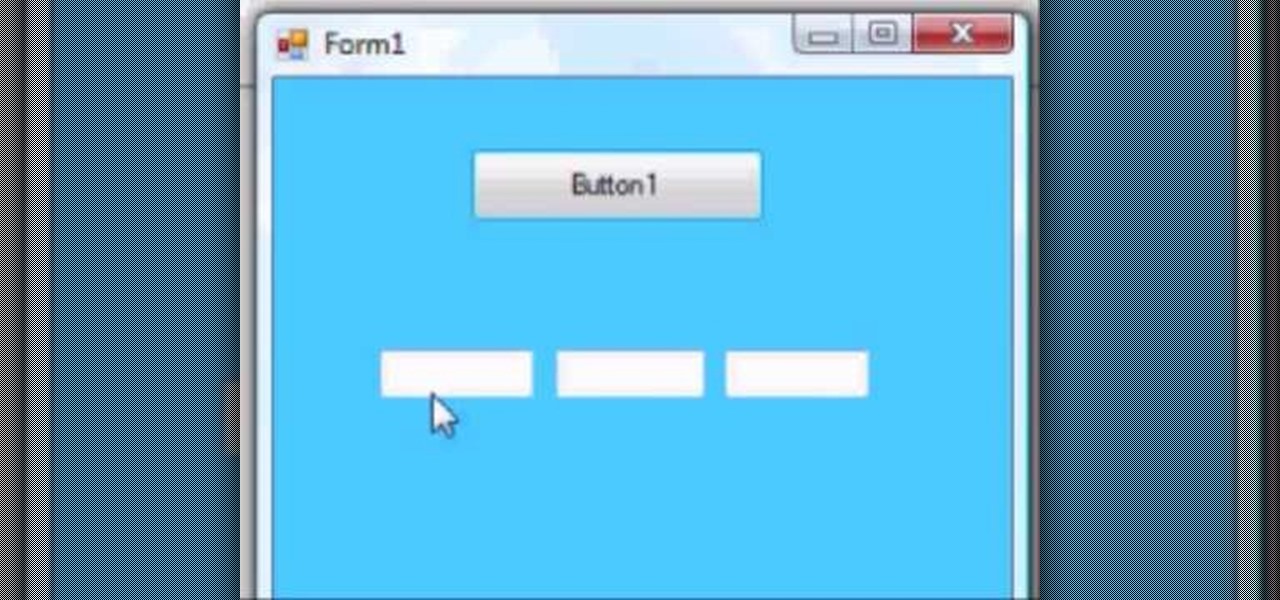
Here we'll take a look at an example of using the Autosize property on a form to make it resize in response to its controls

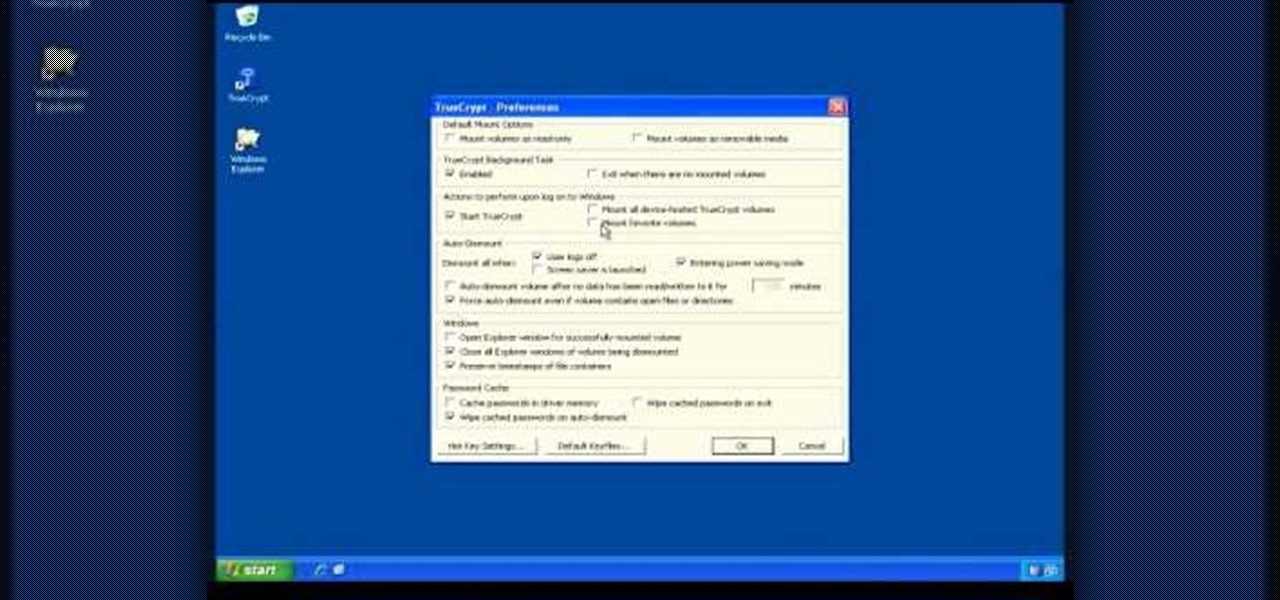
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

Rich DeMuro from CNET shows you how to use Apple's Boot Camp program to get the best of both worlds by configuring your Mac to run two operating systems.

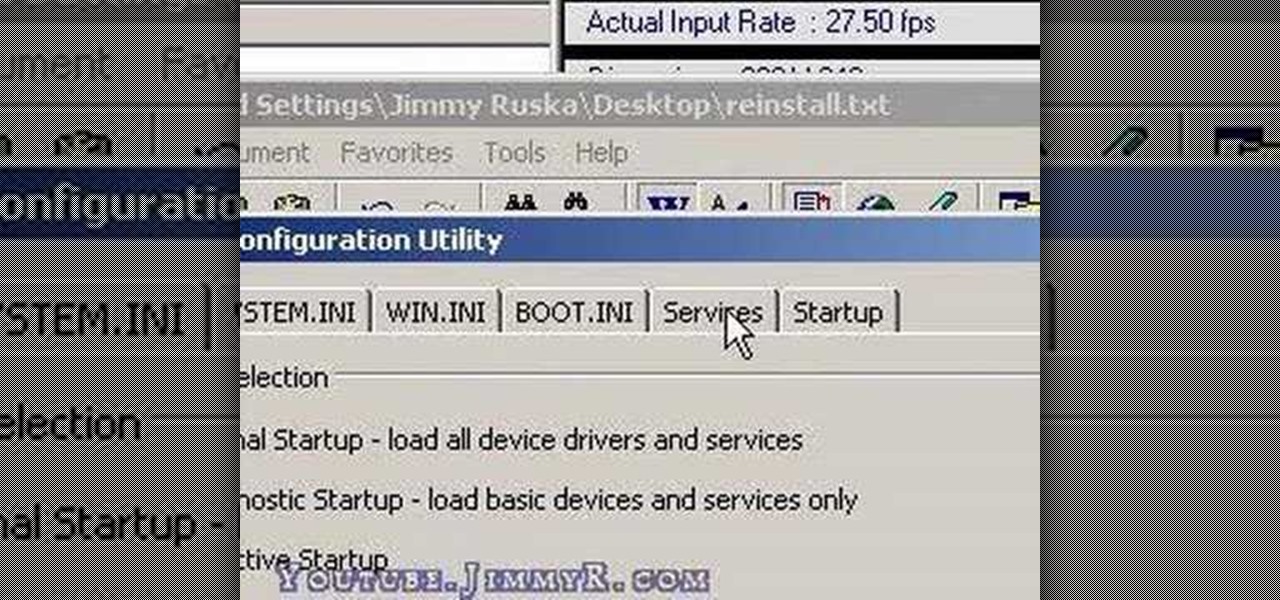
Have you just installed Windows or are you looking to improve Window's performance. Learn how to make Windows function faster and more efficiently by adjusting system settings and using a few free tweaking programs.

Virtual CD technology allows you to copy CDs and DVDs to your hard drive so that you can play them without a disk. Learn about ISO files and how to use a virtual drive program like Daemon tools to create and open them.
The Minnesota Department of Public Safety issued a press release today announcing the suspension of a drug recognition program conducted by the Minnesota State Patrol. The program was exposed earlier this month by activists and members of Communities United Against Police Brutality in Minneapolis.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

The world has been overflowing with Microsoft Kinect hacks, each more amazing than the last. The latest innovation, created by a group of engineers at USC, promises an exciting future in gaming (and gets gamers off their asses). The program is called FAAST, and allows for full body motion control in different PC applications, such as World of Warcraft, as demonstrated below: Previously, Hacked Kinect Captures 3D Video in Real Time.

In this clip, you'll learn how to create an eye-catching fog effect when working in MS Visual C++. Whether you're new to Microsoft's popular general-purpose programming language and IDE or are a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free, official video tutorial. For more information, including detailed, step-by-step instructions, take a look. Create a fog effect when creating an OpenGL program in MS Visual C++.