Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Tagine is both the name of a cooking vessel and also the dish that is cooked within it. In fact, some might say tagines are the national dish of Morocco. These slow-cooked stews and braises, often combining meat, vegetables, spices, and dried fruits, have a character unlike anything I've ever eaten.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Most people give their fruits and veggies a cursory rinse under the faucet before eating or cooking them, but is that few seconds under running water really enough to remove any remaining dirt, pesticides, or wax clinging to the surface?

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

When it comes to milk, my family consumes anywhere between two and four gallons every two weeks. That's about four to eight gallons every month. That's a lot of milk—and a lot of empty milk jugs! Instead of simply tossing them in the recycling bin, why not get creative and make something useful out of them yourself?

Magic tricks are a fun way to pass the time or entertain a group of friends. The ball and vase trick is easy to learn using the basic principles of magic trick deception. Pick one up and start spreading joy and wonder to people near you.

Another name for jumper's knee is patellar tendinitis. Jumper's knee is an injury that affects the tendon connecting your kneecap (patella) to your shinbone. The patellar tendon plays a pivotal role in the way you use your legs. It helps your muscles extend your lower leg so that you can kick a ball, push the pedals on your bicycle, and jump up in the air. Learn about the different causes of, symptoms of, and treatments for jumper's knee in this video.

The trick in this how-to video works with any carbonated beverage (never use beer). Take your beverage and cool it down to a temperature around 20F or -7C. Either the freezer or outside if it is cold enough. When opened it will freeze instantly.

In this free video series on how to animate drawings, learn the basic techniques and principles behind capturing your artwork.

In this video series on how to draw animated cartoons, learn the fundamental techniques and principles that guide the development of any animation idea.

In this series of kitsch avante garde instructional music and space sounds videos, our theremin expert explains the basic principles of this bizarre instrument. He also tells you how to operate the controls and even demonstrates how to coax a song out of it. Join Brain Wilson, John Spencer and any number of science fiction soundtrack composers on the evergrowing bandwagon of theremin disciples.

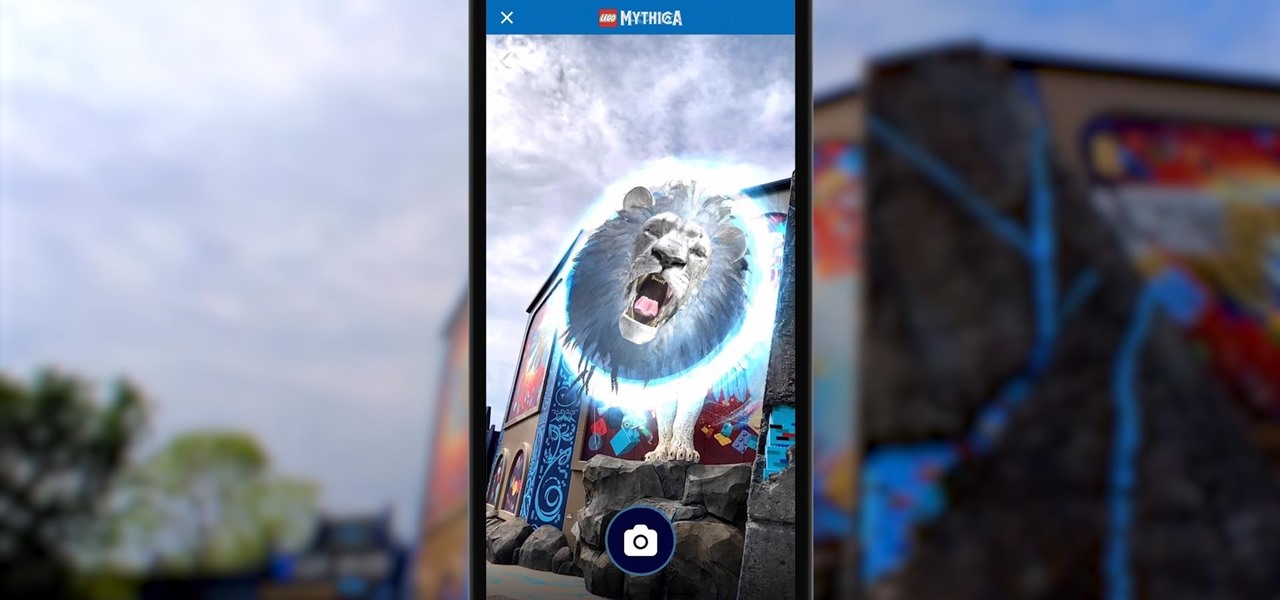
Few brands have been more enthusiastic about augmented reality than Lego, which has now expanded its AR experiences from toys to theme parks.

White or light-colored dinnerware is a classic: it looks crisp, clean, and elegant. The only problem is that after you've used it for a few years, the surfaces bear a lot of grey scuff marks from forks, spoons, and knives being dragged across the surface.

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

Create positive home energies with feng shui astrology. Learn how to incorporate ancient Chinese traditions with modern feng shui principles to decorate and design a comfortable living space with this free video series from a leading feng shui practitioner.

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

In the Android community, there's a lot of discussion about how display notches should be used. For some, hiding the notch is more appealing, but others feel that hiding it wastes screen real estate. Well, Essential just provided another solution that should satisfy both sides.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.