
Did you know there's a way to make animating your own cartoons that's way easier than it looks — and that you can learn all the skills you need from home? Whether you want to pick up a fun, creative hobby over the holiday season or learn the skills to start working in animation, The Ultimate Cartoon Animator 4 Pro Mac Bundle will have you quickly making your own cartoons. Right now, it's on sale for 74% off, at just $49.99 (regular price $196).

Who doesn't love cartoons? Whether you want to take up a creative hobby over the holidays, learn animation for an exciting new side hustle in 2021, or buy the dream gift for the person in your life who loves all things animated, this deal is one to take advantage of today. Right now, you can pick up The Ultimate Cartoon Animator 4 Pro: Windows Bundle — with an amazing 74% discount — for just $49.99 (regular price $196).

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.
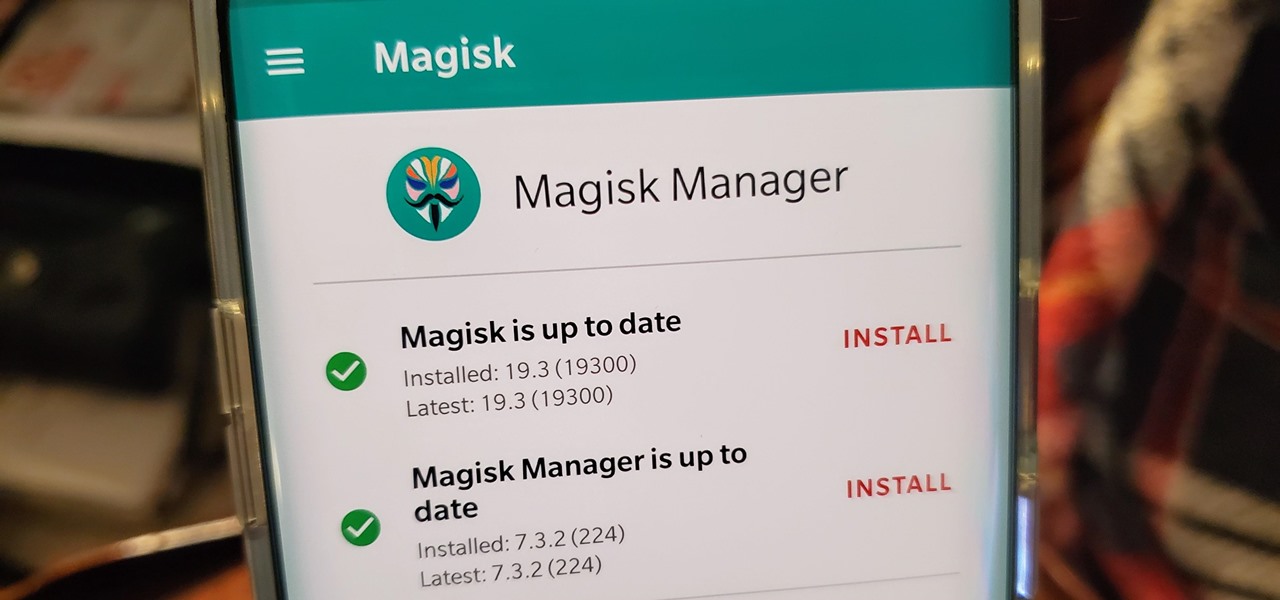
OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.
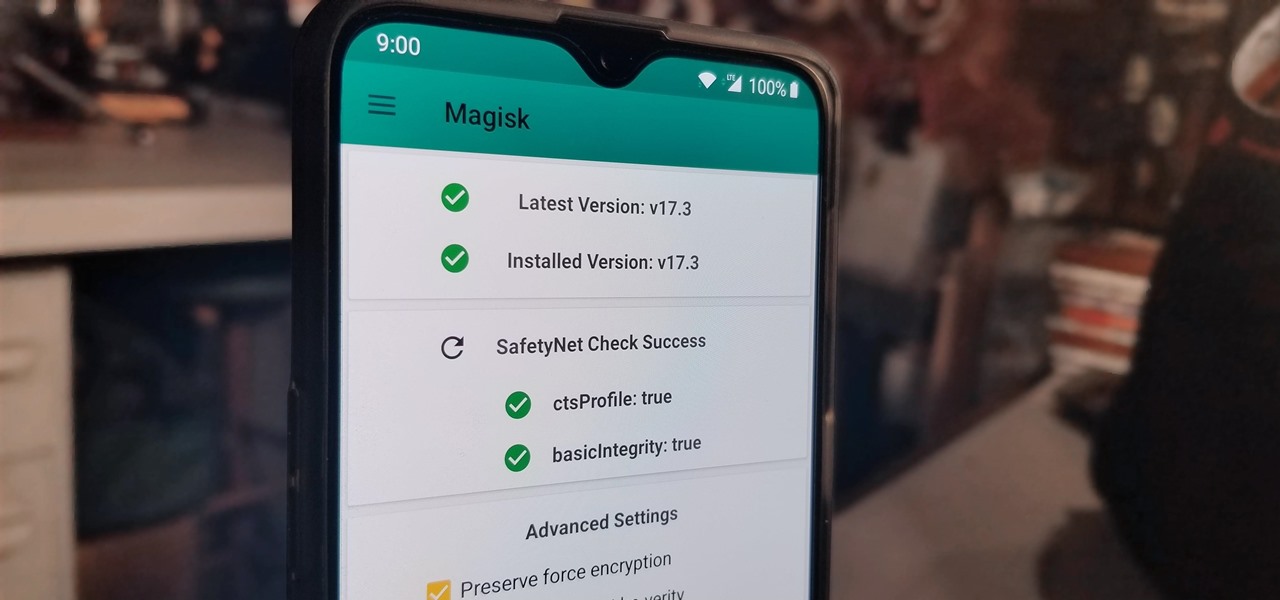
With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Tagine is both the name of a cooking vessel and also the dish that is cooked within it. In fact, some might say tagines are the national dish of Morocco. These slow-cooked stews and braises, often combining meat, vegetables, spices, and dried fruits, have a character unlike anything I've ever eaten.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Most people give their fruits and veggies a cursory rinse under the faucet before eating or cooking them, but is that few seconds under running water really enough to remove any remaining dirt, pesticides, or wax clinging to the surface?

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

When it comes to milk, my family consumes anywhere between two and four gallons every two weeks. That's about four to eight gallons every month. That's a lot of milk—and a lot of empty milk jugs! Instead of simply tossing them in the recycling bin, why not get creative and make something useful out of them yourself?

Korean cuisine is largely rice-based, like many other Asian cuisines. One distinguishing characteristic, though, is the profusion of side dishes present in Korean cooking. In this Korean food video series, learn how to make an easy recipe for gimbap, a dish almost like sushi—except that it often does not have a raw fish component. Our expert will show you step-by-step how to put this recipe together, including a list of ingredients, rice cooking tips, how to steam the spinach, how to cook the...

Korean cuisine is largely rice-based, like many other Asian cuisines. One distinguishing characteristic, though, is the profusion of side dishes present in Korean cooking. In this Korean food video series, learn how to make an easy stew recipe called kimchi chigae. This dish’s main ingredient is kimchi, but it calls for kimchi that has been sitting around a bit longer. An increased amount of fermentation is a desirable quality that affects the flavor of the stew significantly. Get step-by-ste...

Create positive home energies with feng shui astrology. Learn how to incorporate ancient Chinese traditions with modern feng shui principles to decorate and design a comfortable living space with this free video series from a leading feng shui practitioner.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

Primarily caused by the bacteria Borrelia burgdorferi, Lyme disease is the most common tickborne disease in the US. By all predictions, 2017 is expected to be a banner tick year in several regions. If you have children, it is important to know what to expect.

Samsung and Apple are back in court, but this time it's not just money at stake. The Supreme Court's decision could have a far reaching effect on patent law and innovation in design.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Learn music theory from music instructor Mark W. Black, owner & founder of "Promethean Studios" Dallas, as he teaches basic essentials of music theory for beginners in this video series. Mark covers such topics as: the staff, treble clef, bass clef, how to identify notes on the staff, measure, pitch, the quarter rest, ledger lines, notes above the staff, half-notes and whole-notes, counting beats, rests, intervals and counting intervals, half-steps, guitar half steps, characteristics of Weste...

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.








































