
How To: So, You're a Steampunk… Now What?
Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!


Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

One of iCloud Photo's biggest perks is its ability to store large video files taken with your iPhone, so you can fill up your iPhone's storage with other items. That said, when you play back those videos, you may not be watching the footage in its original quality. Instead, they may be low-res versions. To view the high-quality originals — or to make sure that's what you see — just follow this trick.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google Now, Voice Search, and Now on Tap rolled into one service, with an extra layer of personality added on top. The end result is one central location for all of your Google needs, be it web search, screen search, playing m...

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?
Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.
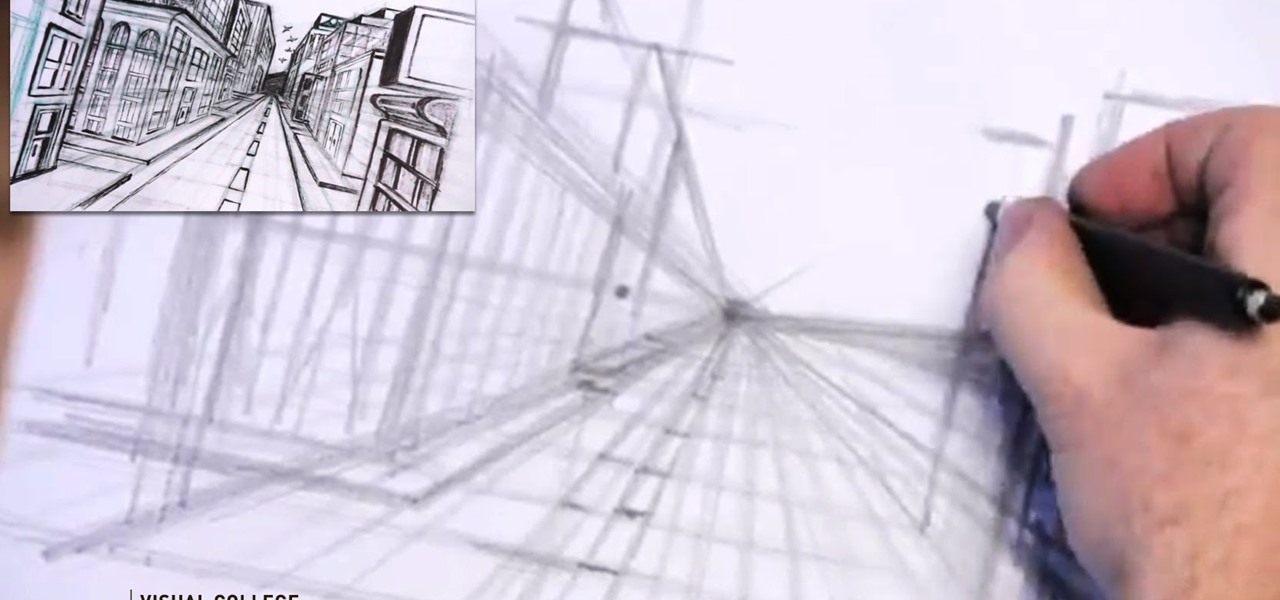
Video: . Step 1: Today We Are Going to Draw a City in One Point Perspective -- Buildings in the City Going into One Point Perspective. Let's Start Our Drawing with the Vanishing Point and Horizon Line. In Order to Get the Feel of the Drawing We Need to Determine Where Vanishing Point Will Be. Feel Free to Improvise and Change It Depending on What You Want to Achieve. Start Mapping Lines in.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!
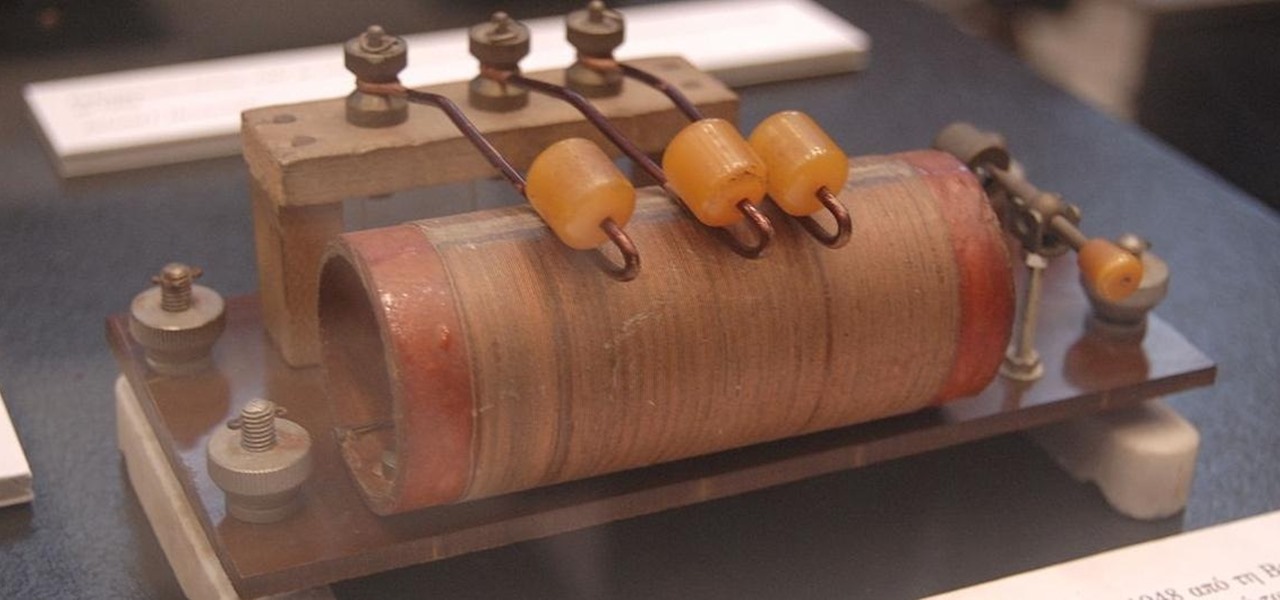
There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

Today is the 10-year anniversary of the death of Apple co-founder and former CEO Steve Jobs. To commemorate the occasion, Apple has posted a message and a mini-documentary on its website.
Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.