One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

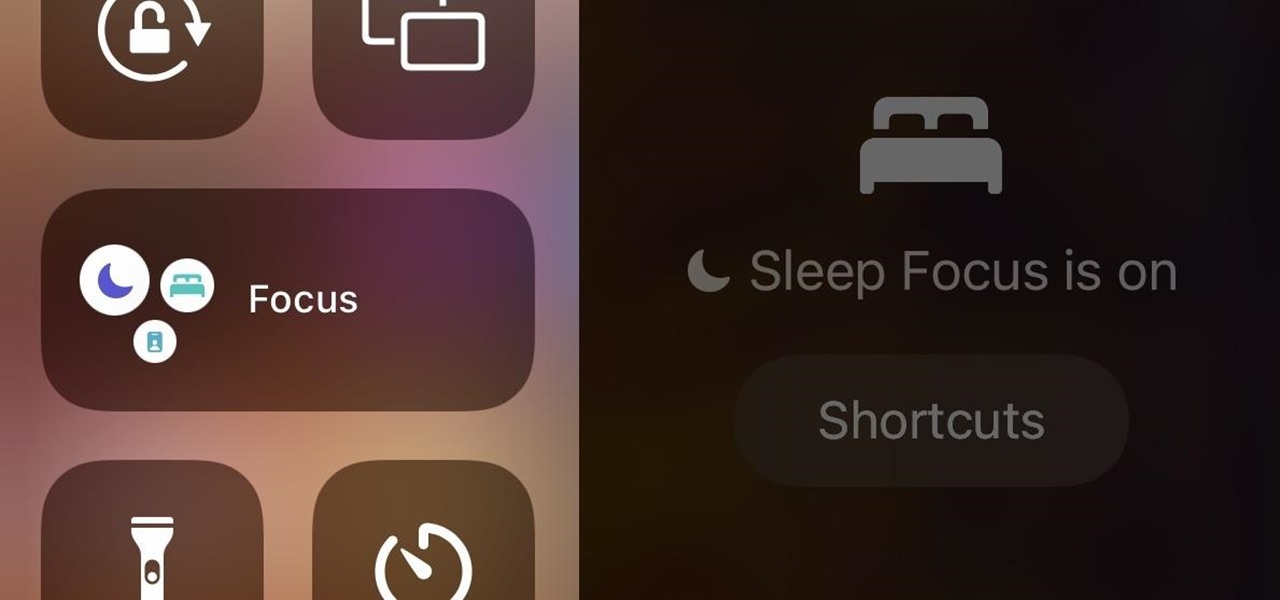
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

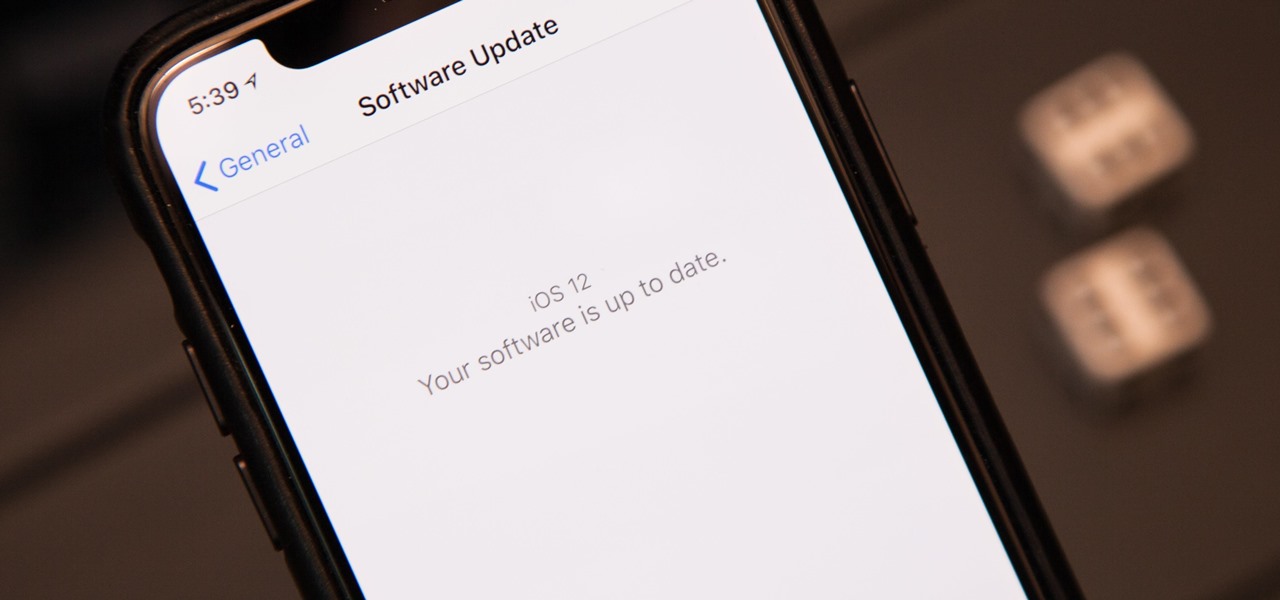
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

This video shows how to attract a man like a magnet! There are three powerful principles involved. Men are very attracted by confidence. It is not a question of acting confident, but of being confident. You need to practise thinking about what you like and appreciate about yourself. You should not try to impress a man because he can sense that you are auditioning for him. Principle number one is to stop trying to impress him. Men love to pursue a woman. Think about yourself as a flower and th...

In this tutorial, you will learn how to model a Ducati rear tire using Cinema 4D. We're sure the same principles will apply to any motorcycle tire you decide to model. The guy gives VERY detailed information about tires which should be helpful. Model a Ducati rear tire in Cinema 4D.

Singer and songwriter and singing teacher Jules Rendell takes us through the characteristics of pop singers like Beyoncé and Mariah Carey. She'll show you how to sing like an American Idol or X factor winner. Sing pop music.

Phillip Bourton explains how to open a computer and replace an optical drive without damaging any important components. He explains what characteristics should be considered when upgrading an optical drive, like type of drive and speed. Install an optical drive in a computer.

The Interactive Lab Primer (ILP) has been developed as part of the Royal Society of Chemistry Teacher Fellowship Scheme, one of the themes of the Chemistry for Our Future program, and initiative which aims to secure a strong and sustainable future for the chemical sciences in higher education. The aim of the ILP is to address the diverse range of experience and skills students bring with them to a university by offering a resource to support their transition from school to the university chem...

Double click an edge, select a loop. That's the main principle behind edge loop modeling in modo. Modo has an entire suite of edge tools available for modeling - this tutorial shows you the basics of edge loop selection and getting started with this method of modeling in modo. Edge loop model in modo.

The durability and aesthetic characteristics of brick patios and walkways make for the foundation of great spaces around your home. While installing brick walks and patios is not a difficult task, it may be rather time consuming depending on the size of the patio or walkway. When laying brick that will be walked on it is necessary to use paving quality bricks. These bricks are generally fired longer and at a higher temperature making them more suitable for a variety of weather conditions and ...

This is really cool. He goes pretty deep into the principles of magnetism before actually showing how his generator comes together and works. Great information.

there is no explanation, but this video does visually illustrate the basic principles of VAWT design and construction.

Do you love the internet? Me too. That's why you should learn about Net Neutrality. Though this video was made a few years ago, the basic principles have stayed the same, and Net Neutrality laws are currently on the tables of governments all over the world. Get informed and save the internet!

This is how to make a cheap fast 18 inch armature. The same principles could apply to making smaller armatures.

Say what you will, this wave-shaping safety pool's got heart. And, thanks to the principle of wave interference, quite a lot of other shapes besides.

These are a series of clips to show you how to deal with the different situations when turning right at traffic lights. In the U.S. or countries that drive on the right, these principles will apply to left hand turns. Deal with right turns at traffic lights - UK.

This how-to shows a great muscle combo workout: legs and abs. Men's Health, the preeminent source for fitness videos, breaks it down for you.

If you've ever been to an amusement park or carnival, or even just been on a stroll down the boardwalk or promenade, then you probably know exactly what a caricature drawing is—those cartoony depictions of people or things with extremely exaggerated or oversimplified features that create a comedic effect. Caricatures aren't just for street artists, though—they also work great for political satire and entertainment purposes.

Amazing series of charcoal/graphite drawings and oil paintings by Hong Chun Zhang. "Twin Spirits are large charcoal hair drawings, self-portraits of my twin sister and me. I use long hair to exaggerate our major characteristic and as a metaphor to reveal something that is beyond the hair. These drawings are presented as scroll paintings in order to accentuate the length of the piece and the flow of long hair..."

An emotional vampire is somebody who sucks the positive energy out of your life, in turn leaving you feeling drained afterwards. They can come in the form of a family member, friend, coworker, or neighbor. Unlike real vampires who are out of sight during the daytime, emotional vampires can come into your life at any hour of the day to ruin your mood and undermine the parts of your life that make you you.

Do you have a lot of stagnant energy in your life right now? Maybe all you need to do is check to make sure the drains are working properly in your kitchen and bathroom. Or place a small fish tank somewhere in your home to attract more wealth and prosperity.

Roof ventilation principles are very straightforward -- a cool attic is a happy attic! You need to create a flow of air that enters the overhang of your roof through soffit vents, then flows straight up through the rafters and out through a ridge vent. To help facilitate airflow, it may be necessary to install a thermostat-controlled exhaust fan.

In this video tutorial, Creative Cow leader Tony Ross revisits the tutorial how to build a basic site about Colors in Flash. This version is created using Actionscript 3. The basic principles learned from this tutorial will enable the user to create a variety of simple websites. Elements covered are basic Actionscript 3, navigation, labels, button and graphic symbols. Build a basic site using ActionScript 3 in Flash.

n this article, Mylenium is providing insights into the basic principles of working with the Cloner tool in MoGraph for CINEMA 4D. He'll take a hard look at the Cloner and its associated "Blend" mode as well as the other two multiplication tools, the Matrix and Instance objects. Use the Cloner in MoGraph for CINEMA 4D - Part 1 of 2.

This video is a series of short clips that show how to merge onto a freeway. These clips show how to assess the speed of the traffic already on the freeway (or highway) and join the flow of traffic safely. Made in the UK, if you're in a country that drives on the right, just think right instead of left and the principles will still apply. Merge onto a freeway or highway.

At the beginning of every class, or almost every class, we do a series of exercises. The Japanese word for this sort of calisthenic exercise isundo. These exercises derive from the Goju style of karate created by Miyagi Sensei in Okinawa in the early part of the 20th Century. In devising these exercises Miyagi no doubt borrowed liberally from the Chinese, whose influence on the southernmost island of the Japanese archipelago was immense.
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.