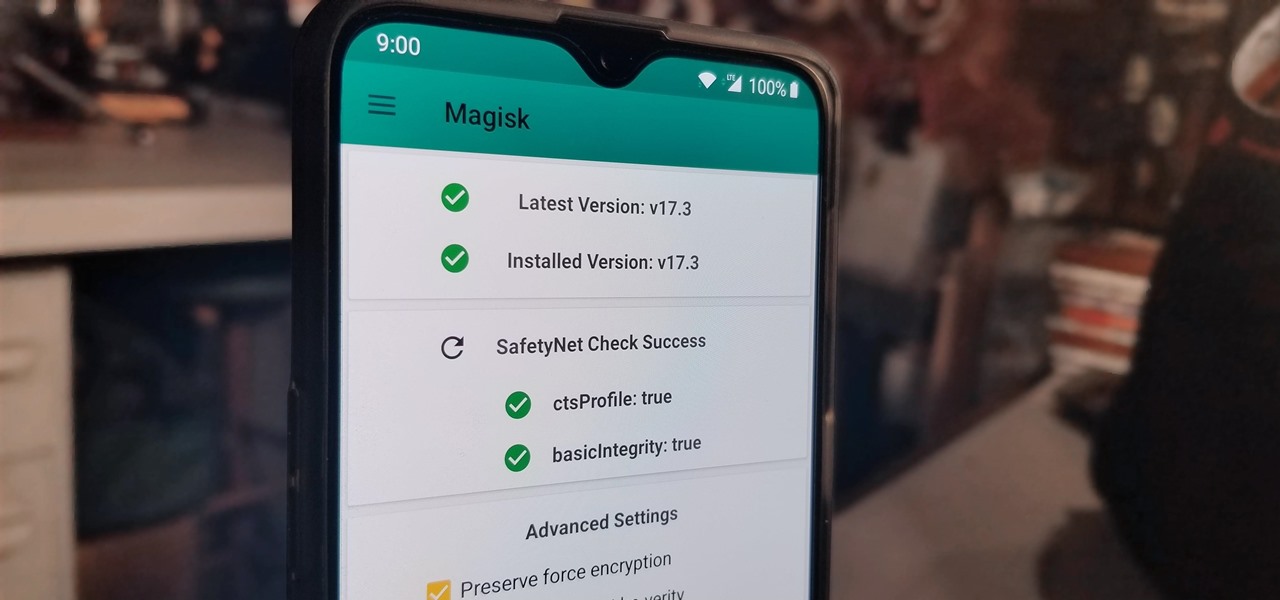
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

You've likely seen some impressive art carved out of a bush or tree before that looked like it required a lot of work and skill to create. While that may have been the case in the past, software engineer Javier Davalos used the Microsoft HoloLens to turn a bush into a perfect topiarian sphere with no training whatsoever.

Microsoft's enjoyed being the only mixed reality headset on the block for a little while, but the Meta 2 intends to join the party very soon. According to UploadVR, in a couple of weeks they'll begin shipping alpha versions of their headset with improved hand tracking.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

Whether you have AT&T, Verizon, Sprint, T-Mobile, or any other mobile carrier, chances are your smartphone is sold locked to only work on that specific carrier's network. Sure, you could unlock your carrier-subsidized device, but that would mean breaching the Library of Congress' latest Interpretation of the Digital Millennium Copyright Act—making the whole process illegal. As softModders, boundaries and regulations are things that we don't take lightly, although many times we have to begrudg...

The fill tool will allow you to alter the appearance of objects in your web design document and can be very useful for marketing purposes. The fill tool can be used to give objects one solid color for simple designs.

The video featured in this article demonstrates the function and design of a powerful form of air cannon that operates using a purpose made valve that opens very rapidly. This allows for a massive amount of pressurized air to be released at once to throw a projectile many hundreds of yards. The design of the cannon also allows the barrel and the air chamber to occupy the same space, and so it is very compact and manageable which makes for an enjoyable shooting experience.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Meet the Wonderbag. The "first non-electric slow cooker" uses an insulated bag made of poly-cotton fabric, polyester, and repurposed foam chips. You bring your one-pot meal to the desired cooking temperature, usually via the stovetop. Then you turn off the heat, pop the pot into the Wonderbag, and it will continue to cook thanks to the retained heat in the bag.

A new API in Android Lollipop allows apps to color the status bar to match their overall theme. Google billed this as a more immersive user experience that allows app developers to extend their color branding even further. It certainly seems like a win-win on the surface, but unfortunately, not many apps are using this feature yet.

Most people who cook end up having at least three or four different kinds of spatulas in their drawers. I personally have at least five. However, if I had to do it all over again, I would purchase only one, and that would be a flexible fish spatula.

Watch out Samsung (and you too, Pebble, Sony and the still unrealized Apple), your hold on the smartwatch market is about to get a lot less firm. Announced today, Google has released Android Wear, their platform for developing smartwatches, along with a preview of the Moto 360 smartwatch from Motorola.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

The first developer preview of Android Oreo 8.0 was only out for a couple of days before Chainfire created a new root method for it. For the time being, only the Nexus 5X and Nexus 6P are supported by this first SuperSU ZIP, as the Pixel's dual-partition layout has created some hurdles, though Chainfire is surely working on overcoming those at some point soon.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

When I finally saved up some cash and got my first good chef's knife, I vowed to do everything by the book: clean it properly, hone it regularly, sharpen it faithfully, stand by it in sickness and in health, blah blah blabbity blah.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

Did you know there's a way to make animating your own cartoons that's way easier than it looks — and that you can learn all the skills you need from home? Whether you want to pick up a fun, creative hobby over the holiday season or learn the skills to start working in animation, The Ultimate Cartoon Animator 4 Pro Mac Bundle will have you quickly making your own cartoons. Right now, it's on sale for 74% off, at just $49.99 (regular price $196).

Who doesn't love cartoons? Whether you want to take up a creative hobby over the holidays, learn animation for an exciting new side hustle in 2021, or buy the dream gift for the person in your life who loves all things animated, this deal is one to take advantage of today. Right now, you can pick up The Ultimate Cartoon Animator 4 Pro: Windows Bundle — with an amazing 74% discount — for just $49.99 (regular price $196).

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

When it comes to milk, my family consumes anywhere between two and four gallons every two weeks. That's about four to eight gallons every month. That's a lot of milk—and a lot of empty milk jugs! Instead of simply tossing them in the recycling bin, why not get creative and make something useful out of them yourself?

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.