
News: Sony Xperia XZ1 Boasts 3D Scanning Capabilities
At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.


At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

Late last year, two surgeons from the Instituto de Ortopedia e Traumatologia de Jaraguá do Sul in Brazil started using a combination of 3D printing and the Microsoft HoloLens to help plan spinal surgeries. And now, with the rest of their team, they've successfully performed a surgical procedure on their first international patient using their 3D impression planning and augmented reality process.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

I'm back! We're learning Java WhileLoops today.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hello friends. This is actually my first how to.

What's up guys! It's time to discuss strings in more detail. Review

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

3D printing is getting closer and closer to becoming an everyday reality—which means revolutionary things are going to start happening for the home cook. Already there's a 3D printer that can produce edible tailored fruit and the Foodini, which can print full meals, including spaghetti and burgers. However, neither are available for purchase, and most likely won't be within reach of the average cook for years.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

This video shows you a wild style lip: leopard print!
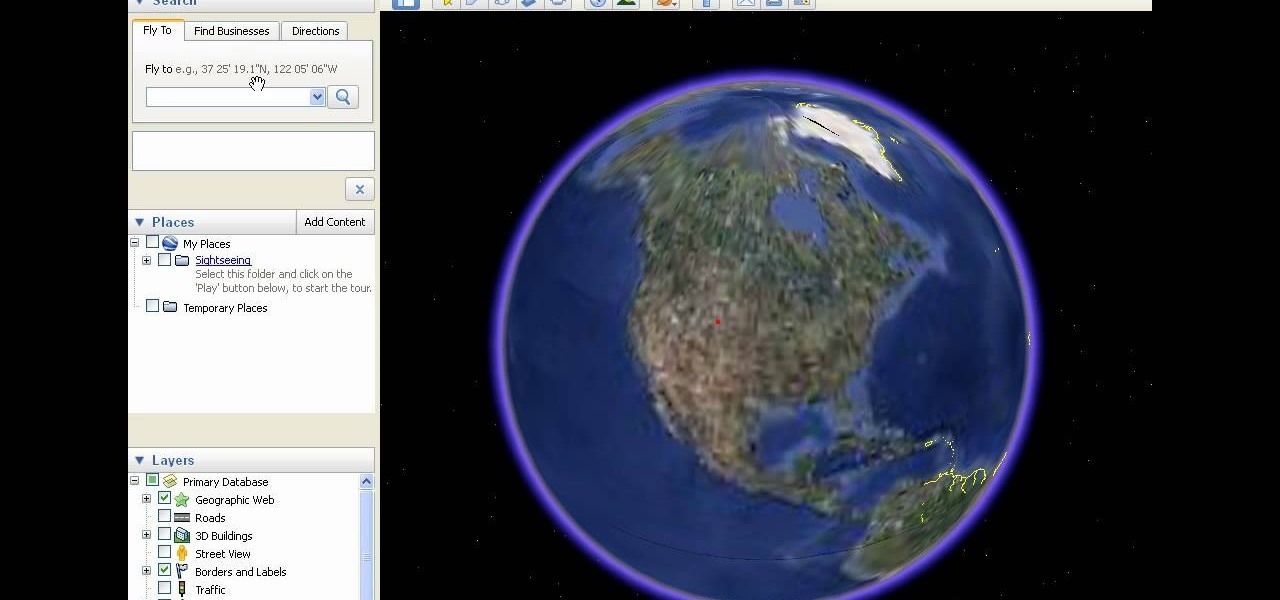
This video shows how to download and use Google Earth. To download it, go to earth.google.com and click “Download Google Earth”. Then follow the directions according to where you want to save it, and it will automatically be installed. You will see an icon pop up on your desktop. Double click on the icon to open Google Earth.

There are a lot of things out there in the design world that people have seen and liked, but didn't know how to make. LIke vector lights. Watch this Illustrator video tutorial to take a look at those cool glowing, color changing, fading, bright, neon-like, fanning spread of glowing colors. Maybe there's no specific name for them, but for now, refer to them as 3D Light Ribs. You can use these in photographs, illustrations, composites, print work, web design, and maybe even a logo or two! You w...

Make your own art masterpiece of a professional basketball player: Watch this tutorial to learn how to draw Lebron James. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Watch this tutorial to learn how to build up tones with cross hatching when drawing. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Paper plane designed by Joost Langeveld. This one is not very difficult to fold and flies like a rocket. Just a little glue needed.

All coloured patterns are drawn by hand for making these origami flowers. The flower looks like a daffodill but it's slightly different. Design: Joost Langeveld

Origami plane designed by Joost Langeveld. This bomberjet is pretty easy to fold. This is an origami tutorial brought to you by Joost Langeveld origami, a dutch origami artist. Joost offers some of the prettiest, most creative models. Joost has been doing origami for seven years and about a year and a half a go, started designing models.

Funny origami toucan designed by Joost Langeveld. This is an origami tutorial brought to you by Joost Langeveld origami, a dutch origami artist. Joost offers some of the prettiest, most creative models. Joost has been doing origami for seven years and about a year and a half a go, started designing models.

Origami amaryllis folded and designed by Joost Langeveld. The stem for this flower is made of two large papers. The flowers themselves are not very difficult to fold.

Folding this tiger lily is almost the same as folding a normal origami lily, but for this tiger lily a hexagon shaped paper is used.

This week, Etsy How-Tuesday presents Kari aka ikyoto and Stella aka lookcloselypress of The {NewNew} York Team. Today we're going to learn how to screenprint our own snowflake gift wrap for the holidays. Kari and Stella remind us that recycling paper bags is a great source for materials for this kind of project.

Watch this video tutorial from the Polish Guy to see how to polish a chrome car rim using Flitz Polish and a buff ball. In this polishing tip we polish a Jeep wheel using Flitz Metal Polish and a Flitz BuffBall. The tutorial includes detailed work instructions and best practices.

Learn how to create this funky, hot pink and lime green leopard print eye makeup look with this tutorial. This look uses the following products: 88 eyeshadow palette from Coastalscents, NYC liquid liner and pencil, Too Faced First Base, Too Faced Jewelry Box, and Lancome L'extreme Mascara. With this how to video you can achieve this bright pink and neon green leopard print eye look. This is a great look for a costume party or Halloween.

In this quick tutorial learn how to paint your nails in a leopard print pattern. Make sure to prep your hands and nails before painting them. You will need two shades of pink nail polish, glitter nail polish and a Sharpie marker. Watch this how to video and you can create these fabulous pink leopard print nail designs in no time.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

When you're sharing a printer, dealing with cables and networking can be a hassle. Having a printer with built-in wireless or using a wireless conversion kit for standard printers, allows easy sharing of your printer with multiple computers.

Bored with the same old stationary? You can create you own! It's just a few easy steps! *Using the on-screen menu on the printer, scroll to the second page and select "Print ruled papers".

It's easy to screenprint. Draw a design, tape it to a t-shirt, and use regular household bleach to stain the fabric. Watch this video printmaking tutorial and learn how to design a t-shirt using simple supplies from around the house.

How to set up and adjust a 4 color table top press for screen printing.

When you think of martial arts, only one name comes to mind, and no… we're not talking about Steven Seagal or Chuck Norris. We're talking about Bruce Lee, the epitome of martial arts. Not only was he the best martial artist known to man, he was also an accomplished actor, instructor, director, producer, screenwriter, and philosopher. But there was one thing he wasn't. An artist. Okay, he was a "martial artist", but he wasn't a visual artist, master of the pencil, kind of the drawing world… bu...

In order to make a hair bow out of old magazines, you will need the following materials: a bobby pin, colored duct tape, a ruler, scotch tape, scissors, and old magazines.
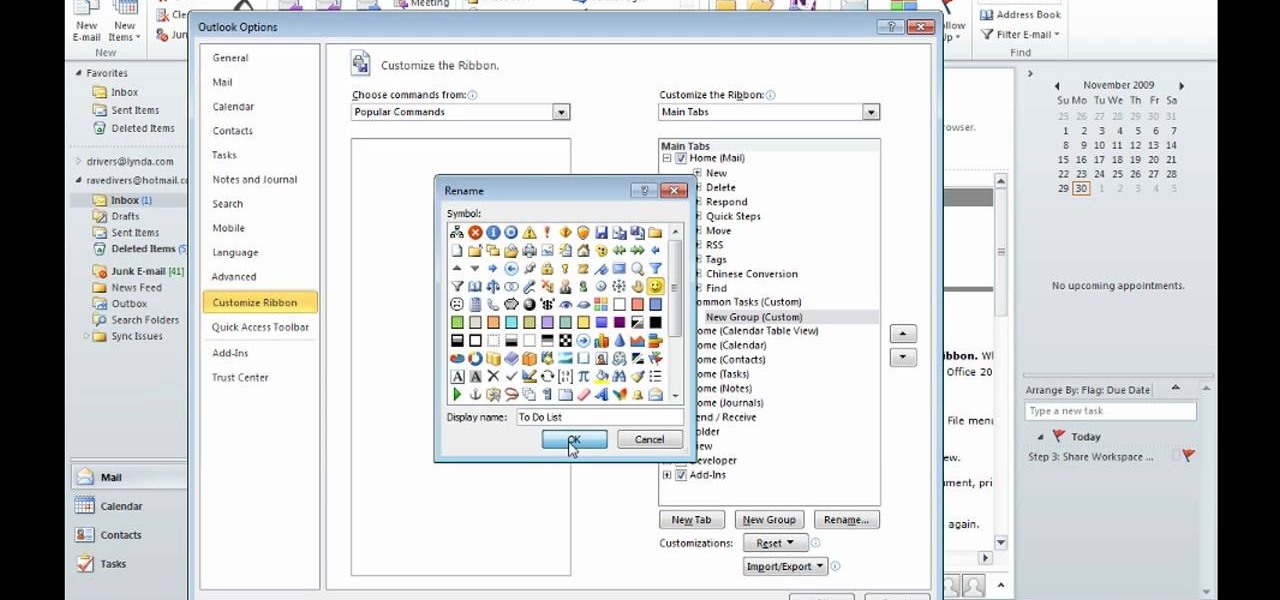
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...
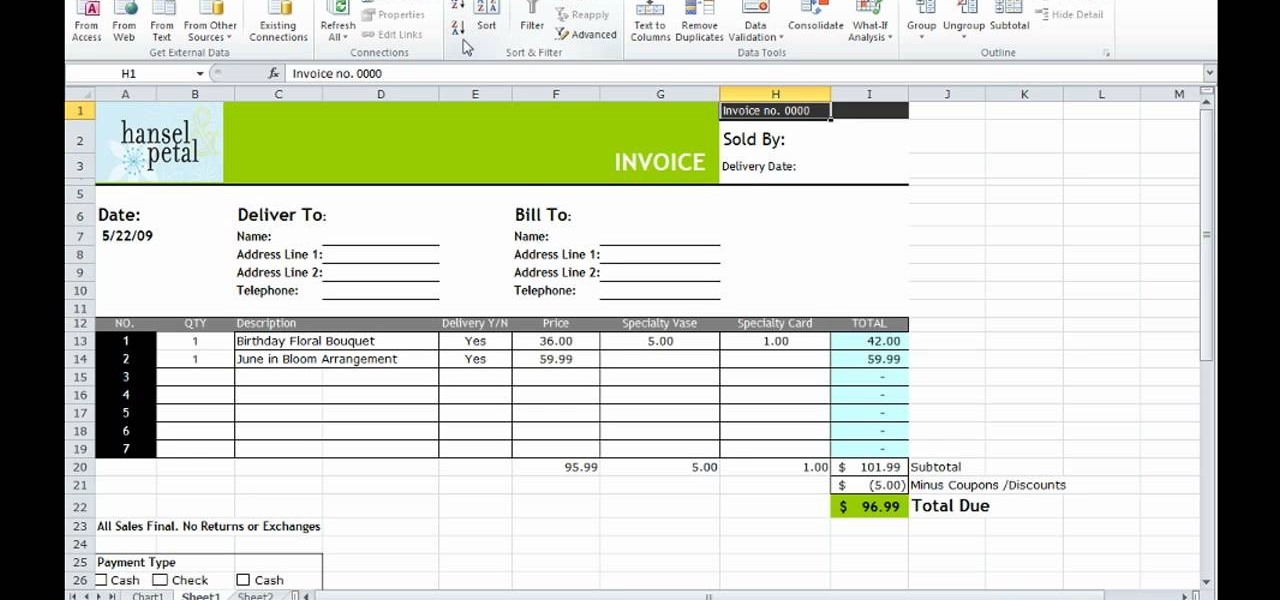
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.