The HoloLens opens up new, digital locales within our physical world, so it was only natural for the HoloLens Challenge to ask developers to create a portal into one. One developer rose to the task and gave life to wall art, turning it into an interactive game called Future Boy.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

When an album sells a million copies, it gets certified as platinum and cements itself as one of its generation's biggest hits. When an album sells 10 million copies, it reaches diamond status and transcends generational gaps. But when an album sells well over 40 million copies, there's only one thing you can call it—Michael Jackson's Thriller.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

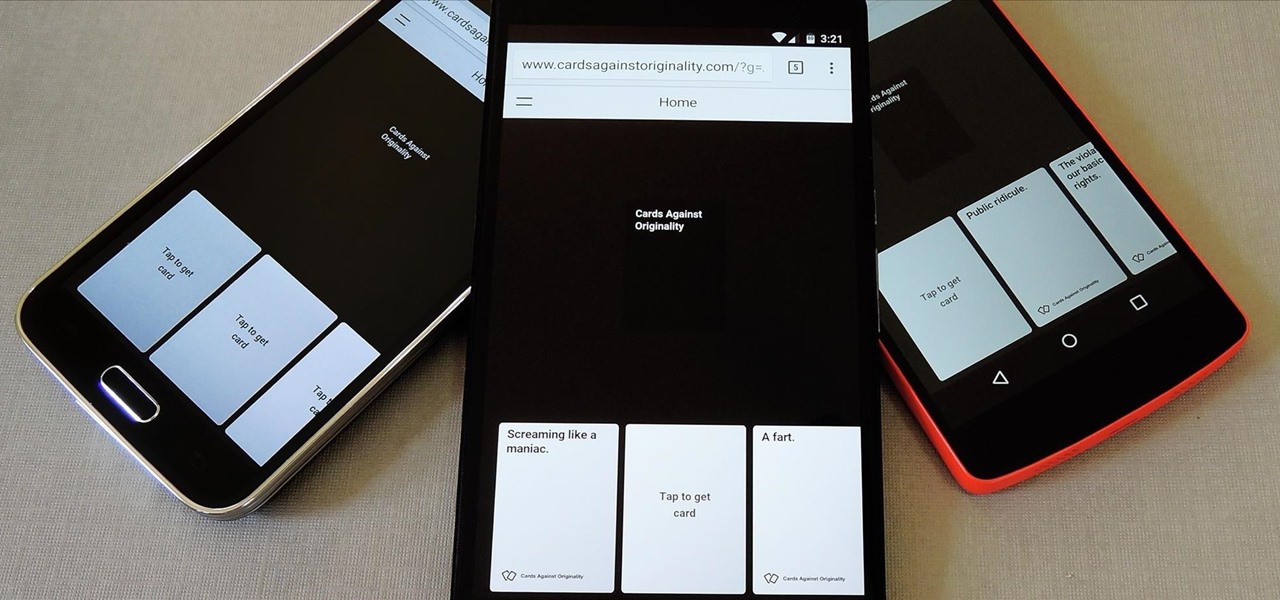
Cards Against Humanity is a popular party game with good old-fashioned raunchy adult themes that go quite well with a few alcoholic beverages. Up until now, though, you had to either print out a set of cards or order the official deck to play—unless, of course, all players happened to have devices that sported the same operating system.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

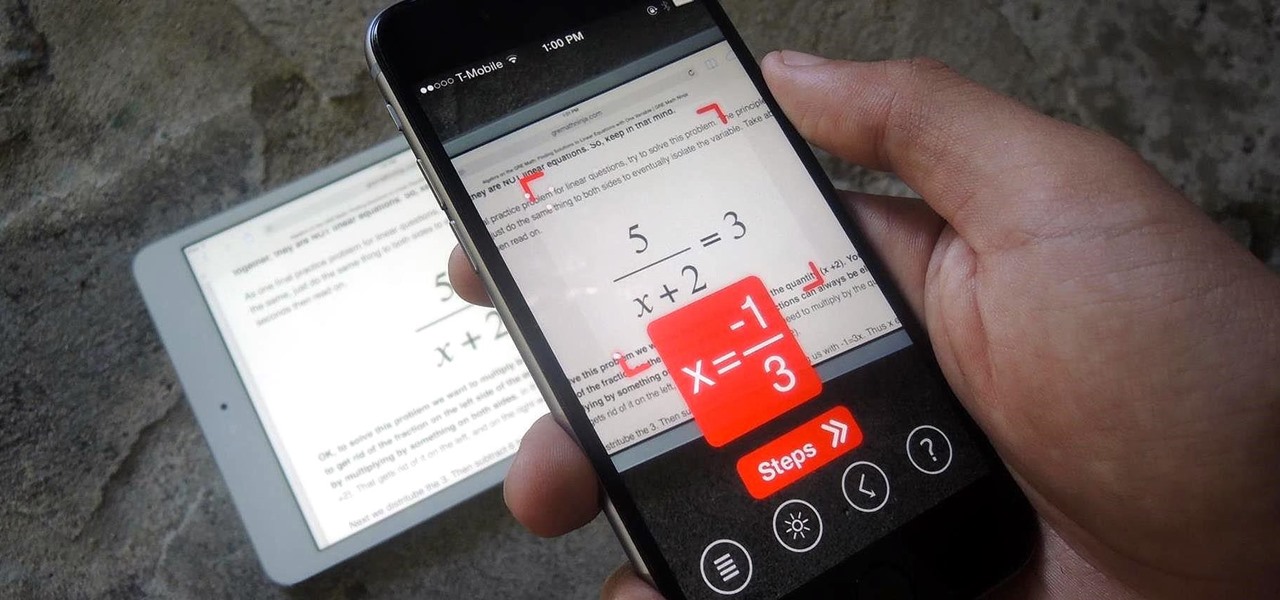
Math homework isn't the easiest thing to get through quickly, no matter how prepared you are. Knowing your stuff simply won't cut it. Going through dozens of equations in one sitting could take up hours of your time. Even when you finish, there's always going to be that one problem you couldn't solve, which could take hours itself to finally get right.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

Everyone loves cupcakes. And it is so much fun to grab a cupcake bite when watching your favorite FIFA match. After all what is a match without some munchies? So this FIFA, cheer away with your team's cupcakes. They're great to win over a bet or just celebrate your team's win.

You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day.

The recently released HTC One M8 and the upcoming Samsung Galaxy S5 are both boasting selective focus features for their camera apps, but with a 13 megapixel camera, the GS4 can take some pretty stellar pictures, too.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

A well-executed jack-o'-lantern can be pretty damn impressive, but some of us lack the carving skills necessary to pull it off and end up disappointed. Sometimes you just don't want to put in all the time required to cut open a pumpkin, gut it, and chisel an elaborate face or cool design into it.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

It wasn't that long ago that we started seeing a variety of beers catering to the Steampunk crowd, so why not some wine?

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

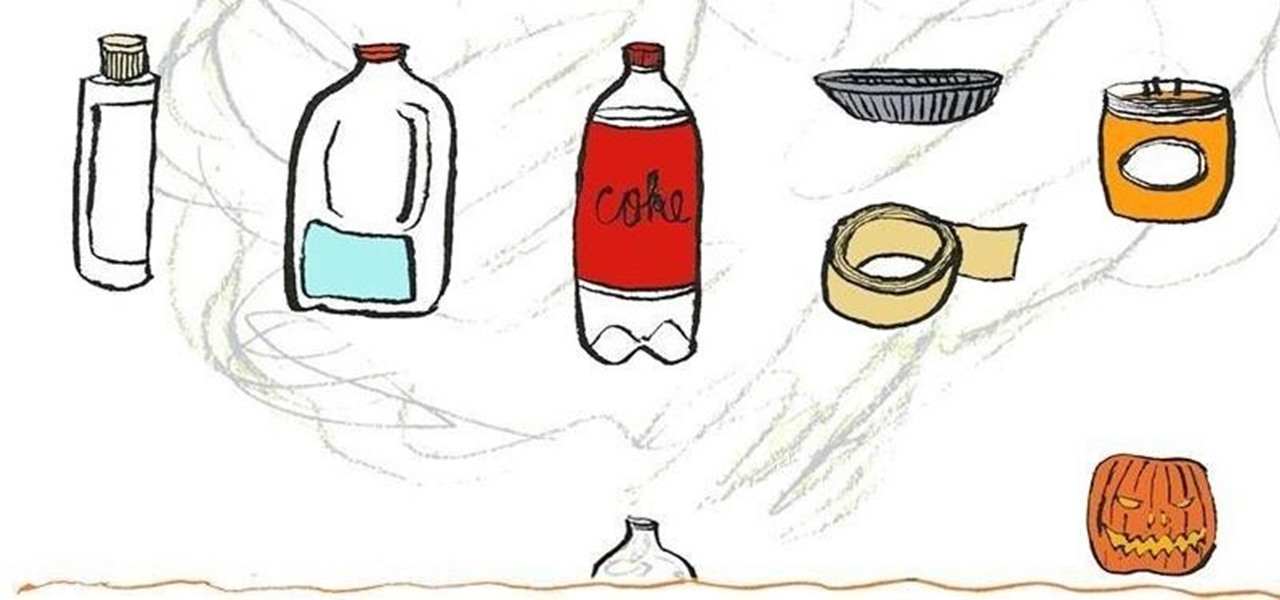
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

When you're a kid, the best part about Halloween is the free candy, but if you're past your trick-or-treating years, there are still plenty of things you can do. With all the costumes, scary stories, and pranks, what's not to love? And now, you can even use your smartphone to celebrate.

You may remember string art from your elementary school days. If so, it probably makes you think of the 2D geometrical designs that took every ounce of patience you had as a kid. Or those laborious curve stitch drawings, which string art was actually birthed from. But thanks to some innovative modern artists, string art has gotten a lot more interesting. Here are some of the most creative applications so far.

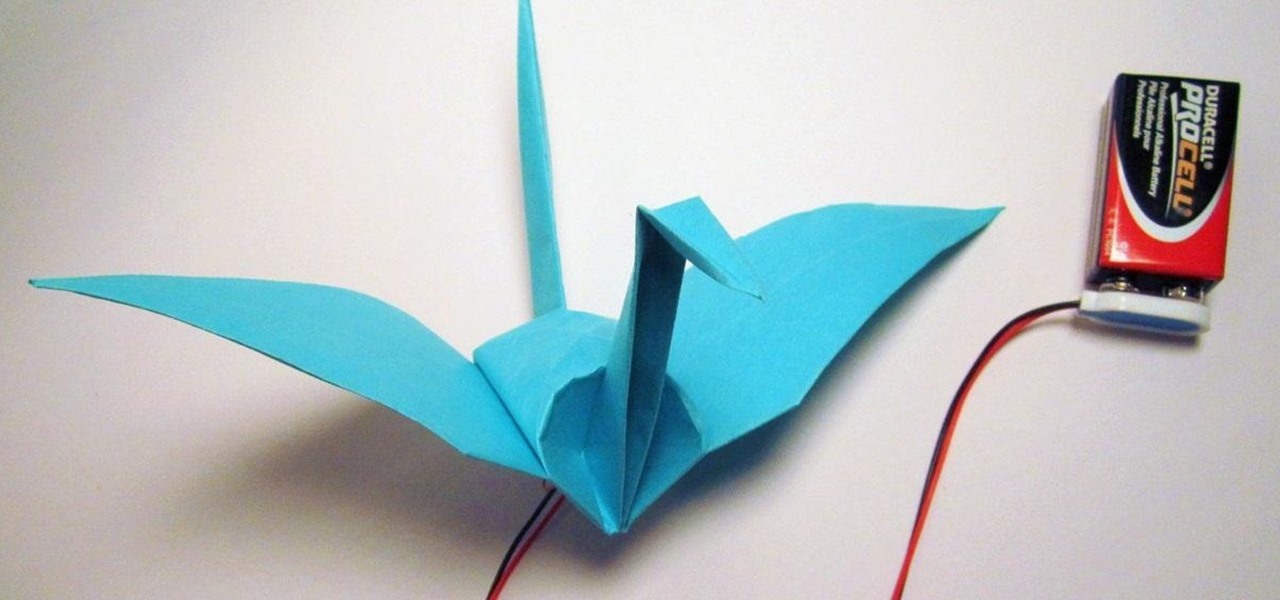
Want to spice up your origami cranes? MIT's High-Low Tech Group made two electronic origami cranes that flap their wings when you squeeze their tails.

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

In this video, we learn how to take a screen shot without using special tools. First, pull up the page you want to take a screen shot of. Once you have that page up, press the "Alt" and "Prnt Scrn" buttons on your computer keyboard. After you have done this, open up the "Paint" program on your computer and find the toolbar at the top. Find the button that says "edit" then hit "paste". After you do this, your page will show up in paint. You can crop it and edit it to the size you need, or leav...

This video takes you through the steps of making Coconut Milk Ice Cream. There is no narration in the video, just some bouncy music and the steps printed in text on the screen while you watch hands measuring and mixing the ingredients. Starting with coconut milk powder, you mix in milk, cook while stirring over low heat then add sugar. After those ingredients melt, you turn off the heat and add gelatin then cool. Then, you add fresh cream, mix and freeze. Simple ice cream that anyone can make!

Wouldn't it be great to create a list of all of the songs on your Music Folder and then be able to print it? Wouldn't you love to have a list of files and folders burned on a CD?