Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

After you've spent your Thanksgiving afternoon working through that turkey, mashed potatoes, and three different kinds of pie, you might find yourself heading to the mall to claim some unbeatable Black Friday discounts on iPhone 11, 11 Pro, and 11 Pro Max. You don't have to go in blind, though. Check out our guide below to make sure you're saving as much as possible on the iPhone you really want.

On iPhones, the share sheet is a powerful yet largely underestimated tool. For the uninitiated, the share sheet is the menu that opens whenever you tap the share button (the box with the up-arrow). This menu features sharing options to first and third-party apps, as well as extra functions like saving, copying, duplicating, and more. Best of all? It's surprisingly customizable.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

If you want your photos to look like they came straight out of a movie scene, the best method is to use split toning. Many Hollywood producers use this effect to recreate the cinematic look of cameras before the digital film era, which is why most people associate split toning with a cinematic feel.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Anyone remember Google Goggles? Well, it's back with a new name: Google Lens. But this time, there's more machine learning and it's integrated into many different Google apps and services. The latest is the Google app for iPhones.

It's no secret that MoviePass is a shell of the service it once was. The primary $9.95/month plan for three movies each month is inconsistent and can change drastically depending on your location. Thankfully, MoviePass isn't the only movie ticket subscription service available. We've compared all the best plans on the market to help you find the one that's right for you.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

While Sony as a company is well-known in the United States, it smartphones are not. For years, Sony has stuck with a boxy design with sharp edges and large bezels — however, they're finally getting with the trends. As a result, the Xperia XZ2 Premium offers a rare combo: A super powerful phone which is also pretty sexy.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

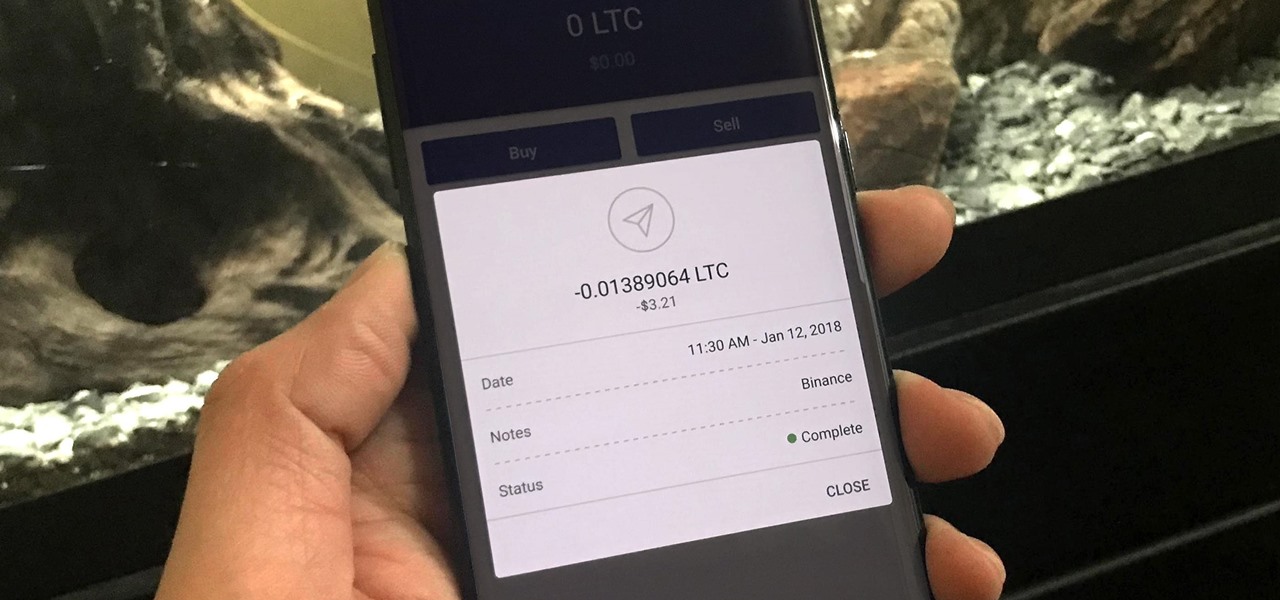
The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinbase, the most popular cryptocurrency app.

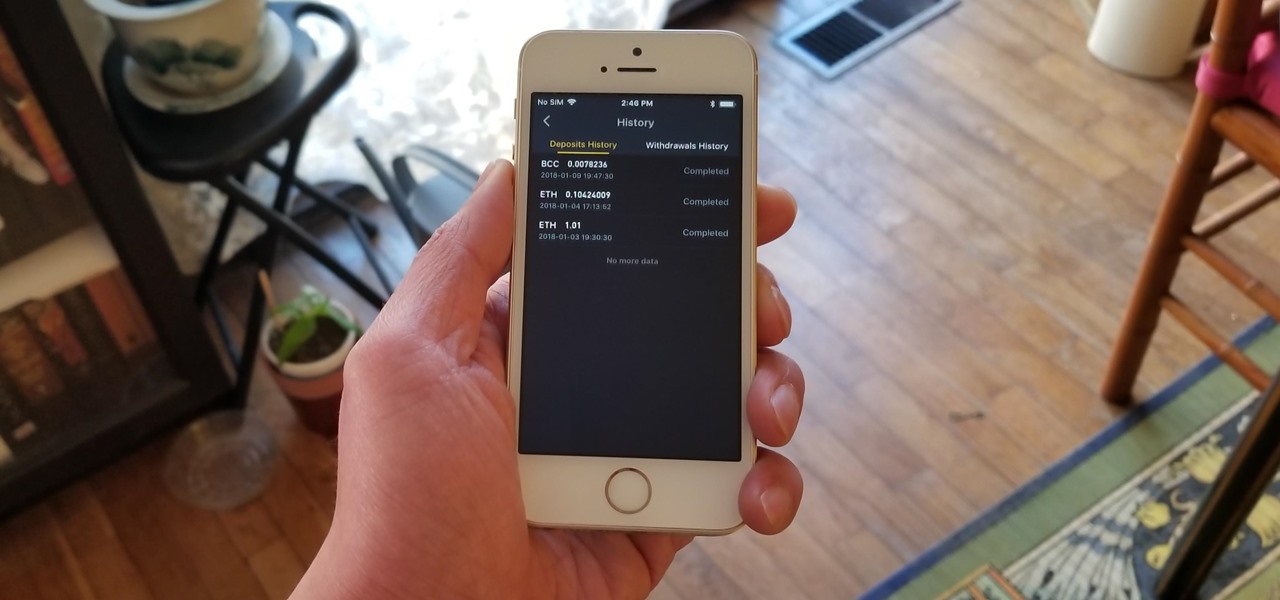
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

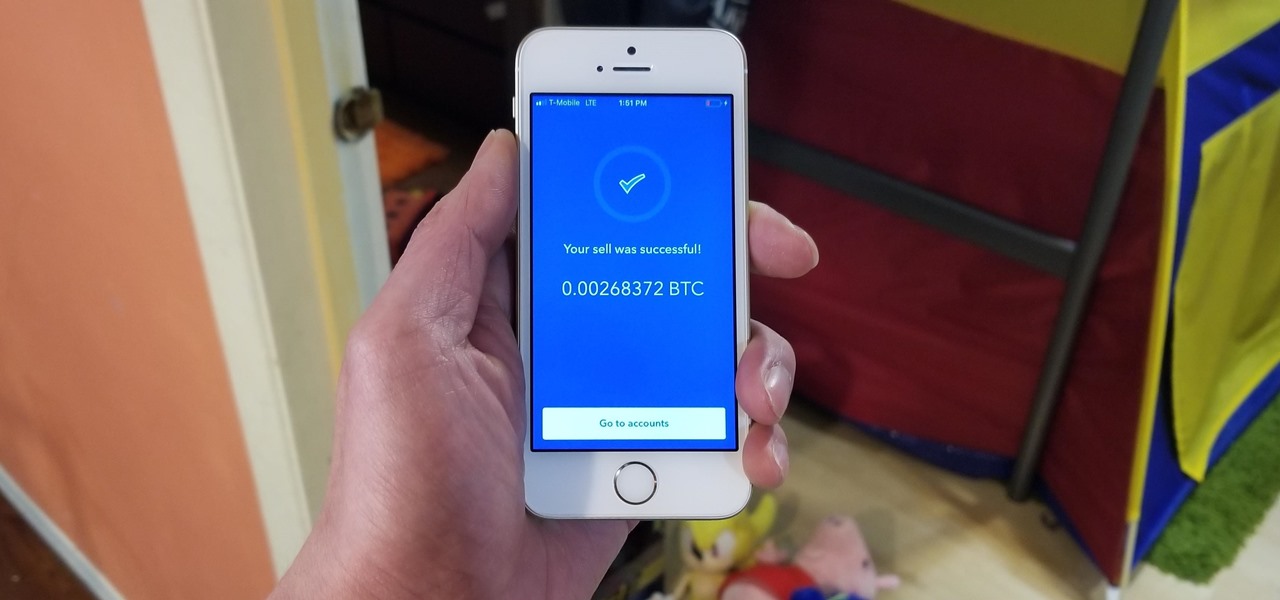
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

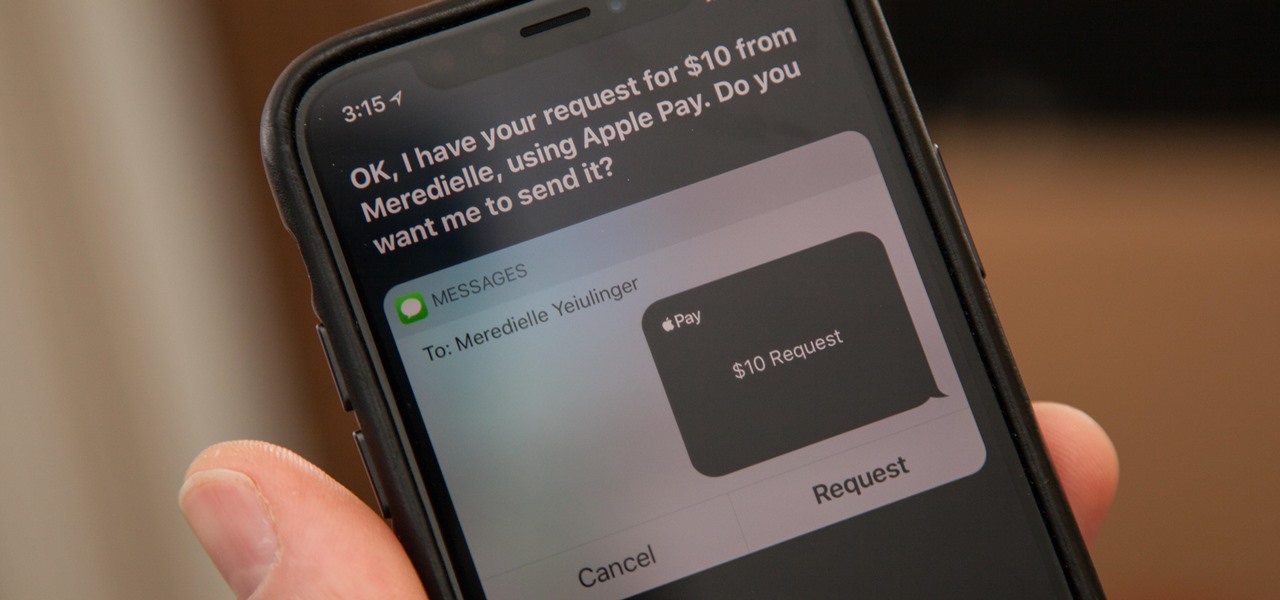
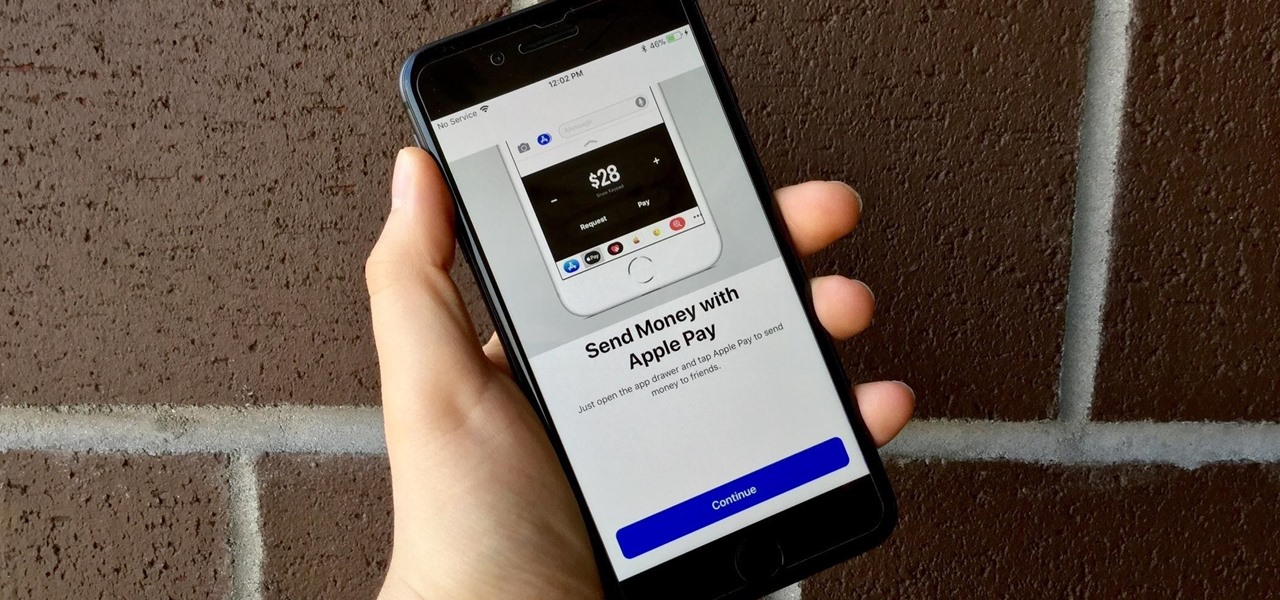
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway.

If you're someone who loves to read, you've probably read a book that made you want to hop into the story and live in the world that wasn't your own. Reading has a way of letting us escape into other worlds and experience things that we normally wouldn't be able to. Augmented reality is similar in that way. Which is why it makes sense that the two would be combined to create an incredible, immersive new way of reading.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

Breaking off a piece of that Kit Kat bar gets a lot more difficult when the whole thing weighs 13 pounds.

Apple just unveiled the new iPhone 7 and 7 Plus at their September event, which means we're inching closer to traffic jams, parking lot fights, and day-long lines at Apple Stores, as well as those inevitable, dreaded words: "sold out."

We keep at least half a dozen hard-boiled eggs in the fridge for times when we're on the go and need a quick snack. Often, we eat them sliced in half with a pinch of sea salt and black pepper, or we just make some deviled eggs or a quick egg salad—but these gets old very quick, and our creativity tells us to do otherwise.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?
Hey everyone. Only found the site a few days ago but really loving it. Been

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.