Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

With iOS 11, Apple's very own Notes app will now come standard with a number of new features that aim to make it significantly more user-friendly and help it compete against more popular notepads like OneNote and Evernote.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.
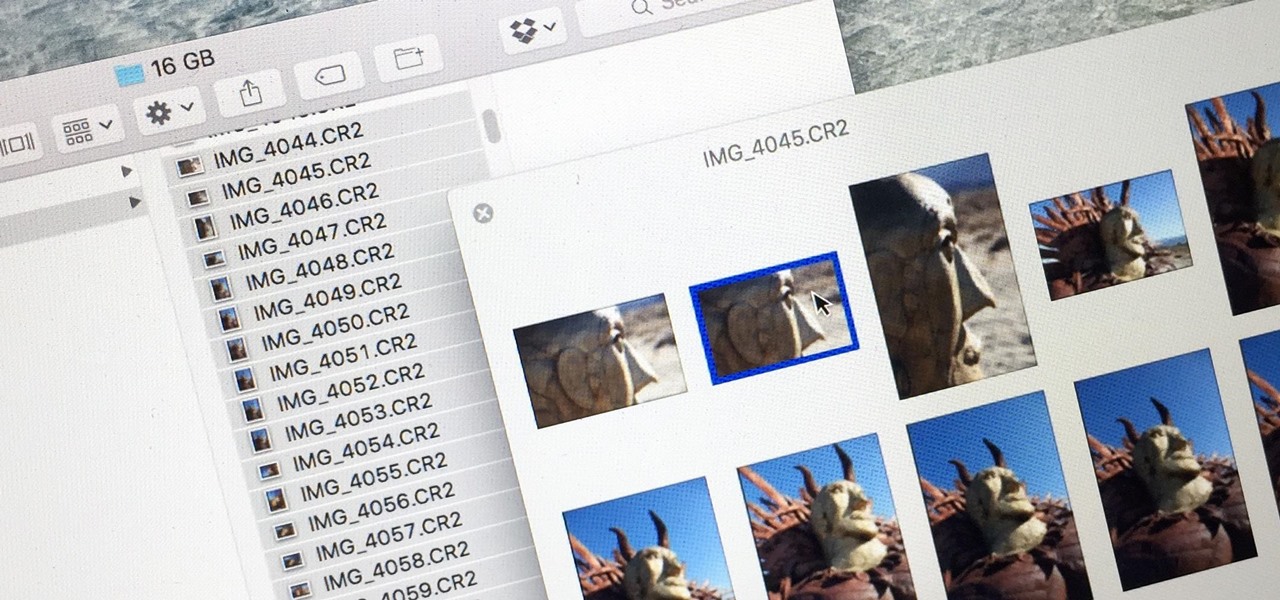
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

If you're all out of prank ideas for April Fool's Day, we've got a few that your Apple-loving friends will enjoy (or hate?). You can have a little bit of fun if you don't have access to their iOS device or Mac, but for the best pranks, you will need access to their devices, even if it's just for a few seconds.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

The internet was blowing up recently over this mind-blowing, mouth-watering video of a woman making a cake decoration out of… wait for it… chocolate bubble wrap. Yes, that's right: she turned the ubiquitous packing material into the mold for an absolutely gorgeous cake embellishment that, deservedly, went viral. You can watch the video below.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

If I could survive on one food for the rest of my life, it would be pizza. The irresistible smell of baking pizza instantly makes me feel both comforted... and hungry!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Contrary to popular belief, sushi is not the raw fish that one gets at Japanese restaurants, but the rice that comes with it. It's hard to tell whether this popular misconception led to or came about because of the primary flavors that we think of in sushi are the fish. We often say a sushi restaurant has great fish, but almost never that it has great rice.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

There's nothing in this life that we love more than making one ingredient or one food tool do multiple things. It saves money! It saves time! It makes us look smart at cocktail parties!

Welcome back, my greenhorn hackers!

Pizza. It's seen you through your best and worst times. It was there during your first relationship and the subsequent dumping. It got you through college, and maybe even your twenties. Domino's phone number is programmed in your speed dial, and though you won't admit it out loud, you love pizza, you really do.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut.

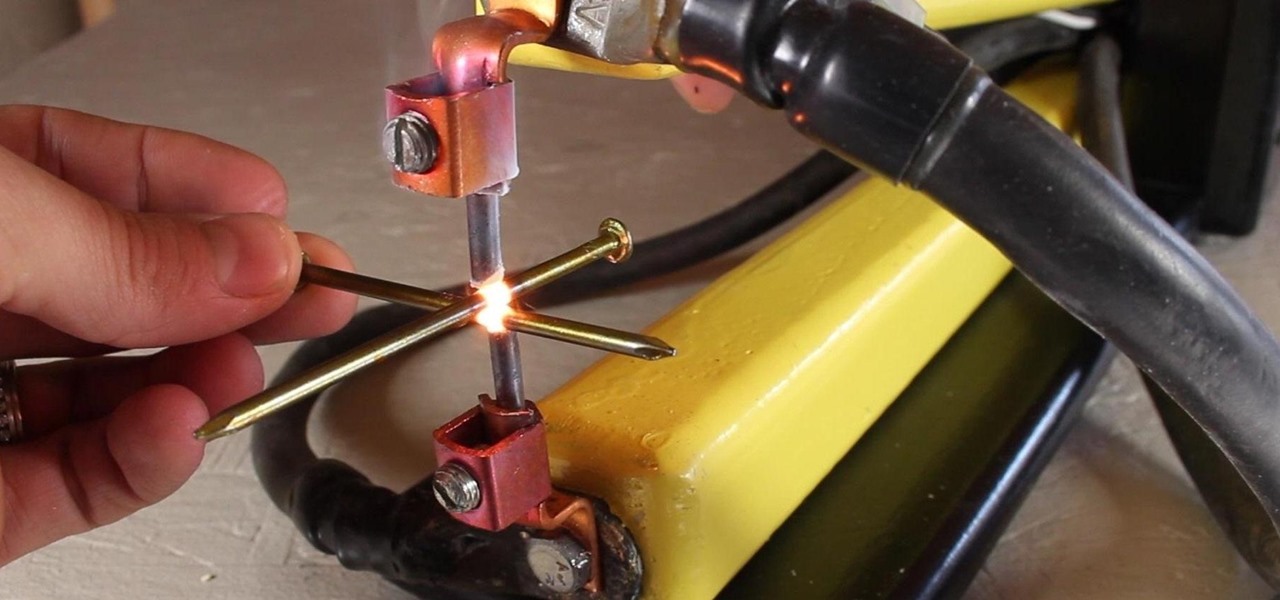
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

Other than sticking your crayon drawings onto your refrigerator door, magnets have a variety of unexpected and sometimes surprisingly practical uses, ranging from keeping your chip bags sealed to creating weird patterns on your nail beds using magnetic nail polish.

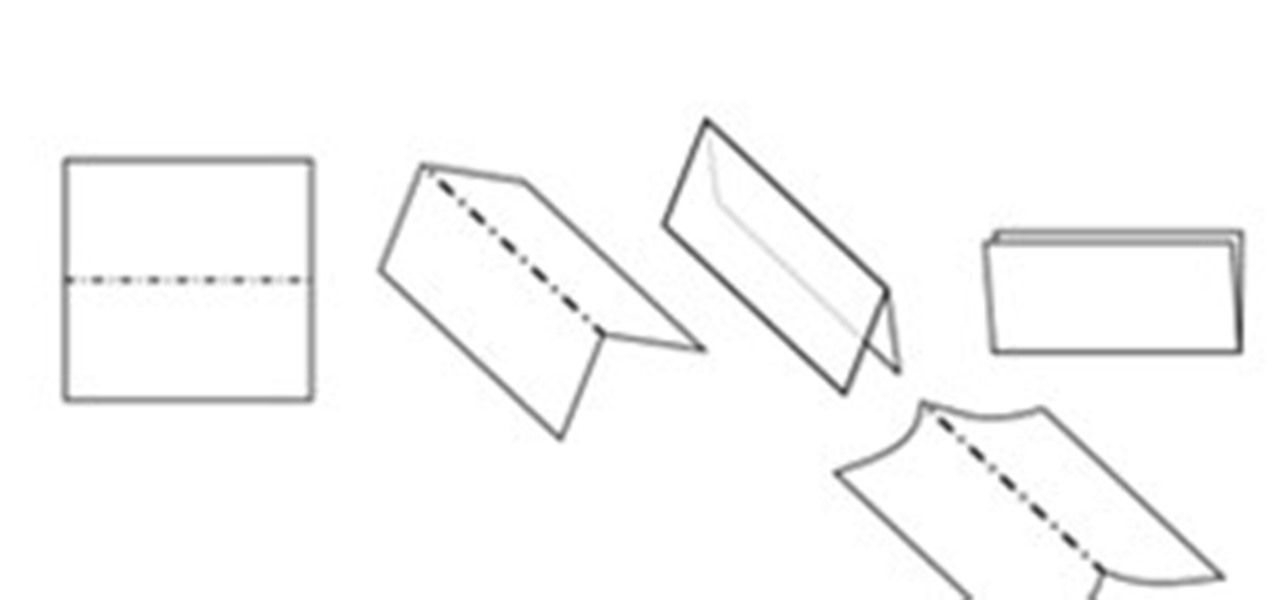
This is a great tutorial on how to make a paper hat and boat. To make a Paper Hat follow these steps: Take one large newspaper sheet that consists of two pages on each side. Fold in half lengthwise (the way it comes in the newspaper). Fold in half again (bringing the top of the paper to the bottom). Fold corners (on folded side) to middle. This will make a pointed top to paper. Fold one piece of bottom of paper up to the bottom of the pointed fold. Fold bottom again until it overlaps a little...

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

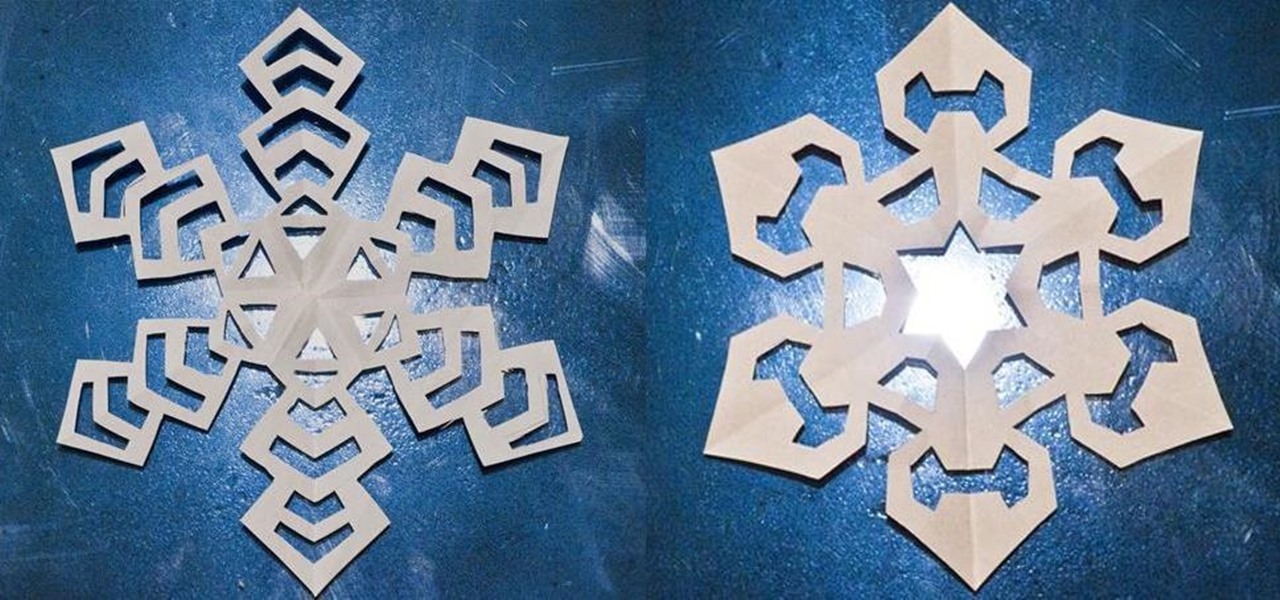
We've all made them. I remember making hundreds of paper snowflakes when I was in elementary school. You take a piece of paper and fold it in half, then fold it in half again. You now have a piece that is one fourth the size of the original. Now you fold it in half diagonally. You then cut slices out of the edges of the paper, and unfold to find that you have created a snowflake. The resulting snowflake has four lines of symmetry and looks something like this: If you fold it in half diagonall...

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.

In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

How to silkscreen a t-shirt at home; get professional tips and advice on screen printing custom designs on shirts and other clothing items in this free silkscreening video.

The screenshot tool on your iPhone can come in handy in various ways, but it may be even more helpful than you realize. So if you thought you knew everything there was to know about your iPhone's screenshot tool, it's time to put your knowledge to the test.

Without realizing it, you may be giving away the GPS coordinates of your home, workplace, school, and other important or secret locations. Unless you've blocked the feature on your iPhone, location data is stored in almost every photo and video you take, and anyone you share the content with can find out where you are or were. But there are a few things you can do to safeguard the information.

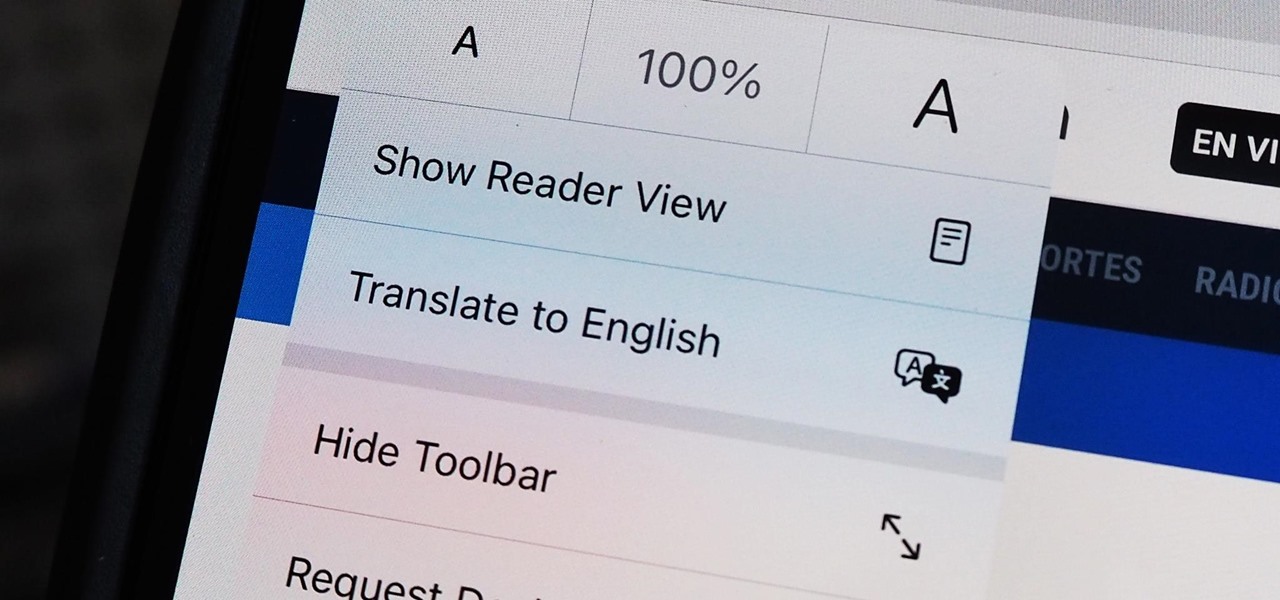
Since iOS 8, it's been possible to use third-party tools such as Bing Translator and Microsoft Translator to translate foreign language webpages in Safari into your primary language. Now, in iOS 14, there's a better way to do it.