
How To: Protect your privacy on social networks
Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.


Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

Getting locked out of a bedroom or bathroom can be a real bummer. Fortunately, these locks are easy to "pick" and get yourself in. This how to shows you clearly what to do to get yourself back inside so you don't feel frustrated all day long. This excellent video takes you step by step through the process. This video talks about 2 different types of locks and the two different types of tools you'll need.
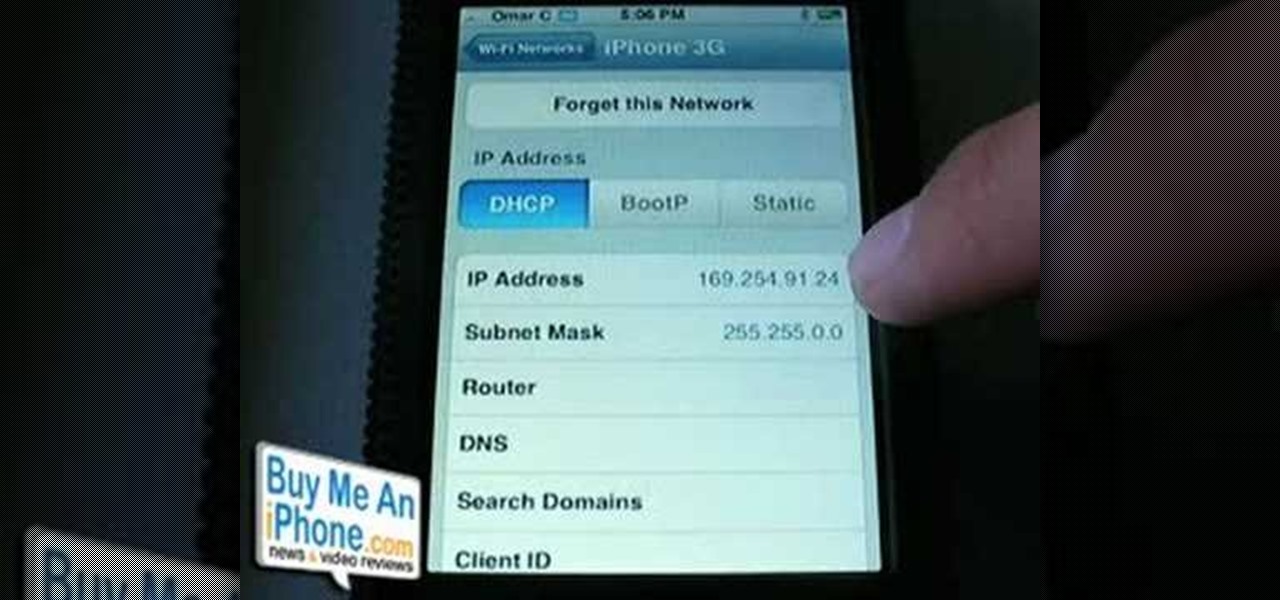
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.
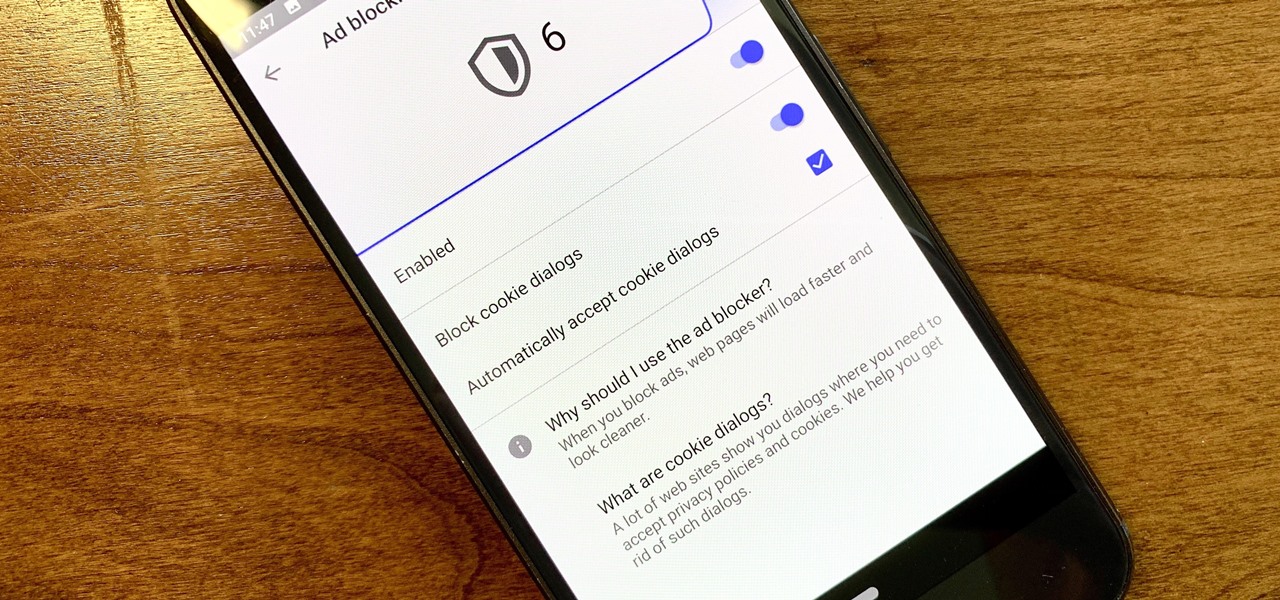
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

Take a folder and organize documents based on the actions required. Actions:
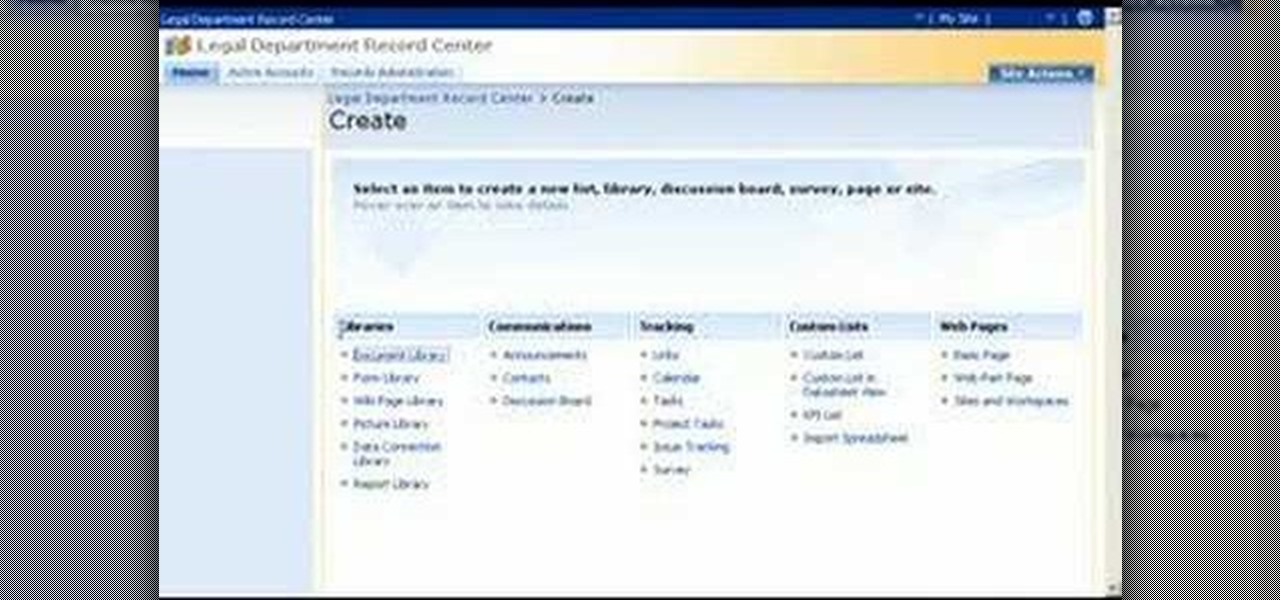
Check out this tutorial and see how to add a library to an existing Record Center site, apply policies to the library, and configure the Records Center site so that submitted documents are routed to the right library.
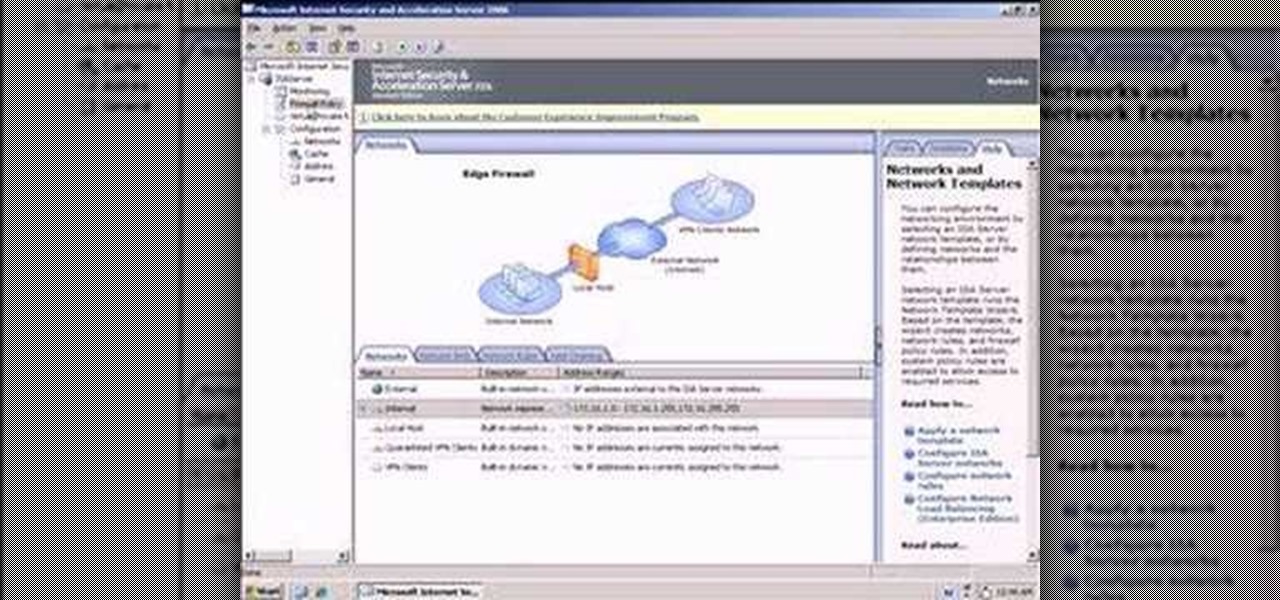
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Check out this video tutorial to see how to collect blood with the BD Vacutainer Safety-Lok Blood Collection Set.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

There will always be a time when you're not entirely sure what you're doing with a certain subject. But the days of weighing the pros and cons yourself are coming to an end. Whether it's a common quandary like "Where should we eat?", or a more specific question along the lines of "Should I buy this shirt or not?", you can now simply AskInternets.
For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through clear your Google search bar history (not to be confused with your Google Search History, which you may also want to disable). This tutorial will teach how to do just that. Take a look.
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial, you'll learn how to use the freeunblockme.com tutorial to surf the web anonymously.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:
In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...
This video makes you understand Flash Cookies and teaches "How to remove them" to keep your privacy.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.
Tired of clicking on interesting looking links in Facebook, only to discover that they are hidden behind a page you have to 'Like' before you can see? If you're surfing using Google Chrome, you can completely bypass this privacy setting. When you get to the page, go to the menu bar and click on 'Inspect Element.' Then you'll see the code for the page, and you'll be able to get around the block to see the page you want.
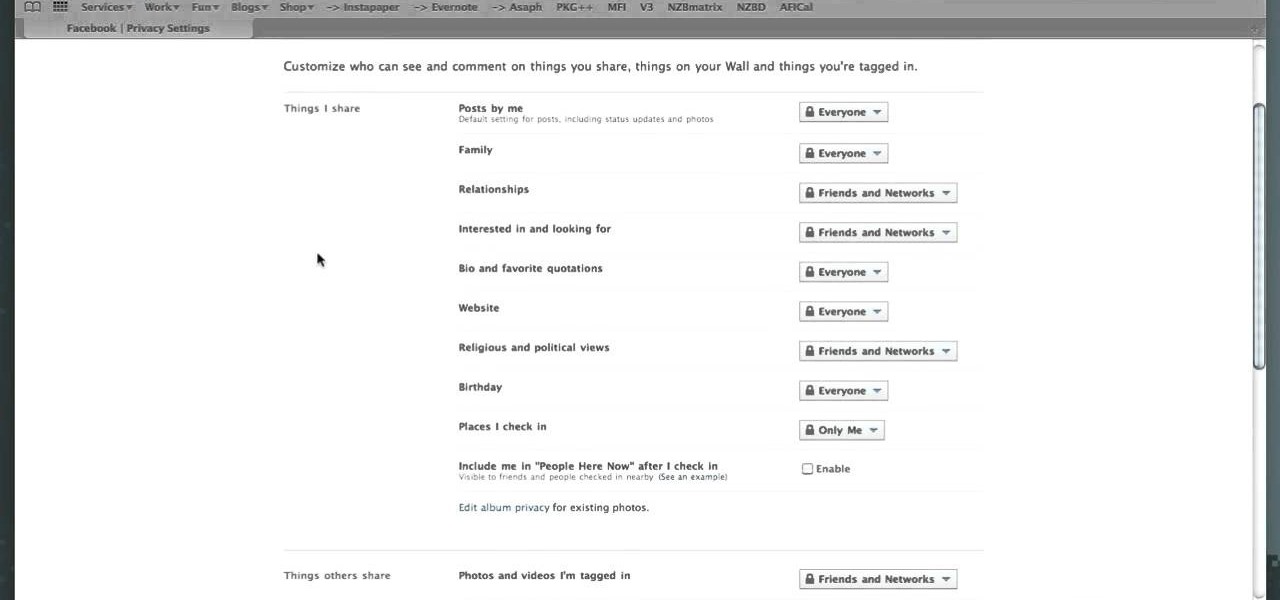
Facebook Places is a new location-based sharing tool that Facebook unveiled not too long ago. It works like Foursquare, in that you can check yourself into locations. Not only that, you can check other people in, and other people on your Friends list can also check you into other locations as well. So if you don't want to broadcast your every move to the universe, you'll have to go into Facebook and update your privacy settings. Again. Better to be safe than let your boss know by accident tha...
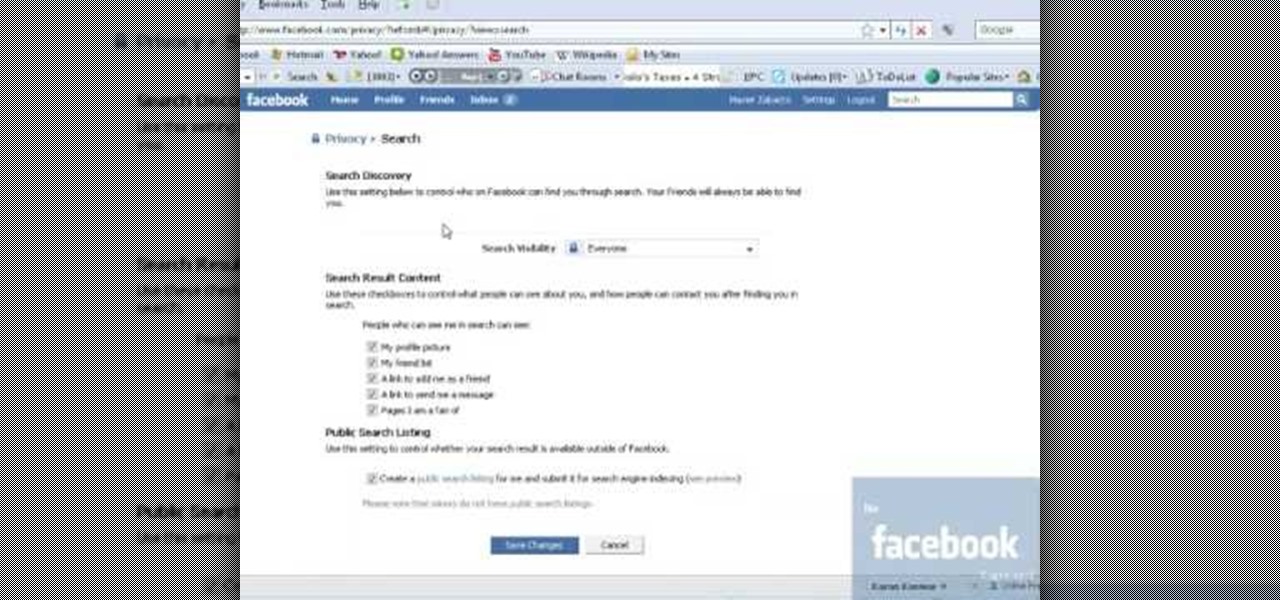
In this video, we learn how to make your Facebook profile less public. First, log onto your Facebook account, then go to your privacy settings. Through there, go to search and choose who you want to allow to search for you on your site. After this, save your settings and move on to the other sections to change more privacy settings. If you do not want people that aren't your friends to see your information or to be able to search for you on Google, this is a great way to go. Making your infor...
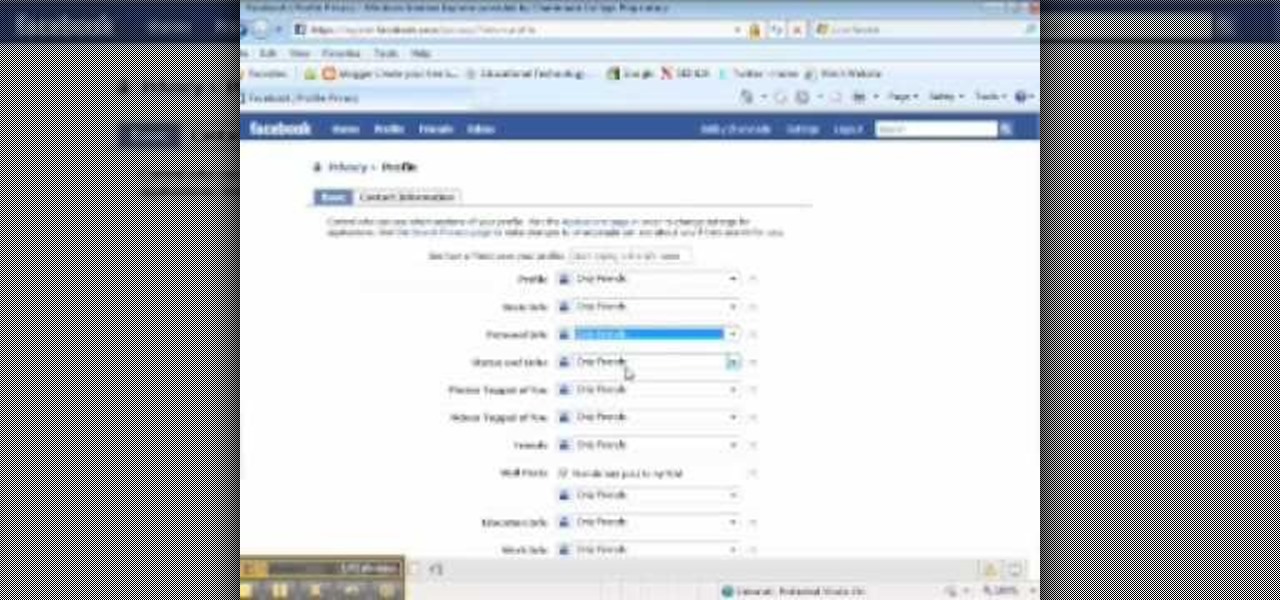
This video tutorial from ChaminadeENN shows how to set your Facebook account to private mode. First what you need to do is to sign in to your Facebook account.
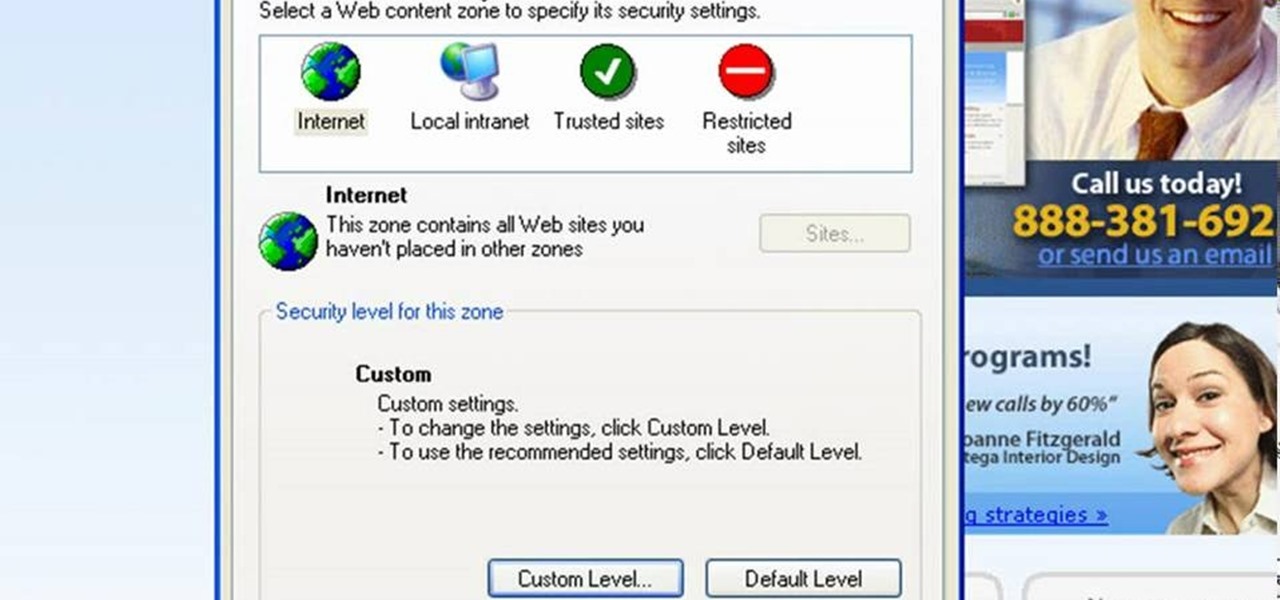
This video will show you how to enable JavaScript, accept cookies, and allow pop ups in Microsoft Explorer. The first thing you will need to do is to go to tools on the menu bar, then choose options, and choose the security tab of the new window that will pop up. To enable JavaScript click custom level, scroll all the way down until you see the scripting section, make sure that all three radio buttons are set to enabled, and finally click ok. To enable cookies, go to the privacy tab and make ...

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.
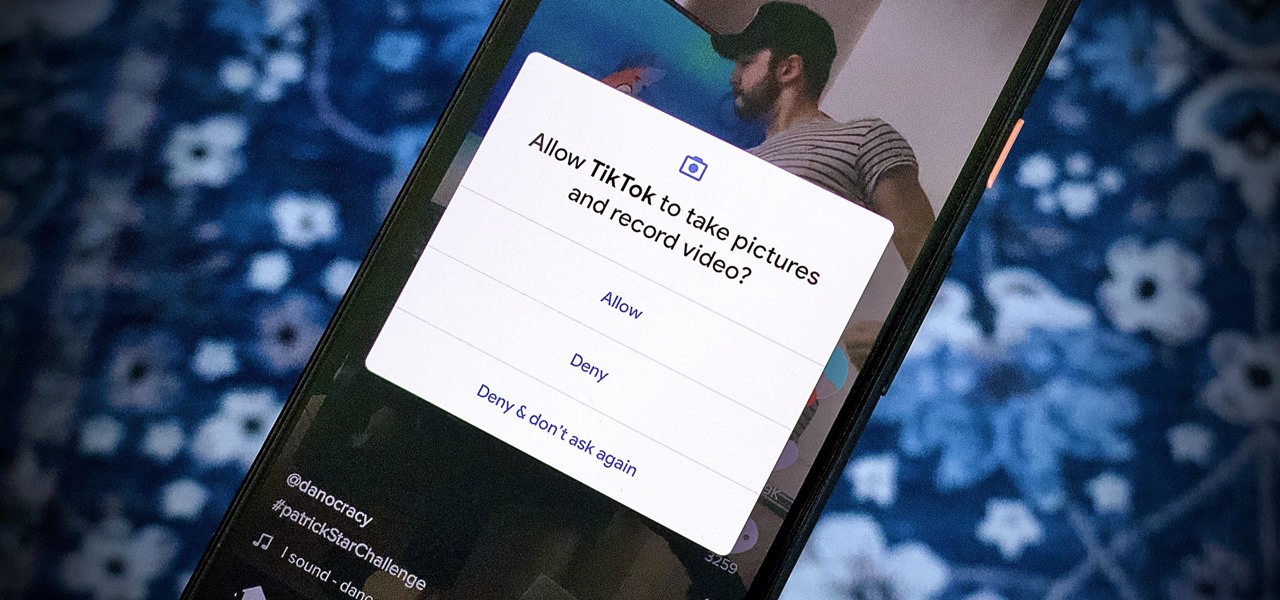
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.
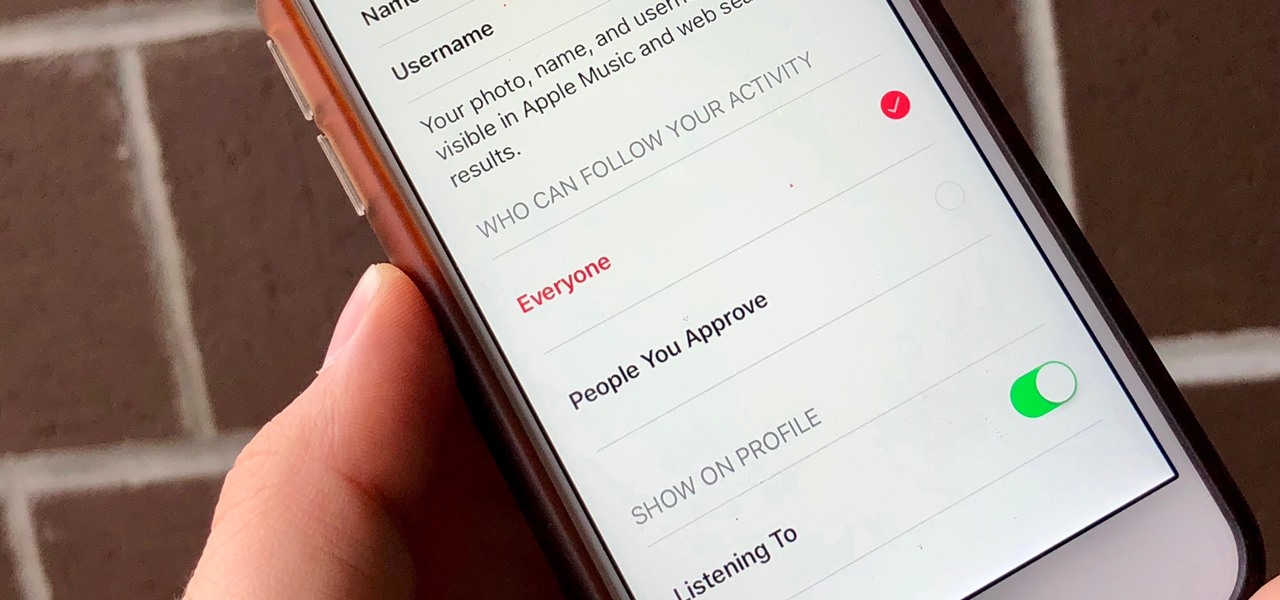
Apple Music, Apple's answer to Spotify, has many interesting features packed in to make that $9.99/month price tag as attractive as possible. One of those features is geared towards social listeners — those who want to follow other Apple Music users and who want to be followed back. But here's the thing: how do you know if your account is public or private?

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.