Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

For all of its drama, Uber's driverless program has states like Arizona excited for the future of self-driving vehicles. But it's not Arizona alone that supports the driverless craze; the Illinois House of Representatives will hear a bill that would allow driverless cars on the road with or without human operators.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

You never know when you're going to need a knife. Whether you carry it on your person for protection or simply use it to open stubborn packaging and envelopes, pocketknives are super practical yet also very dangerous if they accidentally open up in your pants.

This hair tutorial is called a wispy bird's nest after its, well, wispy quality and organized jumble of hair strands that forms into a cohesive whole.

Whatever your favorite flower may be, you can't deny that roses are the most romantic and alluring flowers around. In this tutorial, Reiberry bases a delicate hairstyle on the robust beauty of a rose. This pinned-up side bun is unlike any chignon you've ever seen, and though a bit difficult, the results will be well worth the effort.

Using a curling iron on your hair doesn't have to just mean curly hair. By alternating your curling method and holding the curling iron at different angles, you can actually create different types of curls as well as loose waves.

This hairstyle could easily be mistaken for simply missing a spot while you're pinning your hair into an updo during the morning rush, but the lovely rosebud hair accessory ties it all together.

This video explains how to build a shaded vegetable garden. The instructor begins the video my explaining the benefits using a shaded garden as it offers protection from hail, heavy rains and gives you the ability to control the outdoor temperature better. The simplest way to build your shaded building is to place large wood forms into the ground and place wood planks over the top of each and nailing them into place. The entire frame is then covered with a plexiglass roofing to keep out rain ...

“Great beach hair” doesn’t have to be an oxymoron, if you follow our advice in this how-to video. The elements aren't always kind to your hair, but an arsenal can keep your hair in top shape. To help tame your hair at the shore, try leave-in conditioner, anti-frizz spray, straightening cream, clarifying shampoo, baby shampoo, apple cider vinegar, a swim cap, and when all else fails, a hat (which is great protection from the sun-your skin will thank you too). Check out this video hair styling ...

To pick locks, one must either have an expensive lock-picking set or be skilled with whatever they have available to them. Bobby pins, soda cans, and even butter knives can get the job done, but each needs to be reworked into something more appropriate for the lock in question.

In this video tutorial, viewers learn how to set and encrypt their Wi-Fi password using WPA in Apple Airport. Begin by opening the Airport Admin Utility application from the CD. Then locate your the name of your network and double-click it or press the Configure button at the bottom right of the screen. Now enter your password and click OK. The network should be opened now. Then click on the Airport tab and click on Wireless Security. In the pull-down menu, select WPA2 Personal. Then click on...

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

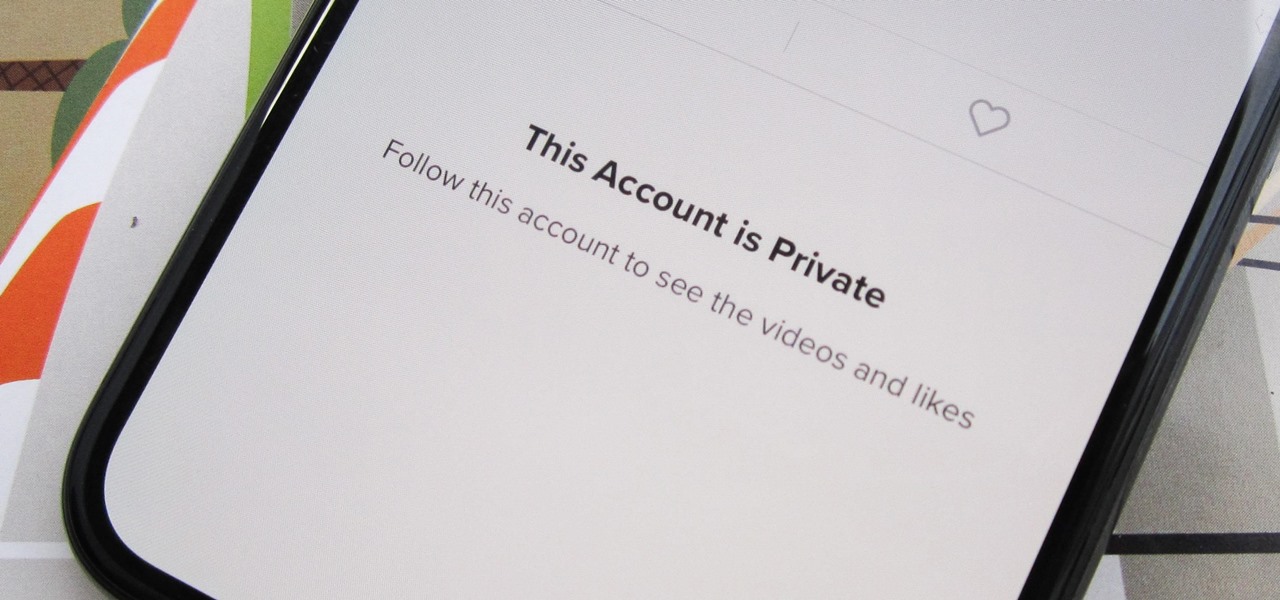
Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

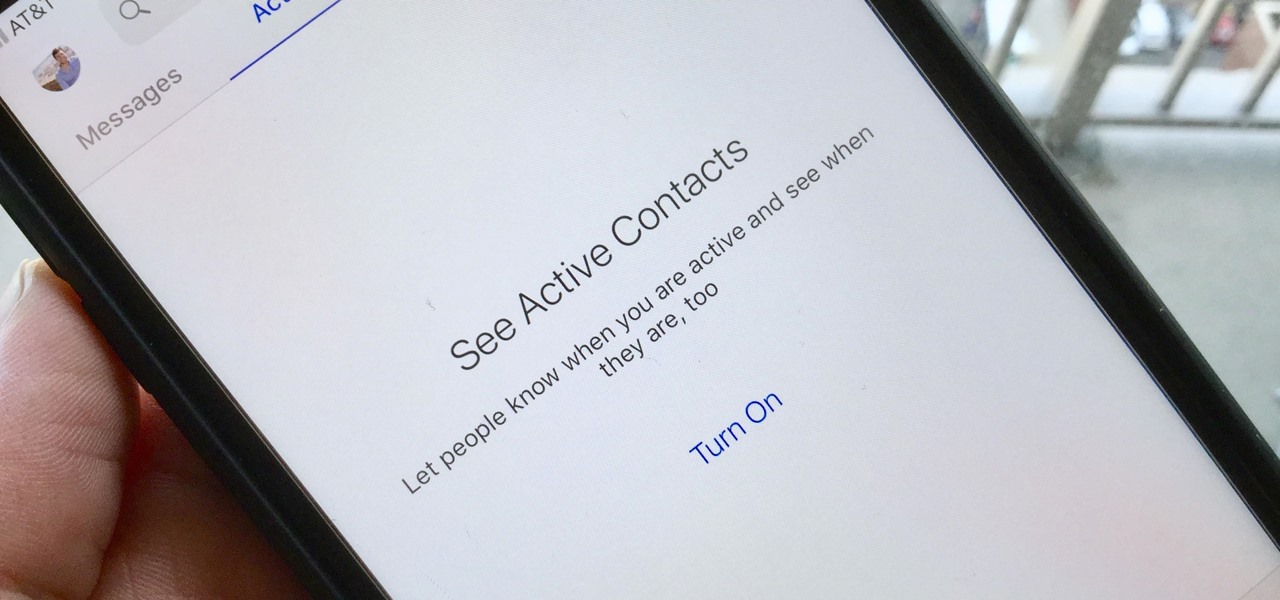
For all of its advantages, Facebook Messenger isn't the best for people who like their privacy. The popular app lets all your Facebook friends know when you're online by default, as well as how long you've been idle, making it impossible to check up with one person without leaving yourself vulnerable to your entire friends list. Luckily, this feature is one you can turn off.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

Welcome back, my rookie hackers!

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

Chris Duncan demonstrates how to jump tabletops and you first need to put on protection. You should keep your legs bent, elbows up and out, and arms straight. Jump a tabletop.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Ahhh! You're locked out of your bedroom, or your bathroom! Well, watch this video and you won't be locked out for long. Fortunately, interior privacy locks are very simple to pick. There are essentially two kinds: one that requires a blade, or knife and the other which requires a long sharp "pin" like object to insert into the handle. Check out this video and never be locked out again! You'll need something like a flat head screw driver for locks with a "slot" in them, and something long and ...

Free up space on your hard drive while protecting your privacy by deleting all of the temporary files on your MS Windows desktop computer or laptop. This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

We all have our reasons for erasing personal data from a phone. Whether you just ended a bad relationship whose face you never want to see again (lots of text messages) or just want to restore your privacy on the cell phone, erasing may be your only option.