The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.
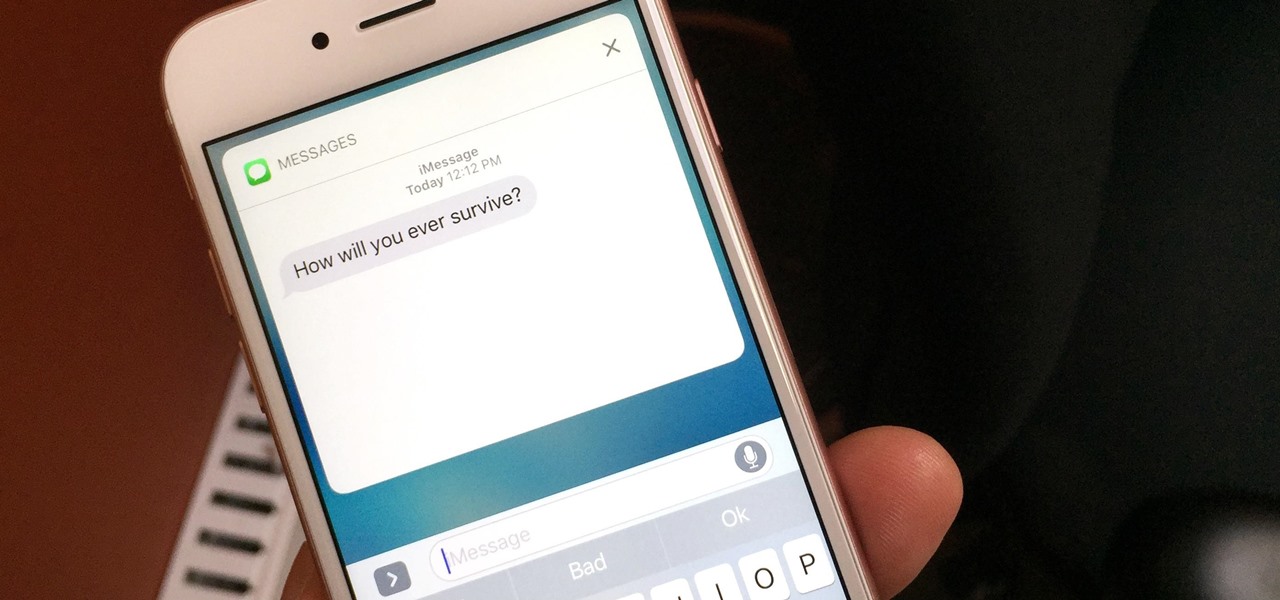
If you have an iPhone with 3D Touch or Haptic Touch, some lock screen notifications will let you respond to a message without even unlocking the screen. This is definitely a handy feature, and it should save a lot of time in some cases, but there are some obvious security concerns.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:
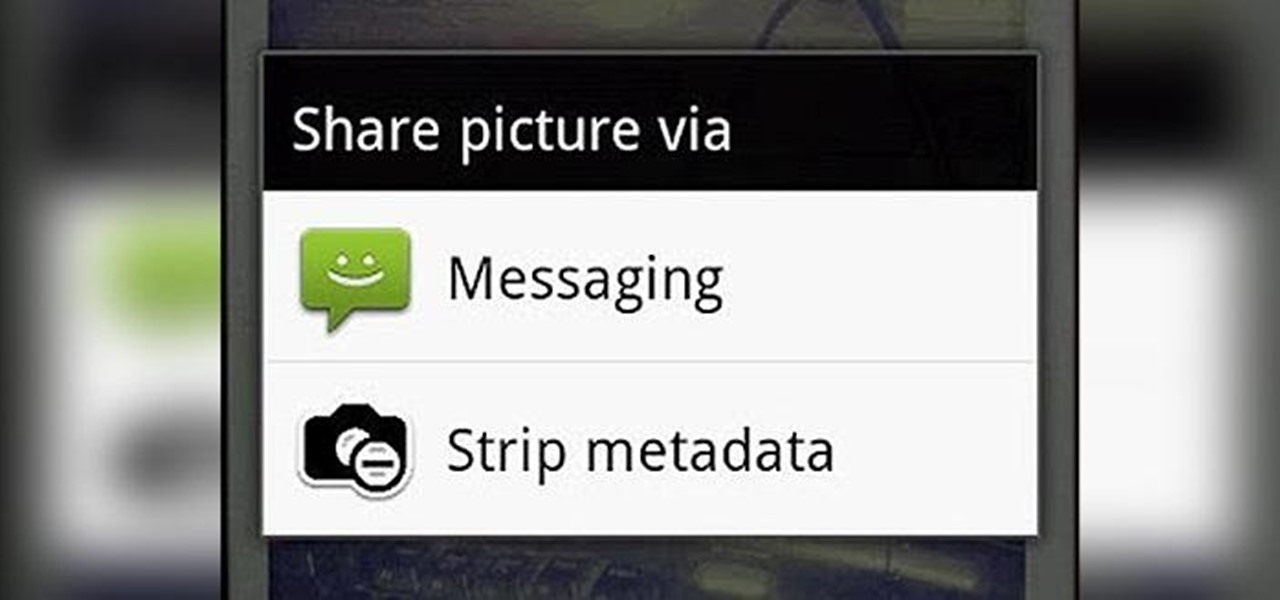
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

Any talk about privacy is a complicated (usually) and touchy subject. In today's world, privacy is an ever eroding pleasure to be had. Numerous cases, like the monumental Kat'z vs United States, have been fought to hold on to this right.

Need some privacy on your home computer? Find out how to password protect folders and make files invisible on a Windows XP pc. Password protect folders and make files invisible.

Ever hear of Spokeo? No, it's not a city in Washington state. It's a website called Spokeo.com, and it marks the complete end of privacy on the internet. If your phone number and address has been posted in a phone book, it's on there. If you own a house, chances are there's a picture of it. If you have a Facebook profile, it's probably listed.
Yesterday senior State Department official Alec Ross publicly announced that the Obama administration opposed CISPA, but refused to entertain the notion of the bill being vetoed.

For those who need security on their Android devices, the standard swipe lock screen just isn't enough, so it's necessary to install applications like GOTO and WidgetLocker to enable either pattern, password or PIN protection. This protection is great overall, but when you're frequently using your smartphone, having to keep unlocking the lock screen becomes quite an annoyance. You could be in a heated text conversation, following directions on a map or compulsively checking the news feed on F...

In the wealthy oil man's world of Arabian camel racing, the tradition of using child jockeys has been replaced with the use of small robo-jockeys in recent years. But after finally ridding the game of the mistreatment of children, the sport is now under scrutiny again. The Dubai police have discovered a new feature illegally added to the torturous, whip-endowed robots: hidden stun guns.

A handy chart I put together so you can see all the collections at one time and decide what to focus on for whatever you may need!

Just because it's Thanksgiving doesn't mean you're obligated by law to serve turkey at dinner. In fact, if you have a smaller family, or guests who just don't dig turkey that much, a smaller piece of meat, like ham, may be a much better choice.

With many states accepting laws about banning the use of cell phones while driving, bluetooth is becoming an important feature to have. Not only does it make things easier when talking on the phone, but it's something that is being featured in many new cars. So in this tutorial, you'll find out how to setup your bluetooth on a 2011 Sorento. So good luck and enjoy!

One of the great features in cars nowadays, is the ability ti connect it with your cell phone. With states accepting laws about driving and cell phone use, this feature can be a much needed addition to your vehicle. In this quick and easy tutorial, you'll find out how to setup your bluetooth phone with a 2010 Ford Fusion. Enjoy!

This video features an old Chinese woman demonstrating how to write some Chinese calligraphy phrases. These phrases can be used to adorn paintings of some traditional Chinese painting subjects, which often feature such calligraphy. We are left to wonder how the host feels about deferring the teaching to his mother-in-law.

Bill D., the tech lead at all3sports.com takes us through the steps involved in unpacking and assembling a brand new bicycle. The first he says is to set up or insert the seat post. He recommends using a work stand if you have one at home. He says not to unpack everything at the beginning, but to just expose the seat pack first. Use a wire-cutter to get rid of the film protection used for packing. He has mounted the frame-set on the work stand. The seat post goes into the frame-set. He asks t...

Over a half-million cyclists end up in emergency rooms each year. Lower that number by following some rules on how to stay safe while biking on the road. Learn how to ride a bike safely on the road. You will need a bike with working brakes, a helmet, a pair of bike gloves, sunglasses, and knowledge of traffic laws.

Tired of getting speeding tickets? Not prepared to start driving by the letter of the law? Well, this instructional video shows a way to con the speeding radar. Regular LED lights can be modified with infrared LED bulbs and will avoid speed detection by the police. Learn how to stop getting speeding tickets and avoid police radar detection by adding LED lights by watching this how-to con video.

Most coin vanishing tricks rely on sleights of hand and some skill; this easy magic trick just uses the physical laws of light refraction, and is much easier than that makes it sound. Learn how to perform this disappearing coin trick, great for a night out at a bar, by watching this video magic tutorial.

Kimberly Law demonstrates how organizing your clothes into so-called "wardrobe capsules" will enable you to get much more out of your clothes. Watch this how-to video to make a wardrobe capsule.

This video tutorial discusses high quality installation of attic insulation procedures. this video is a must-watch for all home insulation contractors in California to ensure that they receive an energy compliance credit.

This informative video tutorial discusses proper installation of home insulation to obtain California energy compliance credit and pass quality inspection. This video is a must-watch for all insulation contractors working in the state of California.

This video will teach you how to properly use the sleeper hold in order to subdue an attacker, but not damage their larynx. This is a real way to protect others and yourself. It is meant to help Police Officers from choking people and avoid law suits from performing the wrong maneuver.

How many women have heard "You can't do that here!" when trying to nurse in a public place? Parents TV's Anne Ebeling explores the issue of public breastfeeding from etiquette to laws that protect nursing mothers.

NLP Lie Detector Eye Accessing Cues Explained. This technique is used by the Federal Law Enforcement Training Center FLETC.

Today's word is "endeavor". This is a noun as well as a verb. As a noun, it means an effort or attempt to accomplish something. As a verb, it means to strive or attempt.

MORE FREE VIDEOS http://www.sozoexchange.com Today's word is "narcissistic". This is an adjective which means having too much love or admiration of oneself.

A close look at an alternative adaptive method for playing nonlinear theremins (theremins whose notes are not evenly spaced) such as the Moog Etherwave Standard theremin.

Obleck is a mixture that defies Newton's third law and kids will love it! Ingredients you will need are 1.5 cups of corn starch, 1 cup of water, and food coloring which is optional. After mixing, if the mixture is too thick, add more water. If the mixture is too runny, add more corn starch.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

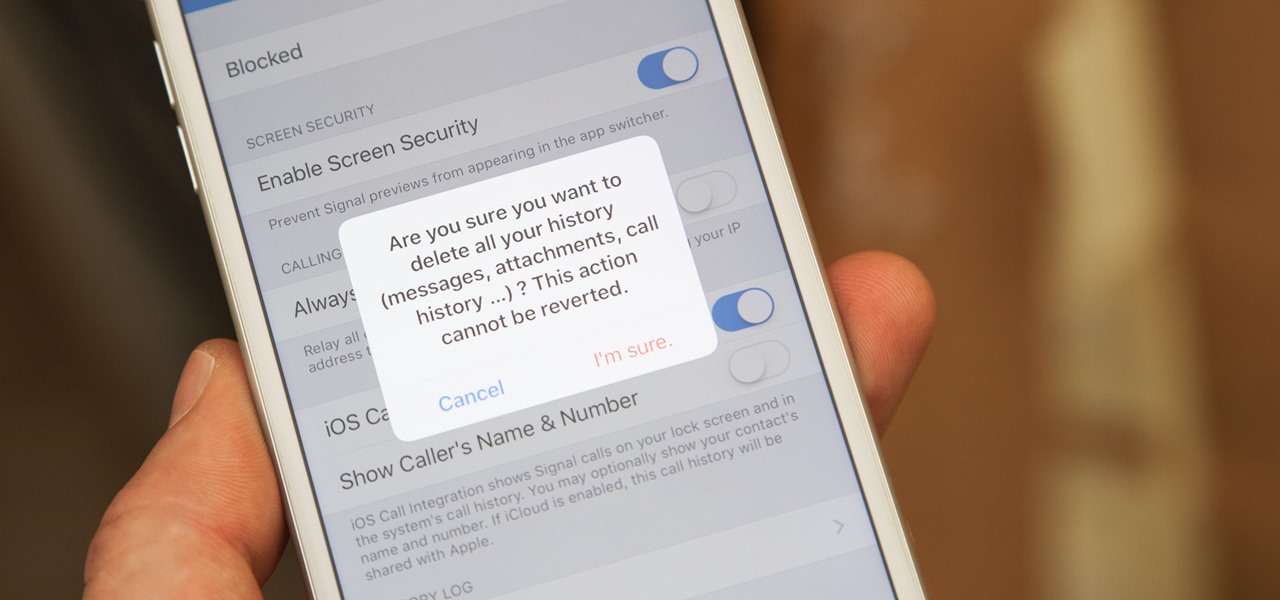
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Driverless transportation is definitely coming closer to the mainstream, but most companies developing the technology have said it will be another couple of years before we see autonomous vehicles being used as an alternative for typical transportation.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...