Protect your privacy. No one else is going to do it for you. Especially on Facebook. This clip will teach you how to alter privacy settings for your photo albums. This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about twominutes. For more information, including detailed, step-by-step instructions, watch this video guide.
Want to change your privacy settings on Foursquare? This clip will show you how it's done using the iPhone Foursquare application. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

Do the new Facebook changes scare you? Are you not sure what information on your Facebook profile is and isn't accessible to people outside your network? Larry Magid will walk you through each privacy setting in this video, beginning with Facebook's newest feature, Instant Personalization. The next part covers controlling individual content like events, photos, and status updates. The more you know, the more control you'll be able to maintain over your information.
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial,

Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

Getting locked out of a bedroom or bathroom can be a real bummer. Fortunately, these locks are easy to "pick" and get yourself in. This how to shows you clearly what to do to get yourself back inside so you don't feel frustrated all day long. This excellent video takes you step by step through the process. This video talks about 2 different types of locks and the two different types of tools you'll need.

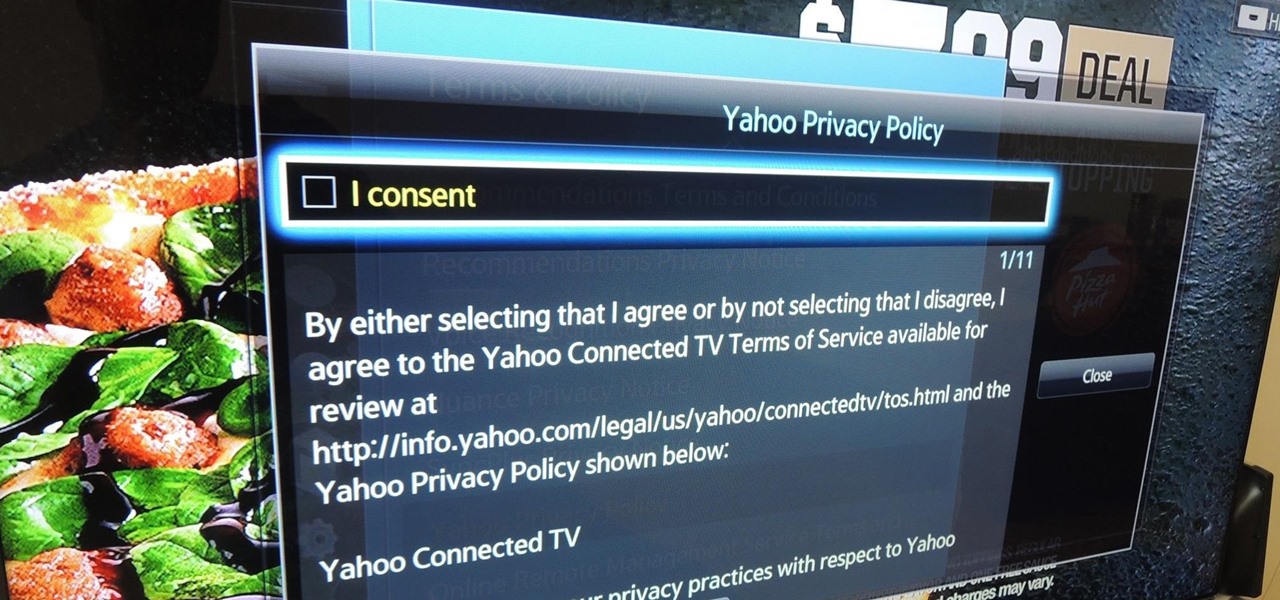
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

Learn what happens during an aircraft rollout from the National Aeronautics and Space Administration, more commonly known as NASA. They spill the goods on Newton's three laws of motion and how they affect the rollout phase of landing airplanes. Learn from the master of space exploration -- NASA!

In this video, learn about aircraft flares from NASA. The National Aeronautics and Space Administration provides valuable information about Newton's three laws of motion and how they apply to aircraft landings and what happens when mistakes happen (flares).

The National Aeronautics and Space Administration (NASA), provides this educational video on how Isaac Newton's three laws of motion apply to aerospace and the climb and descent of an aircraft. The powerhouse of space exploration is one place you should learn these concepts from.

Ever watch a cheesy movie and say "That monster is so FAKE!" but not really understand why? Well monstrous monsters are governed by a little biological rule called the Square-Cube Law, a scientific term combining math, anatomy and physics into one educational tool to recognize theatrical baloney when you see it. Just watch this video to see the explanation of the Cube-Square Rule, how it works and its ramifications for our favorite B-Movie pet monsters.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

Don't look much like Taylor Swift? Don't even have the same colored hair? It doesn't matter—you can still get Taylor Swift's hottest hairstyles as long as you have the right length. Katinthehat4883 shows you her method of mimicking Taylor Swift's latest curly hair. You'll need only four items: a curling iron with glove, hairspray, hair shine serum and thermal protection spray.

The first video introduces the basic electrical quantities of charge, current, voltage, and resistance. The concept of quantities and units is explained. The units of Coulombs, Volts, Amperes, and Ohms are described. The three basic formulas of Ohm's Law (E=IR, I=E/R and R=E/I) are also introduced.

This how-to video is about Fourth Law of Exponents. Before going to see this let's first know what the fourth law of exponent says. The fourth law of exponents says that "any value other than zero brought to an exponent of zero is equal to one".

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

They say that behind every joke is a half-truth. If that adage itself contains a grain of verity, the Daily Show's satirical Glass piece should raise a few eyebrows amongst the Glass Explorer community.

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to get started using Symantec's Endpoint Protection Small Business Edition on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

In this video tutorial the author shows how to use the Cosine Law. He shows how to find an angle of a triangle where he know all the sides of a triangle, using the cosine Law. He uses a lower case letter to designate a side and a capital letter to designate an angel apposite to that side. He gives the formula for the cosine law using a triangle as an example. Now he goes on and demonstrates how to use a scientific calculate. He shows how to use the degree mode in the calculator to solve these...

Applies to Senior, U19 and 7's players. This new rugby law was issued in 2007. It is the 2007 Scrum Law and it covers the crouch, touch, pause, engage steps off the classic rugby scrum. Scrums start off every rugby match.

Get yourself a metal sled that runs on tiny plastic ball bearings, and you'll be ready to demonstrate to your classroom Isaac Newton's third law of motion: Every action has an equal and opposite reaction.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through clear your Google search bar history (not to be confused with your Google Search History, which you may also want to disable). This tutorial will teach how to do just that. Take a look.

As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial, you'll learn how to use the freeunblockme.com tutorial to surf the web anonymously.

This video teaches the basics of Ohm's law, which is an important equation in electrical engineering. The three variables which are used in this equation are V, which stands for voltage, I for current, and R for resistance. The equation for the law itself is I=V/R. This law defines the relationship between these three very important electrical properties. The host of the video further explains what voltage, current, and resistance are and how they work in relation to an electrical current. Gi...

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.