How To: Draft your fantasy football team
Don't let fate decide the makeup of your fantasy football team. Participate in a live draft with these tips.


Don't let fate decide the makeup of your fantasy football team. Participate in a live draft with these tips.

In Judaism, men customarily cover their heads with a skullcap as a sign of humility before God, though it is not mandated by law. In Hebrew, it is called a kippah; in Yiddish, a yarmulke. In Europe, the custom dates to the end of the 16th century. Learn how to wear a kippah (yarmulke) with this Howcast guide.

The adoption process can be long and taxing. Start off right by learning the basic procedure. Step 1: Learn the requirements

Learn how to play "I Hate This Part" by Pussycat Dolls, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here:

In this five-part video tutorial series, you'll learn the fundamentals of working with electronics. To follow along, you'll need a 28-280 Electronics kit from RadioShack.
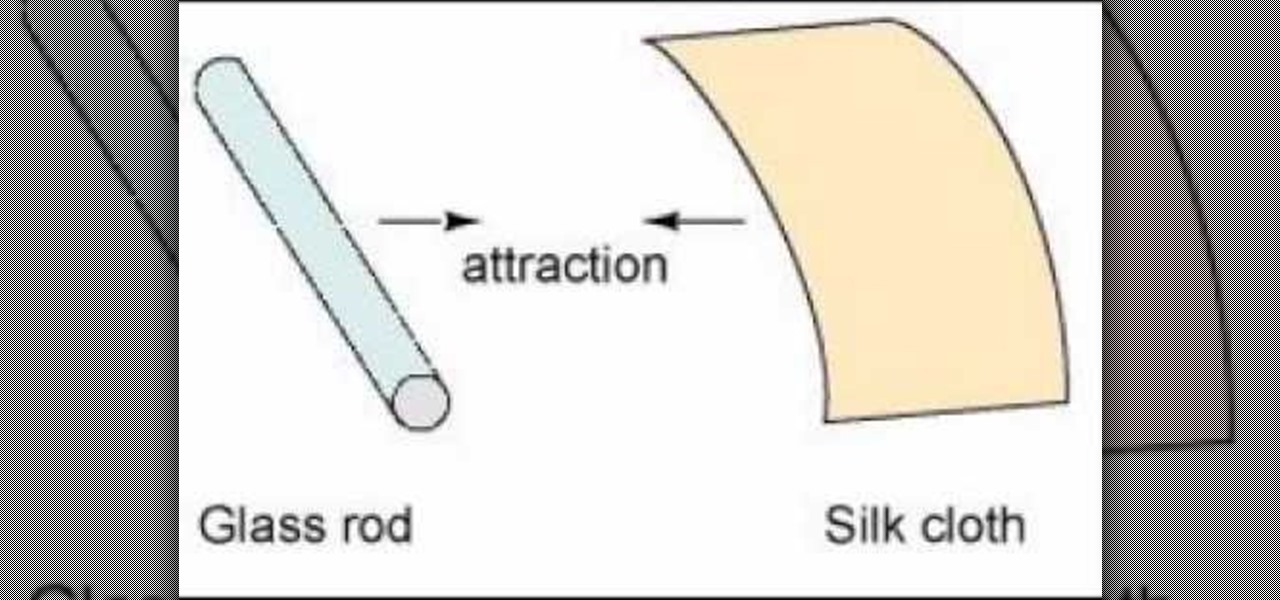
In the first video, you'll see how contact between different materials can result in attraction or repulsion. Experimental results are discussed that led to Ben Franklin's one fluid theory of electricity. It explains how clues were found from rubbing different materials together.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

As necessary as sleep is, millions of people struggle with it every night. More than 50 million Americans suffer from any number of sleep disorders. If you're one of them and want a more satisfying, consistent sleep, then the LectroSound Sleep & Relax Soothing Noise Machine may be the perfect addition to your bedroom. For only $15.99, you can give yourself the rest and reinvigoration that your body and mind crave.
Sure, your search history can be useful, but more often than not, it's a paper trail of privacy infringement. It's perfectly reasonable not to want to see a complete list of your YouTube queries every single time you search for a new video. Luckily, blocking YouTube from saving your search history takes only a few taps.
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.
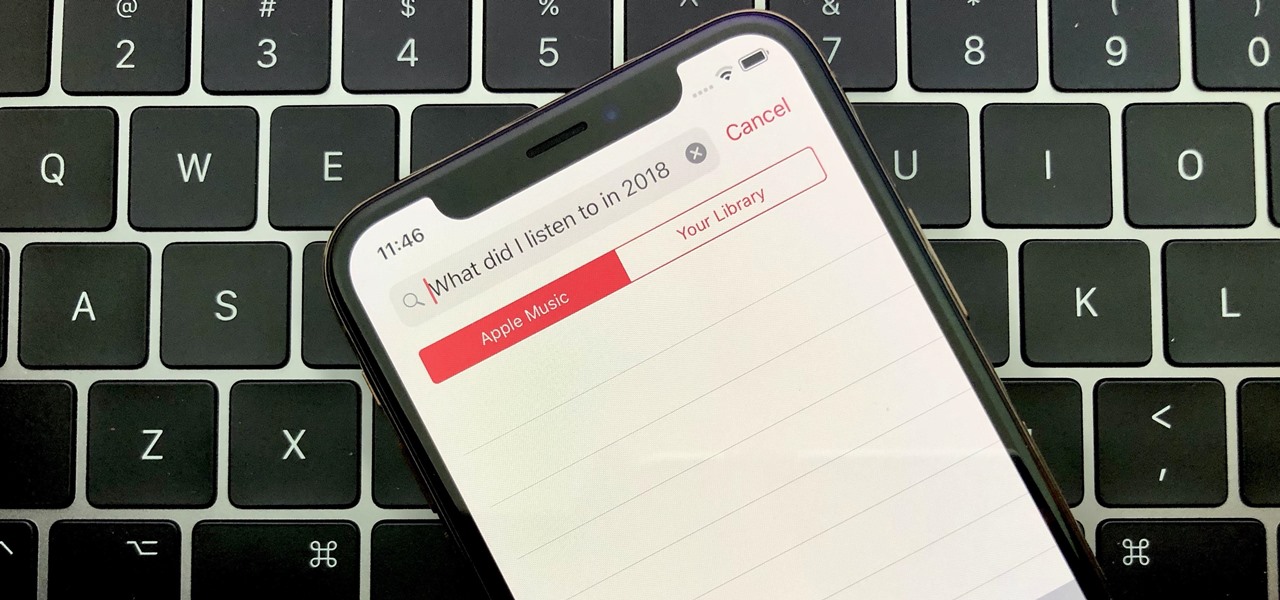
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

While some of our group chats should probably remain private and closed off, others will only get better with more people. Whether you're organizing an event and need a headcount or you want to share a funny YouTube video with a large crowd, you can add all the friends you wish to on Facebook Messenger by sending them a unique link.
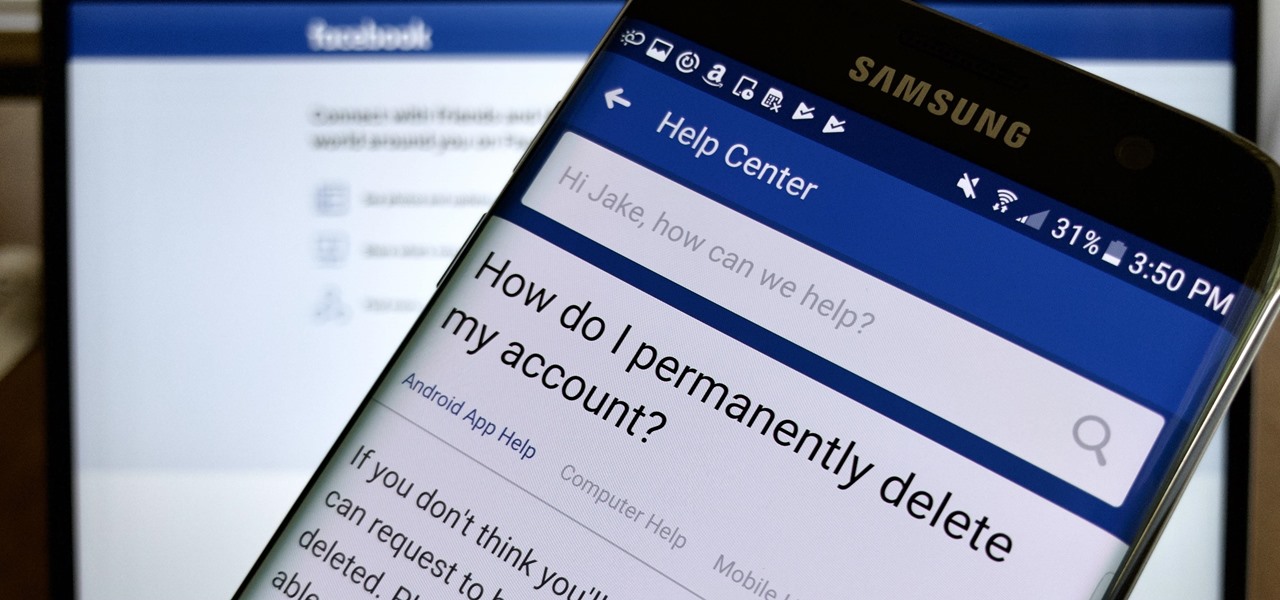
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.
BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.
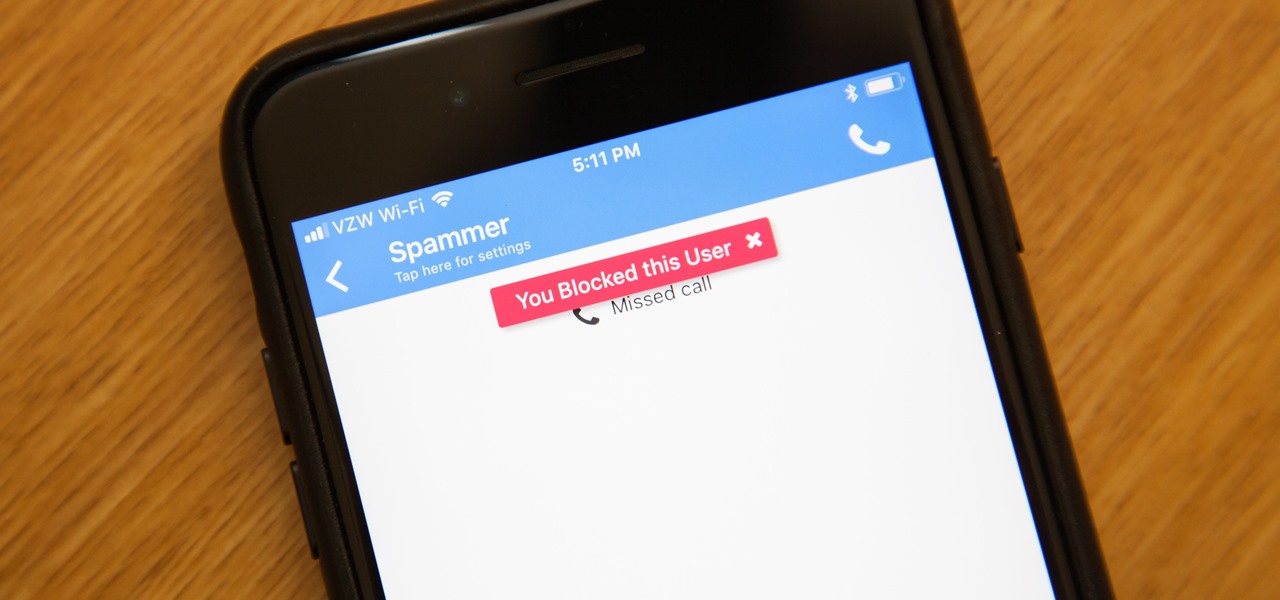
While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

What makes YouTube such a special platform is that anyone and everyone can upload their own content. Big players upload their videos to the same site that the little guy does.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.
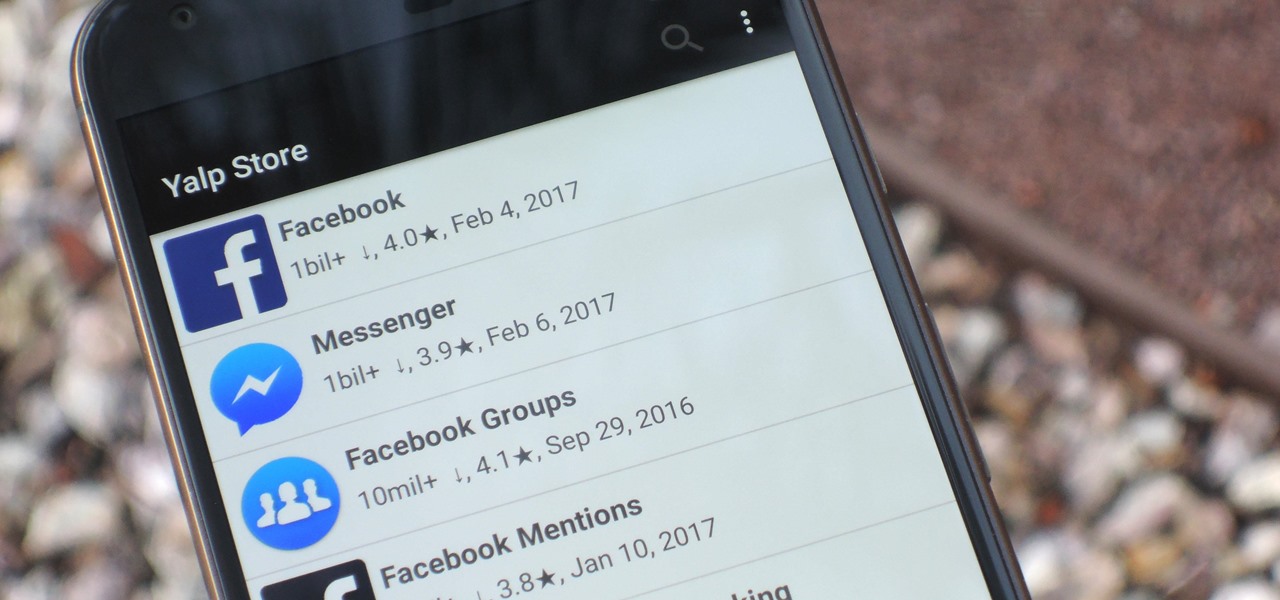
Android is Google's project, so of course you can see the search giant's fingerprints all over the operating system. Aside from the obvious user-facing apps, there's Google Cloud Messaging, Google Connectivity Services, and the much-maligned Google Play Services running in the background, to name a few.


In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Welcome back, my nascent hackers!
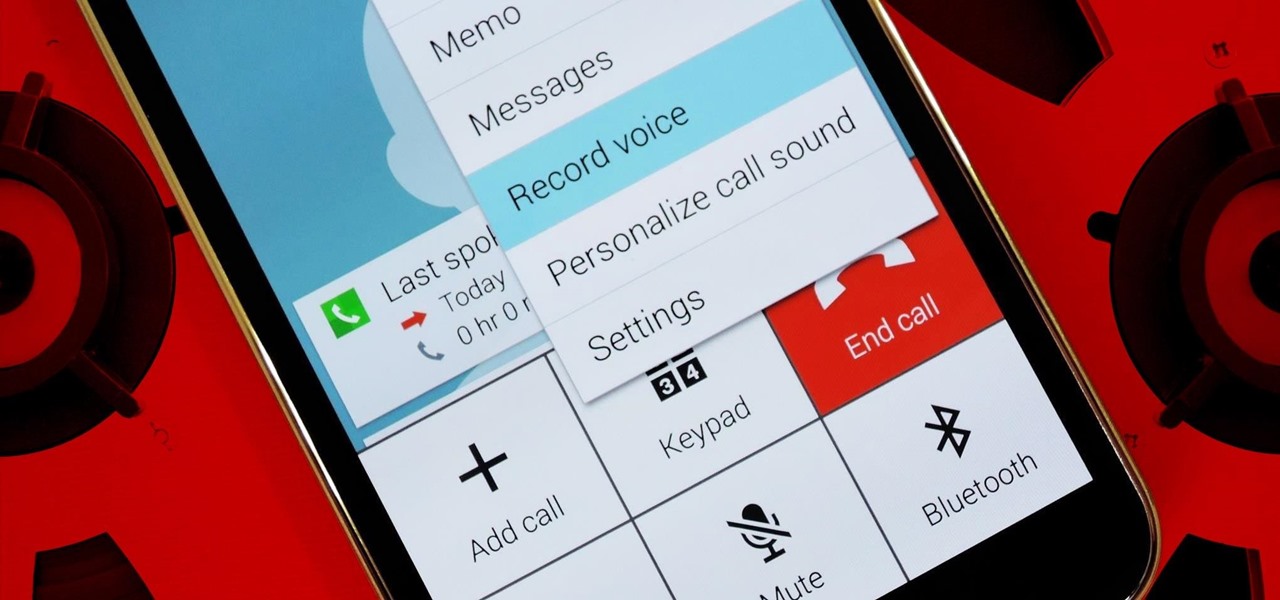
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Do you watch women with sleek and shiny hair with envy? Now you can transform your frizzy hair into a silky smooth style. This isn't magic and does take a little more time than toweling dry. But with a few products, a blow-dryer and a little extra time in the morning you can achieve this look.
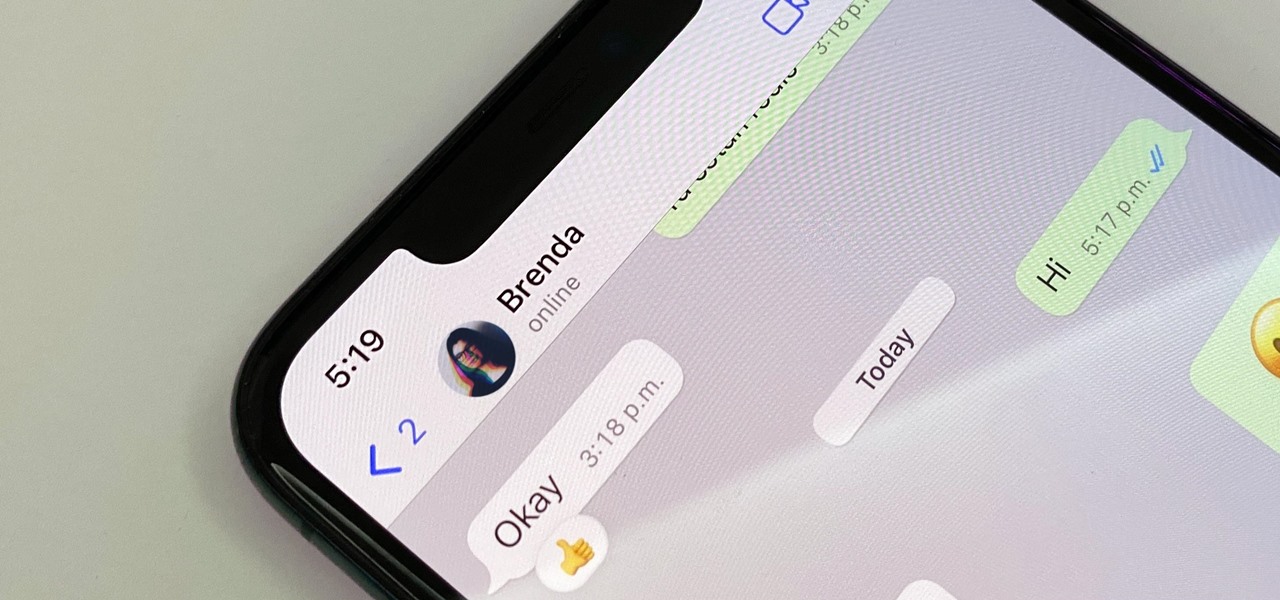
By default, everyone on WhatsApp can see when you're using the app. If someone recently messaged you and sees you're currently online, they may think you're avoiding them if you don't respond right away — especially if you don't share read receipts. However, you can block them from seeing your online or last seen status and apply it to everyone or just specific contacts.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.
Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.
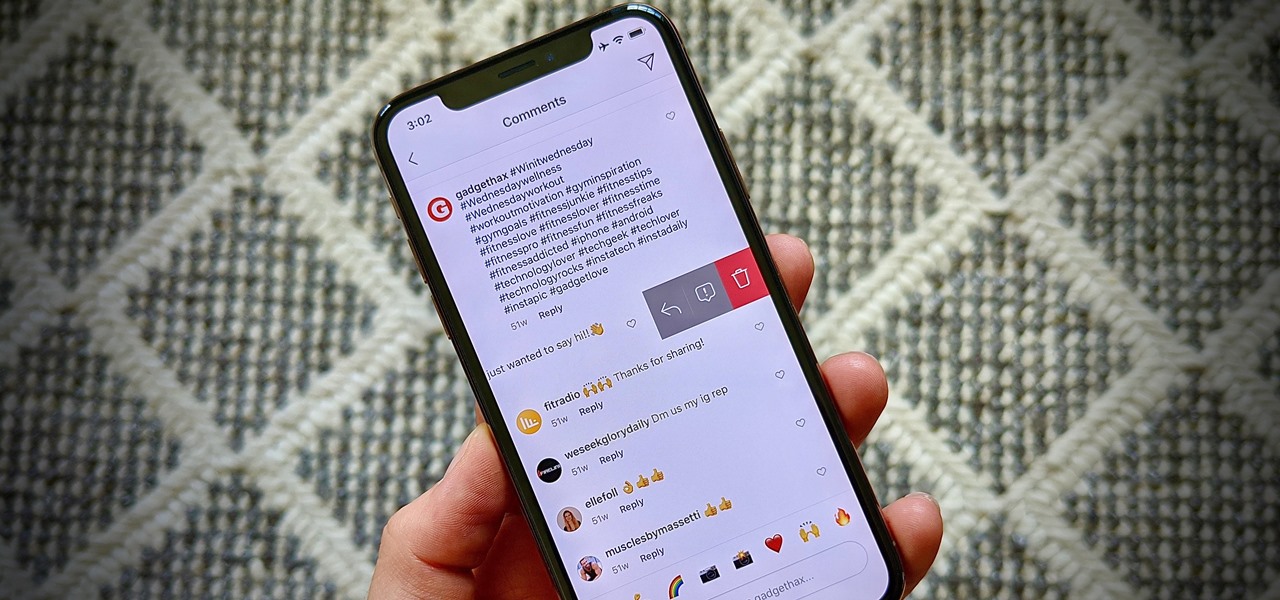
When you post a photo or video on Instagram, it's always nice to see positive comments from friends, family, and even fans. On the other hand, it's never fun to see spam or hate messages underneath your posts. Before, you'd have to delete these comments one by one, but now you can delete comments in bulk.