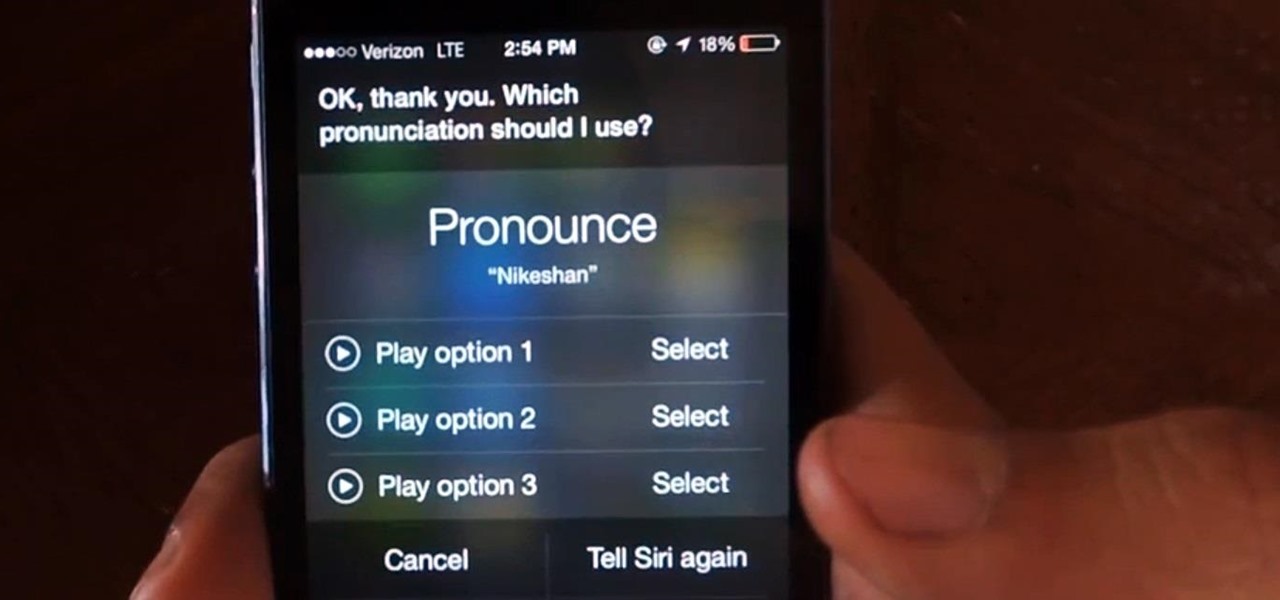
When it comes to pronunciation, Siri absolutely butchers my last name. Instead of pronouncing Aguilar as ah-gew-lar, my own "intelligent" personal assistant pronounces it incorrectly as ah-gui-ler.
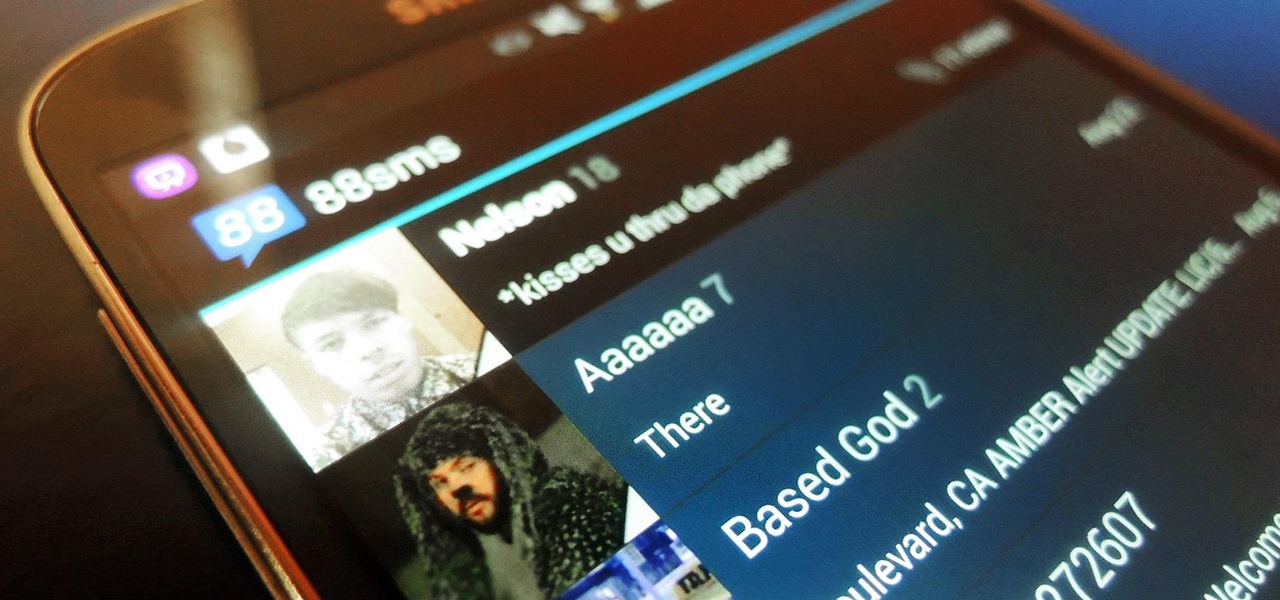
With CyanogenMod 10.2 recently released and the Samsung Galaxy S4 still waiting on Android 4.3, it only makes sense that the coveted features from both firmwares are highly desired by Android owners all over. We've already brought you a feature from each firmware—the cLock home/lock screen widget from CyanogenMod and the Google Play Edition Camera and Gallery from Android 4.3. Now we're bringing you another in the form of an updated text messaging application, ported from both Android 4.3 and...

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

With iOS 7, Apple is finally fighting back against spam, offering the option to block certain phone numbers from sending you text messages or iMessages (plus, phone calls and FaceTime too).

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.

Most of you probably have a set of blinds at home, the most popular being horizontal or vertical. They're great for keeping the sun out of your eyes and maintaining privacy, but unfortunately, each comes with its own set of problems.

I get advice from my friends on a lot of things in life—cool video games, movie reviews, and feedback on my choices in women. Friends can be very helpful in filtering out some of the excess noise and are more likely to give you suggestions you can relate to.

Some of my Facebook status updates are absolutely hilarious, and sometimes (though rarely) even my friends updates can get me on the floor laughing. And like most of you, I'm sure, when you come across something funny—you have to share it.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to release its own real-time picture and video messaging application, aptly titled Poke. One of the biggest criticisms (besides the wave of recent security issues) of Snapchat is that even though the messages self destruct and ...

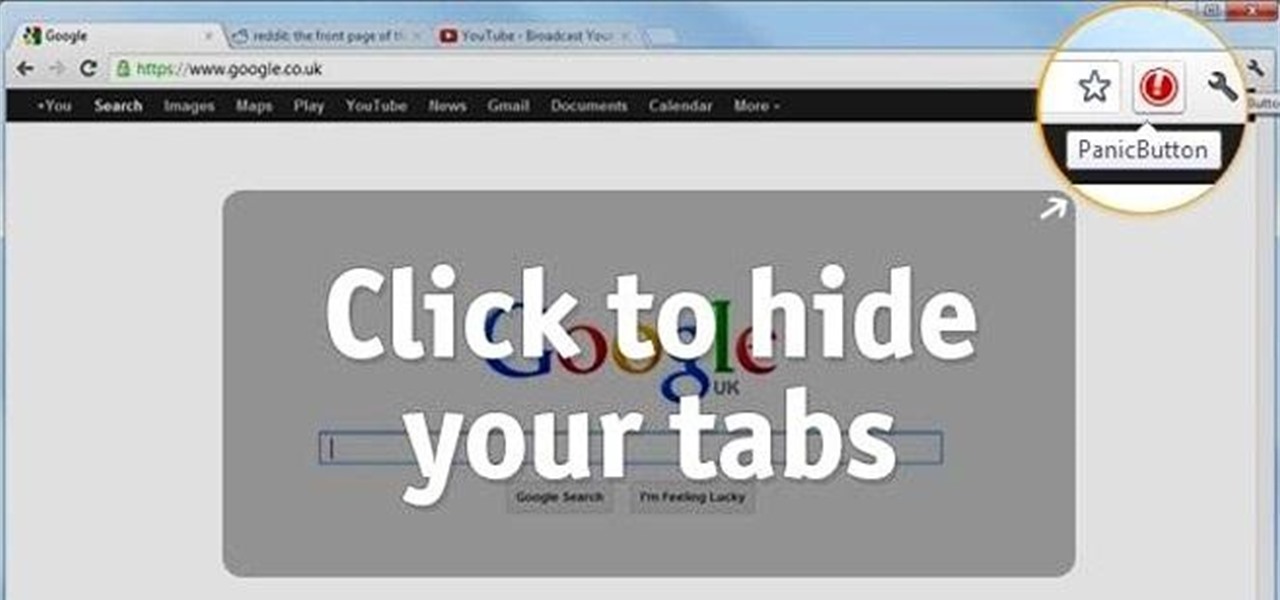
At some point or another, we've all been in that awful situation when someone walks up behind you while you're looking at something you don't want them to see. Whether you're tweeting during class, shopping for gifts online, or looking at something a little more NSFW, there are times when it would be nice to just click a button and have all your open tabs disappear.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

There's a strange grey area for "guerrilla filmmaking" on YouTube. Generally, someone shooting a video needs to get permission from the people in it to show their faces. But on YouTube, that "rule" is more of a suggestion (and sometimes not even that).

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Earlier in the week, Obama’s attorney general stated something that is quite alarming. “In this hour of danger, we simply cannot afford to wait until deadly plans are carried out, and we will not,” Eric Holder said during a speech at Northwestern University’s law school in Chicago. It's a very ambiguous statement. Why do people talk like this? Why can't they just talk straight to the point? Well, most of the time it's to hide something. Take a look at this video: What do you think of that! Th...

In this article, I'll show you how to make an awesome "Death Ray" using the large magnifying lens from an old projection TV. The lens is called a Fresnel lens; a device that employs several ridges to focus light, rather than a complete curve.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

Hi again, Just wanted to share a neat little code that I found way back, when I was presented with a spreadsheet which was locked and asked to ''unlock'' it or do whatever it takes to enable the user to edit it's contents.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

Hello, welcome to my first post! Today, I would like to talk about setting up a Page File Encryption in Windows 7 and Vista. But first - what is a Page File Encryption? Why should you enable this option?

Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

Facebook unveiled a lot of changes last week, and, as usual, it's causing a lot of consternation and controversy. People within my Facebook, and on Google+, keep asking how to remove the ticker, and are trying, and mostly failing to make sense of the changes.

Yesterday, Google's VP of Product Management, +Bradley Horowitz, sat down with founder and CEO of O'Reilly Media, +Tim O'Reilly, to discuss Google+, its future, and where it's headed. You can watch the hour-long video here: I wasn't able to find a transcript for this video, but O'Reilly has helpfully rounded up some of the more interesting points.

It's like the H-bomb. In slo-mo, it's stunning. In real life, it's terrifying. The footage below was uploaded by YouTube user NielsBorg, unfortunately lacking in description, but offers the following information via headline: "T90 shot taken by Photron camera at 18000 fps". The T-90 is a brute of a tank, a third-generation battle vehicle used by the Russian Ground Forces and Naval Infantry. The tank contains an autoloader which can carry 22 ready-to-fire rounds, loadable and ready to go in 5-...

You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean up the streets, compared to just ticketing them.

It's not uncommon for nature to inspire technology and innovative products. Airplanes were inspired by birds, Velcro by burrs and dog fur, bullet trains by owls and kingfishers, and gecko tape by... well, you can probably figure that one out. And one of the deadliest fish ever to swim the oceans has also influenced its share of merchandise; Sharks made humans faster in the water with Fastswim Suits, and now they've helped make one of the most rugged smartphone cases in the world—SharkEye's Ru...

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:
Welcome to Photography Contests World! The purpose of this world is two-fold. First, it will serve as a directory with featured listings of all types of current photography contests. If you have ever tried to search for a photography contest to enter, then you are aware of how many contests are scattered all over the internet. Photography Contests World will strive to bring you information on as many contests possible in one central location, beginning with mostly USA and international contes...

PopSci's Gray Matter demonstrates again and again what the layman should absolutely Not Try at Home. Which is precisely what makes Gray's experiments so fun. Remember when the mad scientist fully submerged his hand in liquid nitrogen? Today's demonstration also plays with what is (quite reasonably) assumed to be extremely dangerous and painful: torching the human hand.

Gain control over your files online with Windows Live SkyDrive 2011, just one of the many new features of the newly released Windows Live Essentials 2011. You get 25GB of free online storage and tons of new features. You can store tons of documents, access all your important files and share the plethora of pictures you've amassed, all within SkyDrive.

Ever been Privacy Zuckered? Roach Moteled? Friend Spammed? If you've been on the net long, odds are you have — and worse! Fortunately, there's a new resource for keeping track of the web's worst design practices; it's called "Dark Patterns" and it aims to "name and shame" sites that employ "user interfaces that have been designed to trick users into doing things they wouldn't otherwise have done."

In the past you may have blocked wall posts so you wouldn't get fuel, goods, and other random things from your applications. But you may wish to rethink this, at least for a while as the new truffle hunting feature requires wall posts.

The day of interactive porn has arrived, all thanks to Steve Jobs. The iPhone 4's new video-call feature, FaceTime, enables users to have live video chat sessions over a Wi-Fi network, via the iPhone's camera and screen. Unsurprisingly, the porn industry was immediately inspired.
I'm having a hard time finding my older posts, so I'm sure you are too. I'll put them all here so you can find them easily. You can bookmark this if you want :)