Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Math scares a lot of would-be electronics lovers away from the field, and if you really hate math this is probably the video in this series where you stop. It will teach you how to use Ohm's Law to calculate resistance and how that applies to a basic circuit.

Angle grinders are very powerful and useful tools, but like many such power tools they are extremely dangerous if you don't know how to use them. This video goes over a variety of must-know safety precautions that you should take before using an angle grinder to grind for your own construction projects. It covers proper eyewear, fire protection, and setting up the device for use.
In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...
This video makes you understand Flash Cookies and teaches "How to remove them" to keep your privacy.

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

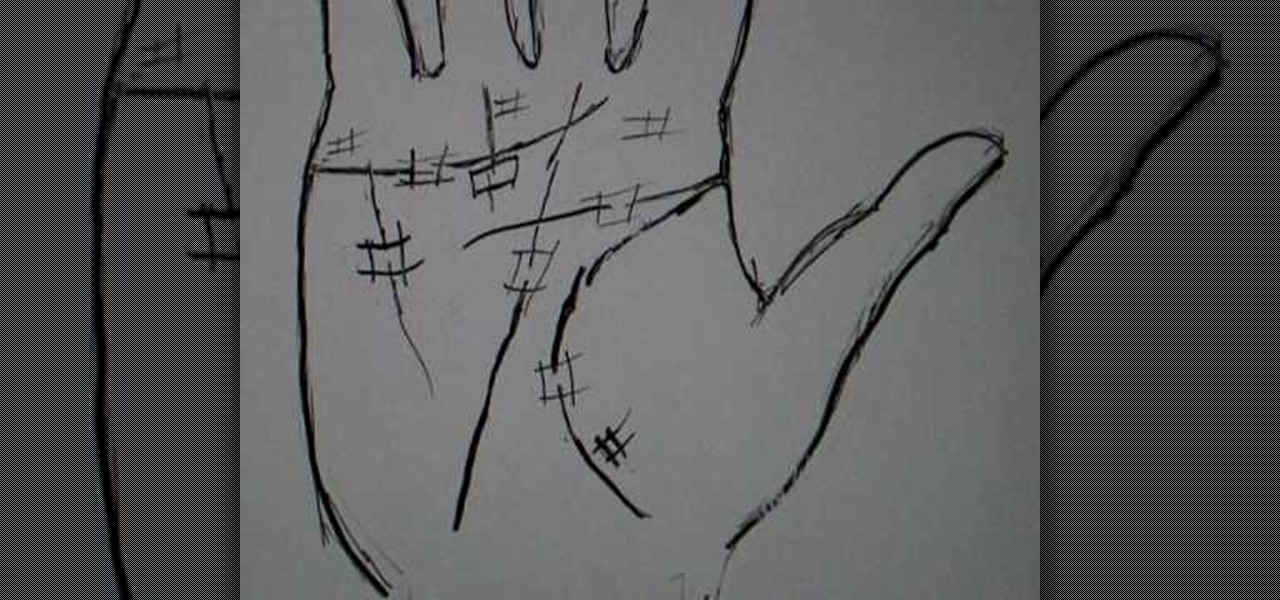
Peter John teaches us how to palm read: The squares on the palm in this tutorial, Squares come in all sizes all around the palm of the hand. If they come on the lifeline, this will mean that a person has a certain amount of protection in their life. If they have boxes that are overlapping, this will mean that a person is going to have a change in their life but they are going to be okay throughout it. The square is like the protection that surrounds the events that are going to happen in the ...

In this tutorial, we learn how to get free virus protection with Avira. To do this, first go to Free AV, and download the software. After you install everything, open the program up. Next, you will want to scan your computer for any viruses that may be present already. It may take a while to scan your entire computer, but it will search all of your different files. If something comes up, you can choose how to deal with it and get rid of the virus if you wish. This is also great for any emails...

In this how to video, you will learn how to remove 3M paint protection film, also known as a clear bra. This is used for protecting the front of a vehicle. To remove it, you will need to use a heat gun on the film so that it will peel off. This takes a while to remove, so be patient. The film itself is very useful, as it protects from rock chips and bugs while driving. Note that it is a lot easier to take off during the summer time since the car exterior is already hot. You should not worry a...

In this video tutorial, viewers learn how to repair the write protect on an SD card. An SD card is a non-volatile memory card format that is used in portable devices. If the write protect on a SD card is broken, the user cannot record any files onto the card. To fix this, viewers will need a small piece of scotch tape. Put the tape on the notch of the SD card. Do not cover the metal tabs at the back. This video will benefit those viewers who have a SD card and would like to repair the write p...

This Spirituality video clip will show you how to wrap a Wiccan cinnamon stick bundle for protection. You need some cinnamon sticks, scissors and ribbon. Cut a very long piece of ribbon, lay it down on a table, place the cinnamon sticks on the ribbon, tie a basic knot flip it over and tie another knot. With one end of the ribbon, go over and in between the sticks and with the other end, go under and in between the sticks. Now put one more knot in between the sticks. One more time go under or ...

Dave Andrews from HelpVids is going to teach you in this video how to configure the Windows XP firewall. To do that, you need to follow these steps: 1. Go to Control Panel and make sure that you are in the classic view.

Learn how to cut tile with this DIY video tutorial. If you need to make angular and circular cuts, use an angle grinder and fit a diamond disk. You'll need to fit a continuous diamond disk, not a segmented one, because a segmented disk will chip the tiles. And if you're using an angle grinder, don't forget your personal protection equipment, ear muffs, dust mask, and eye protection.

With this cool little how-to, learn about Newton's laws of motion and try first hand to see centripetal force in action. You'll need balloons and a coin and a lug nut.

1. First of all you need go to the 'view' button at the top bar menu. From the drop down click on 'view options'. Then click a 'check mark' against the 'kind' and then click 'ok'.

Want to know about Newton's three laws of motion and how they affect aircraft landings? NASA has answers. NASA, aka the National Aeronautics and Space Administration, tells how Newton's laws apply to landings. There's no better place to learn from than the juggernaut of space exploration.

Carol Baldwin-Moody of Wilmington Trust describes the challenges that are present in her line of work as senior vice president and chief risk officer. There is a strong legal backing to every major issue in today’s society. Baldwin-Moody has come across several scenarios that aren’t covered by the dated constitutional law in effect today. In past years, a risk officer was thought to be a management concept that would be useful, but not worth the investment. Lately, a risk officer career has b...

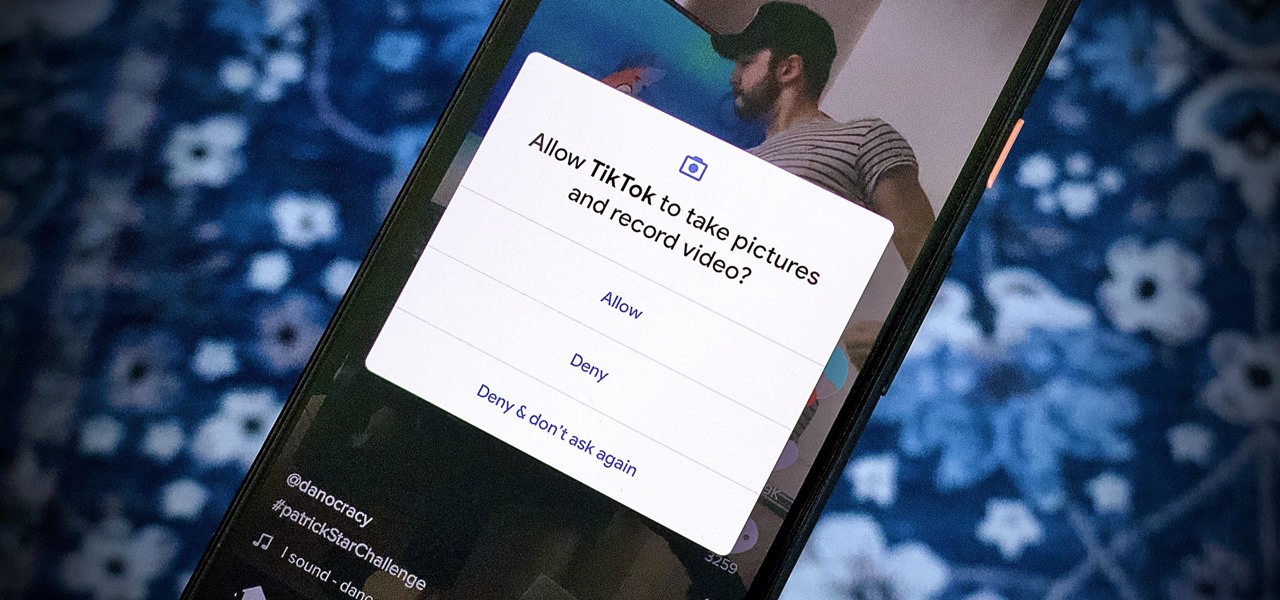
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

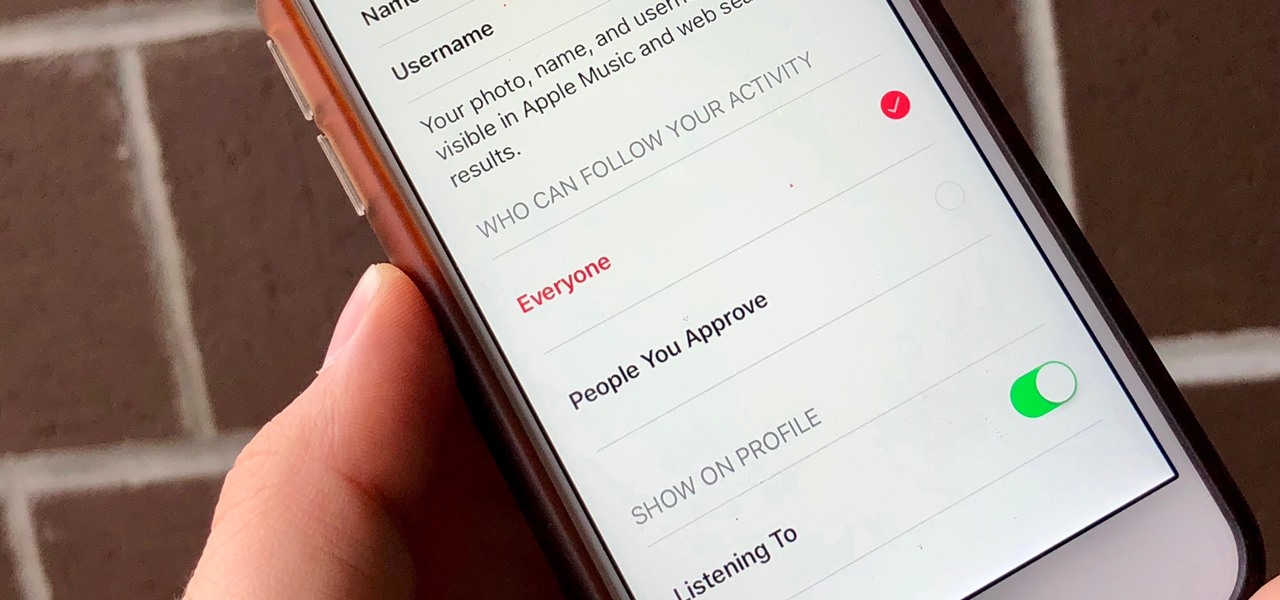
Apple Music, Apple's answer to Spotify, has many interesting features packed in to make that $9.99/month price tag as attractive as possible. One of those features is geared towards social listeners — those who want to follow other Apple Music users and who want to be followed back. But here's the thing: how do you know if your account is public or private?

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Tired of clicking on interesting looking links in Facebook, only to discover that they are hidden behind a page you have to 'Like' before you can see? If you're surfing using Google Chrome, you can completely bypass this privacy setting. When you get to the page, go to the menu bar and click on 'Inspect Element.' Then you'll see the code for the page, and you'll be able to get around the block to see the page you want.

Facebook Places is a new location-based sharing tool that Facebook unveiled not too long ago. It works like Foursquare, in that you can check yourself into locations. Not only that, you can check other people in, and other people on your Friends list can also check you into other locations as well. So if you don't want to broadcast your every move to the universe, you'll have to go into Facebook and update your privacy settings. Again. Better to be safe than let your boss know by accident tha...

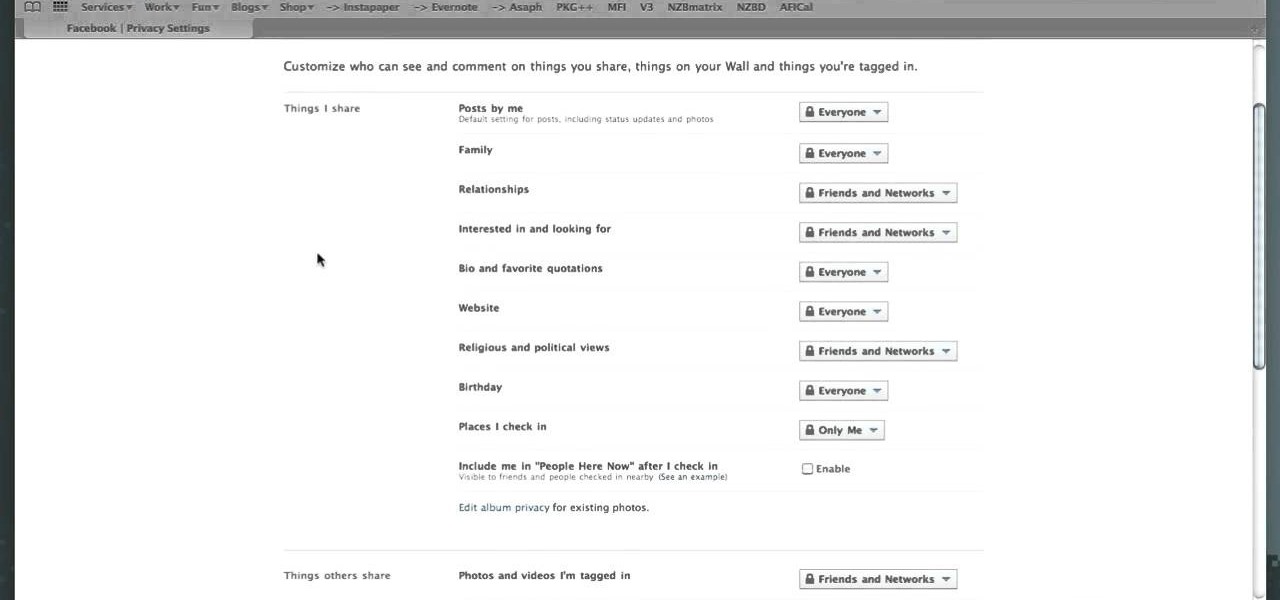
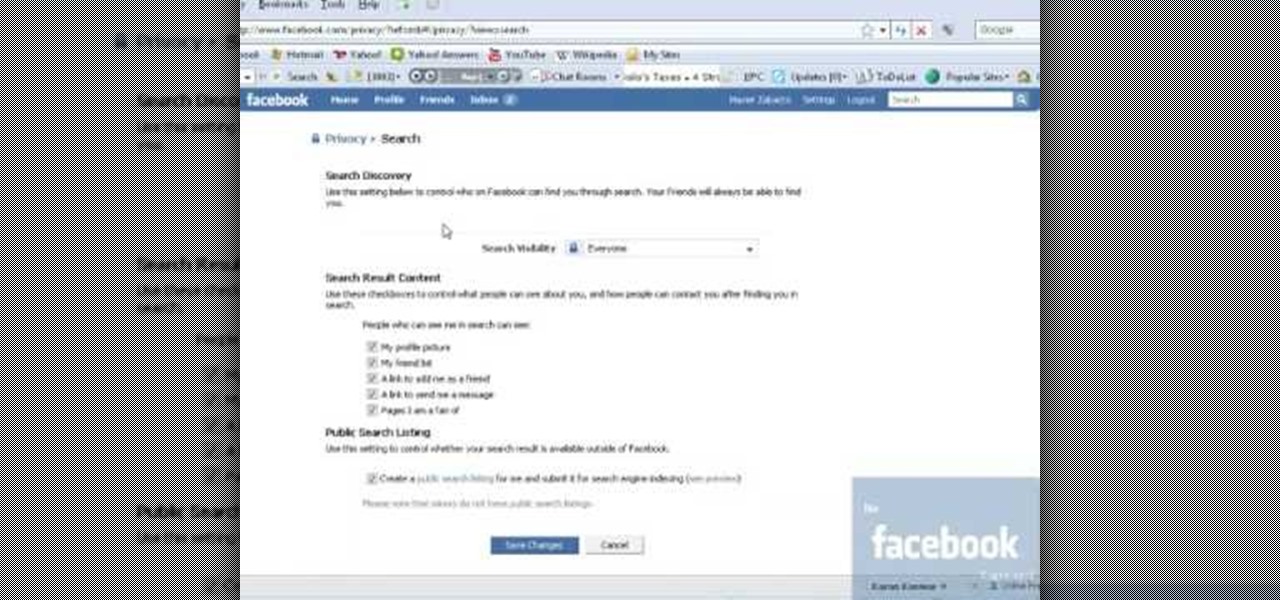
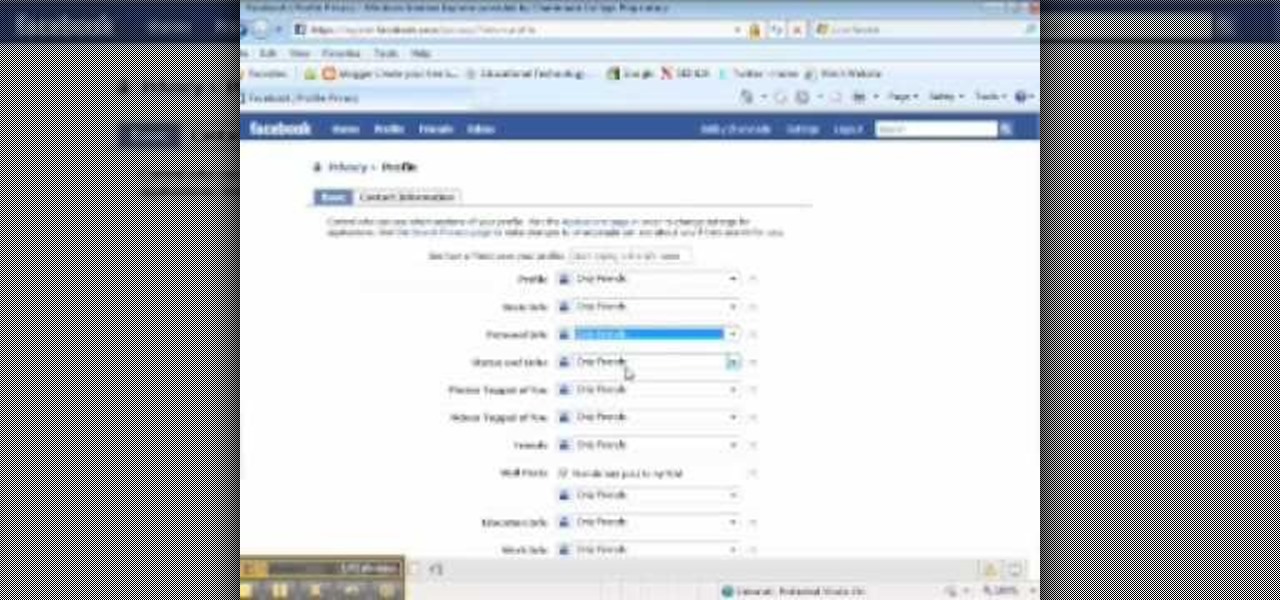
In this video, we learn how to make your Facebook profile less public. First, log onto your Facebook account, then go to your privacy settings. Through there, go to search and choose who you want to allow to search for you on your site. After this, save your settings and move on to the other sections to change more privacy settings. If you do not want people that aren't your friends to see your information or to be able to search for you on Google, this is a great way to go. Making your infor...

This video tutorial from ChaminadeENN shows how to set your Facebook account to private mode. First what you need to do is to sign in to your Facebook account.

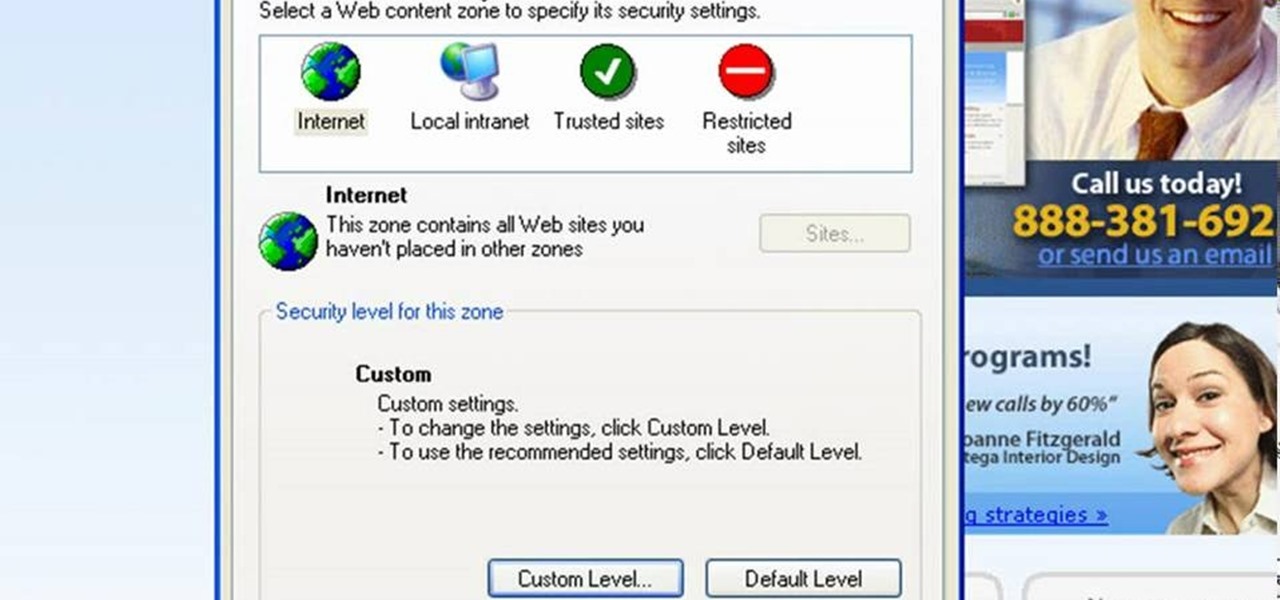
This video will show you how to enable JavaScript, accept cookies, and allow pop ups in Microsoft Explorer. The first thing you will need to do is to go to tools on the menu bar, then choose options, and choose the security tab of the new window that will pop up. To enable JavaScript click custom level, scroll all the way down until you see the scripting section, make sure that all three radio buttons are set to enabled, and finally click ok. To enable cookies, go to the privacy tab and make ...

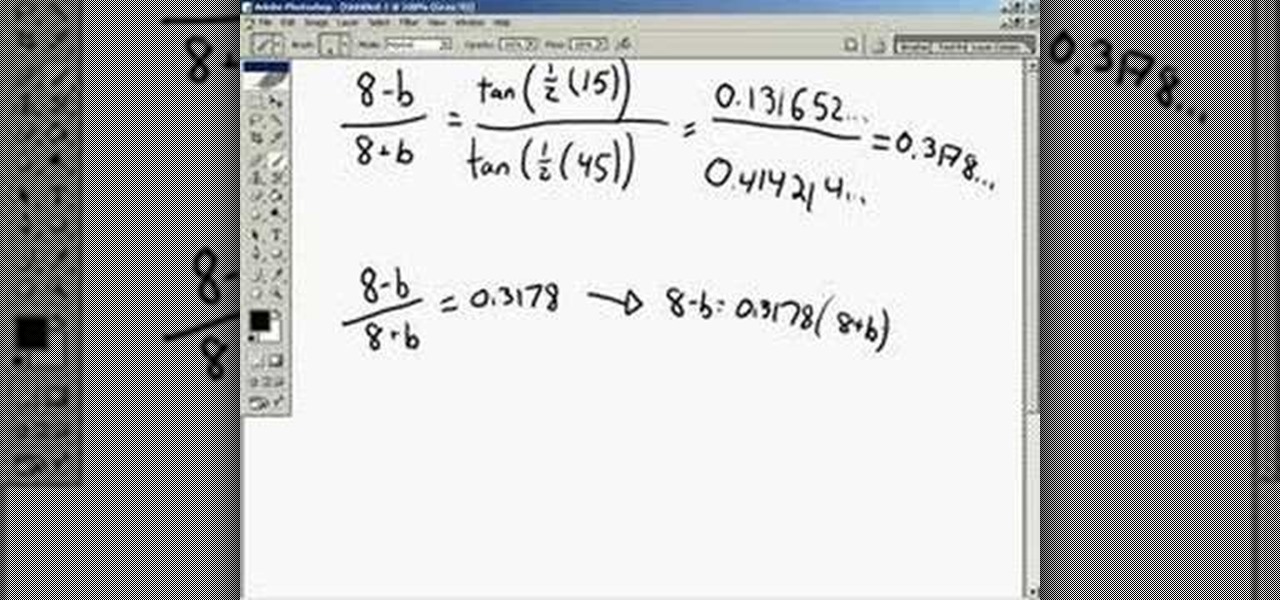
This video explains and provides examples for the law of tangents, a law occasionally used in trigonometry.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to unpack and solve problems requiring you to rewrite and simplify an expression with th...

Spyware can cause all sorts of problems for your computer. It sneaks its way onto your computer and then does its damage. You can remove spyware from AOL 9 by double clicking AOL spyware protection on your desktop. If you don't have that, you can search for spyware. Once you open the spyware protection, it will allow you to scan for spyware and display it on the screen so you can choose which software you want to block. This video will benefit those viewers who use AOL and would like to learn...

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

The day has finally arrived — Samsung has unveiled the Galaxy S9 and S9+. Apart from minor upgrades, the two might not appear to be much different from last year's S8 and S8+, but that's not necessarily a bad thing. One feature that hasn't changed is the Galaxy's IP68 water-resistance rating. That's a great score, but it begs the question — what does that number really mean?

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.