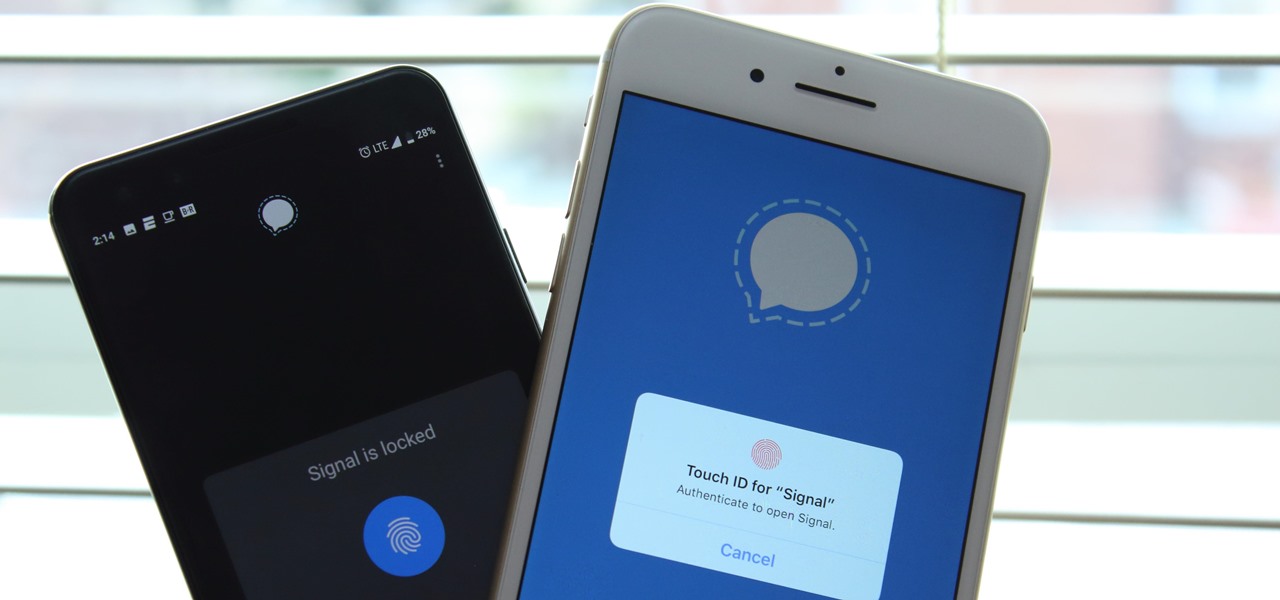
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.
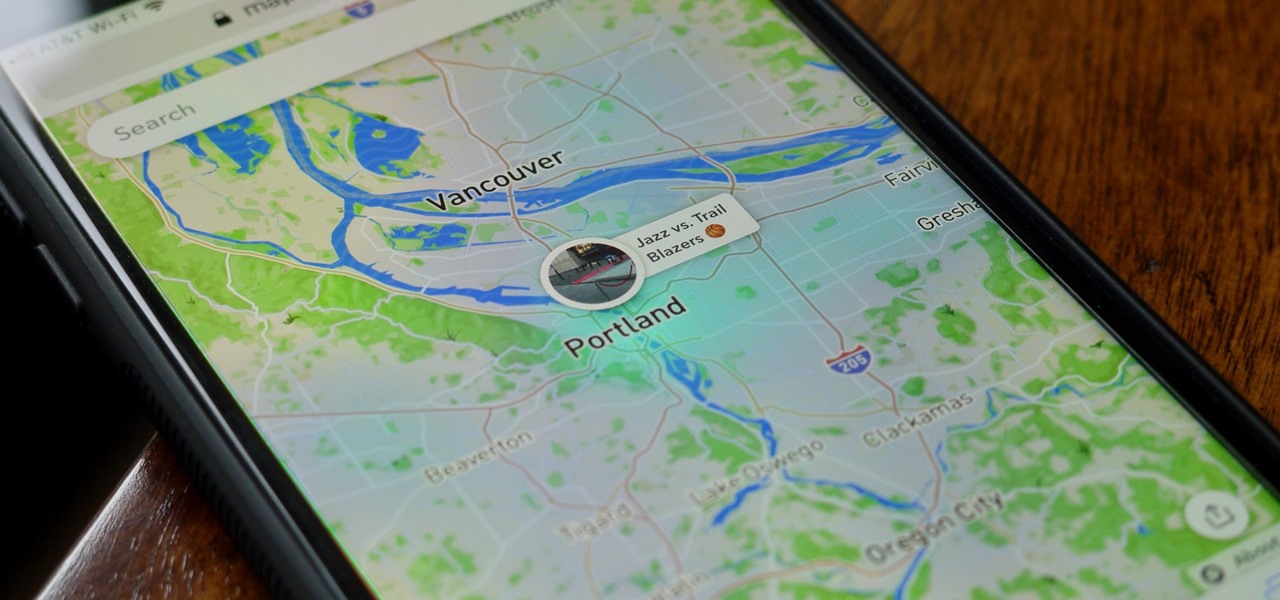
When you need to know how to get somewhere, Google Maps is the app to beat, but the king of navigation doesn't want to stop there. Google aims to make its navigation app for more than just directions, as made clear by its recent feature that lets you follow businesses in the app. Combining timely news and events posted by local businesses with real-time transit seems like the perfect match.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.
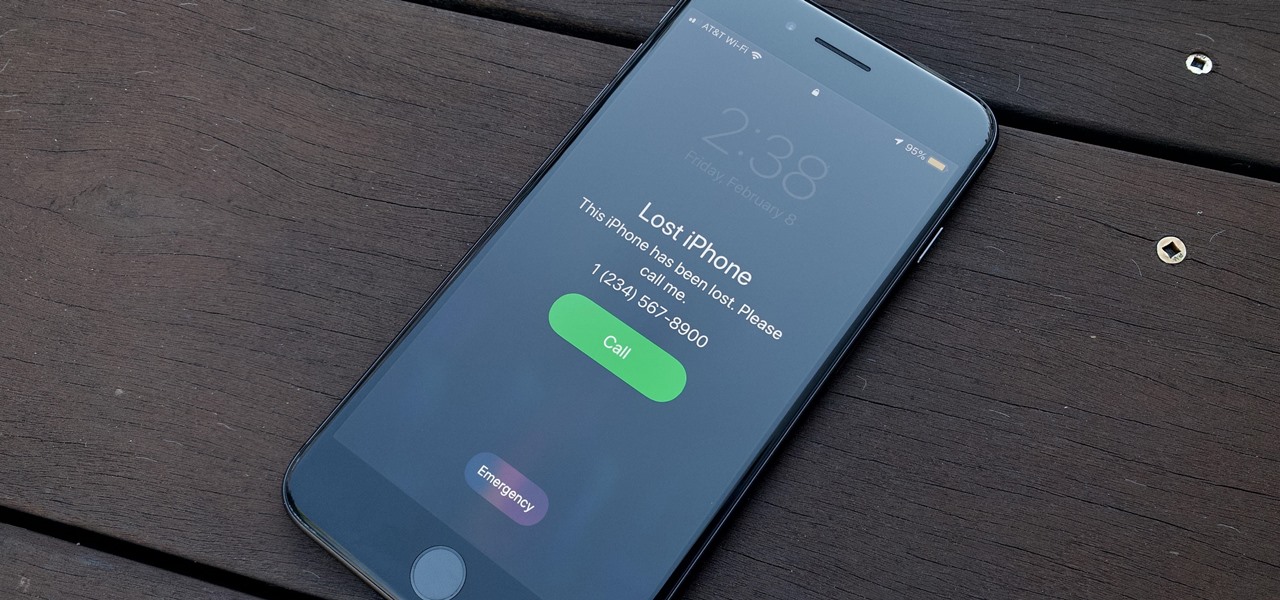
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

On the surface, Instagram is pretty intuitive, so you might think that you already know everything there is to know about using it on your iPhone or Android phone. But this photo and video-sharing app is constantly adding new features, some of which don't make the press releases. Even if you're an Instagram guru, chances are you've missed one of these hidden goodies.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

Anyone remember Google Goggles? Well, it's back with a new name: Google Lens. But this time, there's more machine learning and it's integrated into many different Google apps and services. The latest is the Google app for iPhones.

There has never been a better time to be a movie enthusiast, with more options now than ever to buy high-quality digital titles to watch on almost any device you own. That said, all those choices can lead to your movie collection scattered across different apps and services. What you need is a way to combine those movies into one, convenient location — and there's an answer to that.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

The holidays are here, which means a slew of new smartphones are set to be gifted to loved ones in the spirit of giving. Of course, a great case to compliment and protect that precious flagship is a must, regardless of whether it's a OnePlus 6T, iPhone XS, or Galaxy Note 9. And while quality cases usually come with a hefty price tag, there are plenty of Black Friday deals to keep you from going broke.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The dream of Google Glass lives on via North's stylish and normal-looking smartglasses that bring text messages and navigation prompts into the user's field of view and Amazon Alexa integration for voice-activated assistance.

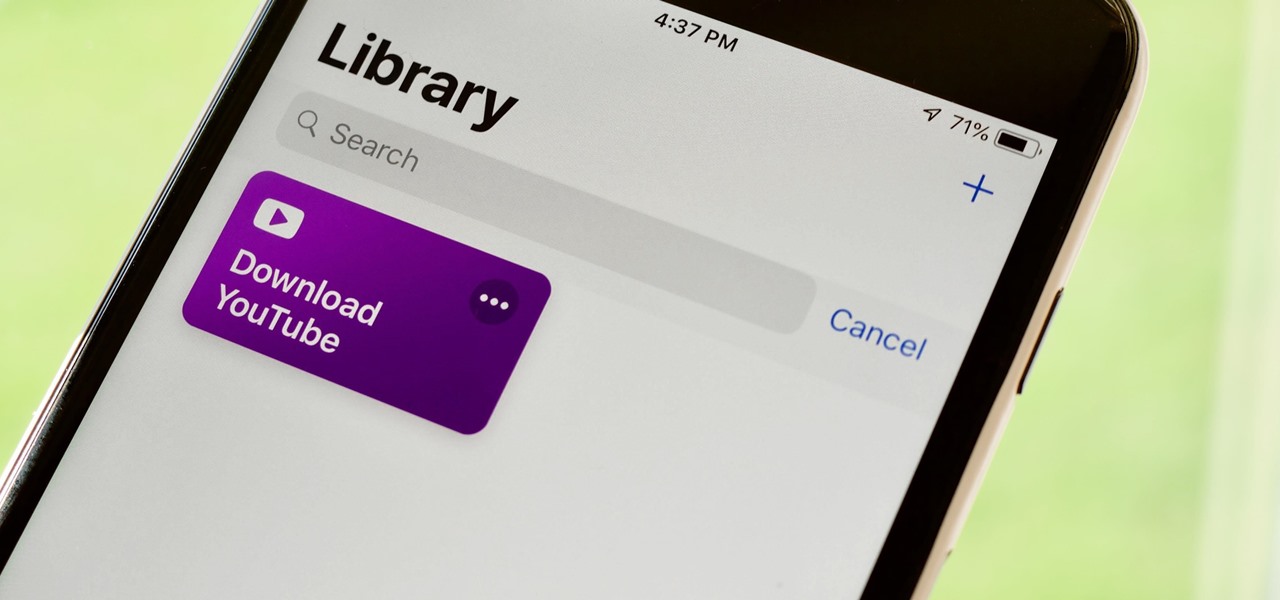
If you've ever wanted to download YouTube videos directly to your iPhone, there's an easy solution — just update to iOS 12 and install Apple's new Shortcuts app. With the Workflow-replacement app, you can add a shortcut that lets you download any YouTube video you want, without needing to jailbreak or use shady third-party tools.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

There are a lot of things that make iOS great, but lock screen widgets are not among them. If you want more information on your lock screen other than the date, time, and notifications without having to swipe to a sidebar of widgets, you'd normally look toward Android. However, iOS 12 aims to shake that up a bit with a secret Weather widget for the lock screen — not for the Today view.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

In case you missed it, you don't have to chat one-on-one anymore in Snapchat. The company added group chats back in 2016, and they are increasingly gaining new features such as video and audio chats, so communicating Snapchat-style with all your friends at once is better than it's ever been.

The augmented reality business was all about audiences this week. Vuzix looked for an audience with the Supreme Court of New York regarding a defamation lawsuit against an investor. Magic Leap held an audience with royalty, showing off the Magic Leap One in a rare public appearance. And Snapchat wanted to remind its consumer audience of all the things its camera can do.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

Not many smartphones are announced at CES these days — instead, you'll mostly see other types of electronics like Energeous's WattUp and Li-Fi. However, ASUS decided to share some good news for their US customers, and it comes in the form of a new phone with some interesting specs and a budget-friendly price tag.

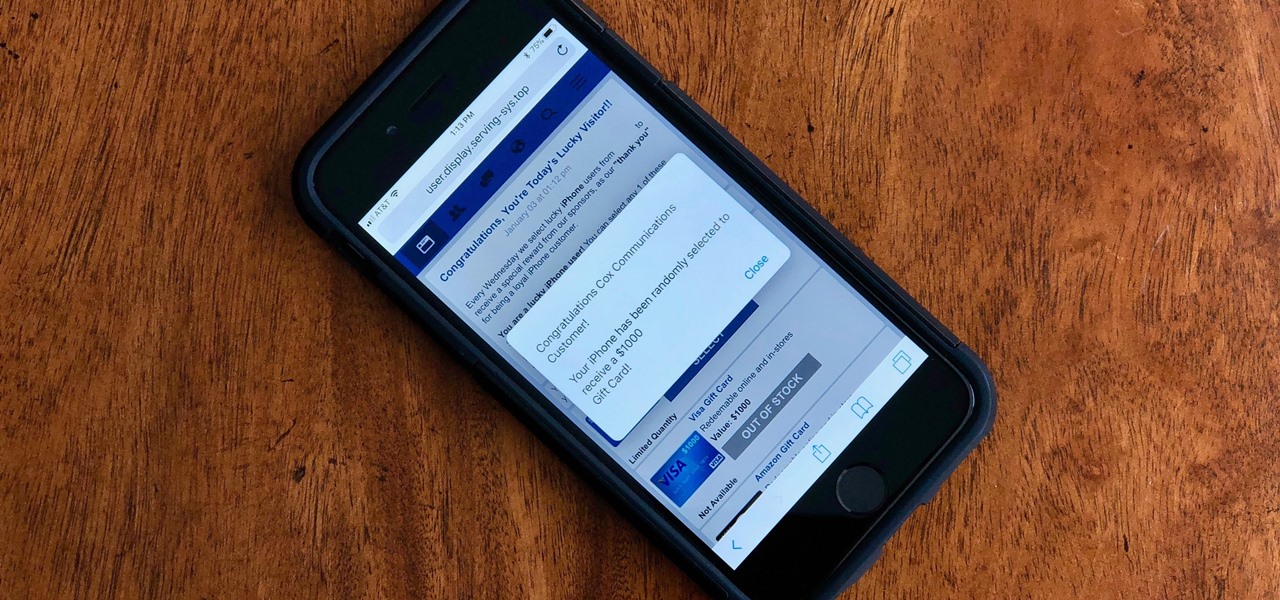
Safari for iPhone is generally a good mobile browsing experience — except when it isn't. Popup ads are a real issue, and they cause both great annoyance as well as concern over iOS security. How do you stop these nuisances and return to a web without fear of popups?

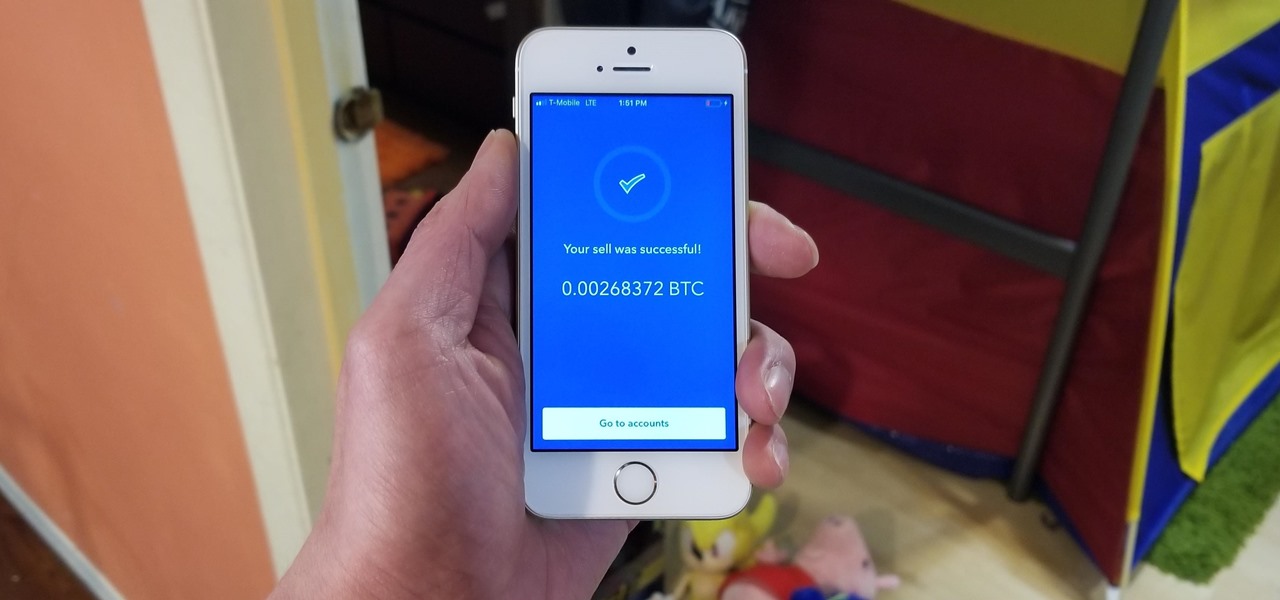
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

Huawei's sub-brand, Honor, just announced a pair of new smartphones to help close out the year. We knew the midrange Honor 7X was on its way, but what came as a surprise was the announcement of the Honor View 10 and its impending release in the US. Thanks to Honor, US customers will have even more choices in the flagship market with this new device.