Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Ever wonder what happens when you hit "ignore" for a friend request? In this tutorial, presented by Facebook, you will learn exactly how to manage your contacts online.

This infographic from SingleGrain aptly and succinctly describes the primary differences between Facebook and Google+. Which social network will reign supreme?
From the article: Foursquare, one of the net’s hottest startups, got an unwanted message on June 20 from a white-hat hacker: it was leaking user data on a massive scale in plain violation of its privacy policy.
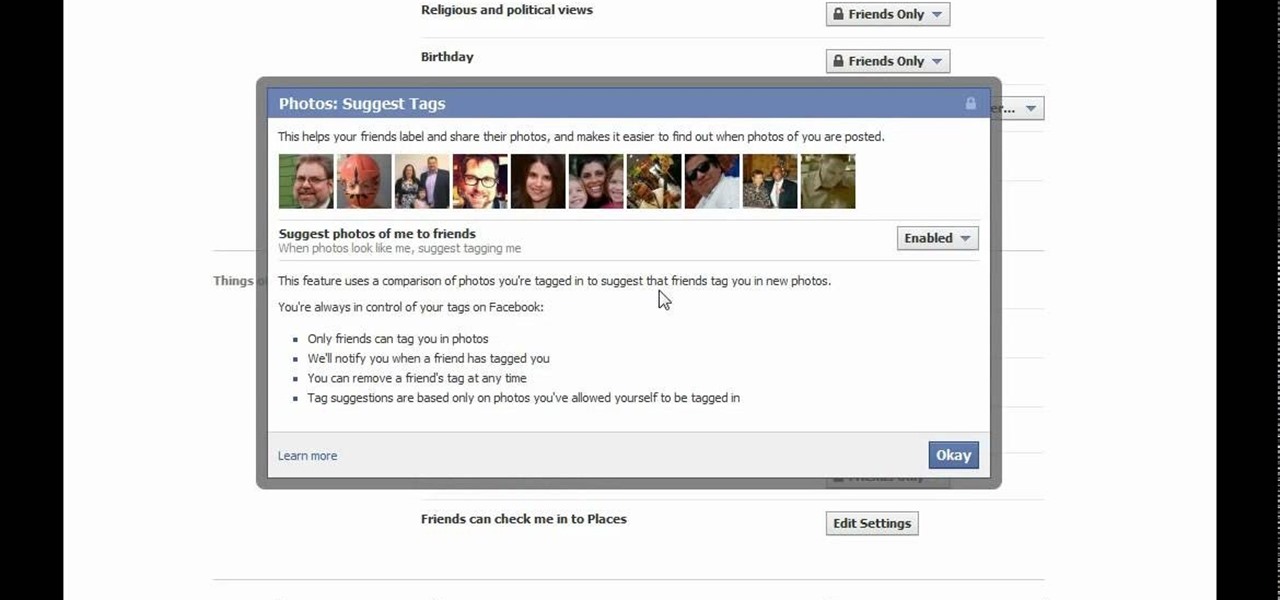
Don't like the idea that Facebook could recognize your face in a friend's photo and suggest they tag you? Take control of your privacy and learn how to disable Facebook's facial recognition feature for photos. You should know when you're going to be tagged in a photo.

Privacy is important. If having your own Minecraft world isn't enough, build yourself a secret room in your Minecraft world. Watch this video to learn how to build a hidden room, perfect for storage of the most valuable items in Minecraft beta.

Sometimes it's necessary to do a complete restore of a device, even an Android one like the Samsung Galaxy Tab. To reset the Galaxy Tab to its factory settings, hit MENU < SETTINGS < PRIVACY and click on FACTORY DATA RESET. Lastly, click on RESET PHONE (it's okay that it's not a phone) and then ERASE EVERYTHING.

In this tutorial, we learn how to keep personal information private when using Facebook. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

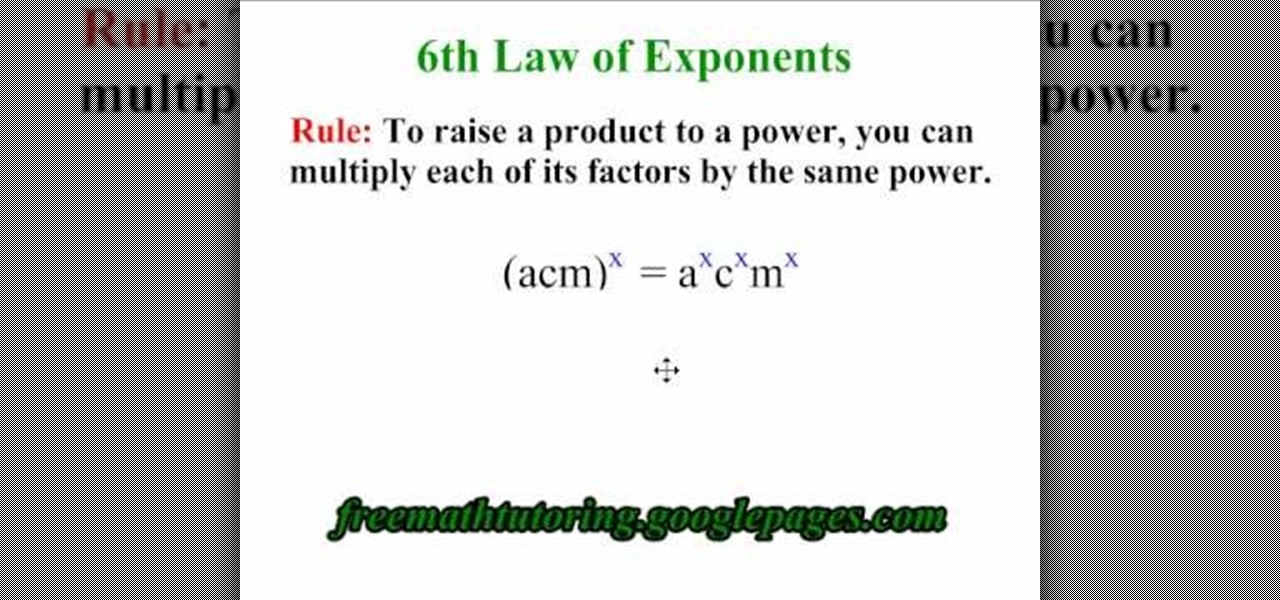
This is a video tutorial in the Education category where you are going to learn how to apply the 6th Law of Exponents. The 6th law of exponents says, to raise a product to a power, you can multiply each of its factors by the same power. For example if you have (acm) to the power x, that will be equal to the product of (a to the power x), (c to the power x) and (m to the power x). How is this done? (acm) to the power x is same as (a to the 1, c to the 1 and m to the 1). What we are doing is, w...

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

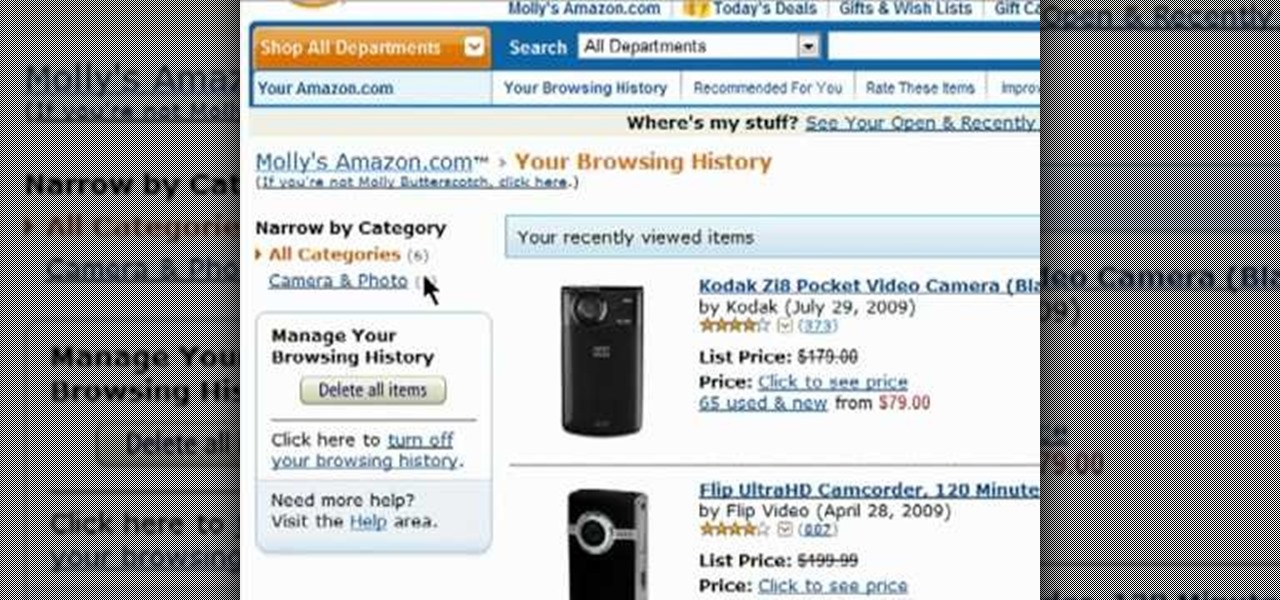
Protect your privacy by editing or completely erasing your Amazon search history. It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

This clip offers easy-to-follow instructions on how to adjust your Facebook privacy settings to prevent your friends (and others) from checking you into locations through of Facebook's Places feature. For more information, and to see how to turn off Places yourself, watch this helpful video guide.

Protect your privacy by using Google Search over SSL. With Firefox, it's easy! And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using Google Search in SSL mode yourself, take a look.

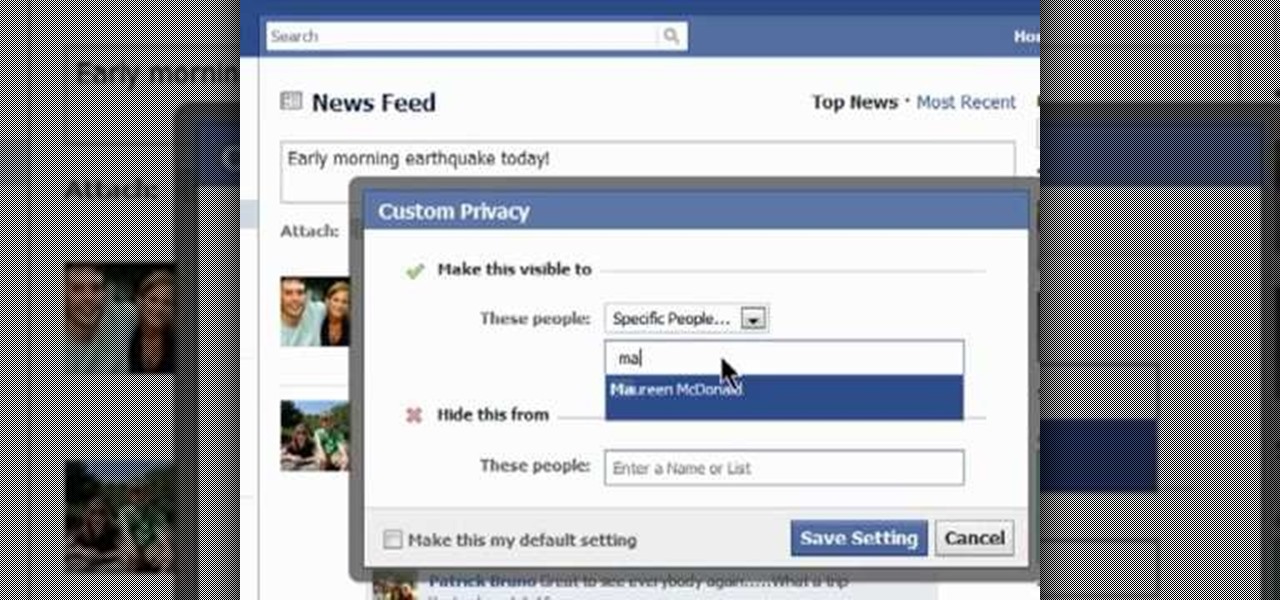
Protect your Facebook posts! This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

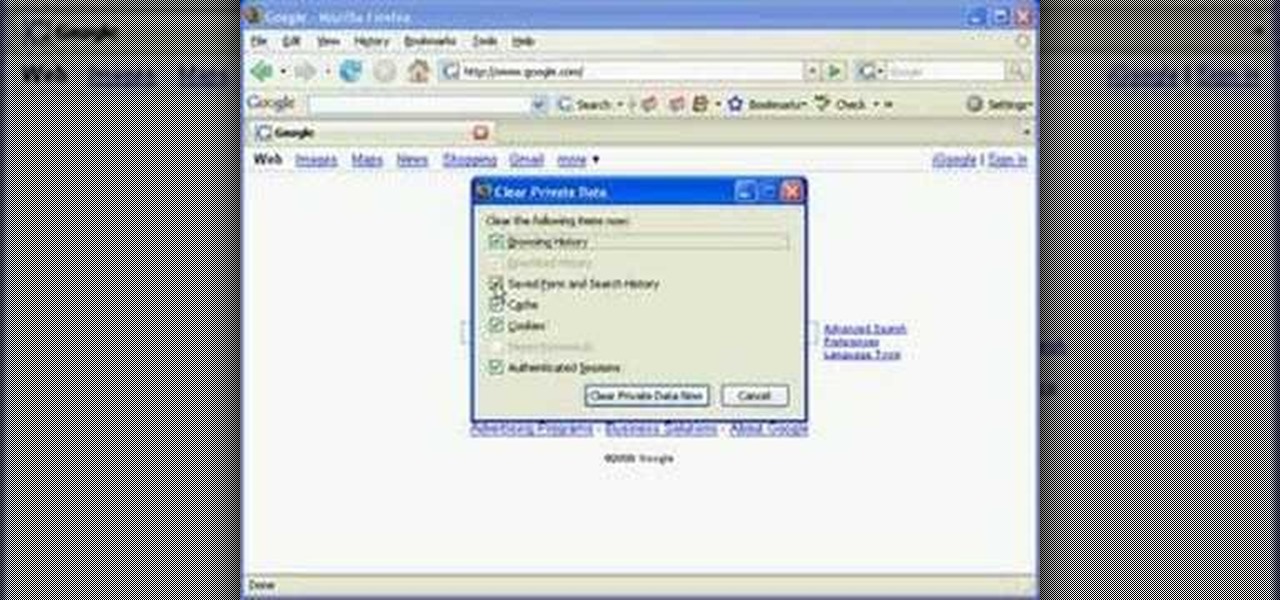
Protect your privacy. With this free video tutorial, you'll learn a method for clearing your Google search history in the Mozilla Firefox web browser. Note, however, that this only works locally and therefore will only prevent those who share the same computer as you from seeing your search history.

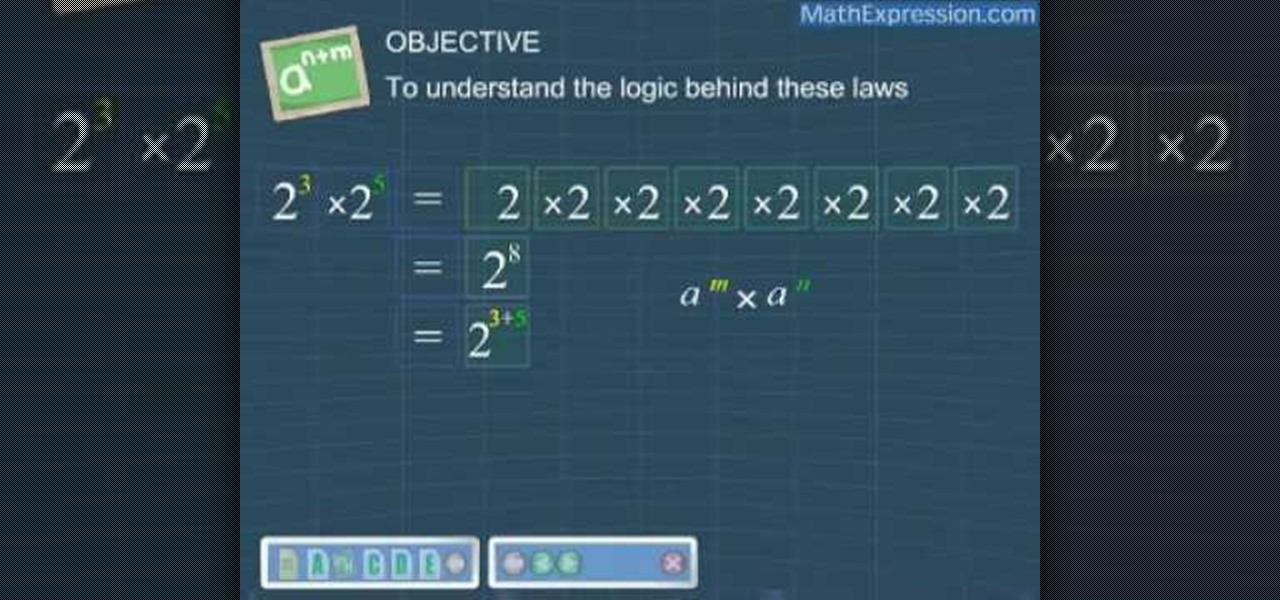
Before you can effectively use exponents, it is necessary to understand the laws behind them. First, in order to multiply a number raised to an exponent, by that number raised to another exponent, just add the exponents: for example, 2^5 * 2^2 is 2^(5+2), or 2^7. In short, a^m * a^n = a^(m+n). Similarly, dividing a number raised to an exponent by that number raised to another exponent can be done by subtracting the exponents: a^m / a^n = a^(m-n). To raise a number raised by an exponent to ano...

In this tutorial the author explains the concept of Newton's Second Law of motion which states that force is equal to mass times acceleration. So the equation to compute force F is F = m * a, where m is the mass of the body and a is the acceleration produced by the force on that body. He explains that even our weight is our mass times the gravity. So now he explains that mass of a body is constant and only our weight changes depending up on the situation we are in. If you want a clear underst...

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Meddlesome mother in laws are pretty cliche these days and a common problem made fun of in many romantic comedies. And while on the big screen the pesky, overbearing mother in law is something to laugh at, having a woman of her nature in your own, real life is ego deteriorating and detrimental to your marriage.

After you start drawing people, you will undoubtedly want to dress them. Drawing clothing is all about knowing how clothes fall, fold and wrinkle. Check out this tutorial, and you will be drawing realistic folks in no time.

There's nothing more disappointing than finding yourself all packed and ready to travel when you find your flight has been canceled. You can make the best of the situation by finding out just what you are entitled to or how to best ameliorate the situation.

Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Log In First, log in to your Facebook account.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

If you use Office 2008 for Mac and all its applications (Word, PowerPoint, Entourage, Excel), than you need to know about the predefined workflows available using the Script menu that uses Automator to help perform mind-numbing tasks. The Microsoft Office for Mac team shows you just how to save time by using predefined workflows in this how-to video.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

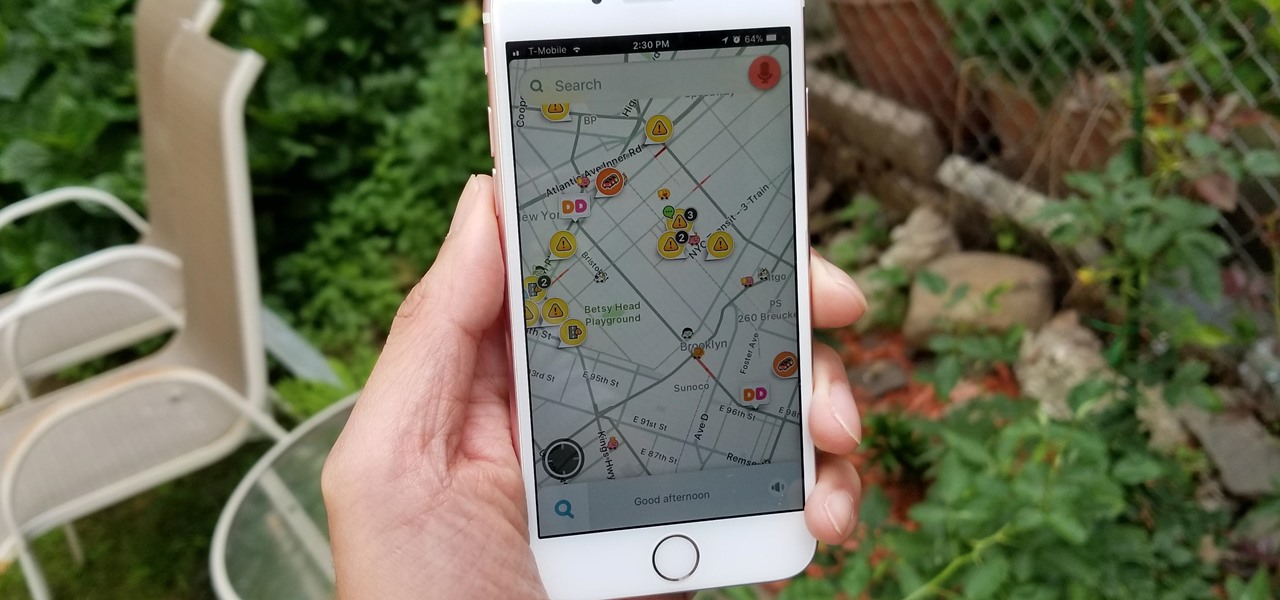
Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

We've heard a lot about self-driving taxis, as car and ride-sharing companies compete to win the driverless gold rush. But FedEx wants to bring its enterprise into the mix, as the head of its freight division has asked the US government to develop laws for self-driving trucks.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.