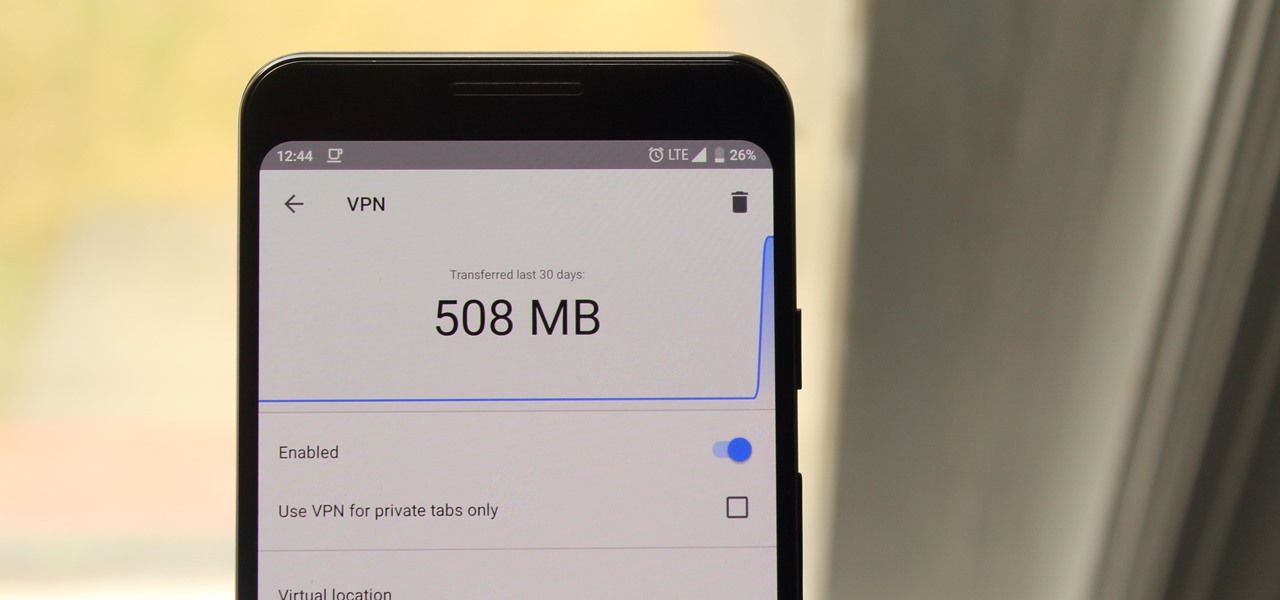
Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Almost everyone uploads their very personal photos in facebook trusting facebook's privacy settings. But question is - is facebook's privacy settings really that trustworthy? Few months ago, while browsing facebook, I found that one can easily access your private photos using the same browser you used to browse facebook.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

With all the documents ready, we need to fill our wallet with money for the travel. This video discusses various ways of filling the pocket. That is how to prepare the money for international travel. Over the years credit cards have been widely used by many travelers, which is safer than carrying cash. In this case we need to contact the credit card provider well in advance and notify them about the travel. Also we need to learn about the various fees applicable to international purchases. Th...

What type of protection does Doug have in this scene from The Brady Bunch Movie?

Zero chance of your ride being jacked with this level of protection. You will need: a 100,000 volt tesla coil strapped to the roof of your vehicle. Created by tesla master, Peter Terren. Previously, Electrifying Transparent Tesla Coil (DIY!!)

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Not exactly enthused about who your daughter chose to marry? Turn lemons into lemonade by getting along with a deadbeat son-in-law – despite how you may feel about him.

Law and business are frequently connected more closely than many are comfortable with. Thus, writing business case studies is a big part of legal life in law school and when working at a firm. Watch this video to learn how to write a great business case study.

In this clip, you'll learn how to get started using Symantec's Endpoint Protection Small Business Edition on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.

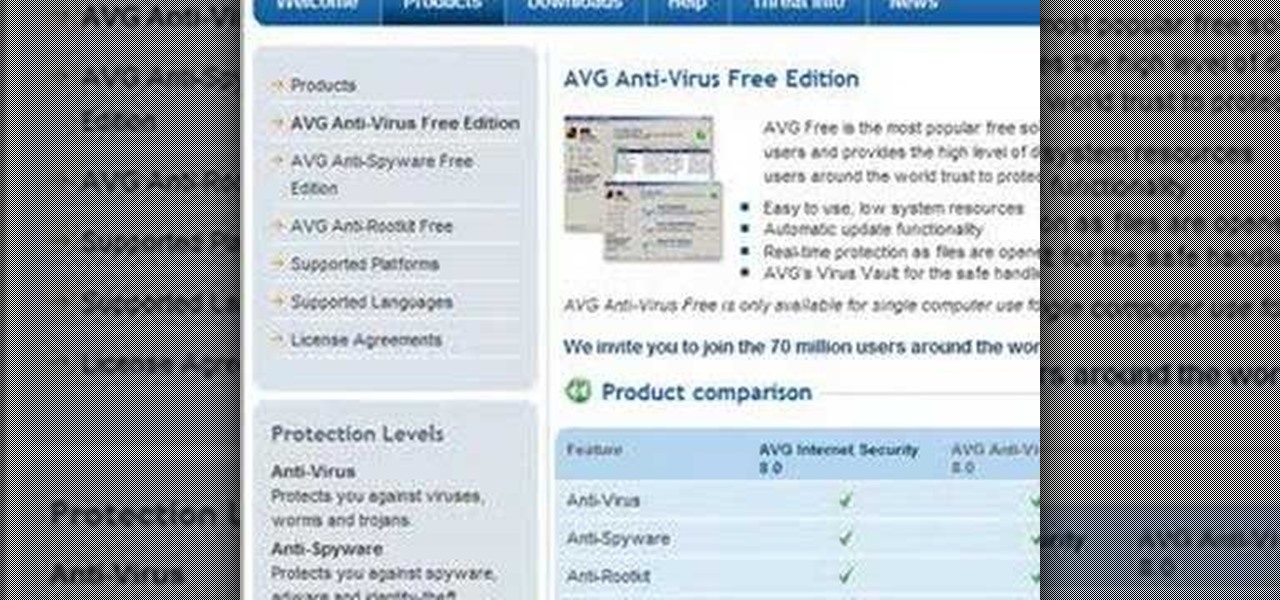
AVG Free from Grisoft provides you with basic antivirus and antispyware protection for Windows and is available to download for free. The only trick is finding it on the AVG website. In this video tutorial, you'll learn how to find and install AVG on your own Windows PC. Take a look!

RC Car Action Magazine Editor Matt Higgins explains how to modify your antenna cap for better wire protection. Make sure that antenna cap doesn't go flying off. Watch this video tutorial and learn how to secure the antenna cap on an RC vehicle.

A pop filter or pop shield is an anti-pop noise protection filter for microphones, typically used in a recording studio. In this how to video learn how you can make a pop filter out of cardboard and fabric for recording with microphones.

This video shows you how to take off the DRM (which is kind of like copy protection) from music and videos that you bought from a Windows Media Player online store like Urge or Napster.

This guitar lesson shows how to play "Breaking the Law" by Judas Priest.

This gorgeous '60s hairstyle was inspired by the Audrey Hepburn film "Breakfast at Tiffany's." This look is quite elegant and suitable for formal events. Most importantly, it is very easy to create.

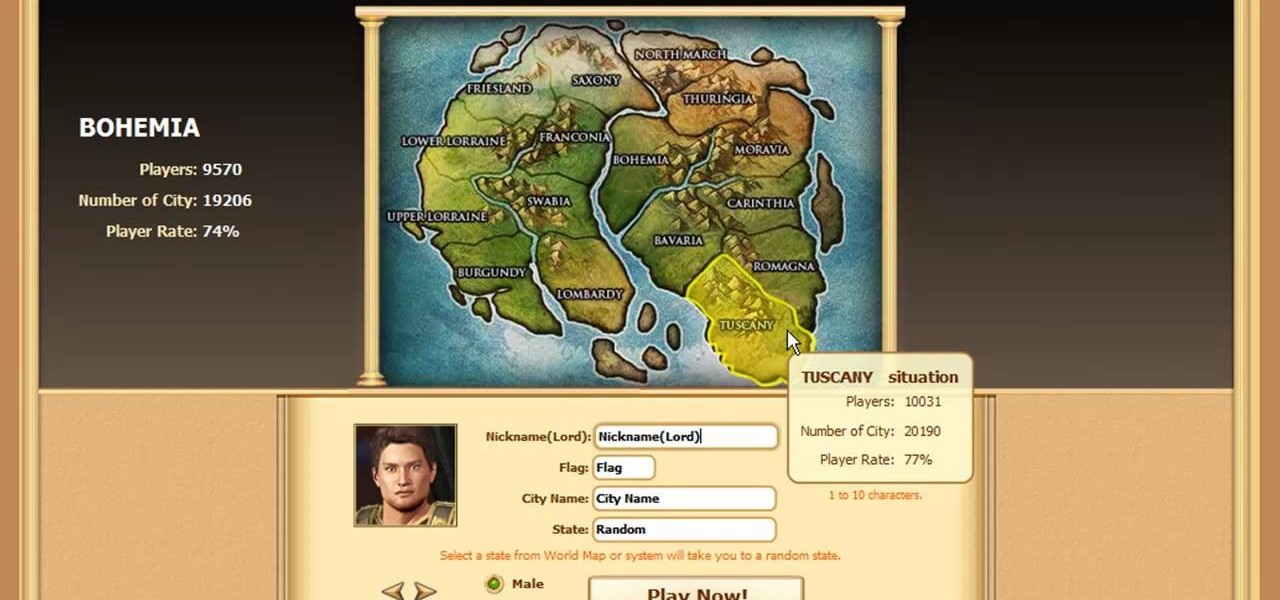
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play the basics in Evony online. See exactly what the game Evony is!

When owning a home one type of lever set you may have in your home is a privacy lever. In a privacy lever set, the main feature is that the door can only be locked from the inside. Sometimes a kid might get locked in or someone may accidentally lock the door behind them. It's really easy to unlock it in an emergency.

I will illustrate a simple, yet effective way to stop tracking and third-party cookies without installing any additional software on your computer. Third-party cookies are often used to track your visits and activities on webpages and can slow down your browser and hinder your privacy. They are often the most common detected adware or spyware installed on most computers.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Have you ever secretly pined away for a career in interior design, even though you're currently stuck in law school because, well, your parents forced you and gave you no other option? Because law school can be a bit rigid in terms of what you learn (pretty much it's just facts and figures and learning sound logic), it's important to indulge your creative side ever once in a while.

Google has caught a lot of flack for various privacy infringements over time. Google Buzz was the latest uproar, when lack of proper prior testing allowed the tool to expose a slew of information users did not necessarily want shared, resulting in massive complaints. A Harvard student even went so far as to file a lawsuit (read more).

Mr.G in the episode 3 of "Summer snow fall" explain the experiment for eddy currents and lenz law by using general house hold items like copper tubes of different dia., 2-neo themium magnets attached together and a ball bearing magnet. At first he took the big diameter copper tube and drop the neo-themium magnets, they fall slowly without touching the surface of the copper tube as they are like freely falling from space with less gravity, for the next time he took small diameter copper tube a...

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

While it may not be an obvious feature, Apple actually built a way into iOS that lets you hide specific pictures and videos in the Photos app that you want to keep on the down-low, for your eyes only. If you show off your photos a lot or stream slideshows to your TV, this is a great way to keep less appealing content private.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

Want some protection for the front of your new Arrma-RC Vortex? Here's how!

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.