There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Free online dancehall step tutorials every wednesday at 10am for the entire summer! Learn your favorite dancehall steps in the privacy of your own home! This one covers the Nuh Linga steps.

We know that Facebook is a very useful social media sites. This video will help you how to hide friends list on Facebook from others.

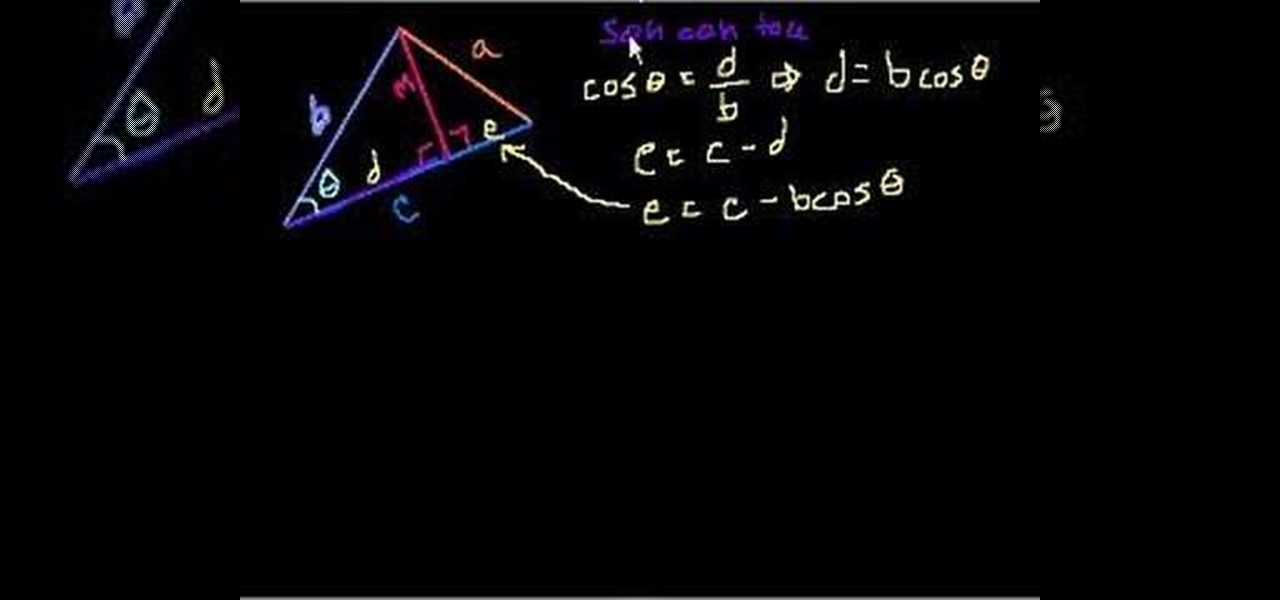
Want to solve for a side of a triangle when 2 sides and an angle are known? Learn how with this free video trig lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free m...

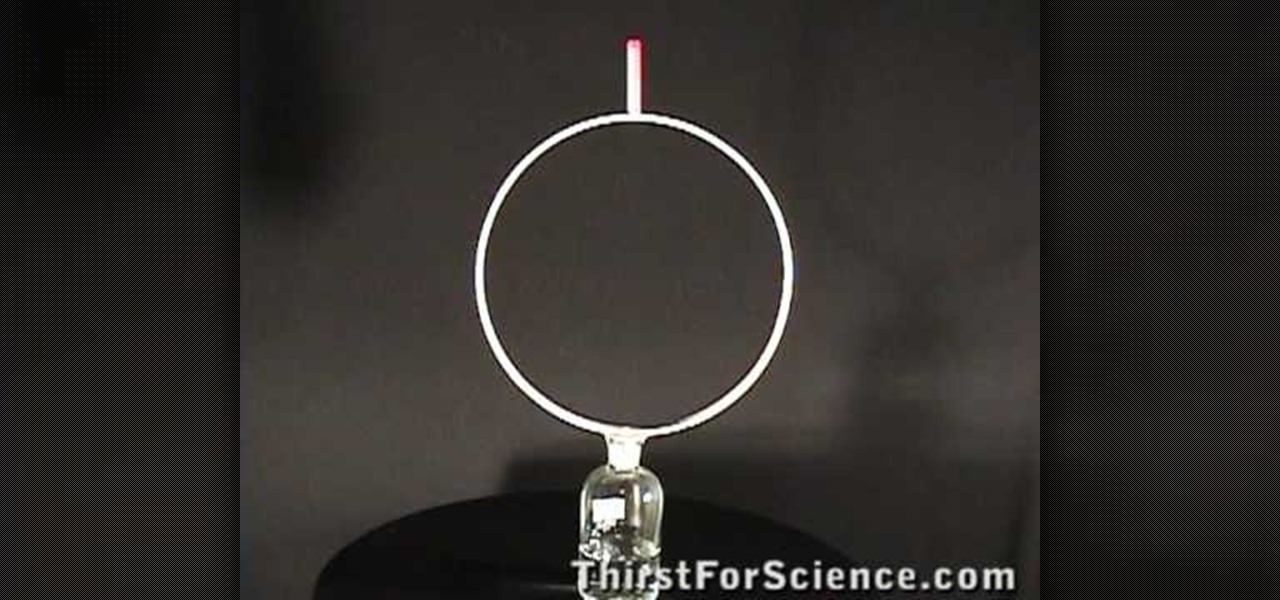
Newtons proposed the concept of inertia. According to him an object at rest tends to stay at test and an object in motion tends to continue in motions unless acted up on by an external force. This is the principle of inertia. The tendency of the body to continue to stay as it was is called its inertia. You can demonstrate this principle with a simple experiment. As shown in the video when the hoop is pulled out the pen cap falls in to the bottle. Here the hoop is acted upon but the cap is not...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

In this video we learn how to make a poppet. A poppet is generally used to give protection, healing to the ones we love. It may be our cat, aunt, home, or whatever we like to do it for. Here in this video we make a poppet for an animal. So the requirements are color shields, scissors, lavender and roots (for protection), citrine. Citrine helps in cleansing. Draw the shape of the animal we require on a cloth of two stacks and cut it using scissors. Use the thread to attach the edges. Leave a s...

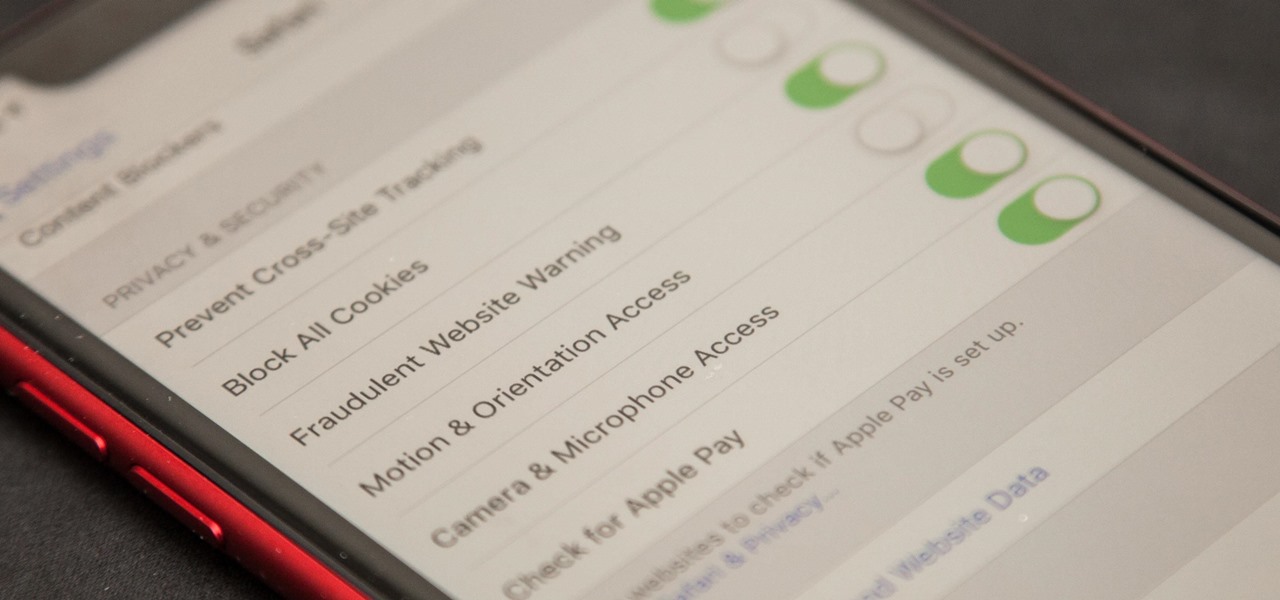
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

You know the signs—sneezing, fever, nagging cough, no energy, no appetite. It's the flu, but this time, it's your dog who's down and out. Yes, dogs get the flu, too. However, a team from the University of Rochester Medical Center and their collaborators have developed a new vaccine that may make the doggy flu a thing of the past.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012.

In this video tutorial, viewers learn how to make their information more private on My-Space. Users will need to begin by logging into their account. On your homepage, click in Account Settings and click on the Privacy tab. Under General Privacy, users are able control who sees their online status, birthday and photos. To only allow friends to view your profile, select "my friends only" from Profile Viewable by. Users are also able to block other users by age and to block specific users from ...

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

In this video, Robert Ahdoot becomes "surfer dude" and shows us the ways of deductive reasoning, as relating to geometry. He begins with a simple example of a syllogism, taking two premises and using them to form a conclusion. This is called the Law of Syllogism. This concept is then used for geometric statements. If two angles are complementary, they sum to 90 degrees. If two angles sum to 90 degrees, then they are acute. By the law taught, it can be said that if two angles are complementary...

This video is a tutorial on how to ride a bike in traffic. The first rule is to obey the law. You would need to follow the laws of traffic as though you were driving a car. If there is a bike lane, use it. It is not a good idea to use the sidewalk as that is reserved for walkers and runners. Ride predictably by signaling your turns. The video tells the viewer which side of the road to ride on, and also provides tips. He also discusses how to ride with another cyclist. This is a very informati...

This video explains how to delete cookies in Windows XP, Mozilla Firefox, Internet Explorer and Opera. To delete cookies in Mozilla Firefox, choose the "tools" option from the tool bar, then choose "options", then choose "privacy". Many options will be given under the "privacy" menu, but make sure to choose the following options- "accept cookies from site" and "accept third party cookies", then choose the option "I close Firefox option" under "keep until" then choose "ok" to delete the cookie...

Looking to impress your friends with some cool tricks? Why not trying to make water defy the laws of nature?

Starting to work at home? With more and more people trying to make a solid living at home, it's important to know the best way to set up a home office – even if you don't have a spare room. Learn how to set-up a solid work environment with tips from this video on how to create the perfect home office.

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

In this epsiode of Video Vocab we're going to look at basic vocabulary related to the law. This is the first in a three-part series: part 1 covers basic legal terms, part 2 will look at words related to a court case and part 3 will look at the vocabulary related to commercial law.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

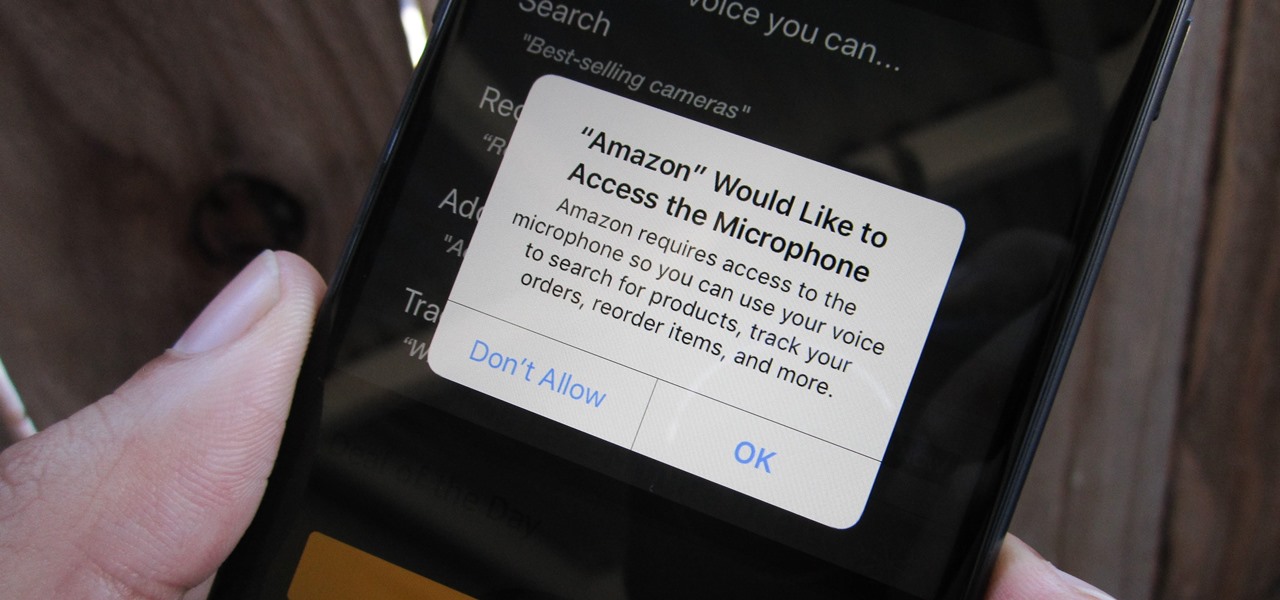
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.